Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craigslist is also one of the most convenient places to buy and sell pretty much anything you can think of. I've used it to buy my bed, my old bike (which was stolen!), and my couch. And while Craigslist is great in many ways...

You would think that a video game involving teddy bears would be for young children, right? That is not the case with Naughty Bear. This video game isn't like those cute and cuddly Care Bears we all know about. It's about revenge. It's about "naughtiness". It's about teddy bears killing teary bears.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

Montezuma's revenge, the runs, the trots, or just diarrhea — everyone gets it sooner or later. What exactly is diarrhea good for, if anything?

Valentine's Day can seem like Singles Awareness Day if you're newly broken up, but that's all the more reason to treat yourself on this pink-and-red consumerist holiday. Whether you're happily single or bitter and bitchy, there's definitely something on this list of Anti-Valentine's Day treats to fit your mood. Remember: cake is still cake!

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

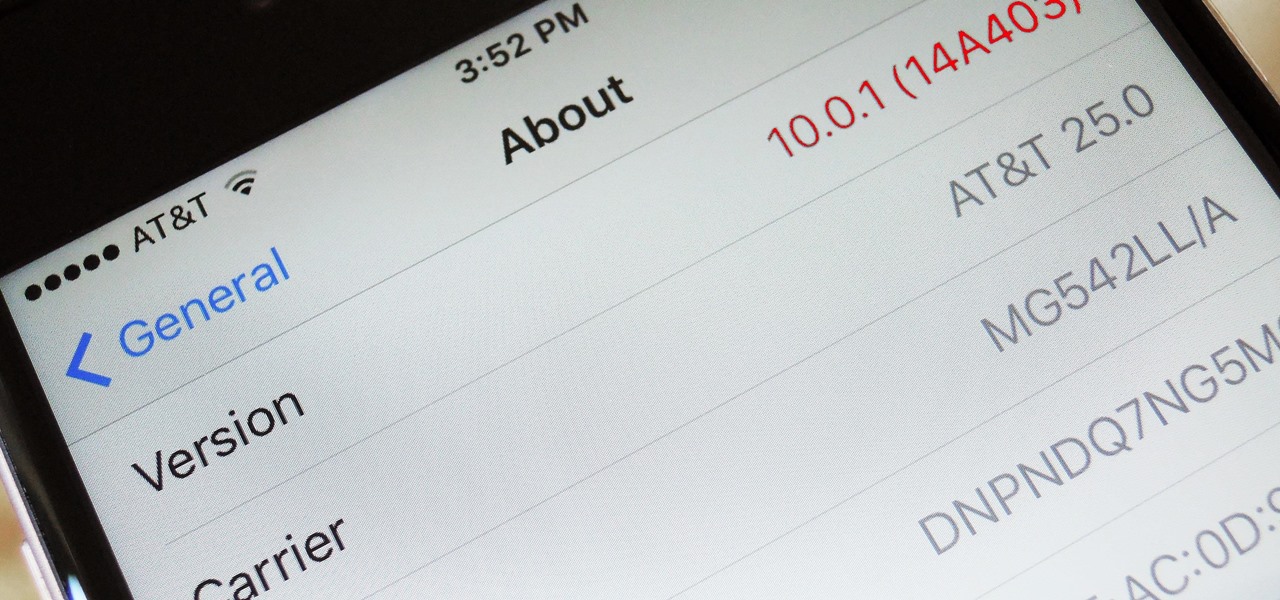
When a new version of iOS comes out, everybody gets caught up in the craze of finding features and playing around with new functionality. But this generally leads to a lack of coverage on the finer aspects of the update—things like bugs, minor tweaks, and pain points that users discover along the way.

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

When there's a crappy stock app you want to hide, the easiest thing to do is just bury it in the back of a miscellaneous folder. But what if there's an app you want to hide on your home screen that you actually use? For instance, what if you don't want everybody in eyeshot to see what banks you use, or don't want anyone to know about your "dating" apps or porn shortcuts?

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as gaming goes. Because of this, a lot of games once reserved for consoles and PCs have made their way to our smartphones.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Go to a place where they sell mattresses. Start bringing in equipment to make a porn. Make sure it's a gay porno.

Here is the movie trailer for "Dogs & Cats The Revenge of Kitty Galore"

The day of interactive porn has arrived, all thanks to Steve Jobs. The iPhone 4's new video-call feature, FaceTime, enables users to have live video chat sessions over a Wi-Fi network, via the iPhone's camera and screen. Unsurprisingly, the porn industry was immediately inspired.
The Afghan Taliban vowed Monday to exact revenge for the killing of 16 civilians, allegedly by an American soldier who went on a house-to-house shooting rampage Sunday in two villages near his base.

This is truly one of the most disturbing and extreme "pranks" we could imagine. Basically, this company claims to sell live pubic lice for you to give to someone as an extreme and ultimate revenge.

This is going to happen to Bam so don't tell him!!! For this to be the ultimate prank on Bam have his parents be in on it.

Revenge is sweet. If you don't have the time or the heart to torment telemarketers, put your name on the National Do Not Call Registry, at www.donotcall.gov. For more information, see "How To Stop Telemarketers Calling". Use this as inspiration for one of your April Fools Day pranks! Annoy a telemarketer.

Yes, I'm one of those annoying people who sign up just to promote their own game. I'll be brief. I turn famous novels into games. The latest is the Count of Monte Cristo, the classic story of revenge. Visit EnterTheStory.com for video, demo, screenshots, all the usual stuff.

Ok, so for this one its going to be on my friend Nathans cousin, Justin, once again. We mess with this guy sooo much ha. Read the whole prank, but it short, He thinks he's gonna be in an actual movie, but instead its a Jurassic Park themed gay porn shoot. So we're gonna tell him we're going to California to be in Jurassic Park 4(he'll believe it, trust me). On the flight we can even have a couple pages of a fake script to read. When we get there it'll be just like any other shoot or at least ...

Planning a trip to Japan? Your basic sushi etiquette isn't quite enough. You'll need to know the right things to say, the right way to kneel, and the right way to consume. Click through for AskMen's top 10 rules on authentic sushi eating.

First came the Rubik’s cube, a simple 3x3 puzzle. Then came Rubik’s Revenge, a 4x4 monstrosity. Eventually, the real whizzes attempted to conquer the V-Cube 6 and the V-Cube 7.

Turn the tables. Our buddy GreeenPro came up with this ingenious prank.

Food is the meeting place of left and right brainers: Culinary arts call for creativity, but is also deeply rooted in the What, Why and How of basic science—baking powder vs. baking soda, the rising of dough, the falling of a cake, etc. Below, two plays on left brain principles—the Möbius strip and the law of gravity—both executed with right brain flair.

Have someone pretend to be a house salesman who's showing some people around a house. On the outside everything will seem normal but as they walk into the house everything goes mad.

REVENANT n pl. -S one that returns 61 points (11 points without the bingo)

FRIDAY SEPTEMBER 24 Tonight one of the worlds most intense directors has a premiere of his new film.

You store everything on your computer's hard drive… precious family photos, your favorite music and video files, valuable financial information, and let's not forget about all that porn (just kidding). You can't back up your data when it crashes, so don’t wait another day to protect your hard-earned hard drive data.

Throw Knoxville in a makeup chair and age him to make him look older, put him in a Catholic priest outfit and send him out on the streets. Have hidden cameras follow him as he goes into porn shops, porn theaters, strip clubs, buys tickets to kids movies, goes to gay bars, reads a Playgirl in public places (bus stops, parks, book stores, coffee shops, etc.) walks around mens rooms and locker rooms, goes to playgrounds, takes pictures and video tapes men at Muscle Beach, etc, etc.