The ball weave is great for the core. This exercise looks flashy, but in reality, your abs are in a static position the whole time. There is very little movement in the midsection. The ball weave is easy perform, but it does require some coordination.

Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSite, basic mission 5. This mission focused on JavaScript, again. This time there is a little bit more security in place.

PayPal has, all in all, been great for allowing Web 2.0 economy to grow. For most entities, it's the best way to send money between two people on the internet.

These days, I keep multiple browsers open so I can keep track of all my work and personal items. As a staff member of WonderHowTo, a lot of my work is done through our Google Account, which is separate from my personal Google Account.

Introduction In this post we will look at how to access a PosgreSQL database in your C/C++ application. It's not as hard as you might think, but you need to understand the procedure and the functions used.

After his fall from Asgard into space, the Asgardian Loki meets the Other, the leader of a warmongering alien race known as the Chitauri. In exchange for retrieving the Tesseract,2 a powerful energy source of unknown potential, the Other promises Loki a Chitauri army with which he can subjugate the Earth. Nick Fury, director of the espionage agency S.H.I.E.L.D., arrives at a remote research facility during an evacuation. Physicist Dr. Erik Selvig is leading a research team experimenting on th...

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

Last week, we discussed whether Google should require you to use your real name for Google+ profiles. Google is working on eliminating fake profiles, and in the process, they've booted some real people, including actor +William Shatner. If you find out that your Google+ account has been suspended, you can appeal the suspension and get your profile reinstated.

Always falling asleep behind the wheel? The National Highway Traffic Safety Administration (NHTSA) estimates that there are over 56,000 sleep-related accidents each year, resulting in 40,000 injuries and 1,550 deaths annually in the United States. Don't want to be a statistic? Then you may want to try out ASP Technology's mobile application which aims to keep you awake when you're fatigued on the road.

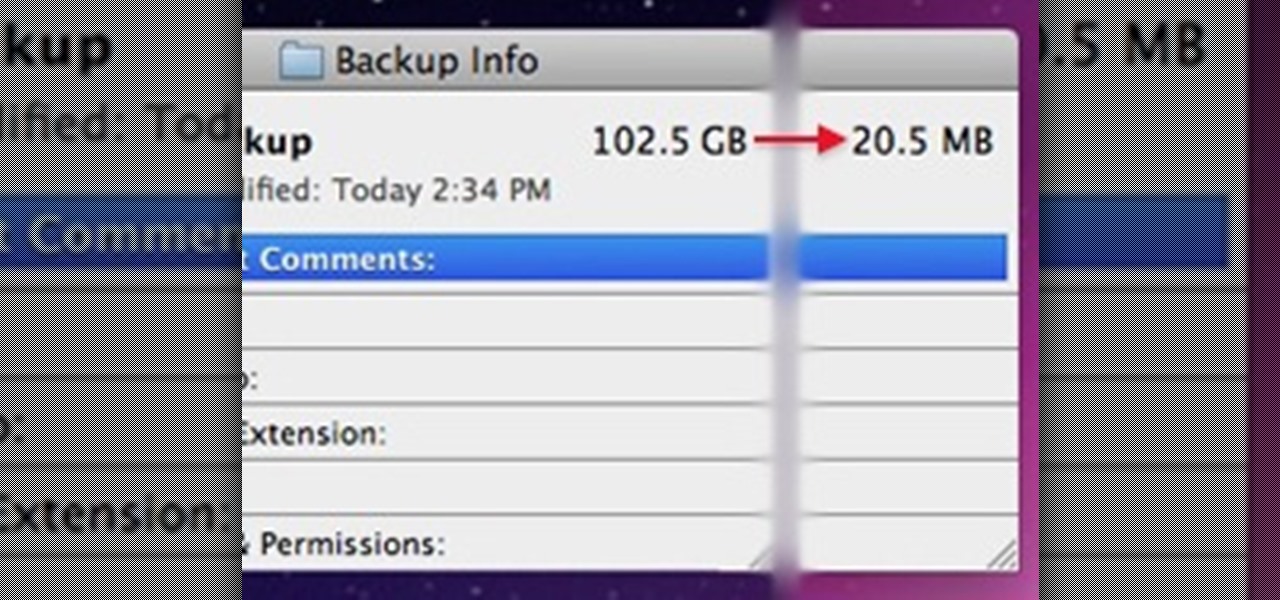
By now, you probably know that your iPhone secretly tracks and stores the locations you've visited in a backup folder on your computer's hard drive. The files are unencrypted, which means anyone with access to your computer or device can retrieve the information, which is downright scary. But Pete Warden and Alasdair Allan are making it fun with their iPhone Tracker application, which lets you map out everywhere you've been with your smartphone.

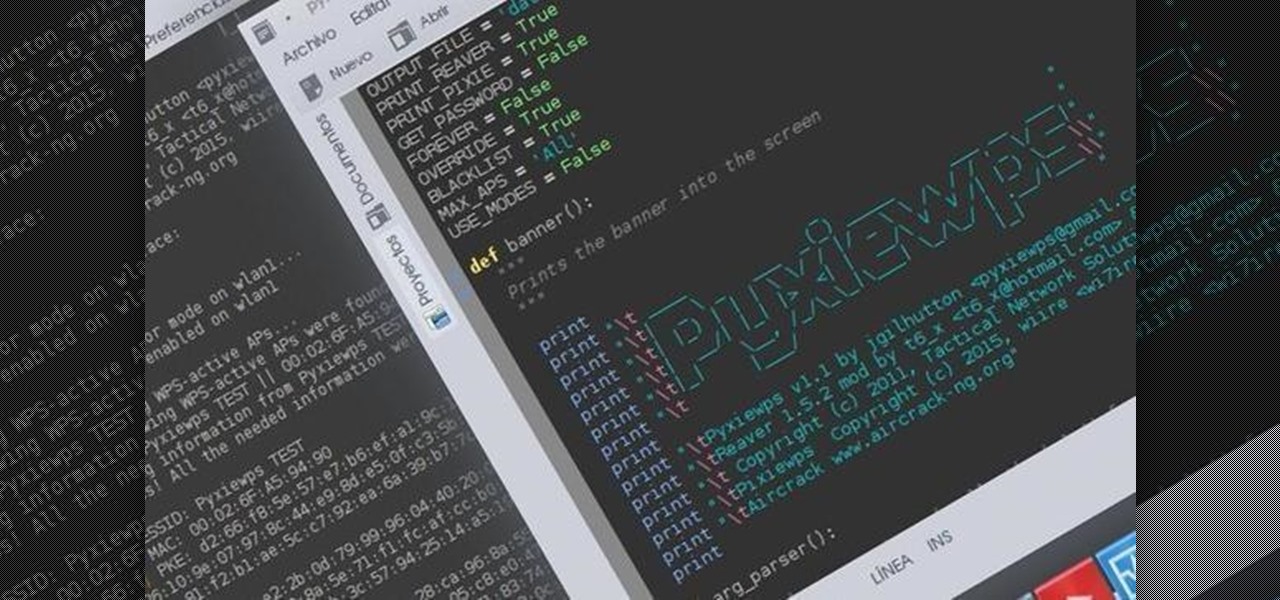
Helo my dear friends! A few days ago, I shared with this community my wrapper-script (a wrapper is a program that joins other programs that do the real job) to automatize the attacks on Pixie-Dust vulnerable routers. I was recieving complains from non-Kali users that had problems trying to launch the program, so I decided to make a good installer so anybody can use it in any DEB based distro.

Google+ is nearly complete. We've got hangouts, pages, photos, games, and lots of ways to share what we love and build an audience. But it seems like Google isn't quite done yet. Since most of Google+ has been "shipped", it's now time to "ship the Google" as +Larry Page mentioned in the quarterly report.

This week, Google held back on introducing a slew of new Google+ features, and introduced new Chrome extensions instead. The new additions won't replace of your favorite Chrome extensions, but they are very useful, and elegant.

You can make homemade pizza with a minimum of tools, or you can buy the entire yuppie menagerie (and let's face it—if you're a foodie, you probably want the toys). Below is a brief rundown of the different options available. Since I'm a relative beginner to the process, I've also linked out to a few in-depth reviews.

In many of my articles, I will refer to applications designed to empower Mac users to automate various tasks on their computer. One such application is called Hazel. Like smart folders, smart playlists, and smart albums found in Mac OS X and iPhoto, Hazel can automate the task of moving, copying, or deleting files in folders on your Mac. I recommend Hazel as one of the most essential applications for any Mac user. Let's explore how it works.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

My JO was watching The Simpsons on FOX the other day, like she wholeheartedly does every evening, and I joined her, much like I always do— though I must admit, I'm not as obsessed with the cartoon family as much as she is. Just like she isn't as obsessed with SCRABBLE as I am.

You can't catch a fish if you don't have the bait… and a buzz bait are great for snagging bass. So, if you're a bass fisherman, you can't not know this information. Get the scoop on buzz baits.

Large, sweaty men are usually the first thing that comes to mind when you hear the word football, but for this video, we're not talking about the guys on the playing field, we're talking about the guys in the fishing boat, the kind of guys who like to use a "football jig".

First Prank: Title: Bull-ish Thugs

What's a jig worm? Well, it's exactly what the name implies: a jig rigged with a trailing plastic worm. If you're not a seasoned fisherman, the answer might not have been so obvious, but that doesn't matter when you find out how important this jig worm is. Wade Bourne of MyOutdoorTV shows you how to fish a jig worm.

In these auto lockout emergency videos, learn what to do when you've locked your keys in the car—aside from calling a locksmith. See how to use special tools, usually readily available to the public, to unlock your car free of charge.