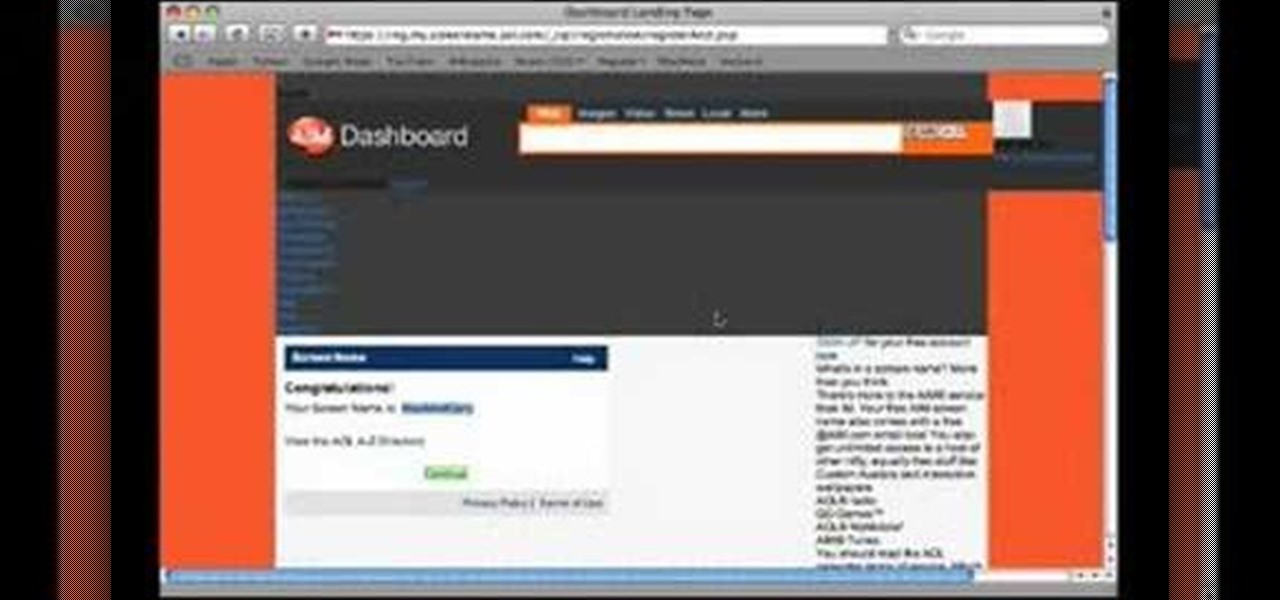
In this tutorial, Gary Rosenzweig of MacMost.com shows you how to sign up for a free AOL Instant Messenger account that you can use with iChat on your Mac. Stay in touch with friends and family while avoiding troublesome cell phone radiation with this how-to.

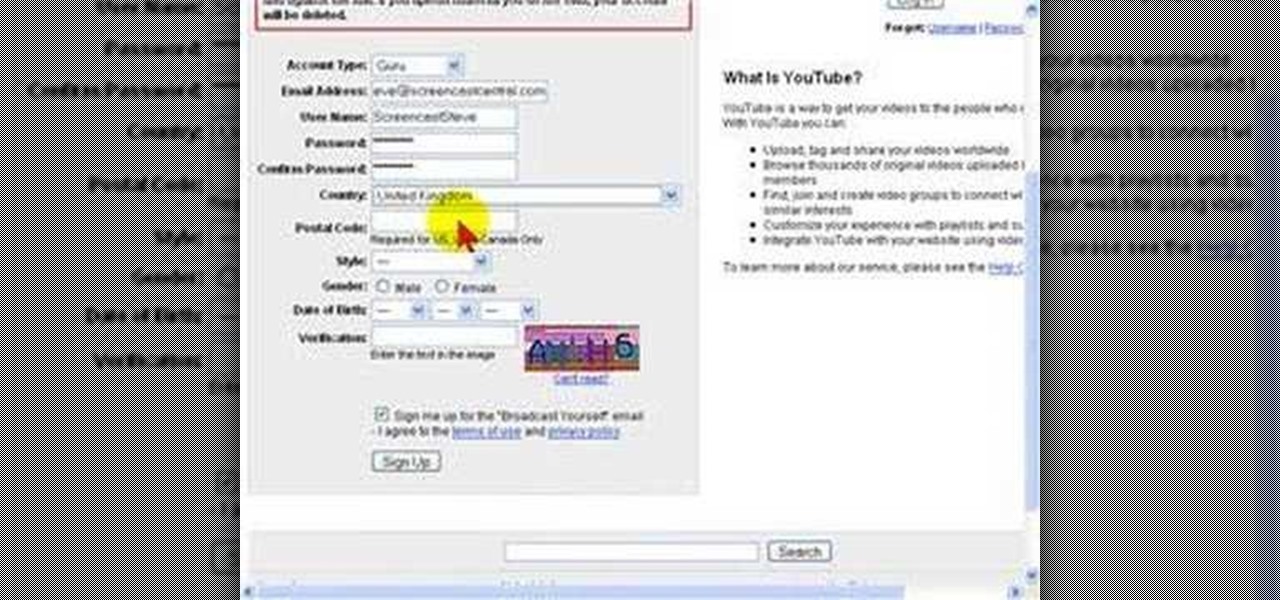
Do you have a video that you want to share with the world? Learn how to sign up for a YouTube account, adjust your account settings, and upload new videos to YouTube.
This will show you how to make an oversea account on the Playstation Network.

How to get a Japanese PSN account to download Japanese games to your PS3.

This tutorial guides you through setting up a default email account using cPanel. This video is provided to you by Scandicsoft.

This is a short tutorial on how to add or delete email accounts using cPanel. This video is provided by Scandicsoft.

YouTube is the latest craze to hit the web, allowing users to upload and distribute their own videos. YouTube now boasts more than 100 Million Video Views per day.

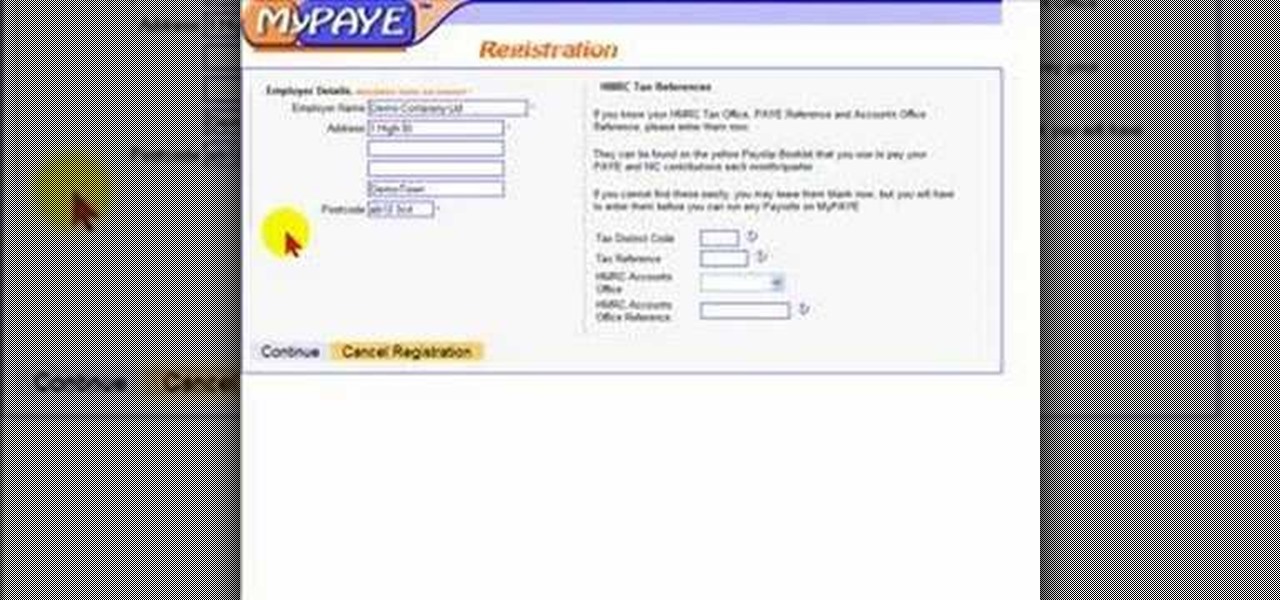
How to set up a new account with MyPAYE an online payroll management service.

How to use the Evolution Setup Assistant to set up your mail account in Ubuntu Linux.

A non-geek tutorial for anyone who wants to take advantage of google's free, web-based e-mail program. This tutorial guides you step by step through the process of how to sign up for and delete a G-Mail account.

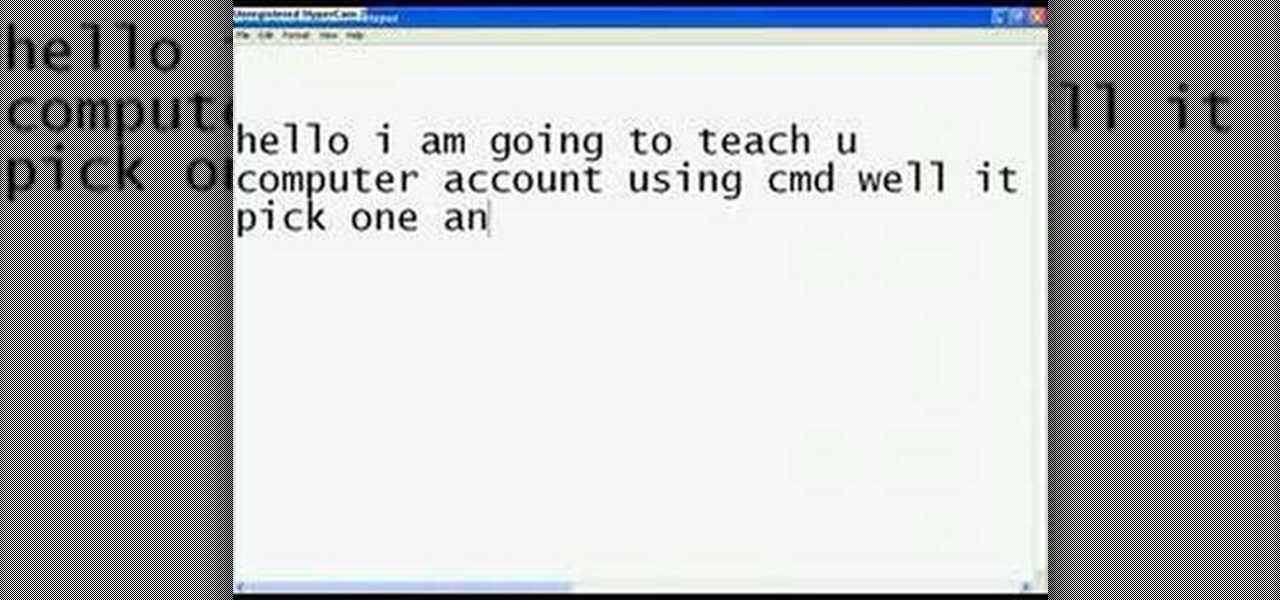
This video teaches you how to change your computer's account password using the DOS command prompt. The first step is to get to the command prompt, you can do this simply by clicking run in the start menu and typing "cmd." You next type "net user" which will show you all of the user accounts on the computer. Choose the one you would like to change the password for and type "net user (account name)." It will then ask you for a new password, you may type anything you like here keeping in mind t...

You can have as many iPhone e-mail accounts as you have addresses. Watch this iPhone tutorial video to learn how to add multiple email accounts to your iPhone. This how-to video is intended for new iPhone owners.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

As the stigma of online dating fades and swiping potential suitors on your phone becomes the new norm, one very real issue that you may have to deal with is catfishing: the act of being deceived by a fictional online persona. Although dating apps do their best to weed out fake accounts, a few of them slip through the cracks and take advantage of innocent people just looking for a connection.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

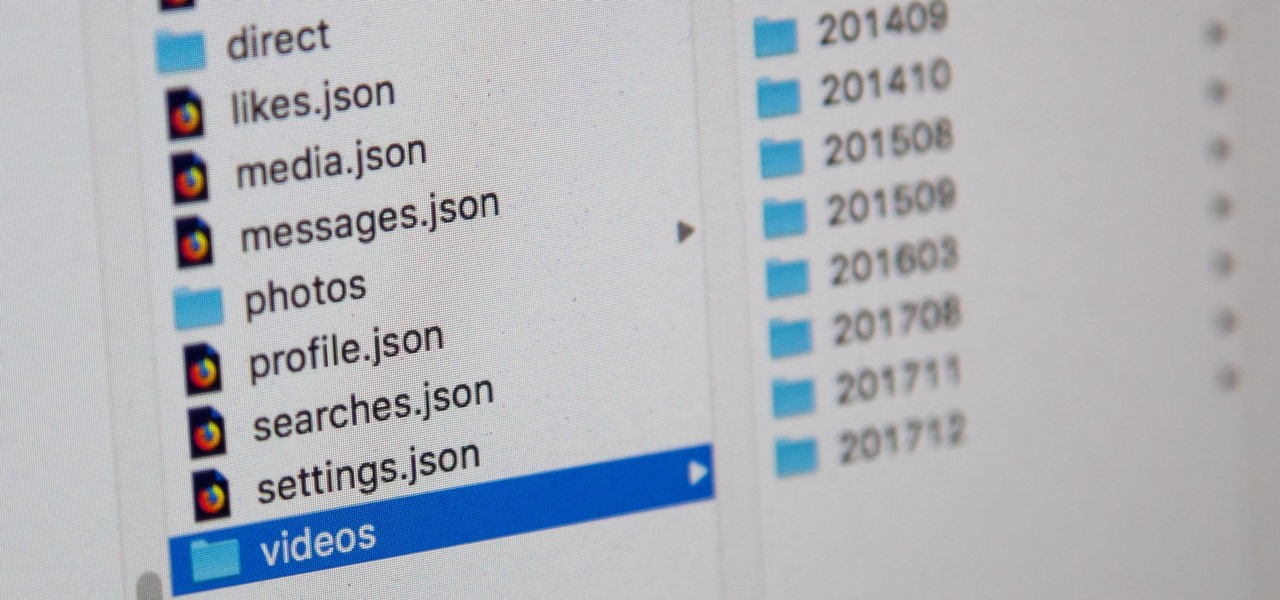
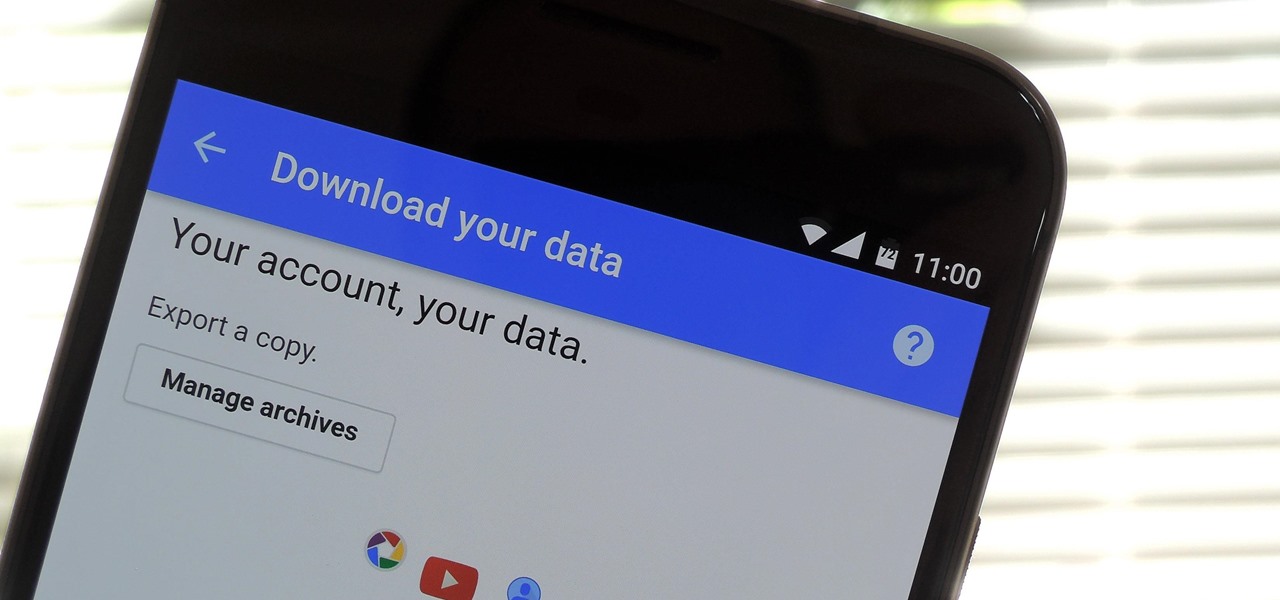
Facebook, parent company of Instagram, has allowed you to download photos and other account data for some time now, but the data request feature is also now available on Instagram to meet the GDPR data portability requirement in the EU — and it's available worldwide, not just in Europe.

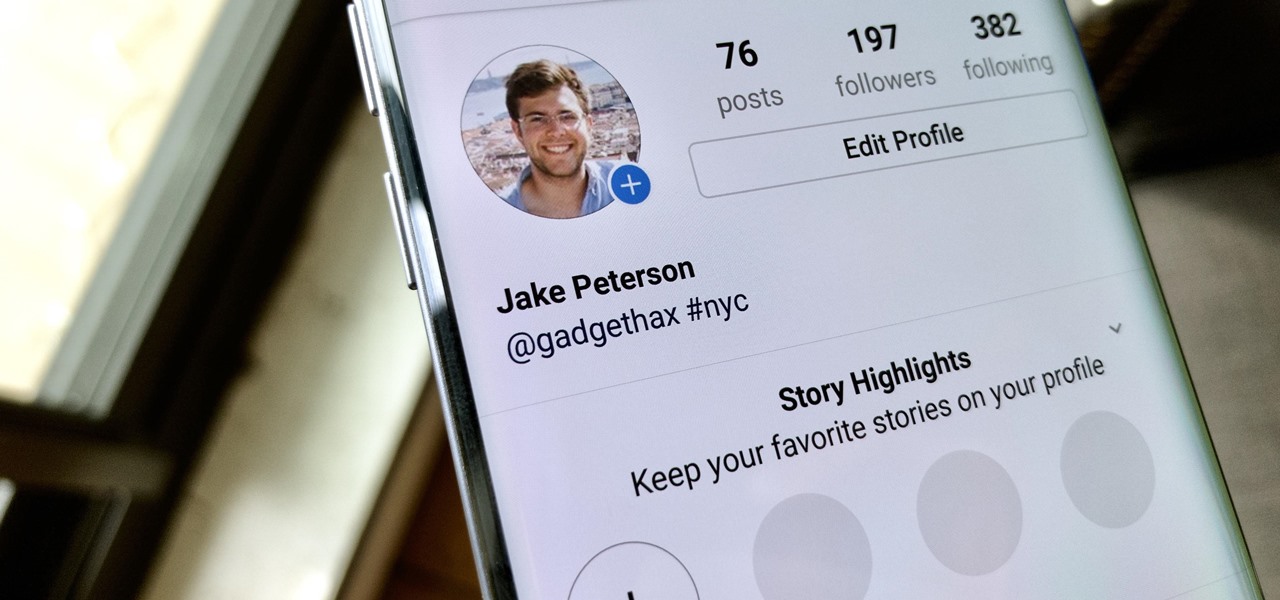
Your Instagram bio could always be used to link to other websites or profiles or just to show off your witty personality. Now, you also have the ability to use this section to tag other Instagram accounts as well as add tappable hashtags. Whether you want to link out to your best friend, company, or the latest trend in your city — if it has a profile name or tag, it can be in your bio.

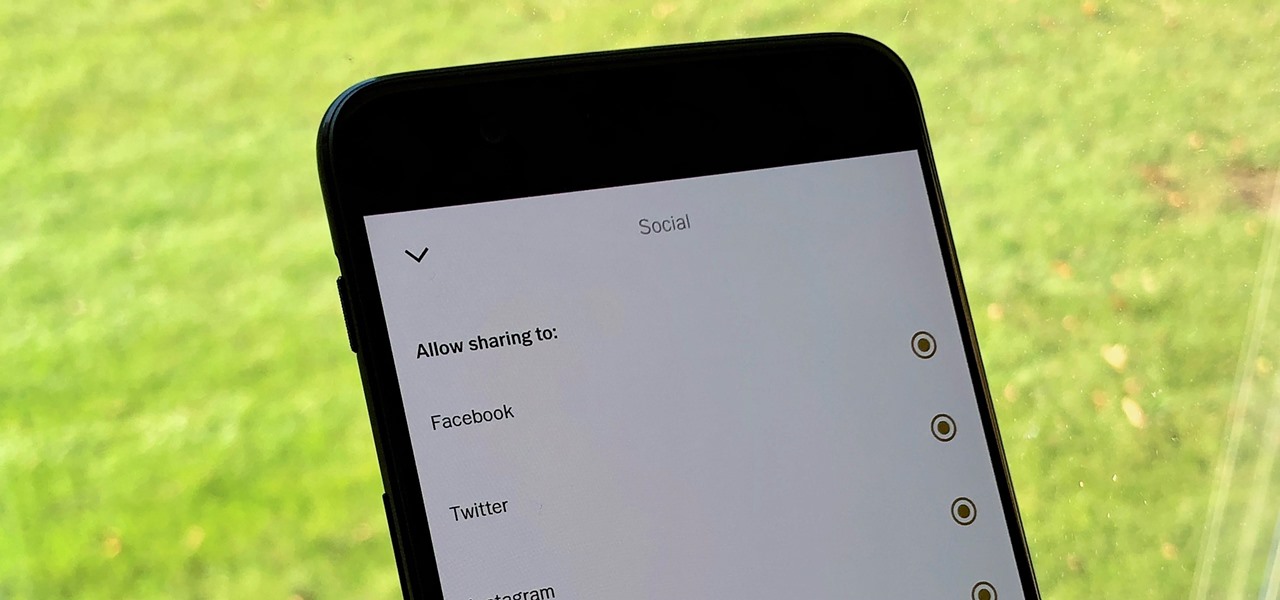
In this day and age, publishing content to one social media account just doesn't cut it. VSCO, Facebook, Twitter, Instagram ... you need to be active on all. And if you prefer editing and posting all of your photos on VSCO, you need a way to share those images with your other accounts.

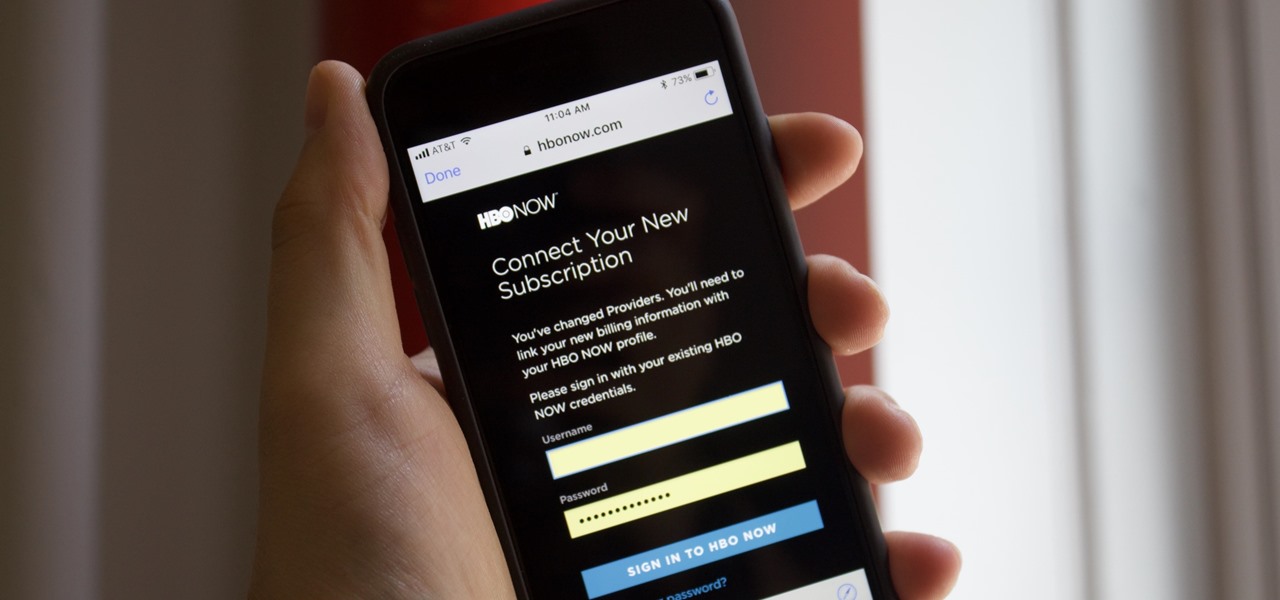
Update: HBO discontinued this service. Your best bet for transferring your data from one account to another is to save a record of your watch list. That way, you can add your titles back manually with your new account.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

If you're an Android user, Google probably has almost your entire digital life stored on its servers. Family pictures are backed up on Google Photos, your e-book library resides with Google Play Books, videos are on YouTube, chat logs in Gmail and Hangouts, starred places and location history in Google Maps, and so much more.

The first time a friend or family member asks if they can borrow your phone or tablet, you probably just hand it over without a second thought. But the second, third, and fourth times? Now it's starting to become a habit, and something probably needs to be done about it.

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

Smartphones generally have limited storage, but counter this issue with an always-on internet connection. This led to the proliferation of cloud storage services, which allow us to store and access our large media libraries remotely.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

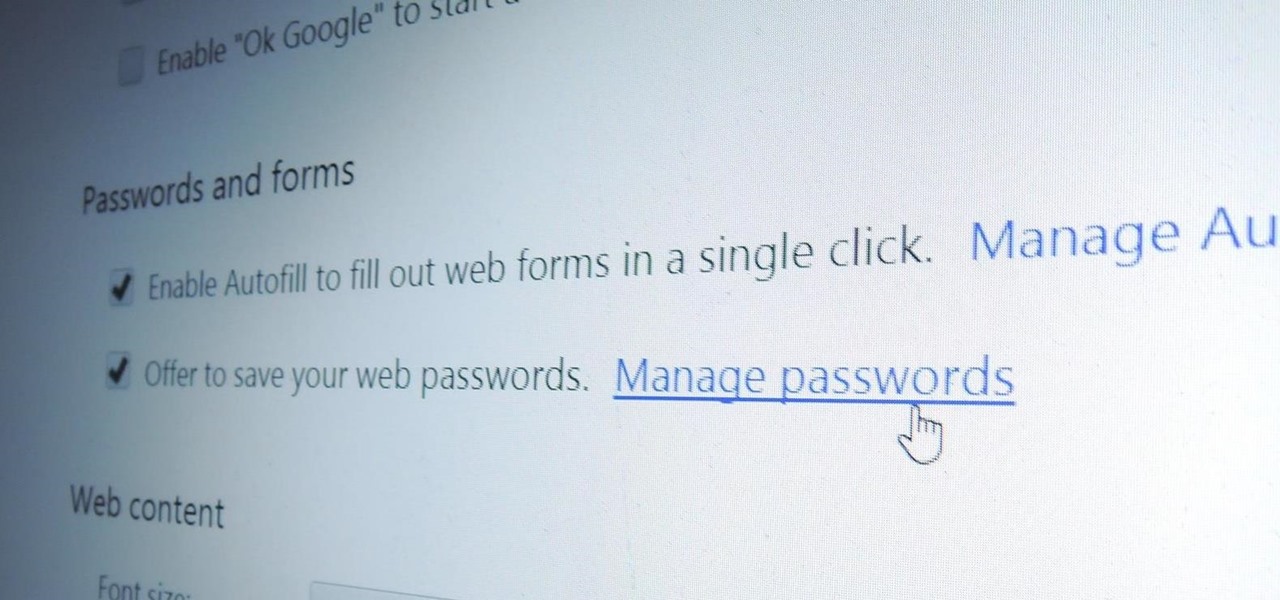
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

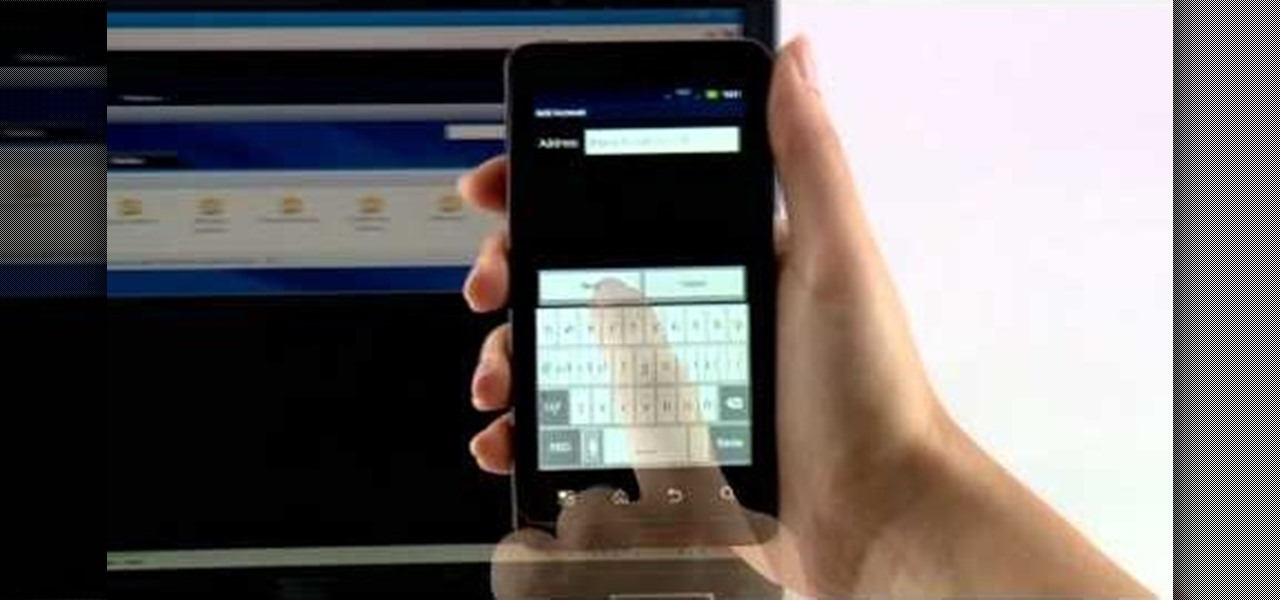
This video will show you how to open multiple Google accounts in one chrome browser. But Google introduced an add-on which will let you do your multiple accounts job at the same time. Watch the video and follow all the steps carefully. Employ the technique in your PC.

This video will show you how to send text SMS from Gmail account. Your mobile number has to register with your Gmail account. The receiver could also respond to your SMS. Watch the video and employ the technique.

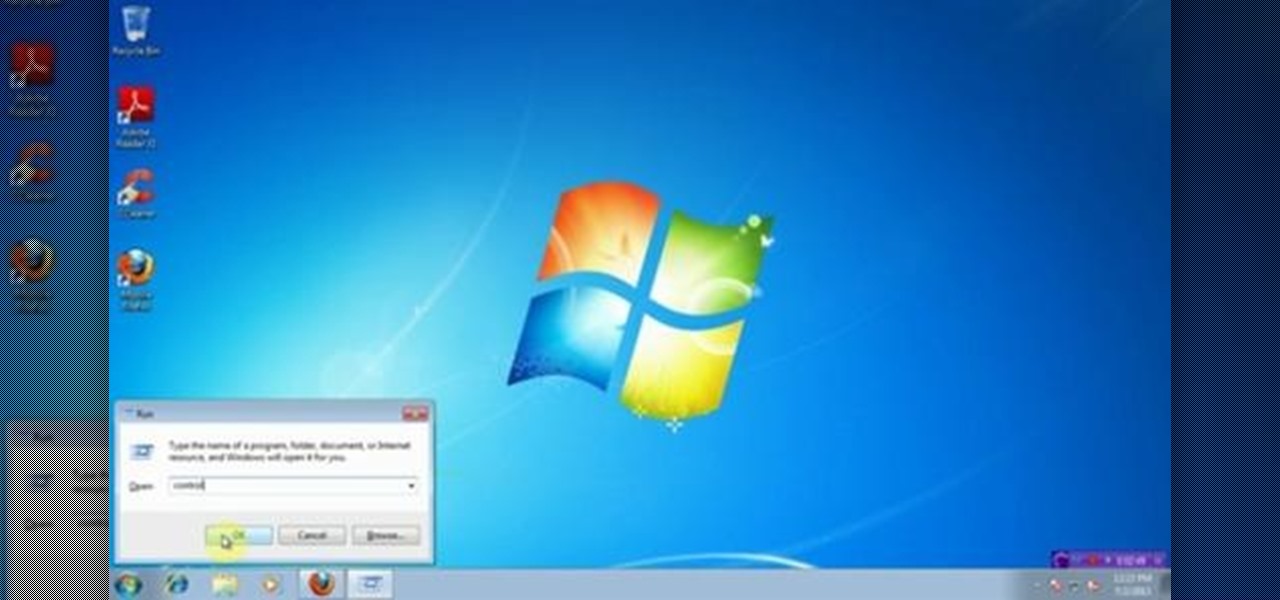
This video will help you how to disable user account in windows 7. This is very easy to employ. Watch the video and follow all the steps to disable user account in your PC.

Snapchat is like that very attractive girl at the bar that has one too many shots and ends up slobbering on the bouncer as she gets led out. Of course she can still recover since she is hot, but you only get so many chances before you just become a complete failure. And that's where Snapchat has been treading these past few weeks.

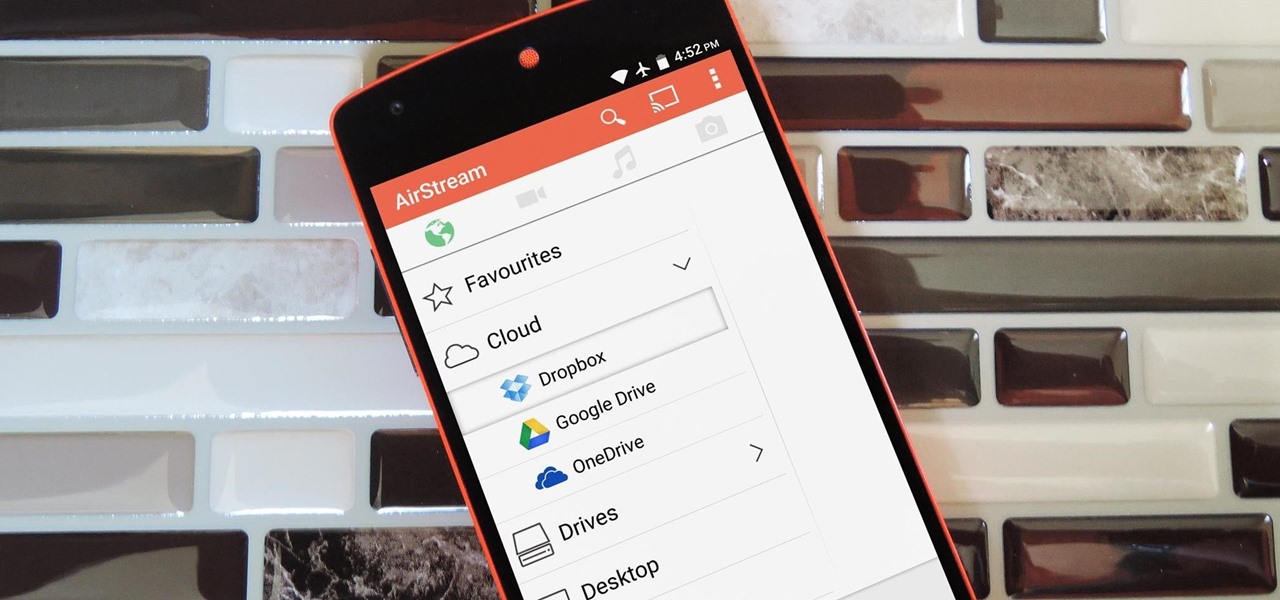
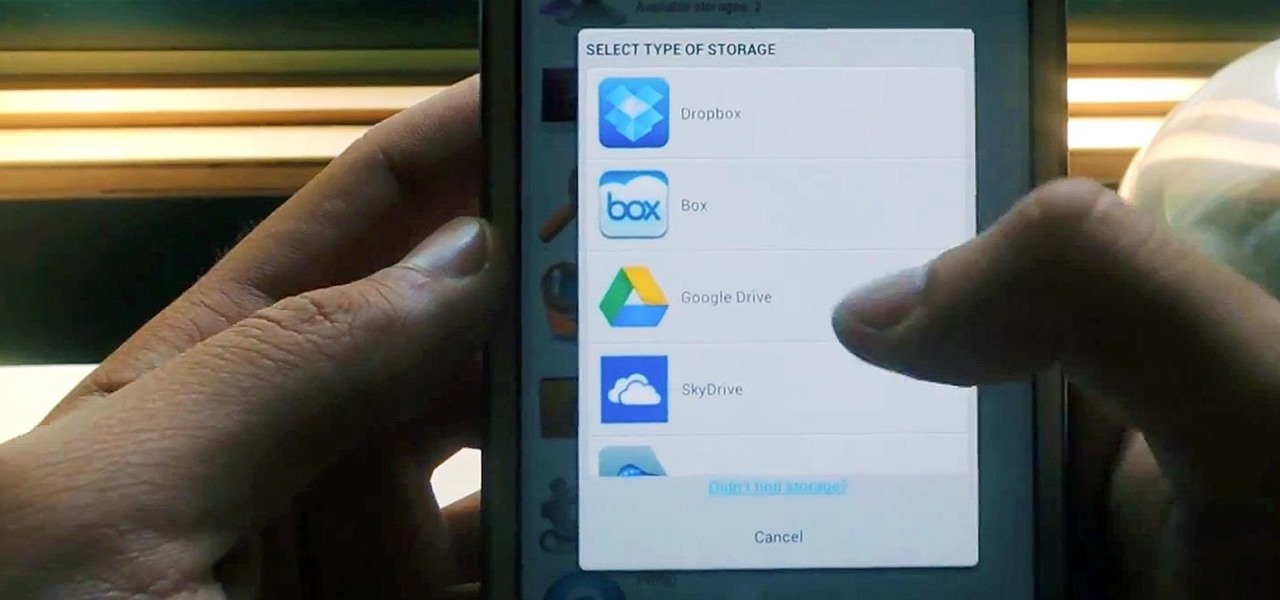
Cloud storage looks pretty good compared to the heavy restrictions that hard drives and other types of external memory carry. The cloud is not only limitless in what it can hold, but it can also easily be accessed from any device that has Internet—your smartphone, work computer, personal laptop, tablet, and more. While accessing a specific cloud storage system like Dropbox or Google Drive may be easy on your Samsung Galaxy Note 2, managing all of them individually can not only get confusing, ...

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

The Citrix Receiver is an app that allows you to securely access your desktop and business applications directly from your Droid Bionic smartphone. You will first need to make an account at the Citrix site, and from there you can decide what you want to have access to on your phone. On the Android app launcher, be sure to pick the Citrix Receiver app so that you can login with your Citrix account.

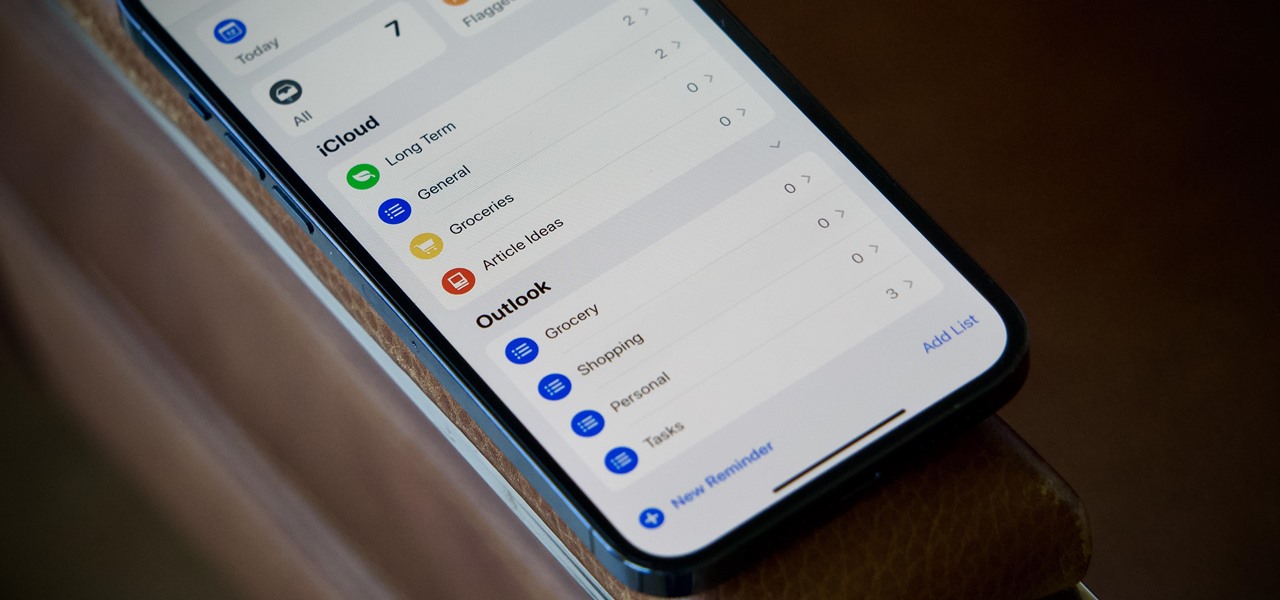
Apple's iCloud is a fantastic way to ensure that all of your photos, messages, notes, and other important data are backed up and appear on all of your connected devices. However, you may have information like reminders attached to accounts other than iCloud, which won't appear when signing into iCloud on a new device. Here's how to get the full picture of where your reminders are stored.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.