How To: Use Your Pixel's Power Button to Bring Up Google Assistant Instead of the Power Menu
There are many ways to access the Google Assistant on your phone, but Android 12 adds another one for Google Pixel models that may be the best way yet.

There are many ways to access the Google Assistant on your phone, but Android 12 adds another one for Google Pixel models that may be the best way yet.

You might think that you have your microwave all figured out, but chances are you don't know all of its secrets. Some microwave tricks are truly hidden; obscure information nowhere to be seen in the user manuals. Other tricks are hiding in plain sight, often overlooked or tossed to the curb because a microwave oven is so simple that instructions aren't needed, right?

When you can't touch the shutter button on the screen in the Camera app, your iPhone has another way to snap a picture or take a video — just press the Volume Up or Volume Down button. But when it comes to bursts and QuickTakes, however, things are a little bit trickier in iOS 13, iOS 14, and iOS 15.

As soon as you try recording a video in the Camera app on your iPhone, any music playing on your device comes to a halt. Apple Music. Spotify. Pandora. Tidal. Deezer. No matter what you're listening to, as soon as you switch to "Video" in the Camera app, the music will stop. However, if you want background music in your movie files, there's a workaround to avoid having to add an audio track in post.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

In a departure from Apple's newer iPhone models with Face ID technology, the 2020 iPhone SE goes back to the old days where the Home button ruled, and Touch ID was the biometrics method. But if you've never owned an older iPhone with a Home button, something as simple as shutting down and restarting the iPhone SE could elude you.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.
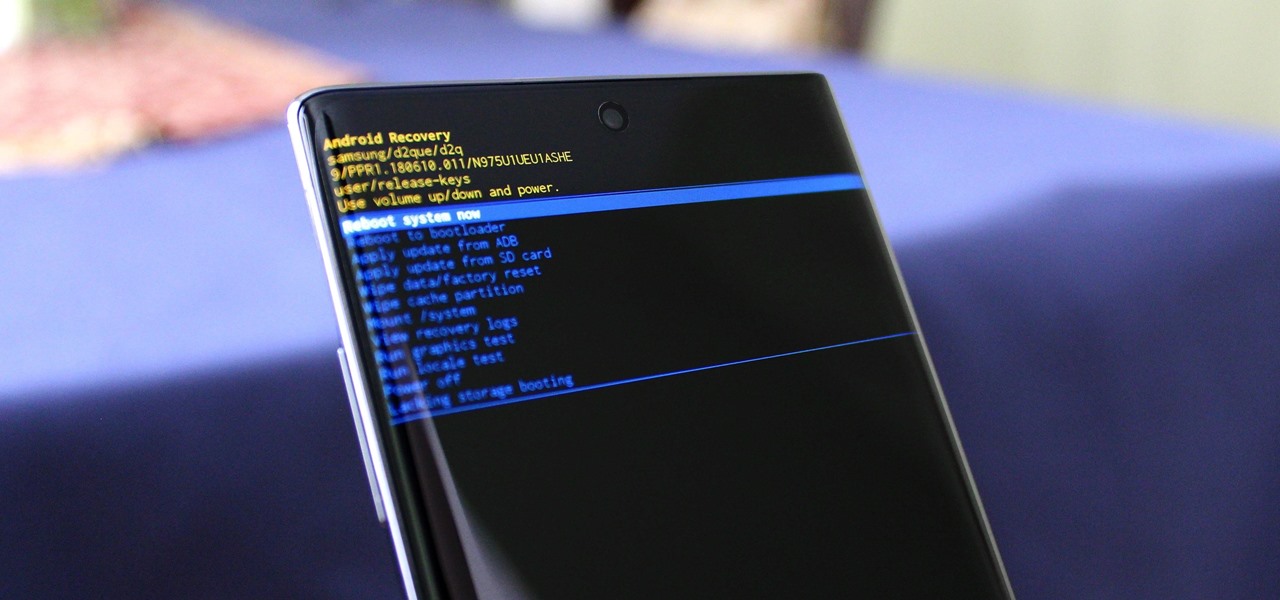
You can't call yourself an Android pro without knowing about Recovery or Download Mode. These menus are critical to do more advanced tasks on your phone, include sideloading software updates and un-bricking a device. But this year, Samsung changed the button combinations that will get you there.

After playing Mario Kart Tour for a little while, you'll notice it's a bit different from previous games in the series. The biggest change is how they've deferred to new players by automating many of the controls. But what if you want the traditional experience? We've got you covered.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

You may not want to disable notifications for the Mail app entirely on your iPhone since you could miss essential emails when they come in. But you can at least silence conversation threads on an individual basis. Doing so won't mute all conversations from the same sender, only the thread you select. Plus, it works for group email threads where things can get chaotic.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

If you use the mobile Slack app, whether for work, school, or play, you know that the background color in discussions for channels, threads, and direct messages is white and that most of the text is black. Unlike with the sidebar, there's no way to customize the colors that appear here, but you do have one other option: dark mode.
On Instagram, you can write text over any picture or video in your Story, but it may be hard to get your message across with a distracting background. Although there is a "Type" option for Stories, which allows you to write text over colorful gradient backgrounds, the selection is limited to just over twenty options, and there are no options for solid colored backgrounds or translucent overlays.

Instagram is all about the hook. If you want followers to stick around, you need to keep your content interesting and engaging. Rainbow text can really make your Stories pop, but it's not really an Instagram "feature," meaning it's not an easy task to accomplish. There is, however, an easy hack that takes all the work out of rainbow-colored text, making your Stories better overall.
Nearly a year to the day after the unveiling Magic Leap One, Magic Leap has dropped another update to the Lumin OS that runs the device.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

The Galaxy S9's Super Slow-mo feature comes packed with tools that help you tweak your slow motion clips like a pro. Among these is the ability to convert your slow motion videos into GIFs with a user-friendly interface. As a result, it's incredibly easy to go from recording to GIF conversion and on to sharing in a few taps.

When you receive a photo or video from a contact in WhatsApp, after you load it, it's automatically saved to your phone's local storage. That means all received content from WhatsApp is visible to anyone who gains access to your default photo gallery. Luckily, there's a new feature available for the Android version of the app that can prevent this from happening.
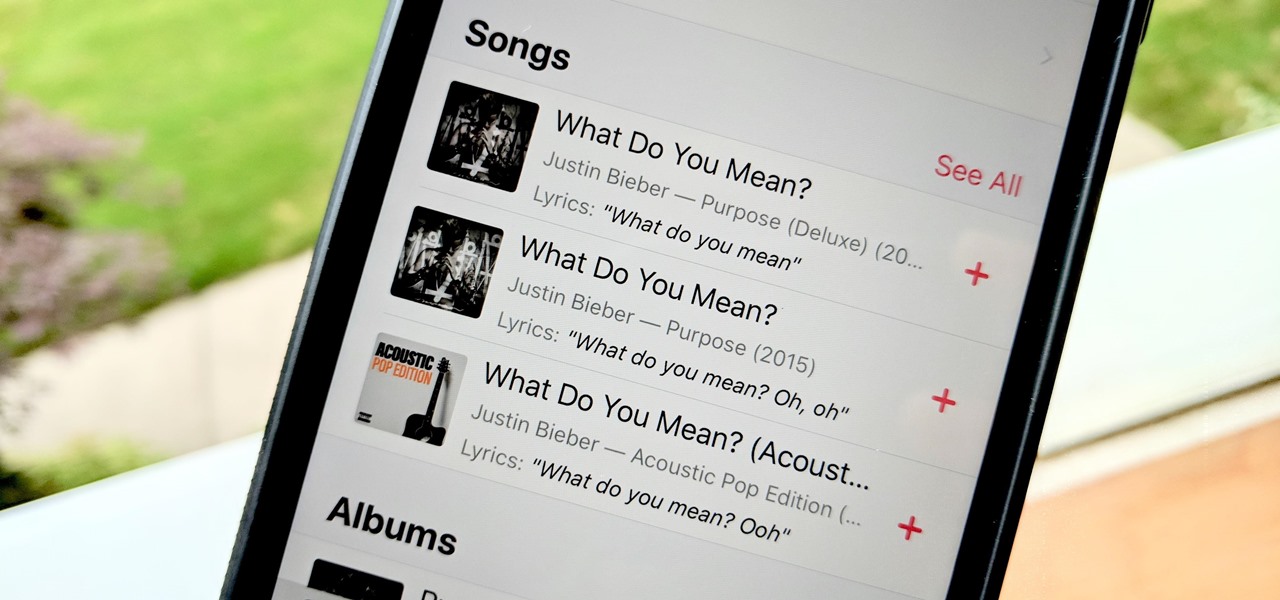
Has this ever happened to you: You're singing a song in your head and want to look it up on Apple Music but you just can't think of its name or even who recorded it? In iOS 12, if you can sing it, you can search for it, as the update lets you find songs in Apple Music by lyrics alone. It's like Shazam, only instead of identifying music by sound, it uses the lyrics in your head.

Ever since 2009, you could send a photo or video that you've already taken right from the Messages app on your iPhone. You would just tap on the camera icon next to the new message box, then choose either to take a new one or select one from your library. If you're running iOS 12, that's no longer the case, but that doesn't mean the capability is gone entirely.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

In the wild world of Snapchat lenses, this week was an especially good one for cool effects. Lens-crafters (really hoping I can get that name to stick) have gotten a lot better at making non-gimmicky lenses that allow you to interact with them in new and unique ways.
When you've exhausted your data plan, streaming isn't an option unless you want overcharges. While Apple Music makes it easy to download songs for offline listening, you need to add the music to your library first. This creates an extra step in downloading music, but it doesn't have to — Apple Music lets you automatically download any song, album, or playlist that you add to your library.

The augmented reality business was all about audiences this week. Vuzix looked for an audience with the Supreme Court of New York regarding a defamation lawsuit against an investor. Magic Leap held an audience with royalty, showing off the Magic Leap One in a rare public appearance. And Snapchat wanted to remind its consumer audience of all the things its camera can do.

Business cards are a great way to keep tabs on the contacts we network with. So why shouldn't our smartphones make them even more useful? Enter Google Lens, which will help you save, search, and expand on the contact information found on all of the business cards you've collected.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.
Many OEMs create skins that run on top of Android to differentiate themselves from their competitors. One example is the LG UX 6.0+ found in the new LG V30, which is Android at its core, but improved upon by the addition of unique features. One such feature is the ability to change the buttons at the bottom of your screen.

Directive Games received the enviable honor of unveiling their ARKit game, The Machines, on stage as part of Apple's iPhone launch presentation.

The fact that the iPhone X, XS, XS Max, and XR don't have Home buttons means that you'll need to learn a few new gestures. There's the home gesture, the multitasking gesture, and even a new way to access Apple Pay, among others. But one less-common action that has issues due to the lack of a Home button is taking a screenshot.

HBO Max's watchlist, dubbed "My List," is a great tool that lets you collect and sort the video content you're interested in. That way, you don't need to sift through HBO Max's enormous catalog every time you open the app — just open your personal list of saved titles and start binging.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

With so many apps being cloud-based, cached data has started to become a problem. This is particularly true if you're low on storage, so developer Dhi decided to do something about it.
Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.