Using breadcrumbs in the kitchen is the perfect way to add crisp and crunch to the usual salad, entrée, or dessert. As chef and media personality Mario Batali once said, "There's almost nothing I wouldn't put homemade breadcrumbs on."

We've all been there: facing a lengthy, complex word that ignores the phonics we were taught in elementary school, unsure of not only its pronunciation, but also its meaning. These words, from autochthonous to esquamulose, are both terrifying and impressive. After all, if someone knows how to use them—and even say them—they must be quite smart. Yet before you begin stuffing every email and presentation with verbose prose, you might want to reconsider what others perceive to be intelligent.

Welcome back, my nascent hackers!

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

One of the down-sides of international long-haul travel is layovers between flights in unfamiliar places. We have a flight to Europe this year via Guangzhou, China, and I've been putting together my notes on how to make the best use of 7 hours between flights, which I'd like to share.

Apple is very tight lipped about their products, and their iPhone is certainly no exception, but when products depend on global manufacturing, it's nearly impossible to keep good secrets contained.

Camping in the rain sucks. It's not enough to deal with your clothes and tent being soaked—it makes starting a fire nearly impossible if you're not carrying waterproof matches. You can buy them pretty much anywhere that sells camping gear, but if you've got regular matches and a candle at home, they're just as easy to make yourself..

If you've recently joined the ever-growing ranks of the cable cutters, you're far from alone. More and more people (myself included) are getting fed up with service providers' outdated subscription models and absurd pricing—and canceling their service.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

It's almost here. Another year has come and gone, and it's time to watch the Baltimore Ravens and the San Francisco 49ers battle it out in New Orleans for Super Bowl XLVII. For the truly football-obsessed, this Sunday is a day almost as exciting as Christmas. Personally, I just use it as an excuse to cook food that's way less healthy than usual since I never quite became a football fan (sorry, Dad).

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

Want to take vibrant photographs like this one? You won't find this filter in Instagram, and that's because it's a little more difficult than just slapping a digital filter on a solo photo. The extra RGB colors are created using a special strip device called the Harris shutter, invented by Robert Harris of Kodak.

Timely costumes for Halloween are awesome—especially really obscure ones—because they're indicative of social awareness. In 2010, I remember seeing several Chilean Miner costumes, which I thought were great. 2012 brings new stories, new characters and more importantly...new Halloween costumes.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

Skulls. What spooky Halloween décor or staging of Hamlet is complete without a skull or two popping up? For ghoulish special effect and/or setting a dramatic scene, skulls are absolutely integral. Well, with some artistry, hardware supplies, and a good dose of patience, you can create your own inexpensive prop skulls for use however you please.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

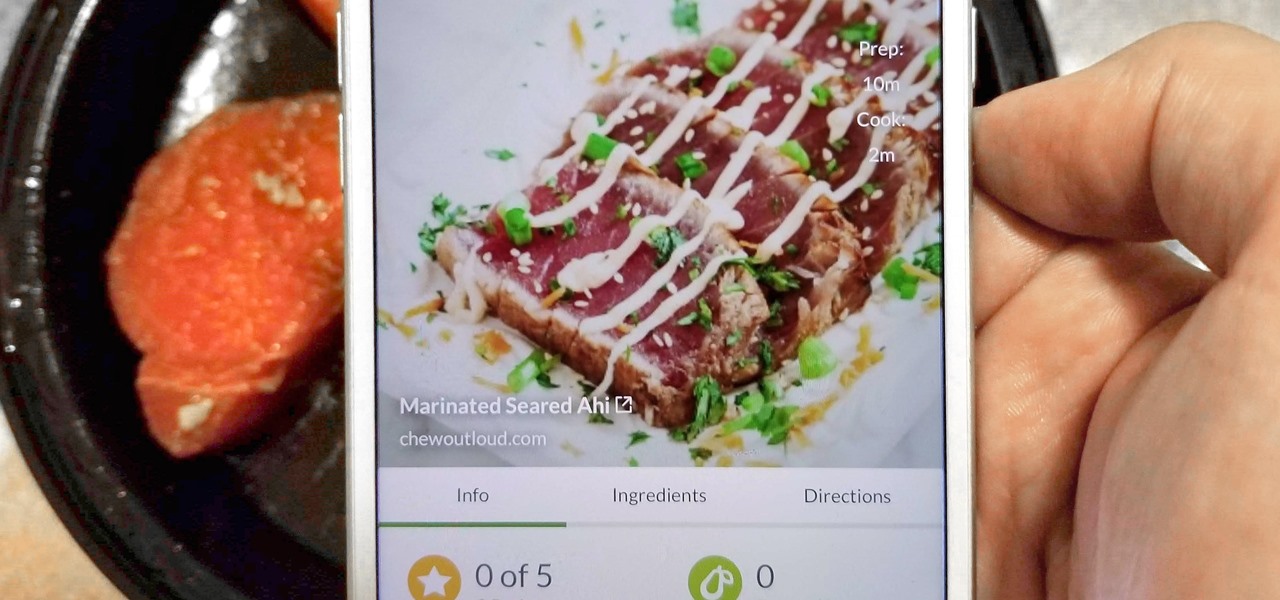
With Tasty dominating Facebook videos and online cooking flourishing, it can be cumbersome to keep track of all your recipes. Someone might send you something, and storing it in an app like Pocket is like jamming all your school papers in one folder — it just isn't practical. Fortunately, there's a better way to catalog your recipes so you can always have them on hand.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Being a city dweller does not mean you cannot save the planet — or your food scraps. Climate change and resource management are big issues. Composting in any size space is not only possible, but it gives you a chance to reduce greenhouse gasses and reuse food scraps. Right now, about 40% of all food in the US goes to the landfill. In addition to planning meals and using your food in creative ways to reduce the amount that goes to waste, you can compost.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

Humanity is standing on an infection precipice. As antibacterial resistant grows, we're running out of options, and a recent scary case of total antibiotic resistance is a frighting view of our potential future. In the end, it was septic shock that took the life of a 70-year old woman with an incurable infection. One of few such cases in the US, her death could nonetheless be the shape of things to come.

The food TV chefs prepare make our mouths water. From one scrumptious creation to another, they fly through preparation without frustration or error. They make us think we can do the same with similar ease and delectable, picture-perfect results. Some of us have noticed, though, that these TV chefs don't always adhere to the same safe food handling guidelines we've been taught to follow.

Juicing fruits and vegetables is very beneficial to your health. For some, it's a trend; but to me, it's a part of my morning routine.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Barbecue season: it's the perfect time to play with fire, produce your best burger ever (until next year, that is), and find even more ways to make beer a part of your daily life. However, even a grilling badass occasionally gets stumped by minor BBQ problems. No worries: We've got solutions!

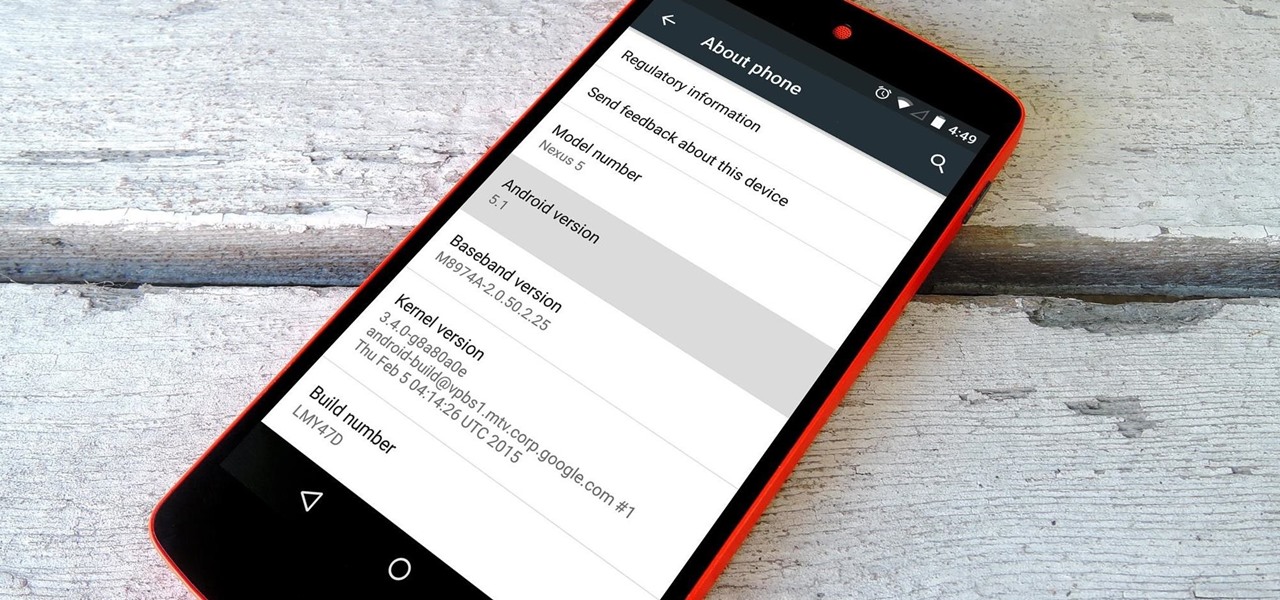
Google inconspicuously announced an Android update yesterday, and while it's not quite the overhaul that the initial Lollipop release was, version 5.1 brings plenty of bug fixes and new features.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

Fifty-four percent of Americans 18 and older drink coffee every day, and why not? With 100 milligrams of caffeine per six ounces of drip coffee, it's just the morning beverage to wake you up and kickstart your day. You can feel the caffeine surge through your body like the Holy Ghost, making you aware, focused, and ready for action.

If you have a good food processor or blender, there's no reason not to make your own nut butters, whether you like almond, cashew, sunflower, or the perennial classic, peanut.

Cheese is one of the most loved foods in the world, and there are hundreds of different types. Some prefer super expensive gourmet cheeses, others are fine with the cheaper processed stuff.

At one point in the '90s, about fifty percent of the CDs produced worldwide had an AOL logo. About fifty percent of the CDs in my home still have that AOL promise of 500 free hours on them. Though they never got me to join their internet service, I did get a lifetime supply of coasters. Thanks to the rise of high-speed internet access and bigger and better hard drives, there's no reason for companies to snail mail any more of those obnoxious plastic discs.

GarageBand can be used to podcast, blog and upload created music directly from the sofware itself. Upload a song created in GarageBand after watching these free videos on software plugin tips and general user tips.

Django is a powerful Python-based framework that makes creating complex, database-driven websites easy to build and maintain. The free, open-source platform emphasizes reusability, the "pluggability" of components through APIs, rapid development, and less coding.

The frustration of searching for the perfect image can be overwhelming. Then there's the issue of copyrights: Can you use it? Do you have to give credit? Are you allowed to manipulate the image?

The WordPress revolution has completely altered the way that people build and distribute websites. Instead of having to memorize endless lines of HTML and Java, both novice and professional web developers are now able to create incredibly detailed and responsive sites using a series of intuitive templates and plugins. And each new version of WordPress comes with an improved batch of features that make web-building even easier.

With the nation facing a shortage of ventilators for COVID-19 patients and no apparent ramp-up in the production of new ones, engineers, medical resistents, and do-it-yourselfers are sharing plans for homemade versions.