
Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.
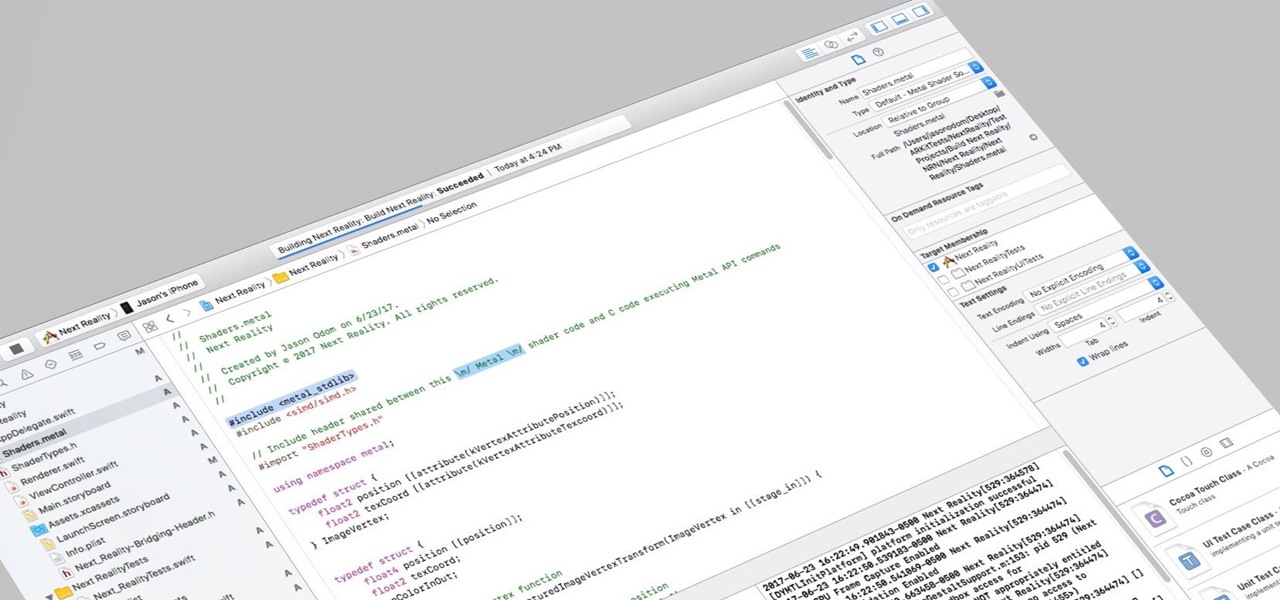
I currently am and have always been what one might call a PC/Android guy. Many that know me well would likely even go so far as to say I am anti-Apple. About an hour after seeing the ARKit demo during the day-one keynote at WWDC, I became the owner of a brand new Mac.

While Lyme disease can be disabling, the wrong treatment for the infection can be fatal.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Mixed reality display manufacturer Realfiction has developed a 64-inch display capable of delivering 3D holograms without a headset.

Water makes up about 60% of your body weight. Whether you like it plain, flavored, bubbly, or in beverages or food, we all need water daily to avoid dehydration and stay healthy. For communities in need of clean drinking water, new research using bacteria may offer a simplified, lower-cost method for boosting potable water supplies.

The evolution of our infection-fighting systems may have something to teach modern scientists. That's what a group from the University of Granada in Spain found when they studied a protein that's been around for over four billion years. Their work, by senior author José Sánchez-Ruiz and colleagues in the Department of Physical Chemistry, was published in the journal Cell Reports.

Pertussis, or whooping cough, is a highly contagious disease that can be life-threatening for young children. New research backs a recommendation that all pregnant women receive a pertussis booster with each pregnancy, as it can help their infants fight off the infection.

Termite poop and biofuels — what's the connection? New research into termites' intestinal comings and goings describes a process that may speed the development and lower the cost of fuels made from plant matter.

The ability of one microbe to adapt is giving it a whole new career as a sexually transmitted disease. Usually content with the back of the throat and nose of those who carry it, the dangerous pathogen Neisseria meningitidis has adapted to cause an illness that looks a lot like gonorrhea.

On October 17, 1943, a story in the New York Herald Tribune read "Many laymen — husbands, wives, parents, brothers, sisters, friends — beg Dr. Keefer for penicillin," according to the American Chemical Society. Dr. Chester Keefer of Boston was responsible for rationing the new miracle drug, penicillin.

Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

An advance in the race to stop birth defects caused by Zika-infected mothers has been made by a team of researchers from Rensselaer Polytechnic Institute in Troy, New York. They have identified the process Zika uses to gain entry into the placenta, and published their findings in the journal Biochemistry.

Most females have had at least one urinary tract infection in their lifetimes. Recurrent UTIs are particularly problematic in young, sexually active women, where about 80% of the infections are caused by the bacteria Escherichia coli, better known as E. coli.

Phase 2 of a Zika vaccine trial began in the United States this week, along with Central and South America.

There could be a fresh outbreak of the Zika virus in the Americas as the weather heats up and the mosquito population blooms.

The Great Barrier Reef in Australia is the largest living system on the planet. Yet more than 90% of the reef is bleaching because of the loss of a tiny algae that lives within the coral.

Cholera is rapidly spreading in Mozambique, with over 1,200 people infected. Since the outset of 2017, cholera has spread from the capital city of Maputo (pictured above) to three of its ten provinces. Health officials report other areas in the country are seeing case counts rise, and two deaths have been logged so far.

Arsenic occurs naturally in the environment, but it is also one of the most commonly found heavy metals in wastewater, deposited there by inappropriate disposal and arsenical pesticides, for example.

Even as health authorities describe the symptoms of Zika infection in the general population as mild, a new surveillance study finds serious side effects are more common, and serious, than previously thought.

A rose by any other name may smell as sweet, but one annoying invasive weed may hold the answer to treating the superbug MRSA. Researchers from Emory University have found that the red berries of the Brazilian peppertree contain a compound that turns off a gene vital to the drug-resistance process.

Have the sniffles? Yes. Does your head hurt? Yes. Coughing? Yes. Could you have influenza? Yes. How do you know the difference? With these symptoms, you could also have a cold.

It hasn't even been eight years since Candida auris was discovered—cultured and identified from the ear canal of a patient in Japan—and now it's drug-resistant, setting up residence in hospitals, killing patients, and wreaking havoc across the globe.

Specialized cells in the lining of the gut may provide a key to preventing an infectious brain disease caused by misfolded proteins.

You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

One of the only downsides to the Pixel XL is that Google's flagship phone does not have stereo speakers. But if Android's awesome development community has taught us anything over the years, it's that limitations like these can be bypassed with some creative software tinkering.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

Samsung's Note series is directly responsible for some of the biggest innovations in smartphones. As the first "phablet," it sparked the current craze for bigger screens, and the S Pen stylus has been mimicked numerous times. Even the curved display made famous by the Galaxy S6 edge made its debut on the Note 4, so this is the one smartphone line you want to keep track of if you like to stay on the bleeding edge.

Hello Guys, Today I have made a script for ddosing sites with VBScript! And I don't know how you guys do it, but I've made a script that refreshes the page in a chosen amout of milliseconds. And if you want it a number of times or if you want it to go on and on. And this is a script to run it on your botnet. But again I don't know if this works on your botnet too.

In many places, May has given way to a surplus of strawberries cluttering the produce aisle. These sweet berries are great in a wide variety of delicious baked goods, from pies to cakes and everything in between.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Virtual reality is all the rage these days, especially with devices like the Oculus Rift, Gear VR, and HTC Vive hitting shelves lately. But before any of those fancy, expensive headsets ever made it to the market, Google came up with a thrifty and inventive substitute in the form of Google Cardboard.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

There are few things more annoying in life than getting interrupted—especially when you're in a groove, jamming out to your favorite song. If we can all agree on that sentiment, then why is it that our phones mute the music we're listening to for a few seconds whenever a notification comes in?

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

After months of speculation and sifting through rumors, Samsung finally unveiled its Galaxy S7 and S7 edge flagships, and they're pretty much what we had been anticipating. But just because there weren't any major surprises doesn't mean that it's not still exciting. Let's have a look.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Most home bakers rely on vanilla extract as a flavor component to their cakes and cookies, but little do they know what they are missing until they trade in their extract for whole vanilla beans. The rich complexity and different notes of flavor of a true vanilla bean are often washed out and distilled into a one-note sweetness, especially if the extract is cheap or imitation. If you want to get more serious about baking, you need to get serious about using vanilla beans.







































