What do Leo Tolstoy (writer), Beethoven (composer), Paul Gaugin (artist), and Adolf Hitler (politician) have in common? They are all considered to have suffered from the sexually transmitted disease syphilis.

In this video tutorial, viewers learn how to perform the double undercut using a deck of cards. This shuffle controls the bottom card. The trick begins with the magician asking the spectator to choose a card. Return the card on top of the deck. Then it will be shuffle and end up at the bottom. To do this trick, create a break between the card and the deck. Now cut the deck in half. The right hand packet is placed under the left hand packet. The card is now transferred to the right hand. The l...

The chefs at the food channel are going to show you how to do a crab boil the best way possible. First, you are going to need a large pot connected to propane gas and to fill it up with 8 gallons of water to boil. Next, you want to add the seasonings to the pot which are, 2 cups of salt, a healthy amount of black peppercorn, 4 bags of seafood pickling mixtures, 3 small bottles of cooking oil, and a nice amount of hot sauce for some kick. You want to add the top back to the pot and let that si...
In this video tutorial, Chris Pels will show how to create a web service in ASP.NET and then call the service from another ASP.NET web site. First, learn how to create an .asmx component which represents a web service in an ASP.NET web site. When creating the web service learn how to control several aspects of the web service functionality with web service attributes. Next, see how to test the web service in the Visual Studio web service test page. Then learn how ASP.NET allows many .NET data...
How to hack Pet Society! Pet Society cheats, tricks, hacks. Watch this video tutorial to learn how to hack paw points and EXP in Pet Society (09/26/09).

Learn how to cast on to knit using a circular loom. Start at the beginning with an empty loom and wrap your yarn around the beginning peg. Working to the right, wrap the yarn behind each peg, and around in a clockwise fashion. Do the same on the next peg, until you have returned to the beginning again. Repeat this process for the second row. Take your tool, which will come with the loom, and lift the bottom stitch over the top stitch and off the peg. Work all the way around the loom to the be...

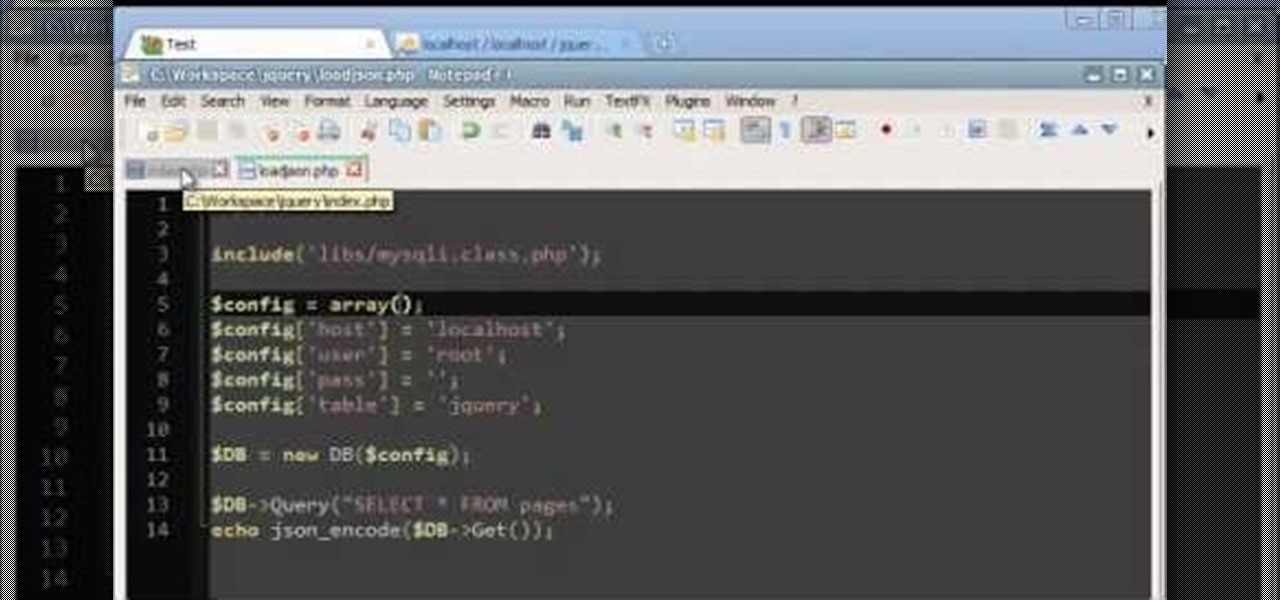
Load JSON (JavaScript Object Notation) data from an existing database file into jQuery by following along with this informative and illustrative video tutorial from JREAMdesign. Here, a database query is used and the results are returned to jQuery via AJAX formatted in JSON.

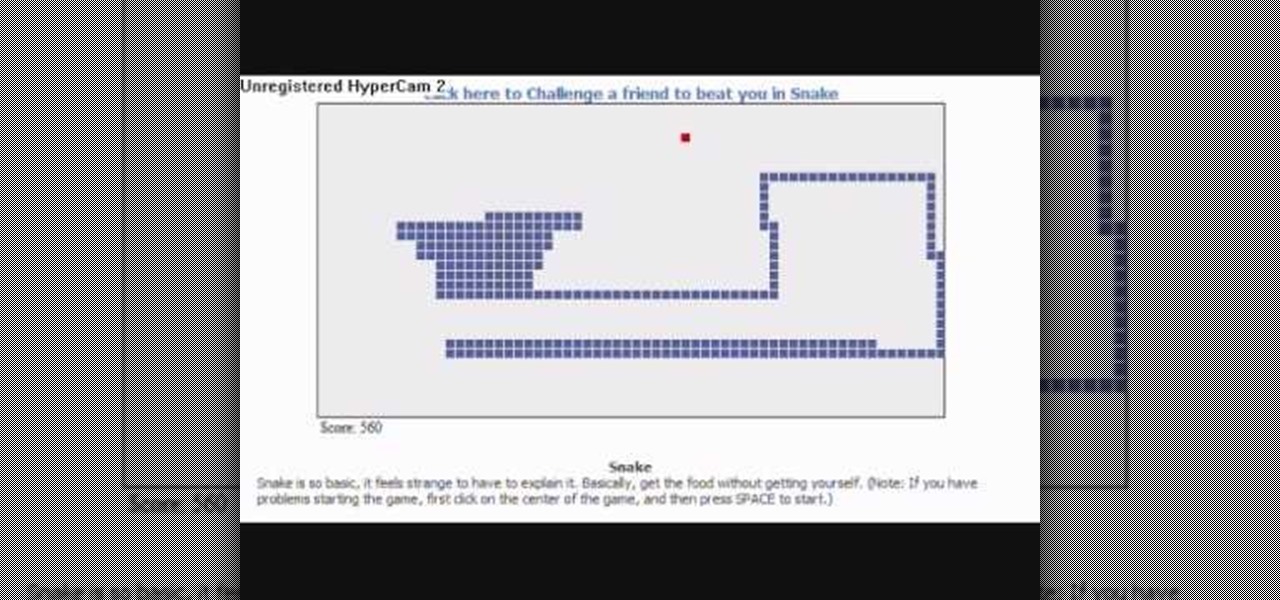
Once a simple video game... well, it's still a simple video game that's returned to your Facebook page. This video demonstrates how you can play the nostalgic arcade game Snake. Catch the food and grow longer without running into yourself!

Flexion exercises are a popular method to flatten a stomach after pregnancy. But always make sure that you give your body time to heal after becoming a new mother. Avoid these Flexion exercises until you're sure that your body has returned to normal.

Learning the blues isn't an easy task, but this video helps make it a little easier. The song you'll be learning is "Coffee Blues" by Mississippi John Hurt. It's in the key of A and is a typical blues progression, in an alternating bass. It's the chords A, D, and E. If you're yearning to learn the delta blues, this is a great first step.

Learn how to do break dance push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

In this video we learn how to perform knee replacement surgery. The knee joint is accessed with an incision. Then, a number of different surgical tools will be used to perform the procedure. The part of the knee joint is removed first with surgical saws. Then, the artificial joint is put back into the area. Once this part is secured with screws, an insert will be joined in with it to keep it in place. The artificial joint is checked for the last time, then sutures are used to closed the joint...

This video teaches you a simple and easy way to make corn dollies. For those of you that don't know, corn dollies are the homes for the spirits of corn that have lost their homes during the harvest. The spirits will live in the doll throughout the winter and will be returned to the fields the forthcoming spring. To make these you will need corn husks, Sharpies, a pair of scissors, and ribbons of your desired color. These corn dollies are a fun project for kids and will be sure to help create ...

Phil and Charlie explain how its done in space. Each Space Shuttle has a toilet that can be used by both men and women. Designed to be as much as possible like those on Earth, the units use flowing air instead of water to move waste through the system.

Check out this instructional RV video to learn how to maintain the LP gas system on your recreational vehicle. Open up the compartment and you will see your LP tank. There is a gauge that tells you how much is inside the tank, there is also a fill station where you fill it up, always make sure the cap is returned after filling it up, so no debris gets inside. There is also a pressure release valve so when you are filling it, the pressure can escape through there so you can get the proper amou...

Well I've converted one of these rc bikes into a snarling (ha ha) nitro powered machine. I'm now going to convert my other stock model into a brushless monster. This particular bike had a rather bumpy crossing from the USA when I bought it from ebay. It got damaged in it's box and was returned to the sender. He, very nicely, found a new set of front forks, fitted them and posted it back to me, for no extra charge! Top Man! It's a bit sluggish, stock, so I think sticking a MAMBA MAX 7700kv mot...

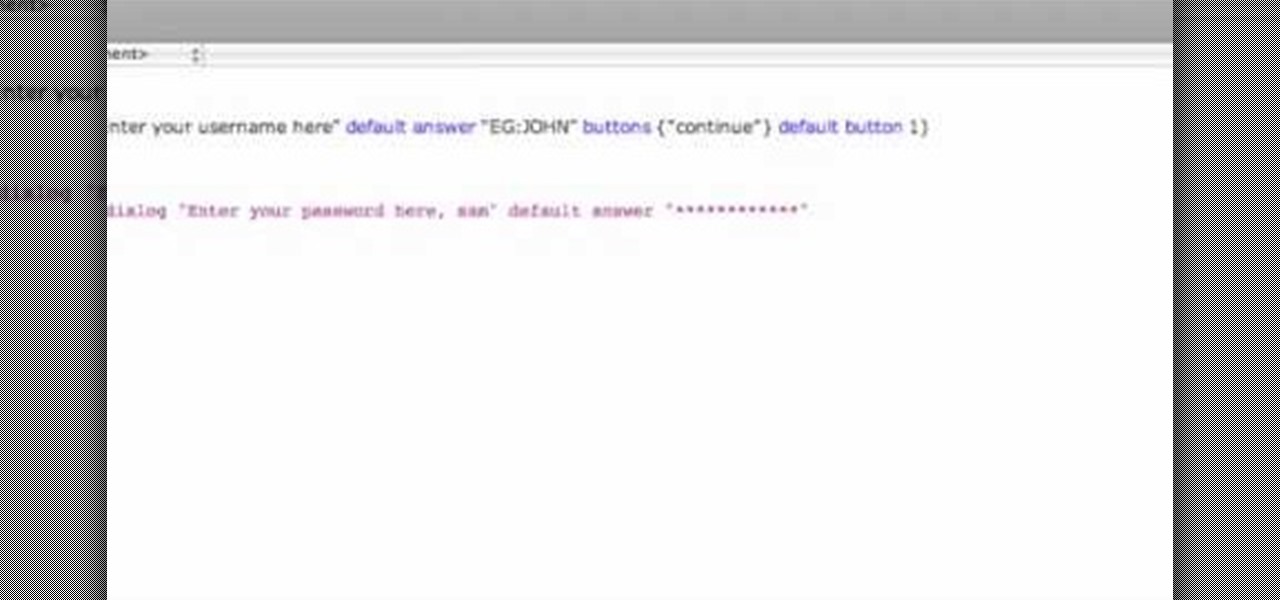
This video shows how to program a password and user protected application in AppleScript.

For anyone who's ever wondered why people are swatting an odd-looking object back and forth across a net, here's the lowdown. Watch this video to learn how to play badminton.

Learn how to do a single dumbbell windmill and Arnold press. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do multi directional speed lunges with shoe tap. Presented by Real Jock Gay Fitness Health & Life.

Welcome back! In the last round of python training, we talked about tuples and dictionaries. We'll be diverging again and talking about logical operators as well as membership operators. These are used very similiar to booleans, so if you haven't read that, I suggest you do so first.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm.

In these PHP basics video the tutor shows how to do form processing. Handling forms in PHP is basically the main functionality of PHP. The forms in HTML take the values of a from and send them to the PHP in real time to do the form processing. In this video the tutor shows how to make a HTML form from the scratch inserting a form into it with some fields and buttons. Now he makes the form post a method to a PHP page when you submit it. Now he shows how to make a PHP file from the scratch by w...

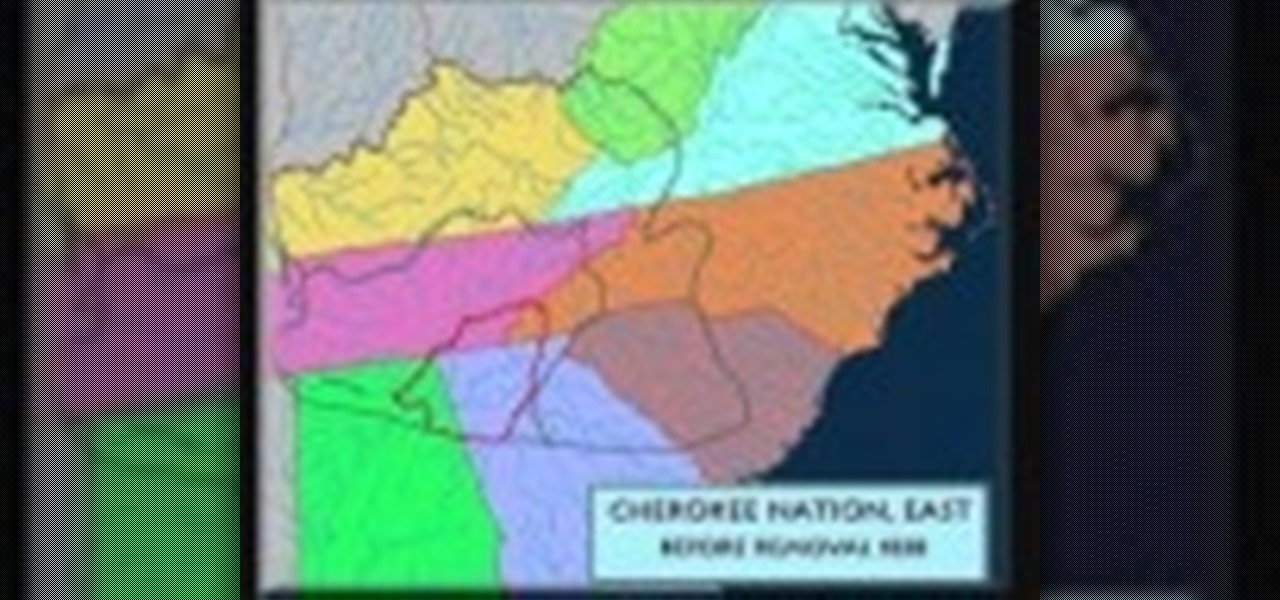
Check out this instructional language video to learn how to speak Cherokee! In this lesson, learn how to sing the Cherokee hymn about the trail of tears. The Cherokee hymn "Guide Me O, Thou Great Jehovah" is a song about the trail of tears presented here in the Cherokee language, in the Giduwa dialect. Although many died on the trail, several returned to the east. Practice your Cherokee by learning this song!

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

Have you tried searching for 4K HDR videos on YouTube, only to get 1080p videos just because the uploader used "4k" or "HDR" in the description? Or have you tried looking for a video about something that just happened, except YouTube's algorithm surfaces established videos first by default, so all the results you get are older than a month? Well, there's a better way.

Yes, bubonic plague—the Black Death that killed millions in the Middle Ages— is still out there. It even infects and kills people in the United States. Without treatment, half the people infected die, but the Food and Drug Administration approved ciprofloxacin in 2015 to treat plague, and it has just successfully been used to stop the infection in five people.

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

Well, first things firsts, it's been awhile! I'm sorry the series has been dead for a little bit, but I recently hit some personal relationship issues and needed to take some time to think. But, now that it's all said and done, the dust can settle and we can start training again!

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.