Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Unless you're someone who's terrified of social situations, chances are you love to talk. But no matter how much you want to share you life story or take over the conversation, you shouldn't. Your socially awkward coworkers that keep their mouth shut might actually have a leg up on you at work, and here's why.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.
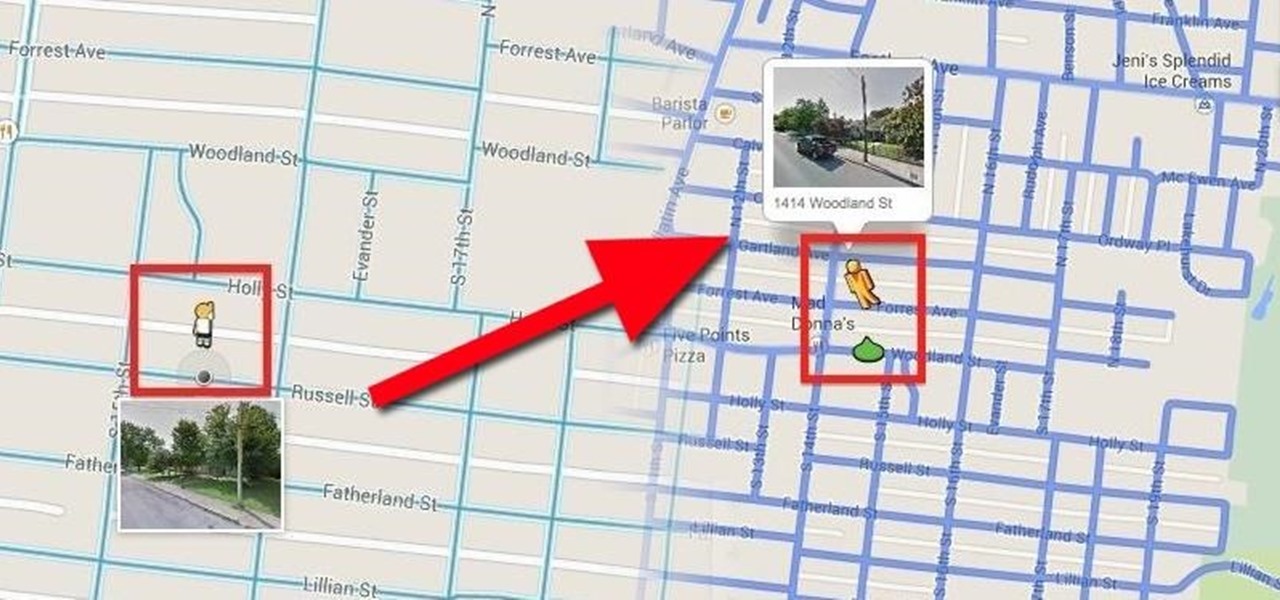
When the Google Maps web app got a massive redesign earlier this year, I was pretty excited to try it out, but it was a fairly disappointing update for me. The slower load times, confusing street view, and bicyclist neglect are just a few of the reasons I don't enjoy it over the old classic Google Maps. The brand new drag-and-drop measuring tool released this week is actually pretty useful, but not enough to change my mind.

It may seem impossible to win an argument against an irrational person, but it turns out the tried-and-true techniques that hostage negotiators use against hostage-takers work surprisingly well in everyday situations. You may not ever deal with a real hostage situation personally, but life is full of negotiations with unreasonable people, and those conversations don't always have to end in rage or disappointment. The mental techniques that professional hostage negotiators use can help both pa...

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Are you searching for a homemade cat repellent solution? This article will cover natural indoor and outdoor deterrents for every scenario where cats are causing trouble. The first part will cover home remedies for training cats to stay away from furniture and other restricted areas inside your house. The second part will cover outdoor repellents for keeping cats away from your garden, plants and yard. Step 1: Indoor Repellents for Training Cats

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?

What is gluten, why do some people think it is pure culinary evil, and why are there more and more products devoted to being free of this mysterious substance? Here's what one person thinks: What Is Gluten Really?

Ever since the much-lauded effects of the Mediterranean diet became widely known, people have been buying olive oil by the gallon. A diet that prevents heart disease, is based on fresh, seasonal foods, and includes a tasty as hell fat like olive oil? Duh—that's a no-brainer.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.
What is Programming? Why need to learn? How to get started? Which language to choose? While surfing web, you must be encountering various softwares, games, etc. and might be thinking to make one, but don't know where to start. Here, I am starting series in Programming.

If you're reading this, chances are you're a softModder, someone who doesn't let anything stand in his or her way from ultimate customization.

With over a million apps available in the App Store, you'd think that Apple would have come up with a better way to organize them on your iPhone.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

This is the first 3D game from the Castlevania series, and it's solely for the Nintendo 64! This 18-part walkthrough series will cover everything involved in beaten Castlevania 64 using the Carrie Fernandez character. She's a young orphan gifted with dangerous magic powers on a vampire hunting mission to stop Count Dracula's impeding return to power. Watch and learn! Then try out defeating the game using Reinhardt Schneider.

In the Xbox 360 game Darksiders, you'll eventually have to play the Iron Canopy level, which consists of The Seesaw, Webbed Floor, Two Lifts 1 Bomb, Loom Wardens, Broodmother, Silitha and Return Silitha's Heart. War will be ambushed and captured as he enters the Iron Canopy. When he comes to, you'll find him hanging from a spider web. Tap the Action button to break free. Make your way around to the left to discover a Soul Chest in hidden nook behind your starting location. Now cross the webbe...

Who could forget the spectacular conclusion to the "Back to the Future" trilogy? The scene where Marty and Doc Brown use a train to push the DeLorean to 88 miles an hour so Marty can return to the 1980s has become iconic. With this tutorial, you can recreate the scene in miniature using fairly inexpensive props.

You don't need flying broomsticks or magic balls to play this version of the game – it's tailor-made for muggles like us.

With a little time, you can turn a pair of rabbits into lifetime bunny buddies. Step 1

Learn how to do full situps with dumbbells and alternate cross punches. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do a low single cable squat power cross punch. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do knee tuck floor crunches. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do single-dumbbell front lunge and power row at bottom. Presented by Real Jock Gay Fitness Health & Life.

Learn how to play a classic vocal warm-up rising through the keys playing a major scale up to note 5 and returning to the root before rising by a semitone

This video shows you how to create a LEGO Star Wars imperial scout trooper from Episode 6...The Return of the Jedi.

In this video, Curtis Smith from Southwest Yard & Garden is joined by Bernadillo County Home Economist Patricia Aaron to talk to us about cooking with pumpkins. There's probably no vegetable that anounces the arrival of fall like a pumpkin. When you're using a pumpkin to make piesm cakes, and so forth, you want to choose a medium-sized one. Smaller pumpkins can make good side dishes. Bear in mind, it takes a bought a half pound of cooked pumpkin to make one serving. Here, we're using a nice m...

Here's how to make this Middle Eastern delicacy. You Will Need:

iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...

In this video tutorial, Mad Cow Moo shows you how to do blurs on footage in Sony Vegas. Looking on the time line for a break in the audio, place the cursor at this point and hit s on the keyboard to split the video into segments Go to the time line to the final frame you want and point the cursor here, creating a highlight, and hit the s key again. Right click on the audio, select group from the drop down and choose, "Remove From". Right click the video track on the left top corresponding to ...

To make Italian meringue butter cream cake icing you need some basic ingredients. The things that you need are 2 Cup Light Corn, Syrup, 2 Cup Egg Whites, 2 Teaspoon Cream of Tartar, 1/2 Cup Granulated Sugar, 2lbs Butter, 1 Tablespoon of extract. Start out by placing the corn syrup into a heavy bottom pot onto medium heat. Onto the egg whites. Start beating the egg whites (medium speed)till a bit frothy and then add the cream of tartar. Increase speed to high and while beating add the sugar. B...

Kare-kare is a Filipino oxtail stew with bok choy and peanut butter. This stew is full of flavorful ingredients that create depth and interest to the marrow rich oxtail. This hearty dish will fill you up while delighting your taste buds with rich flavors. Watch this video to learn how to make a traditional Filipino oxtail stew called kare kare. This will comfort you on cold days. Ingredients: 3 tbsp oil, 2.5 kg/5 lb oxtail or 2 kg/4 lb shin of beef, 3 tsp salt, 2 tbsp annatto seeds, 2 large o...

Learn to do the basic moves of Afro-Brazilian Dance, Capoeira with this video tutorial. Part 1