There’s nothing like a great horror movie to really get the adrenaline pumping during the Halloween season. I don't know about you, but the sight of blood dripping into a pool of even more blood creeps me out, so you can imagine my reaction to harrowing creatures that go bump in the night and rip people's faces off. It's intense, but I love it.

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

What if your fridge knew your food and expiration dates? What if your fridge could tell you which ingredients are missing and where you can get them the cheapest?

This Null Byte is a doozey.

Last week, we discussed whether Google should require you to use your real name for Google+ profiles. Google is working on eliminating fake profiles, and in the process, they've booted some real people, including actor +William Shatner. If you find out that your Google+ account has been suspended, you can appeal the suspension and get your profile reinstated.

Always falling asleep behind the wheel? The National Highway Traffic Safety Administration (NHTSA) estimates that there are over 56,000 sleep-related accidents each year, resulting in 40,000 injuries and 1,550 deaths annually in the United States. Don't want to be a statistic? Then you may want to try out ASP Technology's mobile application which aims to keep you awake when you're fatigued on the road.

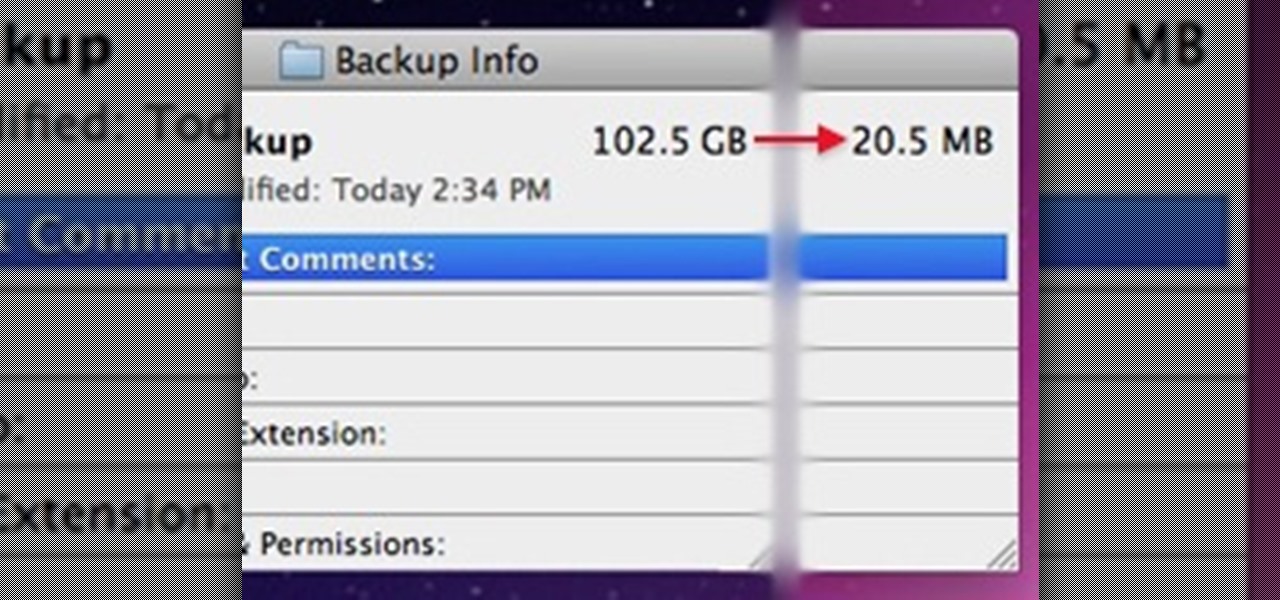
By now, you probably know that your iPhone secretly tracks and stores the locations you've visited in a backup folder on your computer's hard drive. The files are unencrypted, which means anyone with access to your computer or device can retrieve the information, which is downright scary. But Pete Warden and Alasdair Allan are making it fun with their iPhone Tracker application, which lets you map out everywhere you've been with your smartphone.

The Jackass crew are now jewelers. In this idea, you would have to get 8 jewels or stones or medallions, gumball size, and a very thick gaudy gold chain. The chain would be divided into 8 parts and cut. All at once, the Jackass guys would each swallow the jewel and their segment of the chain. In a day or so, or sooner with the help of laxatives, each guy would poop out the stone and the piece of the chain. As soon as all of the parts and pieces have been recovered from each guys poop, the cha...

Facebook's new Timeline feature has been rolling out gradually since its unveiling in September, but yesterday it finally became available to Facebookers everywhere. It's even available on your mobile device, too. Those who want to upgrade to the radical new profile design can do so by simple logging into their Facebook account and visiting the About Timeline page on Facebook.

Torus knots are beautiful knots formed by wrapping a line around a torus and tying the ends together to form a loop. The resulting knot has a star-like appearance when viewed from above. The 36 examples with the least number of crossings can be seen at the Knot Atlas's page on torus knots.

First Prank: Title: Bull-ish Thugs

I remember a time when I had to rent a VHS from the local video rental store. It wasn't all that bad, with the only real annoyances being the trip to and fro, having to rewind the movie and the possible malfunction of my VHS player, which liked to eat tape from time to time.

Google+ is nearly complete. We've got hangouts, pages, photos, games, and lots of ways to share what we love and build an audience. But it seems like Google isn't quite done yet. Since most of Google+ has been "shipped", it's now time to "ship the Google" as +Larry Page mentioned in the quarterly report.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

This week, Google held back on introducing a slew of new Google+ features, and introduced new Chrome extensions instead. The new additions won't replace of your favorite Chrome extensions, but they are very useful, and elegant.

You can make homemade pizza with a minimum of tools, or you can buy the entire yuppie menagerie (and let's face it—if you're a foodie, you probably want the toys). Below is a brief rundown of the different options available. Since I'm a relative beginner to the process, I've also linked out to a few in-depth reviews.

Time is running out. Christmas is almost here, and you still haven't worked your way through that holiday shopping list yet. But don't worry, there's hope yet— thanks to social buying websites like Groupon, LivingSocial, SocialBuy, Eversave, Tippr and BuyWithMe.

Large, sweaty men are usually the first thing that comes to mind when you hear the word football, but for this video, we're not talking about the guys on the playing field, we're talking about the guys in the fishing boat, the kind of guys who like to use a "football jig".

What's a jig worm? Well, it's exactly what the name implies: a jig rigged with a trailing plastic worm. If you're not a seasoned fisherman, the answer might not have been so obvious, but that doesn't matter when you find out how important this jig worm is. Wade Bourne of MyOutdoorTV shows you how to fish a jig worm.

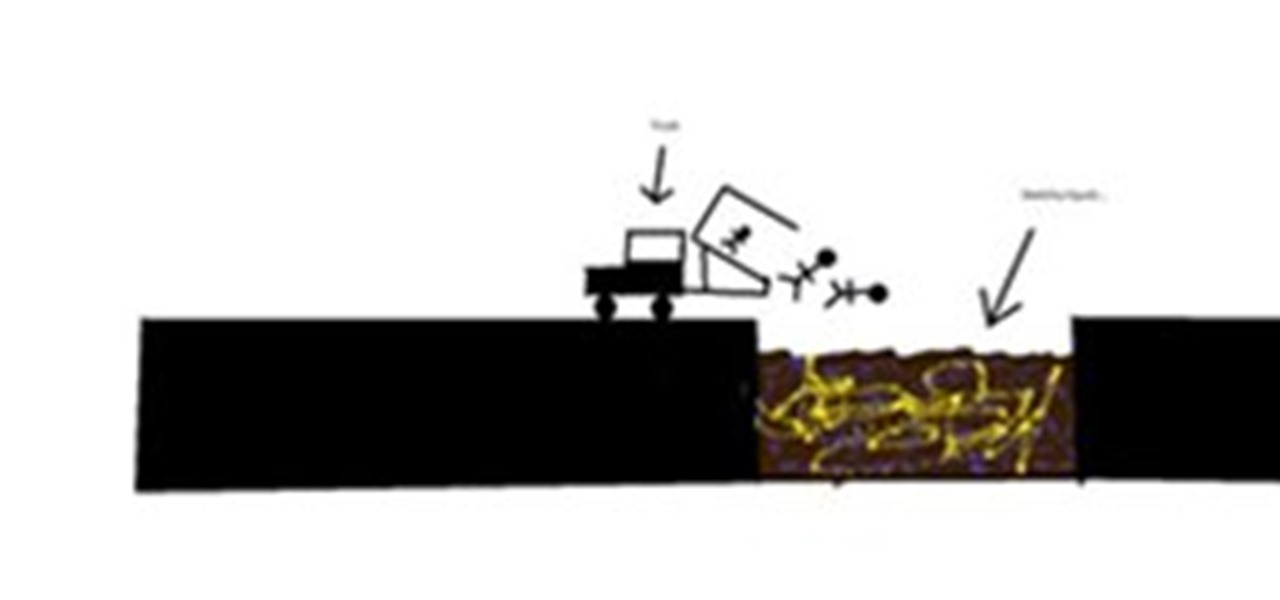
- Prank either 3 to 5 members of the jackass crew. (any members) - Tell them there was a poll on mtv.com asking for people to vote on which stunt they want to see revisited the most. Making Roller Derby In a Truck (from the first jackass movie) the winner. Only this time they have to do it in only thong like speedo's or completely naked (whatever you can get away with for tv.)

It's been a long journey for Netflix users. At first, it was a rough ride as Netflix struggled to find its place in the homes and hearts of movie watchers everywhere. Once monthly subscriptions bumped off the pay-per-rental charges, Netflix soared to great heights, known for their flat-fee unlimited rentals without due dates, late fees, or shipping and handling fees. And it was smooth sailing when streaming services were incorporated into monthly plans, with customers being able to rent DVDs ...

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

Health, safety and security are three main issues which determine if your cruise is a successful vacation.

Fire. It’s everywhere— always has been. From the Ordovician Period where the first fossil record of fire appears to the present day everyday uses of the Holocene. Today, we abundantly create flames (intentionally or unintentionally) in power plants, extractive metallurgy, incendiary bombs, combustion engines, controlled burns, wildfires, fireplaces, campfires, grills, candles, gas stoves and ovens, matches, cigarettes, and the list goes on... Yet with our societies' prodigal use of fire, t...

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

My JO was watching The Simpsons on FOX the other day, like she wholeheartedly does every evening, and I joined her, much like I always do— though I must admit, I'm not as obsessed with the cartoon family as much as she is. Just like she isn't as obsessed with SCRABBLE as I am.