While you can do a lot of things on your smartphone that were once only done on a computer, having a laptop is still necessary and critical for many tasks. Often times, the two devices work very well together.

Android "Lollipop" introduced a ton of cool new functionality. Unfortunately, the Nexus 5 didn't get all of these features, as some were exclusive to other devices. For example, the Ambient Display function on the Nexus 6 that shows new notifications as they come in with a black-and-white lock screen. Sure, the new Nexus phablet has an AMOLED display that doesn't waste any battery to power black pixels, but it would be nice to have this feature as an option on the Nexus 5, wouldn't it?

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

The noodle is a noble thing. And while I love ramen and pasta, I have a real soft spot in my heart for macaroni salad (especially the kind that comes with Hawaiian plate lunch) and the type of pasta salad that's dished up during picnics and barbecues.
Though they share the same name, the HTC One and OnePlus One have completely different sound quality. HTC had put a lot of time and effort into fine-tuning their BoomSound technology, while OnePlus is still fairly new to the game, with brand recognition being a much greater objective than awesome speakers.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Trying to explain something difficult over the phone can be pretty frustrating if the other person doesn't understand you. Using text messages can be useless for auditory learners, and a phone call won't do much good for a reading or visual learner.

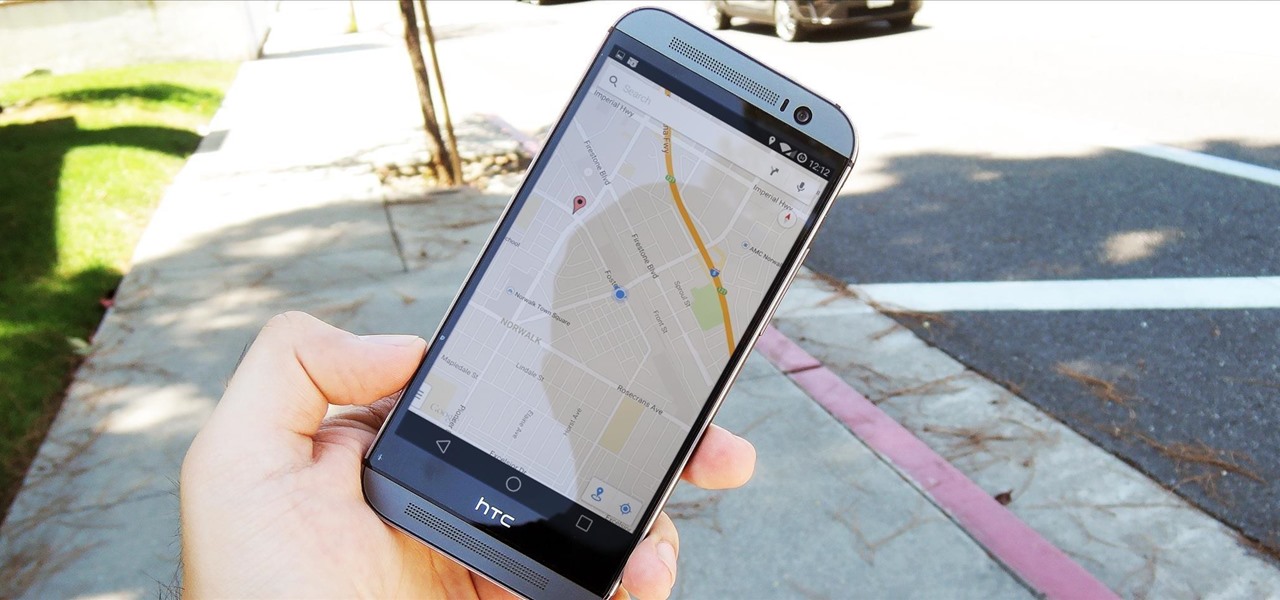
Google's Android Device Manager makes it extremely easy to track down your phone or tablet, but while it's simple to set up and use, it does require your device to have an active data connection, which can be an issue in some areas.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

Hangouts and WhatsApp might be the preferred messaging apps for Android, but it's only a matter of time before Facebook Messenger surpasses them.

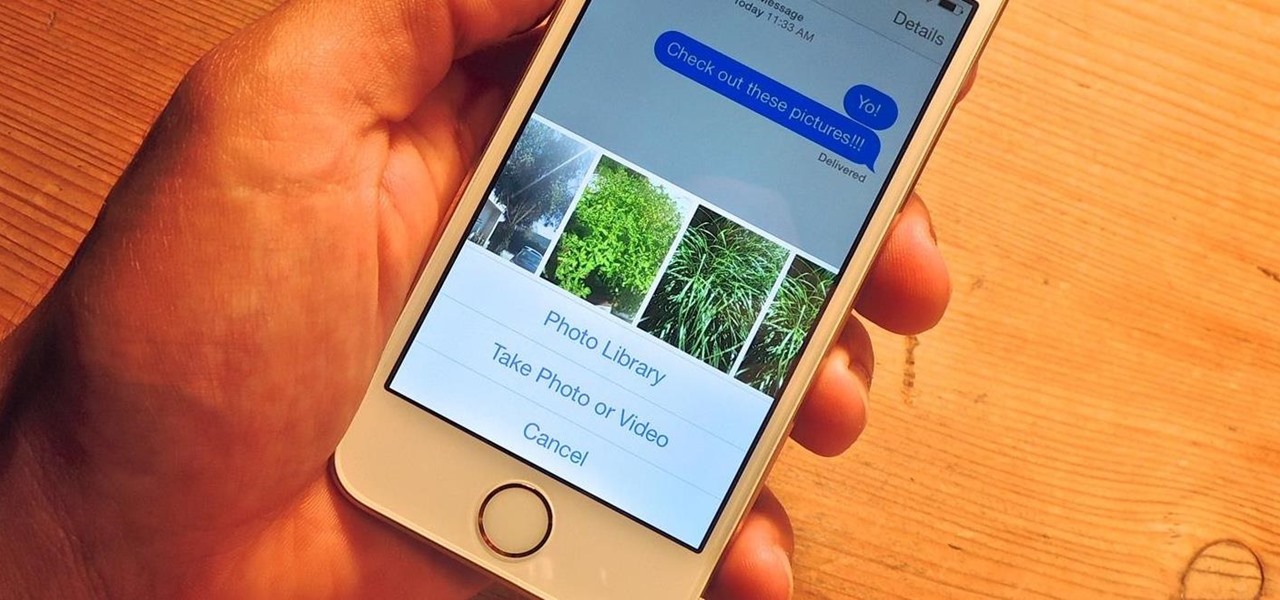
As it is right now, you can only send 5 images by email at the same time from your Camera Roll in iOS 7. There are some workarounds to increase that number, but a new feature in iOS 8 is finally making them unnecessary.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Parents, grandparents, aunts and uncles, and even older siblings have all likely dealt with handing their smartphones over to young children. No matter if they want to play games or watch cartoons or record funny noises, you're handing over a very personal device to those who can mess up what they don't know.

Are you searching for a homemade cat repellent solution? This article will cover natural indoor and outdoor deterrents for every scenario where cats are causing trouble. The first part will cover home remedies for training cats to stay away from furniture and other restricted areas inside your house. The second part will cover outdoor repellents for keeping cats away from your garden, plants and yard. Step 1: Indoor Repellents for Training Cats

I'll be the first to admit how horrible my memory is, whether it's remembering to take out the garbage or paying a bill on time. That's why I regularly utilize the stock Reminders app on my iPhone; it's definitely compensated for my memory deficiencies.

If you've ever noticed, even just for a fleeting moment, that the auto brightness on your Nexus 5 seemed to "glitch out"—you are not alone.

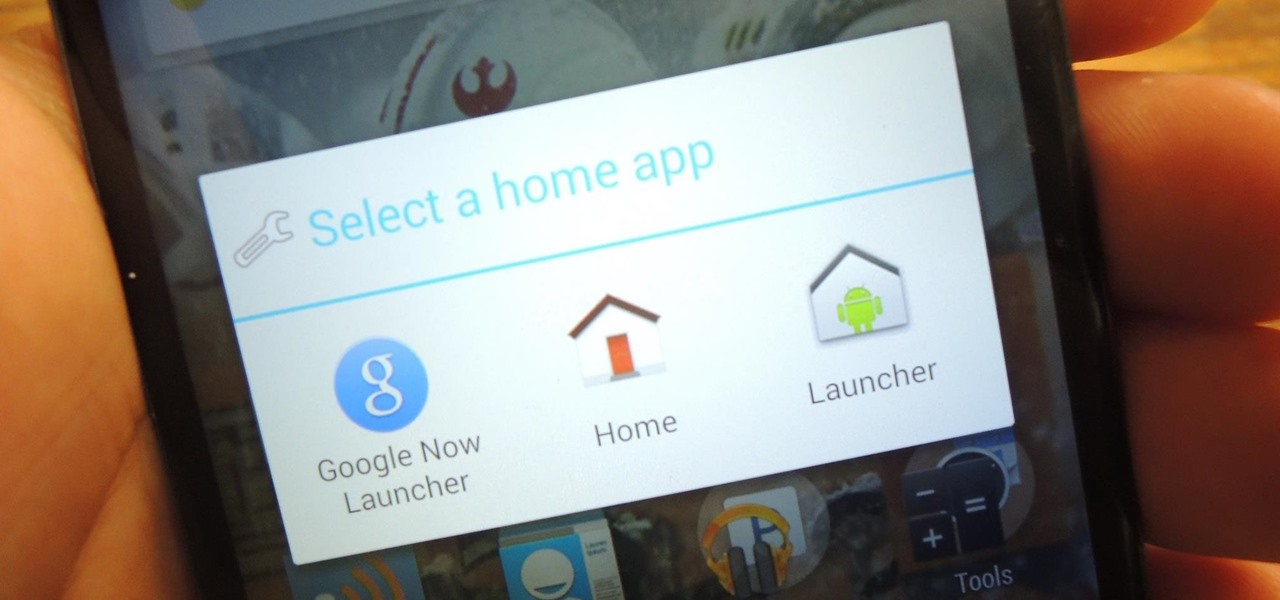
You've seen it a million times. You try to do something on your Android device and a box pops up asking you which app you'd like to use. You could try Photos, Gallery, Drive, Picasa Web Albums...the list is fairly extensive sometimes. And what's worse, after that you have to select "Always" or "Just once". Add it all up, and that's three taps to do something you thought would take just one!

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.
What is Programming? Why need to learn? How to get started? Which language to choose? While surfing web, you must be encountering various softwares, games, etc. and might be thinking to make one, but don't know where to start. Here, I am starting series in Programming.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

This last weekend, Apple released the second beta of iOS 7.1 for iPad, iPhone, and iPod touch, and I've got a firsthand look of what's to come in iOS 7.1—the first major update since iOS 7 was released.

With over a million apps available in the App Store, you'd think that Apple would have come up with a better way to organize them on your iPhone.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

The new Moto X may not have a lot going for it when it comes to hardware, but there are some pretty cool software features that makes it a tempting device. One of these cool features is its Active Display notifications that appear on the lock screen.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

There are some really talented graffiti artists out there. Some of them are good enough that businesses hire them to paint advertisements, rather than hiring someone to scrub their work off the side of the building.

Facebook Home was just released in the Google Play Store a couple days ago, and for those of you eagerly waiting to get it on your Nexus 7, you'll unfortunately be stuck with this message: The new Facebook Home launcher app is blocked on the Nexus 7, because Facebook only released it for a few select Android phones. Home for tablets probably won't appear for months, but that's okay, because you don't have to wait that long! In this article, I'm going to show you how to get Facebook Home insta...

Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.

A lot of people have problems with their cats urinating inside the house, leaving behind the retched odor of cat pee. Others get frustrated when feral or stray cats pee on their porch, patio, or anywhere else outside of their house, as it's not the most welcoming odor when guests arrive.

There are very, very few things better than a solid Hobbit songI mean, I was almost brought to tears when Pippin busted out this one in The Lord of the Rings: Return of the King.

Life has many perils: parasites, predators, and pitfalls. Eventually, any organism will succumb, and if that organism has not first passed on its genes, those genes will face extinction.

TIFF 2012 Wrap-Up - Pounds Personally Gained: 4.5

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

It's already August, which means school will be back in just a few short weeks. If you're getting ready to start or go back to college, that means you'll probably be dropping a few hundred bucks on textbooks. Here are some of the best places online to buy, sell and rent textbooks so that you can get back to more important things, like making your papers look longer than they really are and getting around your school's website blockers. Plus you can spend your money on more exciting things, li...

Assuming everyone knows of the recent "String of attacks" passed between Obama and Romney, I just want to talk about how useless this entire thing is. I'll try to be as un-biased as possible.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

If you love the ocean and love swimming, it's time you step up to the next level… snorkeling. Snorkeling is one of the best ways to explore the underwater life, without fancy equipment or expensive training. And all you need is a snorkel. If you want a better look at what’s underwater, all you have to do is snorkel.

Impress everyone by bringing a beautiful homemade tart to the next celebration. You can use seasonal berries or even other fruits to create a colorful and flavorful dessert that will make any occasion seem extra special. With its rich pastry cream and tangy fruit wrapped in a flaky, buttery shell, the fruit tart is a classic dessert. Make this version with one or more of your favorites berries.