Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

It's easy to forget just how cool face filters are. Augmented reality has come a long way, and apps like Instagram now offer a suite of impressive effects to play with, but some of the best ones aren't easily found. There is a treasure trove of exclusive, custom face filters that are unavailable to the general public, but not at all inaccessible — you just need to know the trick to getting them.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

Picture this: You finally get that awesome angle, the perfect selfie. You can't wait to post it on your Instagram, except there's one problem — it looks a little flat and the colors just seem off. Maybe it's the lights? Or maybe your new smartphone camera isn't as good as you thought? How are your friends getting those beautiful photos they've been posting on social media?

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an understated advantage of the software is how dead-simple it is to modify with root-level tweaks.

With all the controversy around the Pixel 3 XL, the regular-sized Pixel 3 might be the phone of choice for most users. Thanks to the huge boost in screen size, the little brother is now an easier pickup for those who like a bigger screen. And once more, the internals are the same, giving you the same experience as the 3 XL without the display notch.

One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

Continuing our NR30 series this week, we focused on the leaders of the software development industry that make augmented reality experiences possible. In other news, two of the current leaders in making AR headsets, Microsoft and Magic Leap, are pursuing multiple verticals with their products, as both now appear to be interested in making AR headsets for the military.

You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and ensure you're insulated from any potential liabilities that may appear down the road.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

Considering Rovio Entertainment quite literally owes its existence to Apple and the App Store, it may ruffle a few feathers that the company has opted to aim the augmented reality debut of its blockbuster Angry Birds franchise at Magic Leap instead.

Like an overbearing mother, Apple will constantly nag you through annoying red bubble alerts about iOS updates that are ready to install. Fortunately, you don't have to take this issue lying down, as there are ways to prevent your iPhone from receiving OTA updates and their corresponding prompts, regardless of whether your device is jailbroken or not.

All phones (yes, iPhones too) slow down over time. As your device gets bogged down by various apps and you begin to run out of storage, it's just an inevitability. That doesn't make it any less frustrating ... I mean, is there anything more annoying than a slow phone? My answer: No. Of course not. It's the single most annoying thing ever.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

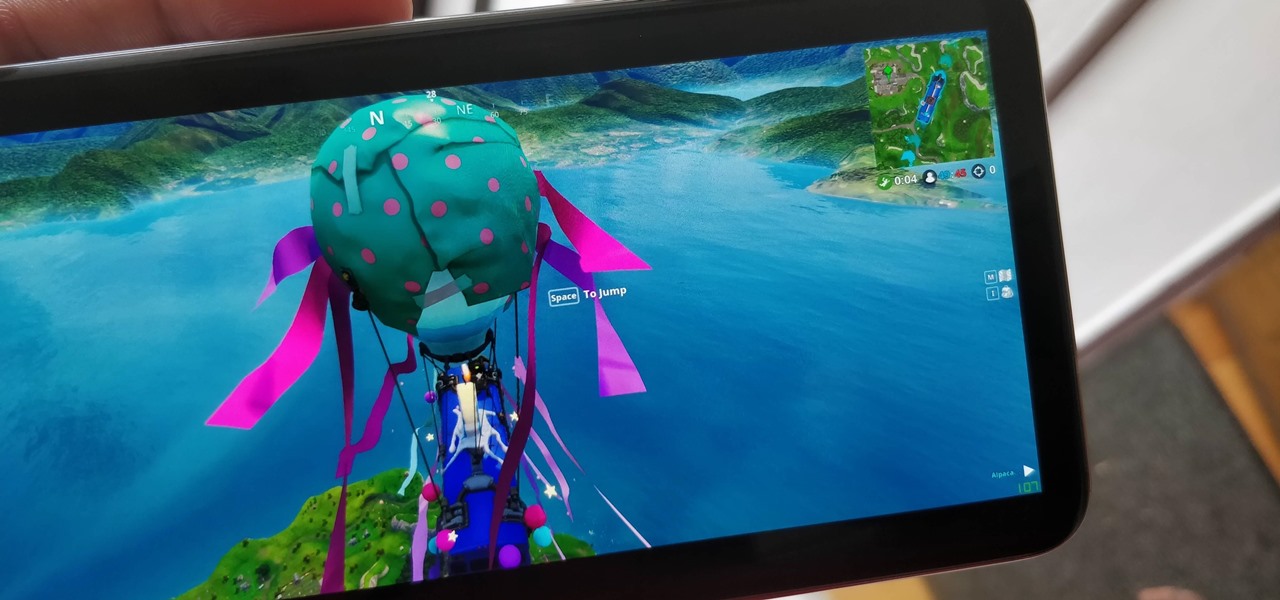
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satisfy our urge to play.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Earlier this month, when Apple announced at WWDC that iOS 12 would include an augmented reality tape measure called Measure, iPhone watchers seemed impressed by the new addition to the company's AR arsenal. Well, just a couple of weeks later, on June 19, it appears that Google remembered it had its own Measure app as well.

During its presentation at Unite Berlin, Magic Leap gave attendees a crash course in developing experiences for Magic Leap One (ML1), we found out quite a bit more about how the device works and what we can expect to experience with the device.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Apple released iOS 12 on Sept. 17, and most of the announced features have been released for the iPhone's latest available operating system. However, some brand new features can be accessed with Apple's latest beta, iOS 12.4. If you want to try out all its new features before everyone else, you can install the developer or public beta on your iPhone right now.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

There's always been a clear divide between flagship and midrange phones. Flagships will run you at least $700, while midrange typically falls between $250 and $550. The main difference is the processor, with midrange phones sporting a 600-series Snapdragon and flagships rocking the 800-series. Now, Qualcomm may have just created another smartphone tier with their newly-unveiled 700-series chip.

Apple's next big developer event happened on June 4, and it was the first glimpse of iOS 12 that anyone's seen. While there were lots of rumored features to be unveiled at WWDC 2018, Apple concentrated mostly on squashing bugs and making iOS work as seamless as it did years ago. Still, we had hoped that Apple would have added these features in iOS 12, but only a few made the cut.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.