In this video, we learn how to play Warcraft III Frozen Throne on Garena. Before you do this, you must have Garena installed by going to Garena Download. Next, open up Garena and log into your account. Next, click on the game you want to play and choose settings. Now, choose the game you want to play and click on "ok". Next, choose the game and your country, then choose a room to play in. Press 'start game', then the game will start to load. Choose local area network, then choose a room and s...
In this video tutorial, viewers learn how to hack the prestige mode in the game Call of Duty: Modern Warfare 2. Prestige Mode is an option that a player can choose after they progress to Level 55 (Commander) and gain a little more experience. With this hack, viewers will be able to prestige their account to any level, and unlock all emblems and titles. Users will need a USB drive to transport files between the computer and the video game console. This video will benefit those viewers who play...
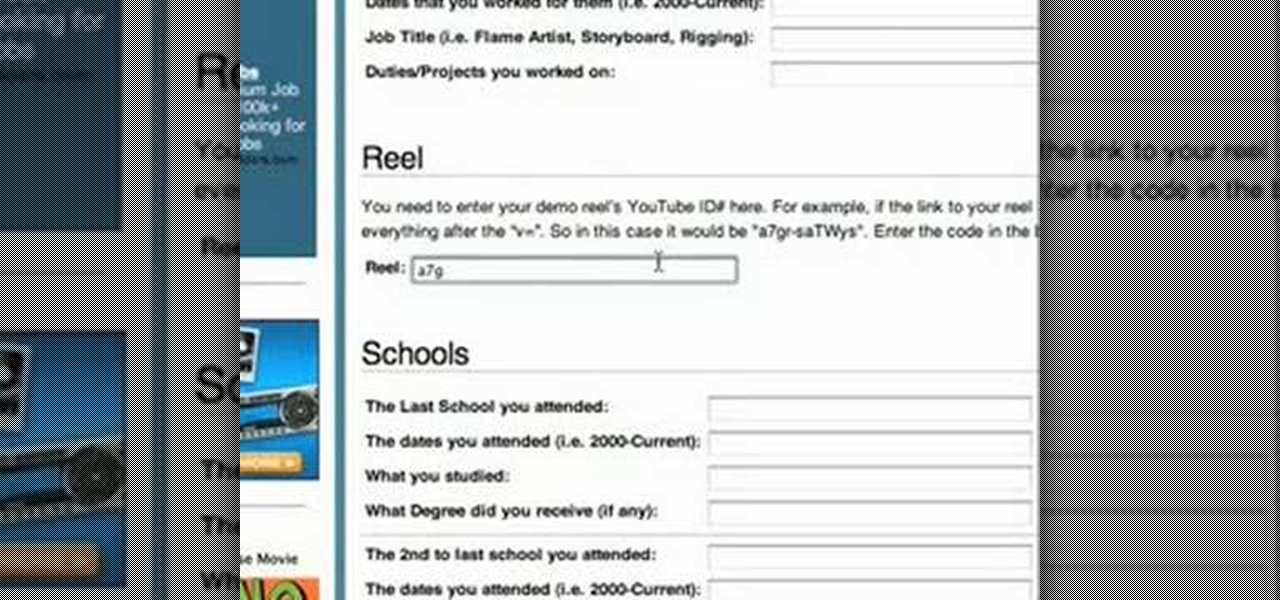
This video teaches the simple steps to make an animation resume at Ani-Jobs. An excellent summary is given below. First click on the Resume cafe tab on the top menu, log in or create an account if you don't have one. Select a suitable category like 2d Artist, click the Storyboard sub-category. Add your name to enter the resume building page and start to input your details. In the reel column give the number that comes after "v e" in the link. Upload your résumé, artwork and your comments, lea...
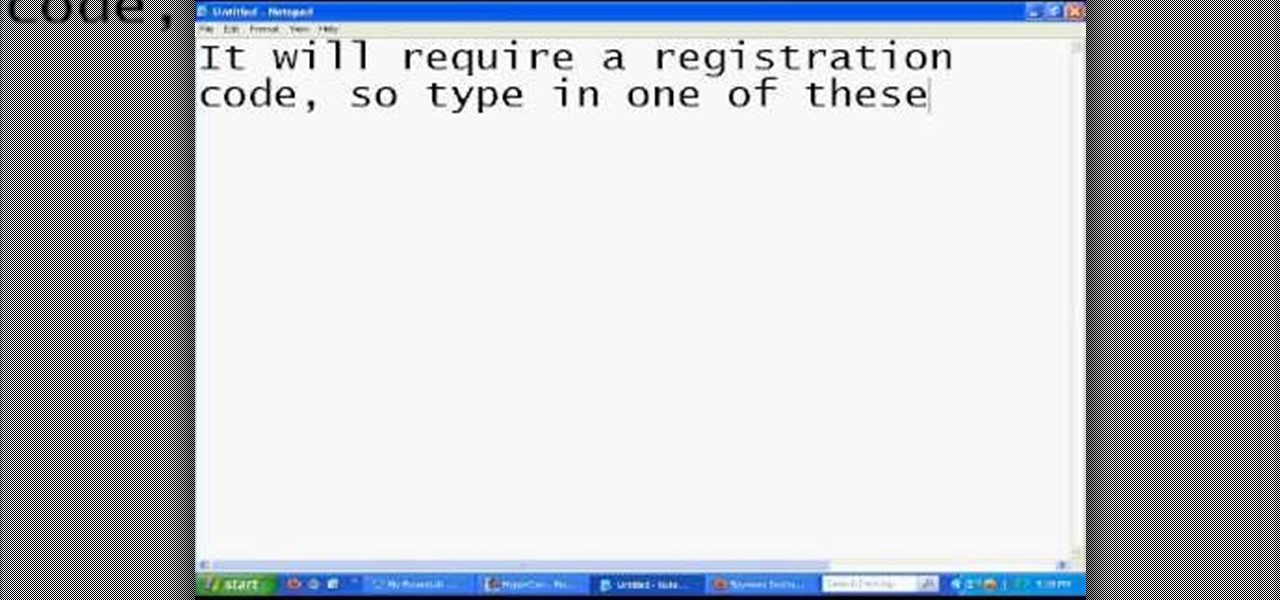
This video shows you how to easily remove the Security Tool virus. The first thing you have to do is restart you computer. Once restarted, immediately hold down CTRL+ALT+DEL. In the Task Manager you should see: Security Tool. Quickly end it now. The virus is temporarily disabled. Now go to: Download and install Spyware Doctor. Scan your computer and click Fix All. It will ask you for an account...
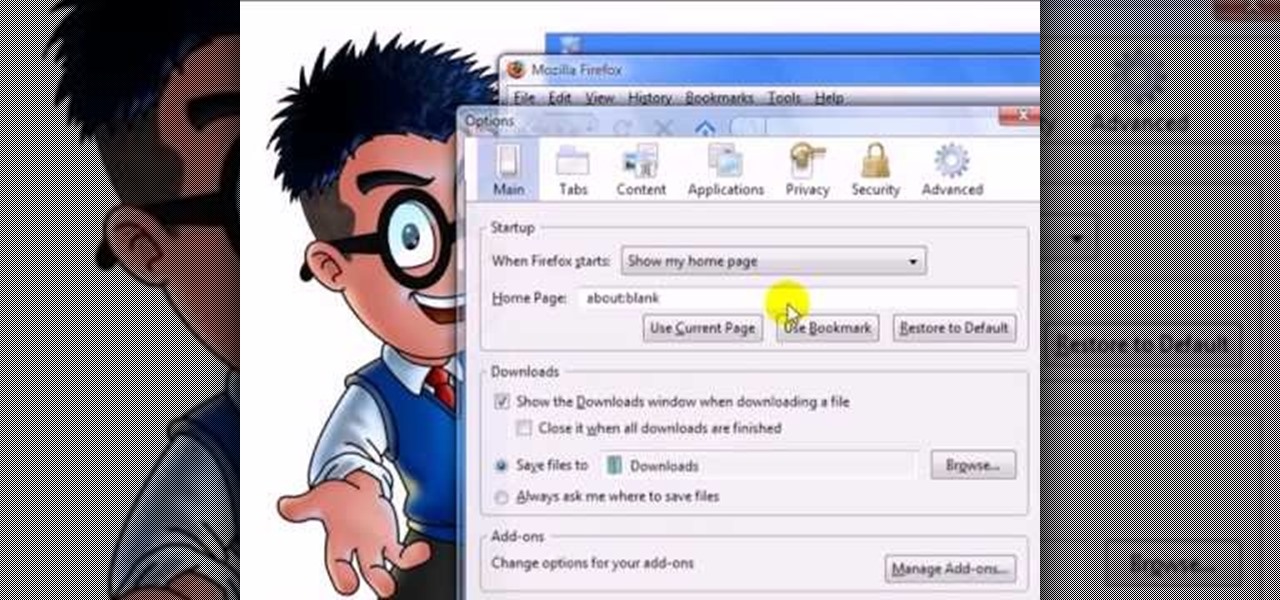
With this useful video, you will learn some tips and tricks about how to delete your web browser history, passwords, cookies, also cache form data and temporary internet files.
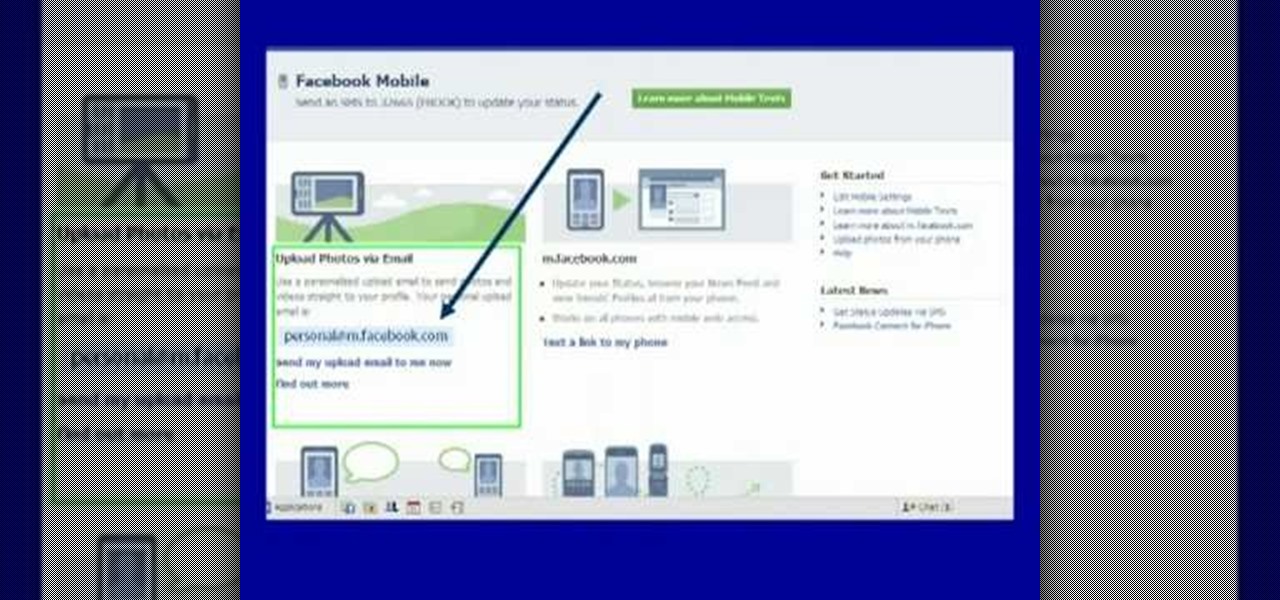
Moniquewade will show you how to upload photos and videos to Facebook by using email. The user has seven steps for you to follow in order to upload photos and videos to Facebook using email services very fast and easy. The first step starts out by telling you to go to Facebook.com. By following each of the seven steps that are provided, you should be able to send different types of photos and videos to your Facebook account just by using email.

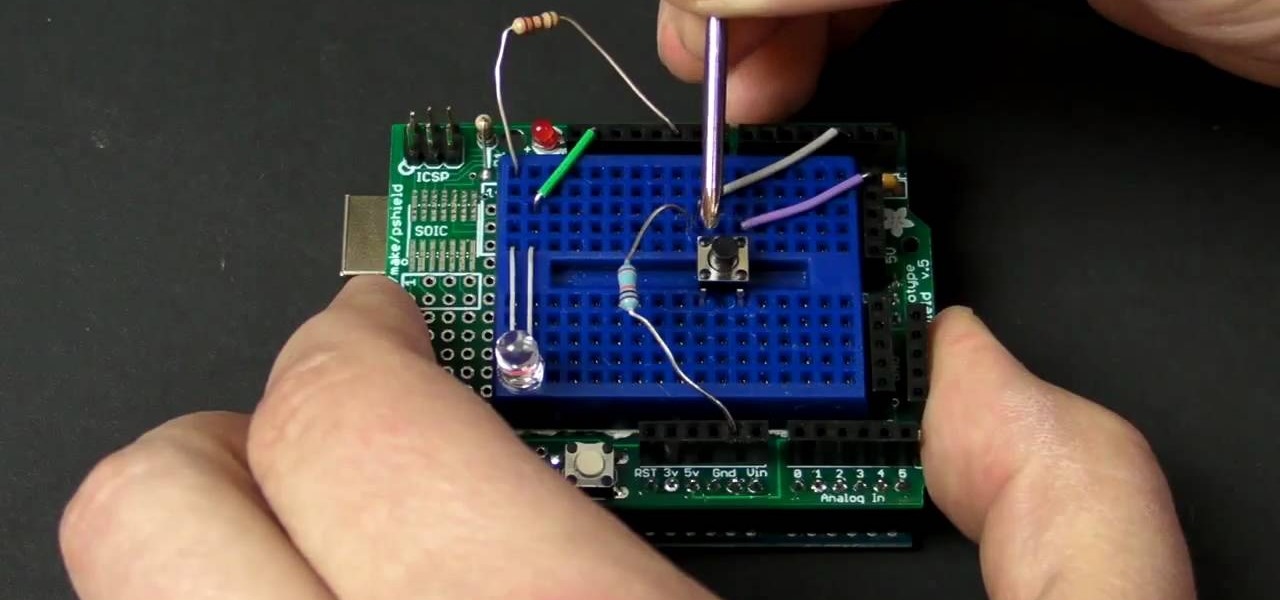
See how to a a button with Arduino with MAKE Magazine! This is a video tutorial on a favorite little micro-controller, the Arduino. This is a really informal how-to, and is meant to show you just how fast and easy it is to work with the Arduino.

You have a webcam, right? Nowadays, who doesn't? But just because you all have webcams doesn't mean you're using them the same way. And a great way to take full advantage of your peripheral or built-in webcam is by turning it into a security camera. This video will show you how to turn it into a security cam by accessing the video feed remotely over the internet. And it's a really simple solution—you just need to sign up for a USTREAM account, which allows you to stream webcam footage live!

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

Open TikTok, and you might find yourself spending hours watching video after video. While each video is usually pretty short, it's highly possible to binge-watch hundreds at a time. It's even more fun to create your own. But as a parent, you may not want your children falling into this same trap, and it's easy to limit how much time they spend watching TikTok videos on their iPhone.

The iTunes App Store makes it easy to buy an app or game on someone else's behalf, and it's a great way to send an iPhone user a thoughtful gift. The Google Play Store doesn't have such functionality, but there are still a few workarounds to accomplish the same goal: gifting an app to an Android user.

With new iPhone models out, you'll have updated cameras to try out, a faster processor, and new colors to choose from. The only thing that could stop you from picking one up yourself is, well, your current iPhone. Here's how to check if you're eligible to upgrade to iPhone 11, iPhone 11 Pro, iPhone 11 Pro Max, or any other iPhone still being sold.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

We're nearly there — Apple released the seventh iOS 12 beta to developers Monday, August 13. While not totally unexpected, beta testers understand the struggle of predicting the next update, as Apple has switched haphazardly between two-week, one-week, and irregular release schedules for both the developer and public betas.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

If you've taken the time to edit a video on your iPhone or Android phone, you probably have a purpose for it. Maybe you want to share it to YouTube in hopes of making the next viral sensation. Maybe you just want to save the video to your phone to show off to friends and family when you can.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

While the official unveiling will happen at Mobile World Congress in Barcelona on March 1st, several images and promotional videos for the HTC One M9 have leaked online.

For quite some time, Netflix and Verizon have been duking it out, and it seems that things have just a little saltier between the two:

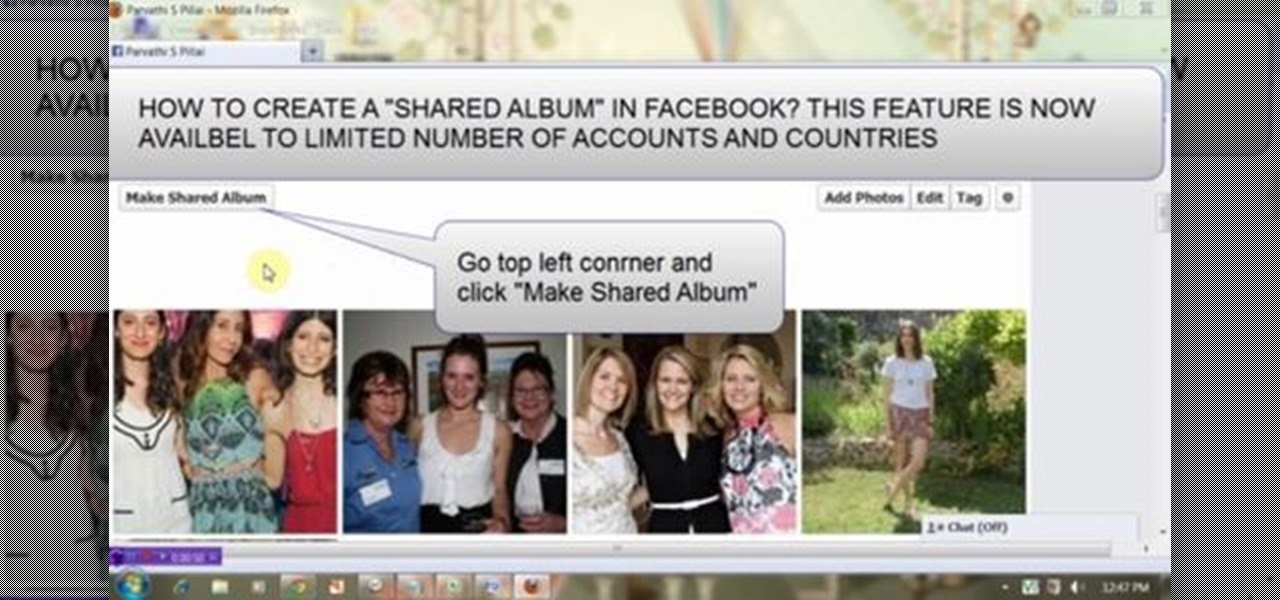
Facebook is a very useful social media sites. Shared album is a place where multiple users can upload, view and edit photos. Maximum of 50 people could share a Shared album. This video will show you how to create a shared album on Facebook. Hope this feature will be available to all users and countries in near future. Watch the video and Employ the technique in your Facebook account.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

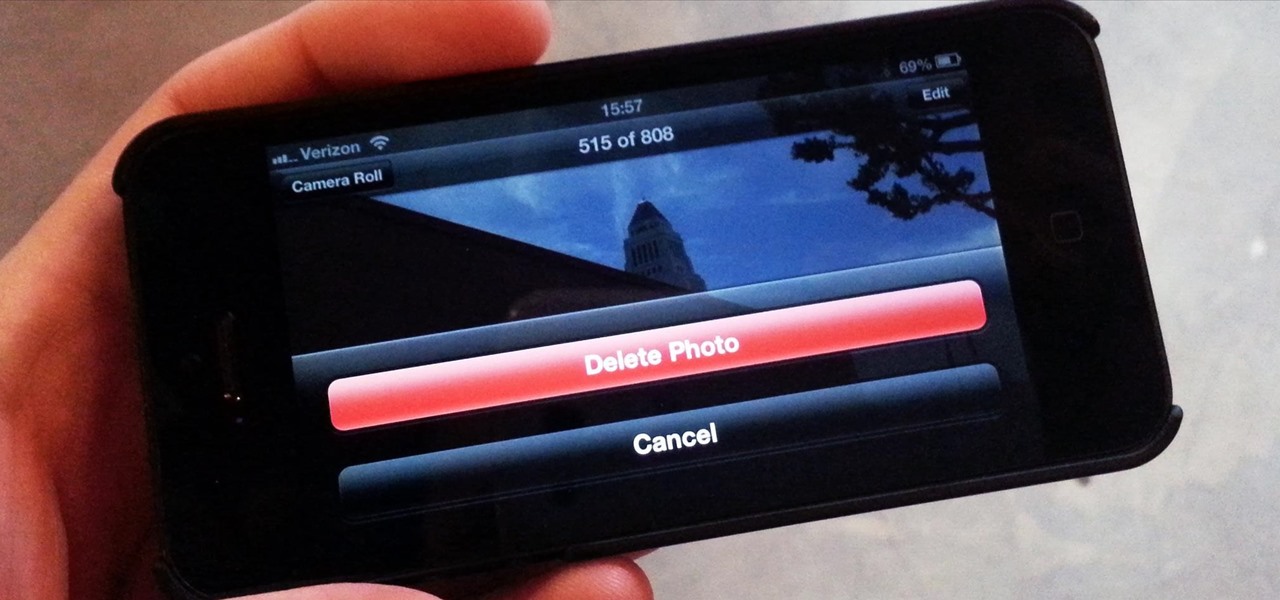
In one of Apple's newer ads, the company claims that "more photos are taken with the iPhone than any other camera." If this is in fact true, then it might also be appropriate to say that more photos are accidentally deleted on iPhones than any other camera.

Attaching files to an email is way more convenient than trying to link people to third-party file transfers. Unfortunately, the standard 25MB limit is far too small to send some files, like large videos or multiple audio files.

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

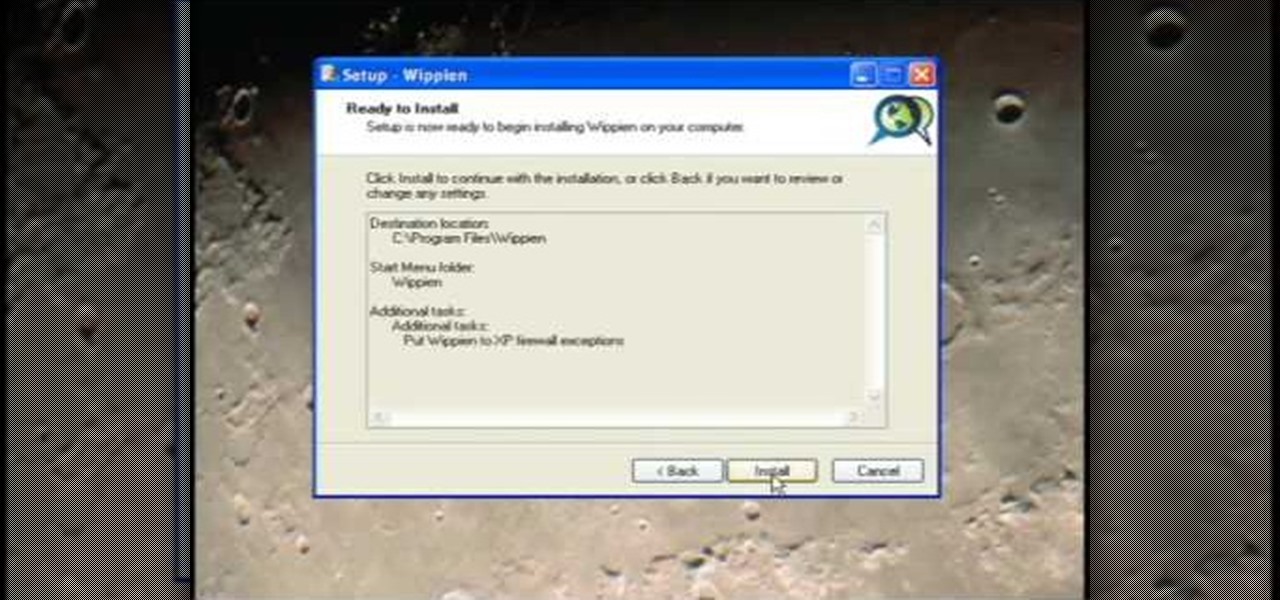
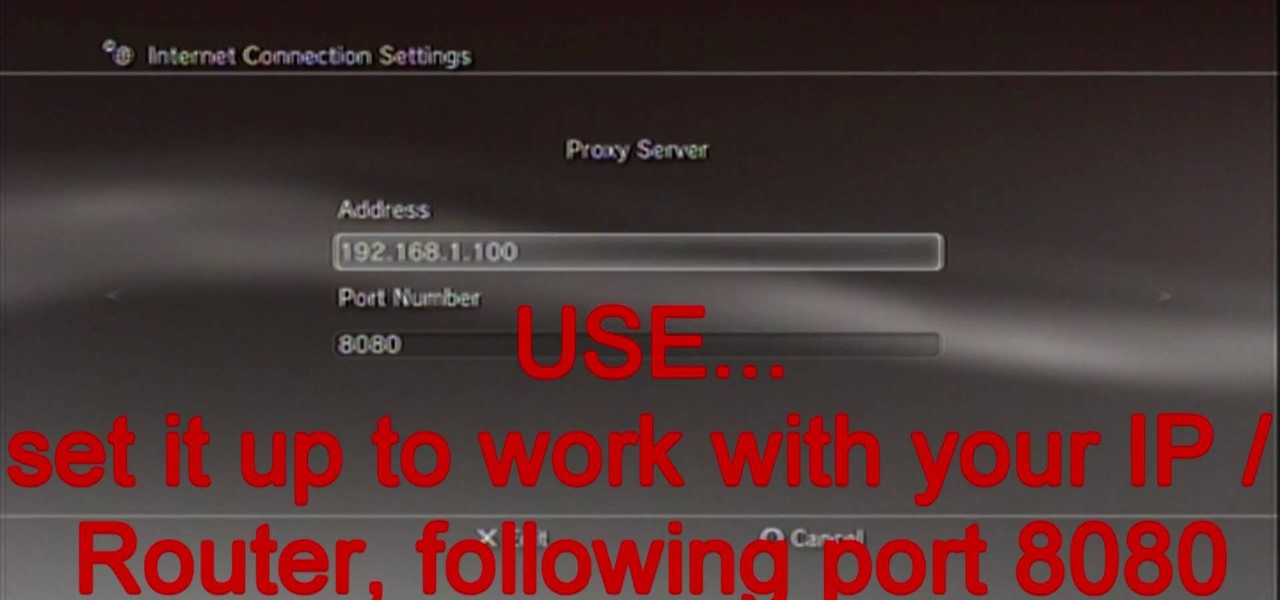
This video tutorial from ruralgeek shows how to set up and use Wippien VPN on Windows XP. First, download Wippien client from here: www.wippien.com.

It was bound to happen with all those numbers floating around in your brain – you've forgotten your Windows password. Here's how to recover it.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

Most of you have probably wondered at least once who has been checking out your social media profiles. While most platforms prohibit you from seeing who's viewed your profile, such as Facebook, Instagram, and Twitter, TikTok is one of the few places that lets you track profile visitors. And unlike with LinkedIn, you don't have to pay for the privilege.

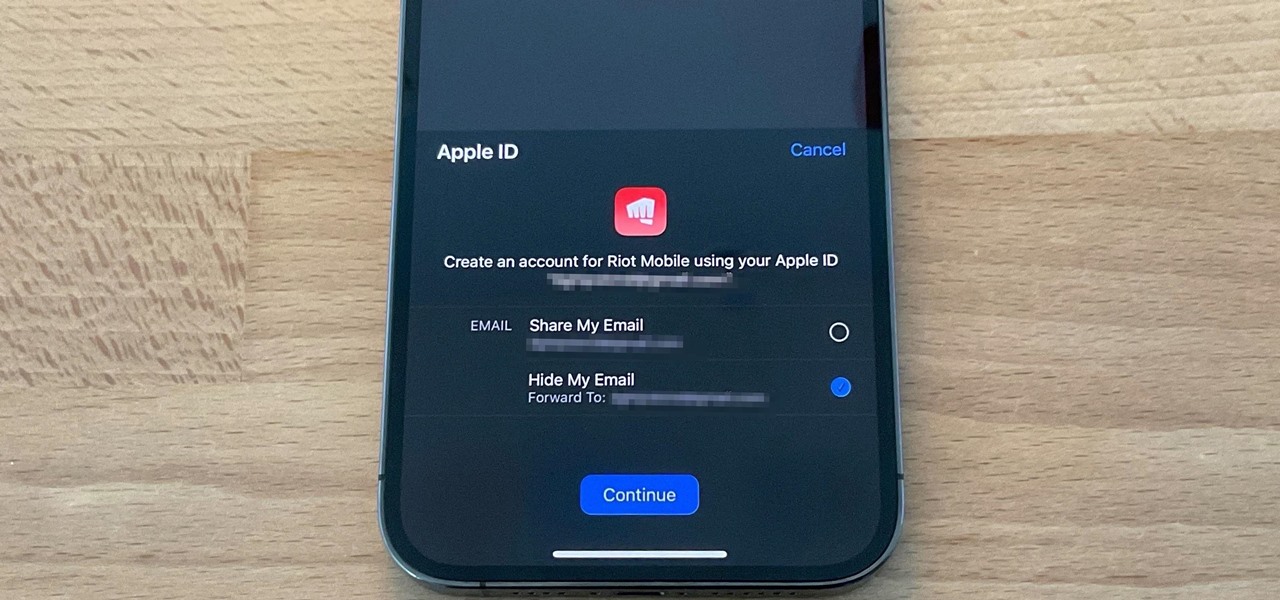
The "Sign in with Apple" service lets you create accounts with third-party apps and websites more easily using your Apple ID. More importantly, it can hide your personal email address using auto-generated disposable email addresses. However, it's easy to lose track of the accounts you use with Sign in with Apple, as well as any throwaway email addresses you used to hide your actual address.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

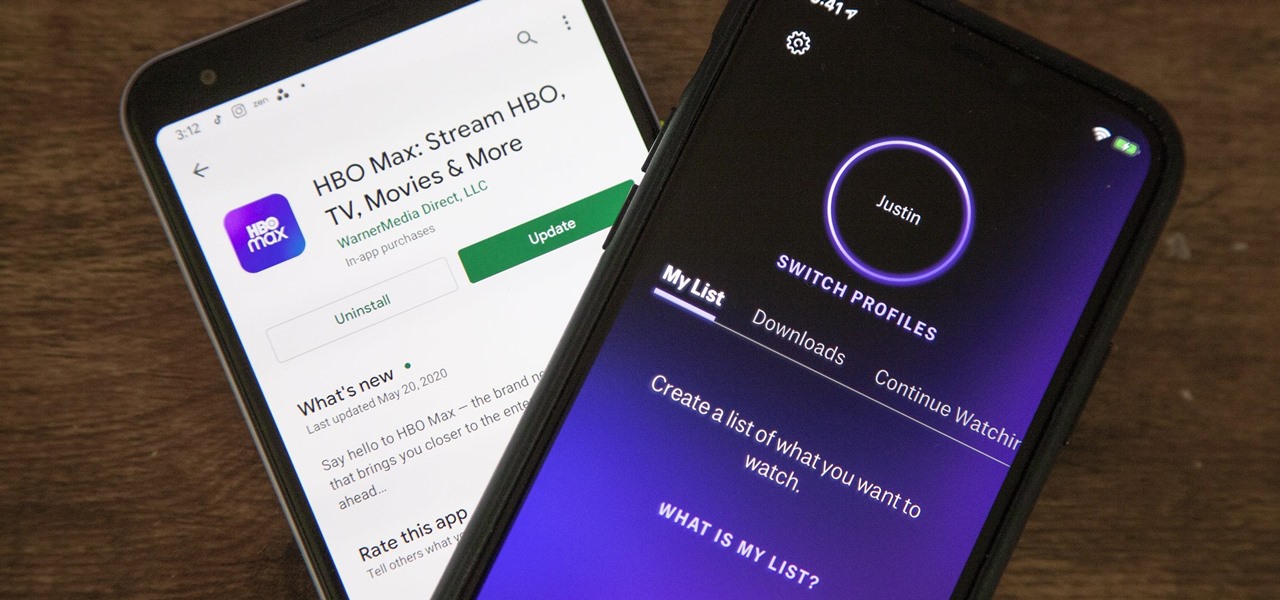
As of May 27, HBO Max is taking over your HBO Now or HBO Go account. If you have your devices set up to auto-install new app updates, you should pause it right now if your HBO app hasn't been updated yet. There's one thing you'll want to do before you make the leap. However, you're not out of luck if you already upgraded.

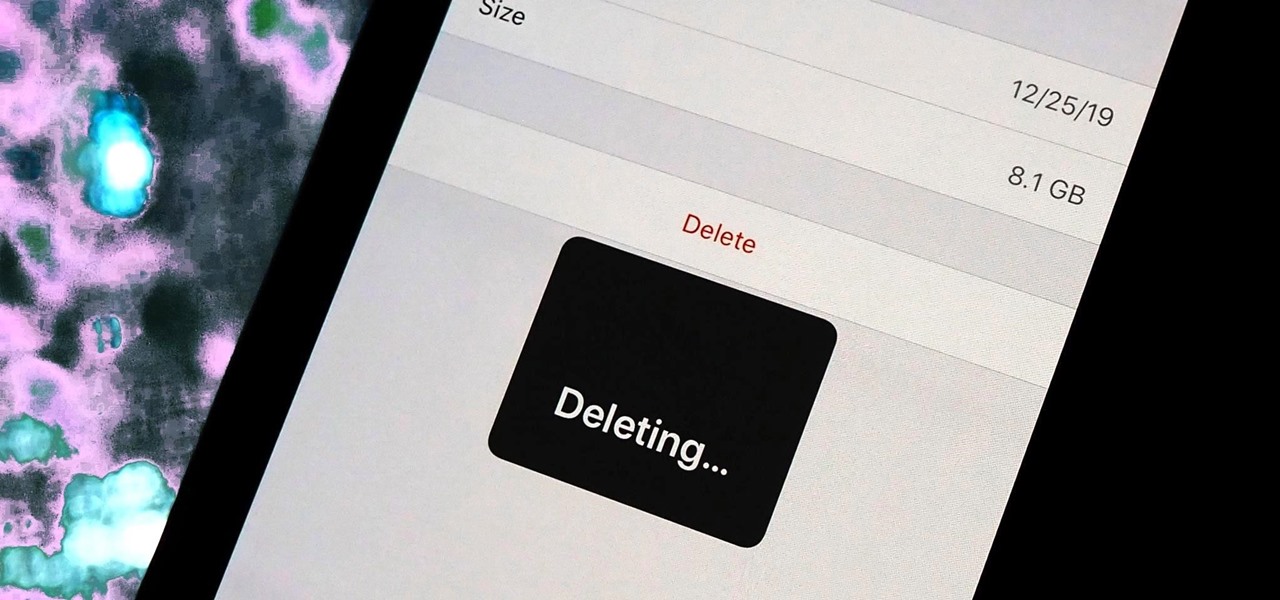
If you use iCloud, you may have experienced alerts such as "Not Enough Storage" and "iCloud Storage Full," especially if you're on the free 5 GB plan. To clear up space on your iCloud account fast, you can delete large files here and there, but trashing one thing, in particular, can clear up gigabytes worth of space instantly.

Following someone on Twitter is an investment. You virtually agree to have their opinions, tirades, and hot takes spewed across your timeline. It can get annoying real quick if they're known to post controversial comments periodically. However, there are other ways to stay updated on someone's tweets without you having to hit the follow button and go all in.

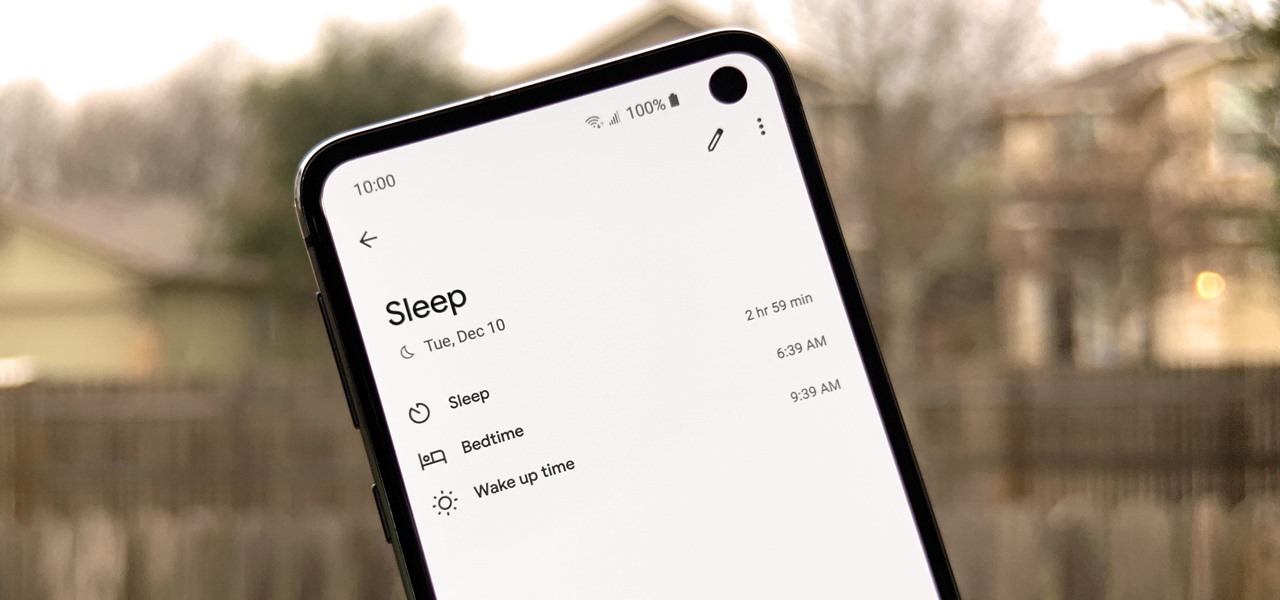
When trying to get fit, something that can easily be overlooked is your overall sleep quality. Your body needs sleep to recharge and it helps to maintain a healthy lifestyle, there's no denying it. Luckily, Google Fit can help you track your sleeping habits without having to jump through any hoops along the way.

Slack is meant for business, but it's inevitably used for personal reasons too, or even just to goof off with colleagues. However, you never know who's looking over your shoulder (nosy coworker? boss?), and you could get in trouble for something sent to you. That's why you might want to hide images and GIFs to help keep your conversations private.

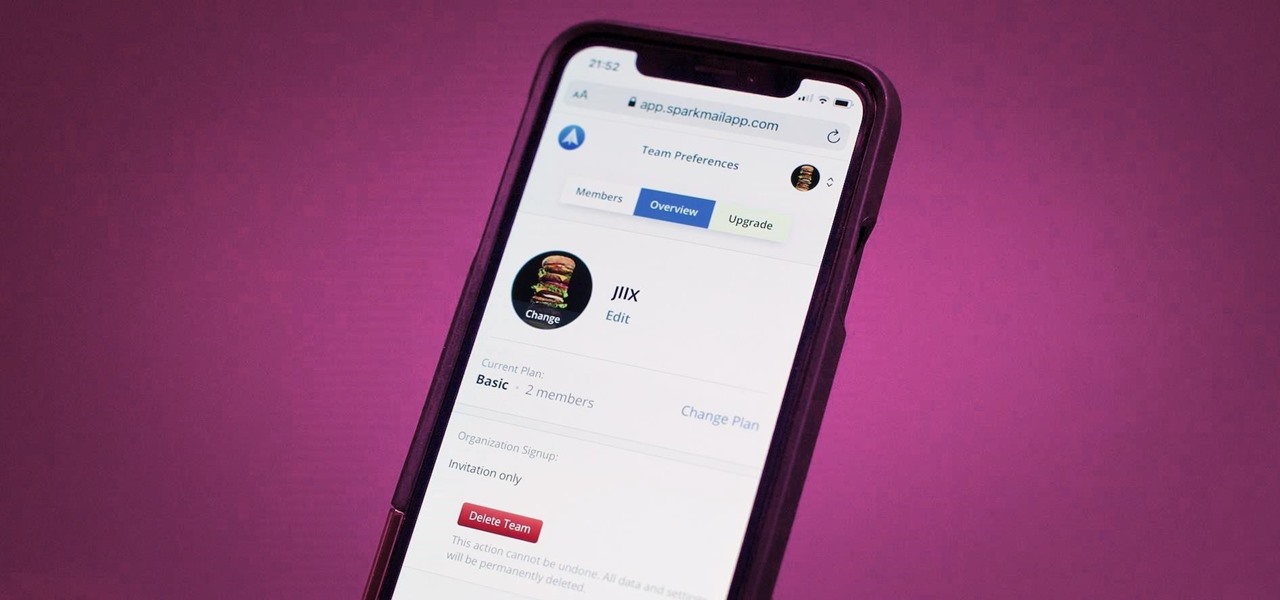
Last year, Readdle released a major update to their popular intelligent email client Spark, which brought a number of new features and improvements, including the ability for team members to collaborate on emails. You can draft new emails and privately discuss existing ones with your team, invite team members into email threads, and create and share links to specific emails.

Apple's Reminders app has never been particularly sexy or appealing, but that changes in iOS 13. Although the productivity tool has always been useful for quick to-dos, it now has an overhauled user interface with several new features, including grouping lists together for improved organization.