If you're having trouble with the Act 1 quest 'Act of Mercy' in Dragon Age 2, or just want to bask in watching a really good gamer discuss his craft while he pwns, watch this video walkthrough, watch this series of three videos and take them to heart.

'Enemies Among Us' is one of the longest, most involved quest in Dragon Age 2, and this walkthrough of it spans a whopping five videos. Stick with it, it's really goods stuff and great viewing even if you aren't stuck on this quest.

This video shows you how to perform the Bandaram trick. Things you'll need: deck of playing cards, elastic band. Select a card and show it to the spectators. Ace of Spades is chosen as the selected card. Return this card back to the deck. Do a table cut trick of the deck so that this selected card is brought to the top of the deck. After the selected card is placed at the top of the deck give it a few shuffles and cut but keep it on the top only. Do a double turnover so that another card come...

Everybody loves burgers and everybody loves sandwiches - so why not combine them? In this tutorial, Betty makes square shaped sandwich burgers from scratch. This recipe is not difficult to make and is incredibly tasty. But, make sure you remember the napkins because this dish sure is messy!

You can never have too much mac & cheese! In addition to her fabulous creamy stovetop recipe, Betty unveils her fabulously gooey baked recipe in this tutorial. This dish has a delicious sharp cheddar bite to it and a crispy crustiness that is to die for! Impress your friends with this very easy and very tasty recipe.

Maybe you get bored with plain old mac & cheese once in a while. Why not spice it up with a bit of an Italian flair? Betty adds a hint of tomato to your traditional family dish; try it out! You won't be disappointed.

Master your tennis serve: the kick serve. Be sure to click on all the video chapters to view the entire tutorial.

Curious about the basics of metal inert gas welding? Watch this instructional welding video for some vital safety tips. A shielding gas tank contains 3,000 psi of pressure, so keep your welding equipment safe distance from your high pressure tanks. To run a bead, you need to set your wire feed speed and your voltage in order to begin welding with an average angle iron. This video provides all of the preliminary steps to running a short bead.

Learn how to do downhill ski series exercises. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do alternate dumbbell swims and dumbbell cross punches. Presented by Real Jock Gay Fitness Health & Life.

Here's a fun glitch you can take advantage of in Dragon Age: Origins to get some extra experience for your whole party. Buy some elfroot from the merchant in the Brecilian Forest, put it in your box at the camp, and then return to the Brecilian Forest!

Varmints can sometimes show up during your FrontierVille game and threaten your crop production. You'll have to clobber them, which can get you food and money but costs energy. Here's a few tips to clobber varmints and protect your farm!

Have you zoomed way in to read a poorly-made webpage in the browser on your Mac and left yourself with no idea how to return the page to normal size? This video will tell you that all you need to do is hit Apple-0 and you're set.

Dark nail polish makes a great fashion statement. However, when it comes time to switch outfits and remove the nail polish, the aftermath can be less than stellar. Removing dark nail polish may leave your nails looking yellow and unhealthy. Watch this video to learn how to treat nail discoloration. Return your hands to their beautiful original state.

See how to make a paper gun -- this video tutorial will show you how to make an auto bolt for a paper gun. It's not that hard to make your own paper gun, so why not try and improve it with this automatic bolt? This means the bolt will return to its original place when released. You will need a rubber band, tape, scissors, and paper.

This make-ahead of time entrée is elegant enough for entertaining, but it's also a wonderful way to dress up an everyday dinner by simply spreading herbed cream cheese over puff pastry, folding it around seared chicken and baking it until golden. Holiday Kitchen shows you this tasty dinner recipe for Herbed Chicken in Pastry. Try it out!

During the holidays, nothing beats the satisfying taste of Brie cheese encrusted in puff pastry. Holiday Kitchen shows you how it's done with this Brie en Croûte recipe that's a must-serve appetizing classic any time of year. To spice up the classic French treat, they've added cranberries, apricots and almonds, dressing it up especially for the holidays

Nothing beats an appetizer packed with healthy spinach and delightful cheeses. It's the perfect party snack, and in this video, you'll learn the recipe for Spinach & Cheese Swirls from Holiday Kitchen. These spinach and cheese appetizers are made with puff pastry, and look so good, your friends will think you're hiding the caterer!

Enjoy the sweet and satisfying taste of pears mixed with walnuts in a dessert designed (unintentionally) by Stéphanie Tatin. Her accidental classic, Tarte Tatin is revitalized with this Holiday Kitchen upside-down cake recipe, where pears take the place of apples, and puff pastry makes all of the kitchen work easier! You can't pass this dessert up!

This recipe from Holiday Kitchen shows you their impressive, celebratory dish that satisfies the most discriminating crowd. Beef Wellington will leave your party guests grinning and wide-eyed as you present and carve this spectacular meal at the table. This masterpiece of meat is worth the effort! But don't worry— there's no foie gras here.

Celebrate the goodness of old-fashioned candied apples with this Holiday Kitchen recipe, where you'll learn how to make Puff-Wrapped Caramel Apples, the perfect dessert-style appetizers for any holiday party. These puff pastry snacks are a presentation worthy of a dinner party dessert, with a cinnamon apple flavor!

Add a healthy twist to your puff pastries and make an elegant appetizer perfect for any party. It's not quite a dessert, but it still taste like one, with cherry tomatoes being the key ingredient. This recipe from Holiday Kitchen will show you how to make these wonderful little Tomato Jewels, a yummy and appetizing little gem.

Fish & chips is the most popular fish meal in the country, & you can make it yourself instead of paying a fortune at your local fish eatery. The special ingredient for these fish and chips… beer.

For a fun novelty project, try making a zoetrope at home. * A plastic coffee can lid

Learn how to do dumbbell squat thrust with alternate lockouts, an advanced exercise. Presented by Real Jock Gay Fitness Health & Life.

If you're a normal, non-corporate video conferencing user, you may not have heard of BlueJeans, but in the corporate world, the software has long been a major staple when it comes to remote meetings.

As NASA nears the launch of another mission to the Moon in 2024, and a subsequent mission to Mars in the 2030s, augmented reality is increasingly being woven into the normal space operations to test various capabilities.

The battle for augmented reality and social media supremacy starts with the people working behind the scenes, and this week Snap pulled off a telling win that could indicate a shift in the AR space.

The electric vehicle space is where a lot of the most cutting-edge technology is used to push vehicles forward (the best example being Tesla).

During the Tuesday launch of Google I/O, the company's CEO, Sundar Pichai, pulled off a Steve Jobsian "one more thing" move near the end of his keynote address that was simply stunning.

Learning to code is difficult, particularly if you're doing it alone. While coding may be among the most valued job skills in many markets, the education is sometimes inaccessible.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

Netflix has offered its beta program officially through the Play Store for some time now. Still, the issue most of us face — the beta availability is always scarce. Without getting lucky and landing a beta spot early on when the gates were open, there wasn't much you could do about it. However, there's now a brand new method you can use to sideload the Netflix beta app and join in on the fun.

If you have an Android device that Netflix does not support, you can check the Play Store and it simply won't be there. But just because you're unable to download it through official means doesn't mean you have to live without Netflix since there's a way you can sideload it manually.

With the Galaxy S20, Samsung has officially removed the Bixby button from its flagships. While it was a controversial key, in its later days, it did give us the ability to launch an app or custom action at the press of a button. There's still a way to do something like that, but now, you'll have to use the power button instead.

After the lackluster update that was iOS 13.3.1, we beta testers were in need of some excitement. Thankfully, Apple delivered the goods with iOS 13.4 developer beta 1, introducing fun new features like fresh Memoji stickers and a new Mail toolbar. Of course, that update was for developers only, so we public testers are thrilled that Apple just released the first public beta today.

We may or may not see Apple's long-awaited take on AR smartglasses this year, but the company is more than getting its practice swings in with its current wearables business, which hit record revenue in 2019 according to financial results released this week.

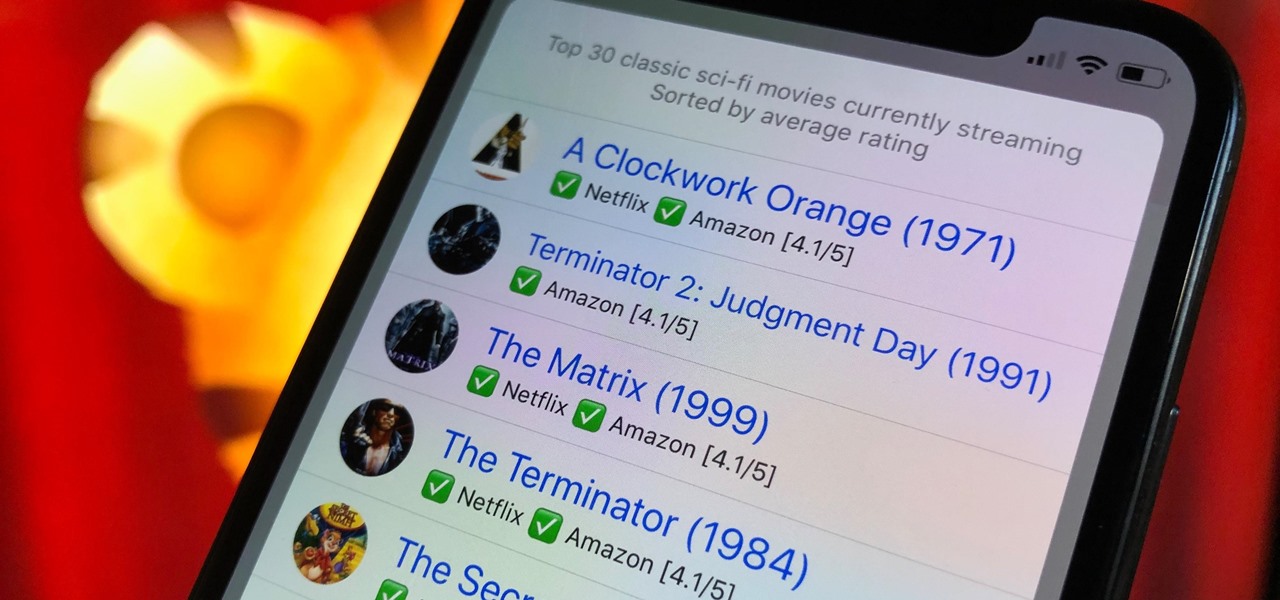
Choosing a movie to watch at home can be incredibly difficult when you don't already have one in mind. But there's a shortcut for your iPhone that can make it easier to browse your streaming media services for something good to play. More specifically, it lets you browse Netflix and Amazon Prime at the same time.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.