This week, another guest returns to our Steampunk R&D show for the second time, Thomas Willeford. In our very first podcast, Thomas talked to us about creating his empire; this time we most notably talk about his recent appearance on the Science Channel's program Odd Folks Home, in an episode entitled "Blow Off Some Steampunk". Thomas Willeford is the owner and operator of Brute Force Studios, and has been responsible for some of Steampunk's most recognizable props and accessories, such as th...

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

An invaluable button on your iPhone can do hundreds, even thousands, of amazing things, but most iPhone users don't even know it exists. You can't push it. You can't click it. You can't press it. But it's the largest button on your iPhone, more powerful than the versatile Side button, and it's hiding in plain sight.

Video may have killed the radio star, but will volumetric capture and augmented reality kill the video star?

When wearables startup North officially unveiled its Focals smartglasses in October, the stylish frames strongly resembled, in form and function, Intel's canceled Vaunt smartglasses.

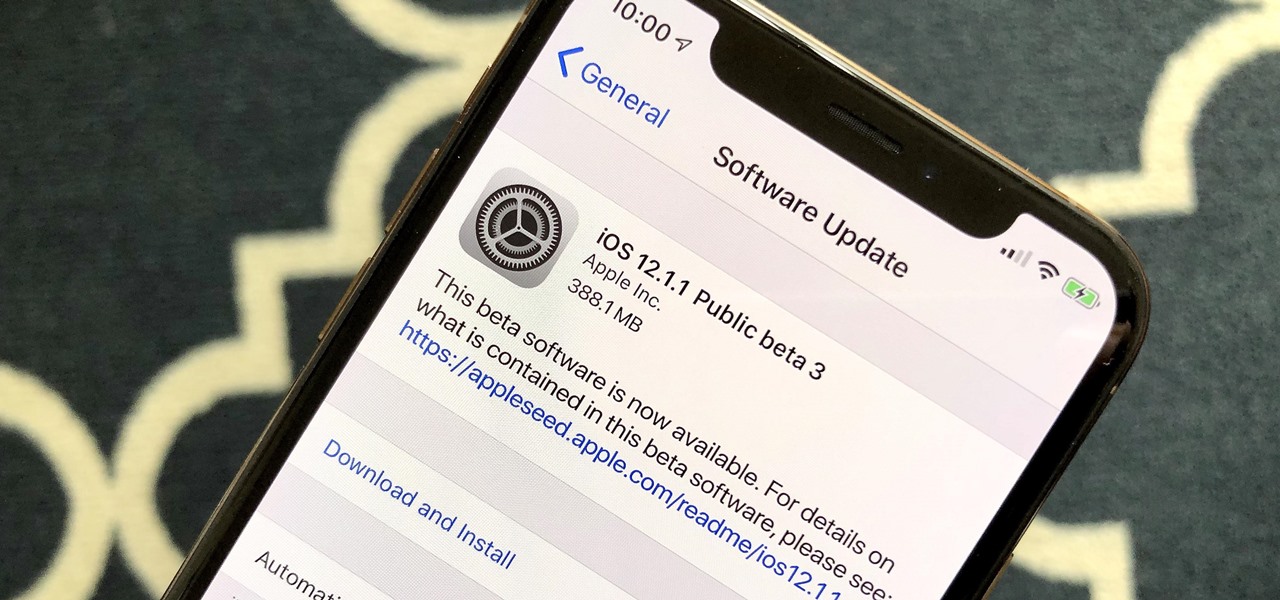
It seems Apple will keep with recent tradition — the third iOS 12.1.1 public beta released to software testers Thursday, Nov. 15, just hours after the 10 a.m. PDT (1 p.m. EDT) release of dev beta 3. Apple likes to take a short time after a developer release to ensure the beta is good enough to release as a whole, as seen with the entire iOS 12 dev beta 7 debacle.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

It's not an official app, but for fans of Rick and Morty, it's a welcome piece of the series' universe until the recently renewed animated show returns to Adult Swim.

While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.

Multitasking on a smartphone has never been better, but it still has some ways to go to compete with a desktop experience. Samsung hopes to change that with a new multitasking view on the Galaxy S9, which allows the user to open notifications in a new, smaller window on top of the app they are currently using.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

We've already seen how VR can have some therapeutic benefits, but not the dramatized version. A play called Ugly Lies the Bone emotionally examines how war veterans can heal (or at least treat) their PTSD using virtual reality.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Economists have long since known that people want to be rewarded for taking on risk. Investments are thus judged by their risk-adjusted returns (Sharpe ratios). A typical hedge fund has a Sharpe ratio of around 0.5. This means that its excess annual return over the risk-free rate is about half its annual standard deviation.

One of the most popular (but smallest) maps in the first Call of Duty: Black Ops was Nuketown. The tiny map allowed for maximum death tolls, making it an awesome map to play (and die) on. In the latest Call of Duty: Black Ops 2, that map returns in the form of Nuketown 2025, a futuristic version of the same level. It was available for free on November 13th to anyone who pre-ordered the game, purchased a launch copy, or purchased the Hardened or Care Package special editions of the game, thoug...

If you've ever found yourself wandering about a room, holding your phone up to the sky searching for a signal, this is just the trick for you. Edward from Redmond Pie found a great way to configure the readout with just a simple phone call, making your iPhone display its exact signal strength in decibels (dBm). Step 1: Put Your iPhone into Field Test Mode

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Samsung's One UI 3.0 skin is built on top of Google's Android 11 open source code base, which means you get all of the standard features, plus some cool bonus stuff from Samsung. However, it's one of those standard AOSP features that you might find most useful if you send a lot of ADB commands.

Some of the oldest art on Earth was created 36,000 years ago on the walls of the Chauvet Cave in France. However, these days, physical access to the cave is restricted in order to preserve the site.

Usually, flying into unknown territory would mean riding into the "danger zone", but Paramount and Snapchat are taking the trip anyway with one of Summer 2020's most anticipated movie sequels.

For years, Magic Leap has promised to deliver stunning augmented reality experiences that will outperform any other competitor, and a newly revealed partnership hints that the company may be able to deliver on those promises.

If $200 was too much for you to get in on some Star Wars augmented reality action, Best Buy is now selling refurbished Star Wars Jedi Challenges sets for $79.99 and new ones for $99.99.

Fans of The Walking Dead can now kill time until the series returns from its winter hiatus by raising walkers from the labels on bottles of wine influenced by the show.

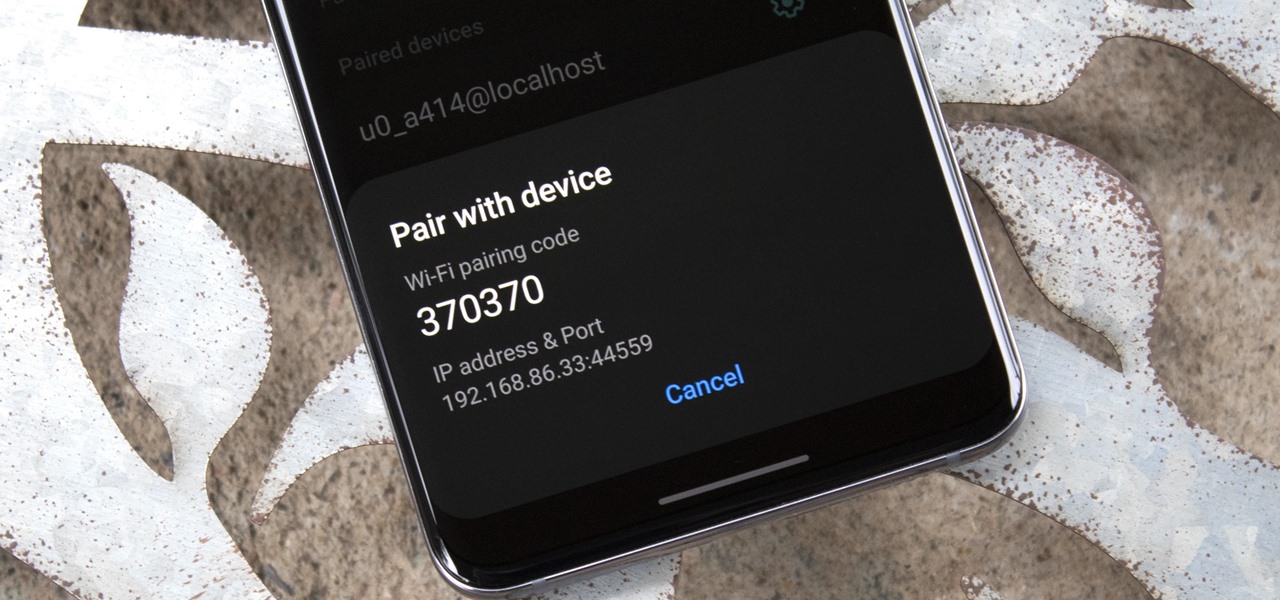
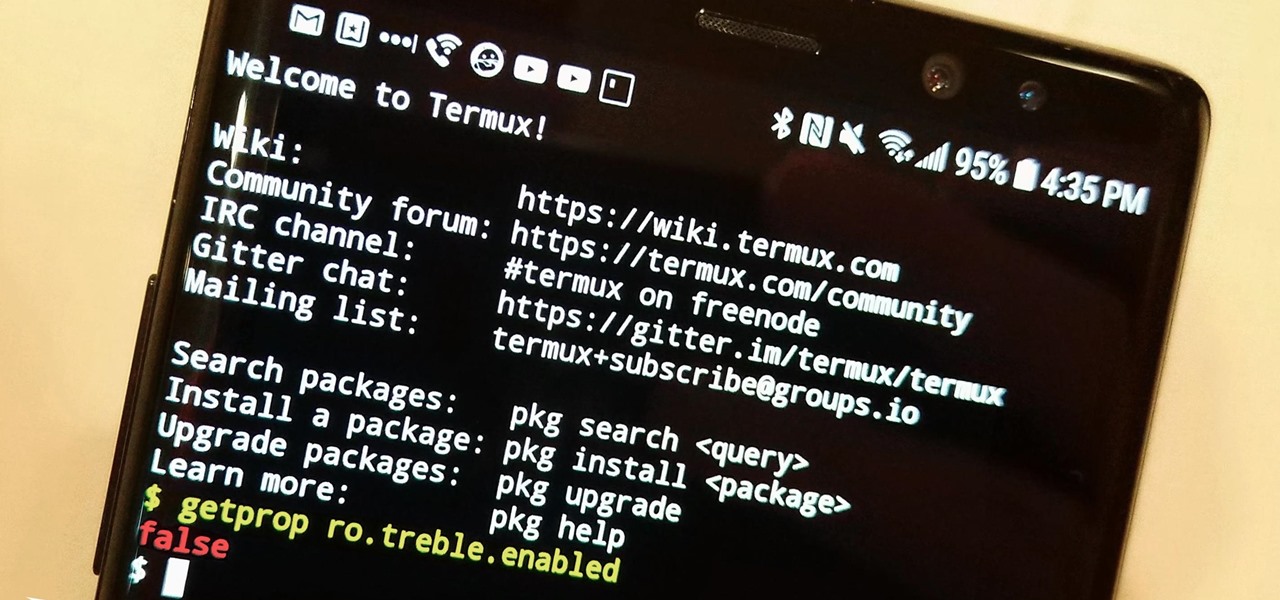
The Oreo beta updates for the S8 and Note 8 have been avilable for some time now. If you're interested in running Oreo on your Galaxy Note 8, you can check out our guide on how to do so. As we dig deeper into the updates, one question on the minds of Galaxy fans is whether or not the Oreo update will support Project Treble. Today, it appears we have an answer.

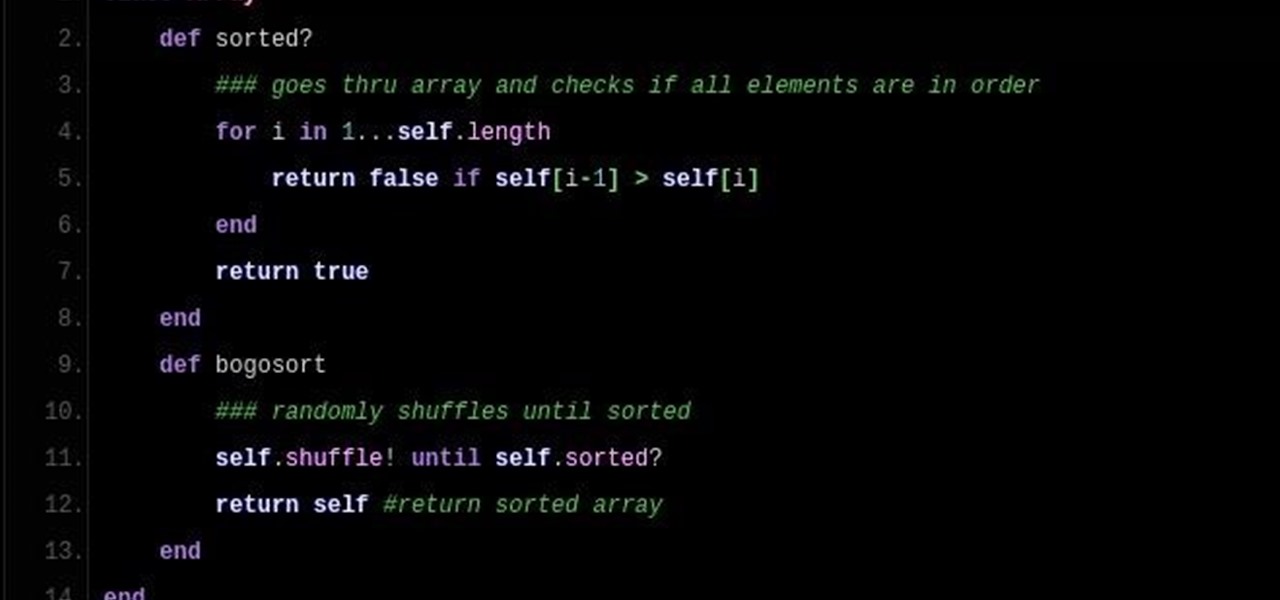
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

You know how sometimes you accidentally send a minecart shooting out down your tracks, and you can only watch helplessly as it fades into the distance? And then you know that you have to go find it and break it, so that it doesn't stop up your cart traffic on your tracks.

Assuming everyone knows of the recent "String of attacks" passed between Obama and Romney, I just want to talk about how useless this entire thing is. I'll try to be as un-biased as possible.

There's more than one way to get free credits and discounts in the Google Play Store for apps, games, books, movies, in-app items, and other Play Store content. You may know a few of them — but some of these may surprise you.

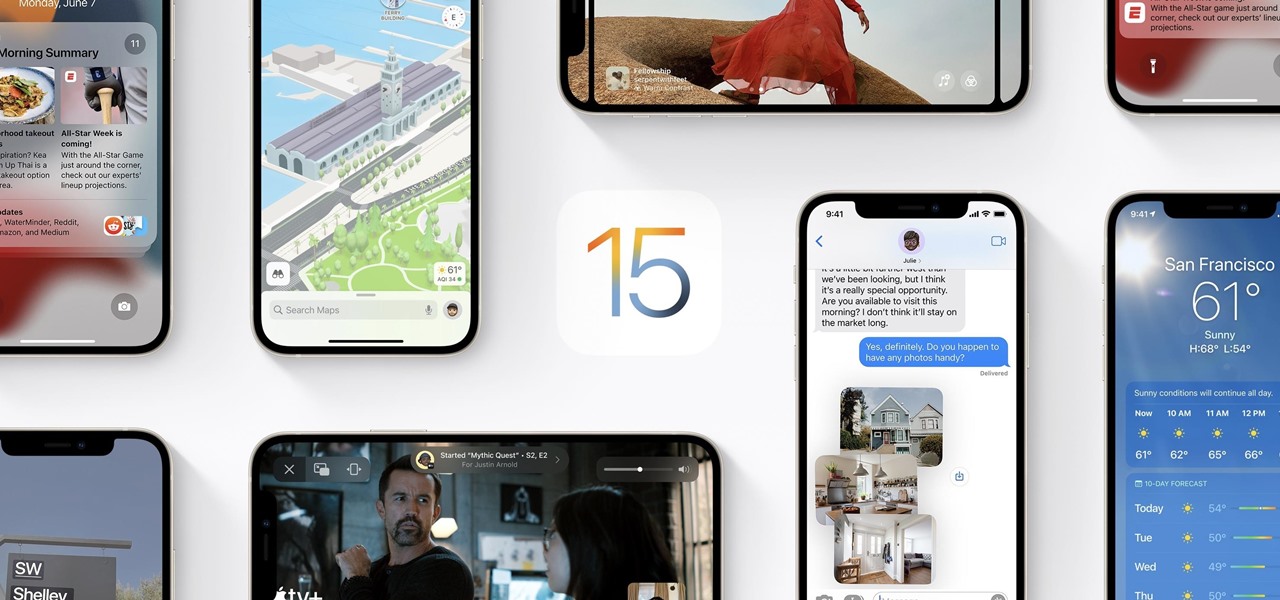
Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes.

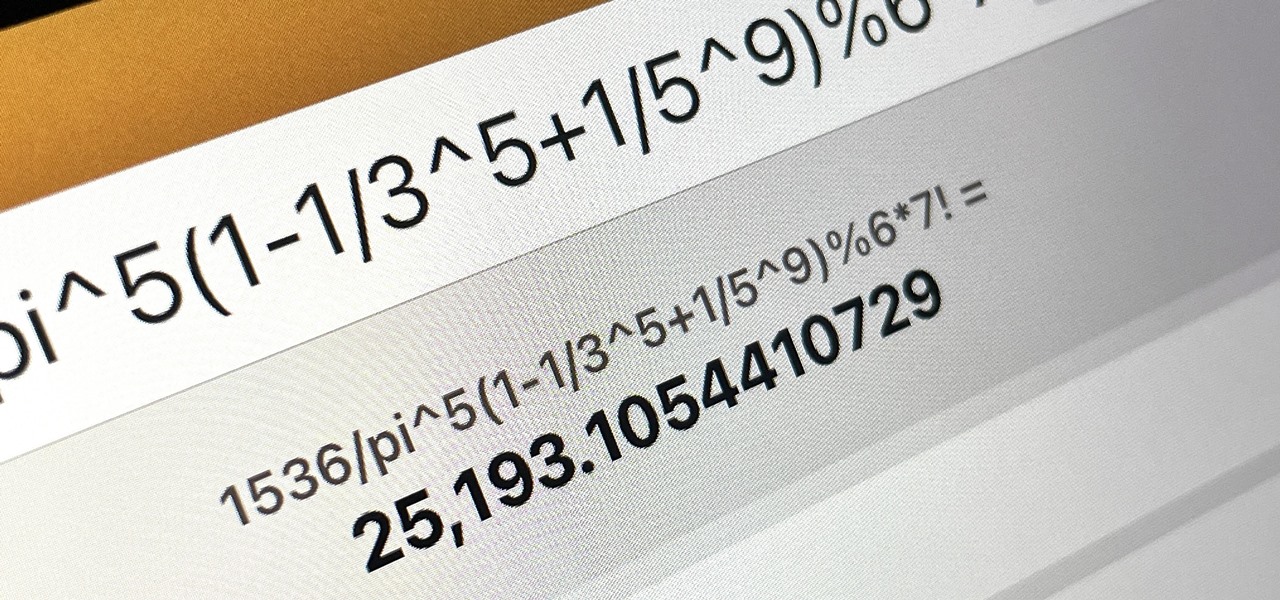
There is no iPad version of Apple's Calculator app (at least, not yet), so you won't find it on your Home Screen, in your App Library, or as a shortcut in the Control Center. But that doesn't mean your iPad doesn't have an official calculator.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.