If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

The holidays are quickly approaching, which means everyone will be scrambling over the next couple of weeks to find the cheapest options for flights to wherever home is. There are so many sites to buy them from that it can be hard to know where to start, so we've compiled some tips and tricks for making the process as painless as possible, whether you're flying home for Thanksgiving, Christmas, or whenever.

They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few important dates you need to know.

Nintendo may be developing cases that'll turn your iPhone into a gaming device like the Game Boy, but until something materializes there, you're stuck with cheap knockoffs on Amazon or a real Game Boy or Game Boy Color. But there's something else you can do to play eight-bit Nintendo games on your iPhone right now.

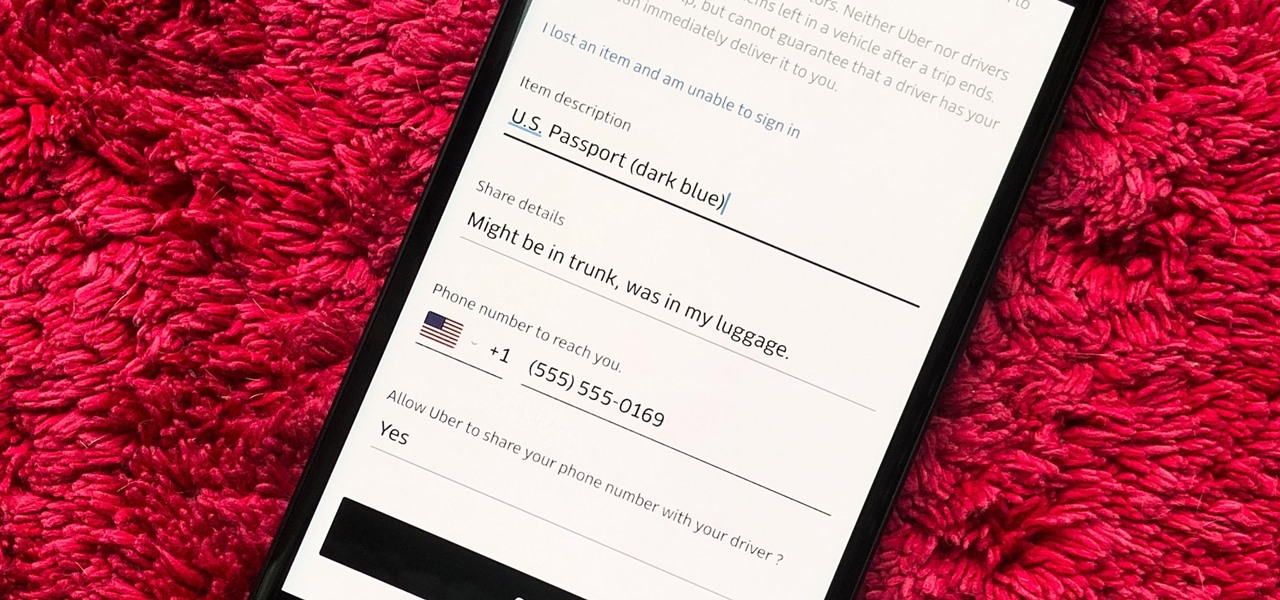
You would think that recovering your smartphone or another important item that you leave behind in an Uber ride would be a simple process, but it can actually be a pain in the ass. You have to find out how to report it to the driver, hope the driver is honest, pay a fee, and contact Uber directly if none of that works. But we're here to help make this process as easy as possible for you.

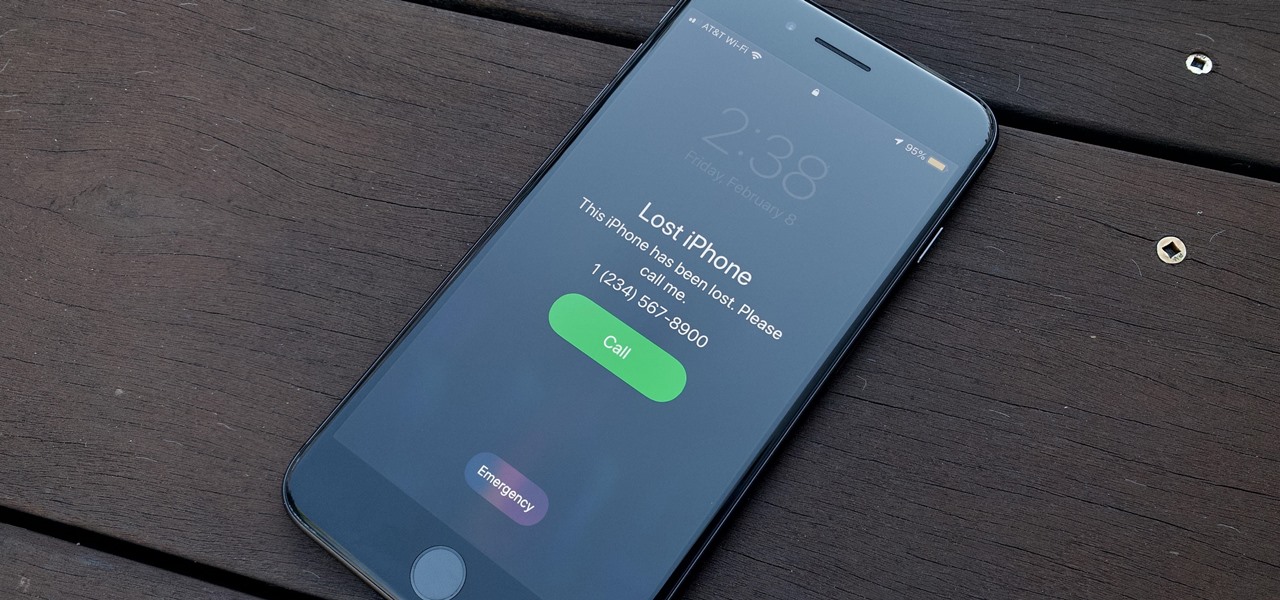
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-gooder won't know to contact you, and that's where Find My iPhone's "Lost Mode" comes in handy.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

While there are over 100 cool features iOS 12 has to offer, there are some things Apple has made more annoying on iPhones or just has not addressed yet.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

If you've read any health news in the past year or so, you've probably been bombarded with headlines announcing that frequent sitters face certain death, even when you're just relaxing and watching TV at home.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

The mission to rise above the fray to become a leading player in the augmented reality business is a moving target that depends on innovation, resources, and timing.

Apple just released the fourth public beta for iOS 14 today, Thursday, Aug. 6. This update comes two days after the company released iOS 14 developer beta 4, 15 days after Apple seeded developers the third dev beta, and two weeks after the release of public beta 3.

Apple just released the fourth developer beta for iOS 14 today, Tuesday, Aug. 4. This update comes 13 days after Apple seeded developers the third dev beta, and 12 days after public testers got their hands on public beta 3.

Apple released iOS 13.0 on Sept. 19 and announced on the same day the release of iOS 13.1 on Sept. 30. But that deadline was pushed up to Sept. 24, and that's why we have 13.1 just five days after 13.0. But that's good news since we don't have to wait any longer for some of the features promised in iOS 13 that didn't make the first cut.

Comparing the present-day states of the consumer and enterprise sectors of augmented reality is like evaluating the merits of sports car versus work trucks. Like consumer AR, sports cars are sexy and exciting, but perhaps a bit impractical at times. On the other hand, enterprise AR is utilitarian, but it gets the job done and, in the long run, pays for itself.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

There's no denying that there are some seriously useful new features in iOS 11 for iPhone. But there's also no denying that Apple got a few things wrong with the latest iOS update, as well as left a few important features out.

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

Part of the mainstreaming of augmented reality is learning to adopt new habits around the hardware delivering these groundbreaking next-gen interface experiences.

A lot of digital ink has been spilled heaping scorn on Magic Leap. Much of that media schadenfreude was due to what some believed were unmet promises versus some of the early hype around the product. Others just seemed to be rubbed the wrong way by the startup's Apple-esque secrecy and penchant for attempting to coin new terms and frameworks for things that were, mostly, already in play.

After years of complaining about rising prices, OEMs are finally listening to consumers. It couldn't have come at a better time thanks to potential recession due to COVID-19. As evident with the poor sales of Samsung's Galaxy S20 series, consumers are not looking to spending $1,000+ on a smartphone just for the latest specs.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Thought I would cross-post a piece I did a while ago.

While Google's generative AI wallpapers for Android won't be out until the fall, you can take advantage of emoji backgrounds and cinematic wallpapers on your Pixel smartphone right now.