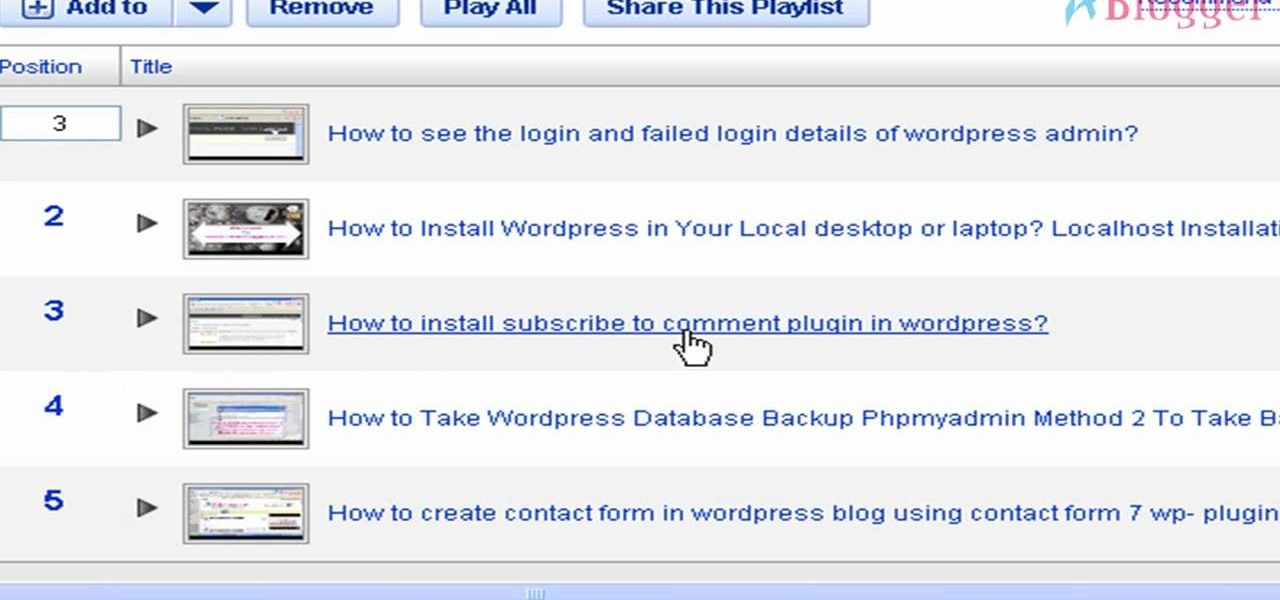
Once you have created a YouTube playlist on your YouTube channels, there's things you can do to customize it, like rearrangement of the uploaded videos. Reordering and rearranging the videos in your playlist is easy, so if you don't want your uploads to appear in reverse chronological order… you want your own order… watch this video to see how.

After you have mastered going forward and forward gliding you may want to expand your skill set and start skating backwards. You will use a simple undulating motion that will allow you to propel yourself backwards.

This video tutorial shows how to execute a yarn over with the left hand. Great for lefties to learn how to knit a yarn over stitch, without having to mentally reverse the directions.

This video will show you how to take back knit stitches one stitch at a time. This is handy for when a mistake is made but isn't caught for a few stitches and then need to 'reverse' a little. This technique is designed to be used for a small number of stitches, not for many many rows of knitting.

Jeff Schell shows you how to create a spinning headline or front page of a newspaper. You'll see how easy it is to build this special effect for any type of image or clip using a pair of rotation keyframes and scale keyframes, and by specifying your keyframes in reverse order.

If you're in the market for a new smartphone and want nothing but the best of the best, now's the time to act. Some of the greatest phones money can buy are being released as we speak, while others are still in their prime and will continue to be for most of 2024. Whether you want an iPhone or Android, we've rounded up the best picks you have to choose from for top-of-the-line specs and advanced features.

You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Using a technology we like to call "Hive Computing," several Android apps allow you to contribute idle processing power to help further scientific research. This basically means that when you're not using your phone or tablet, it can join forces with other idle devices to form a supercomputer that scientists can use to potentially make a world-changing breakthrough.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

The music and sound effects that play in the background of any videos you edit helps set the tone, so it's essential to get it right. Enlight Videoleap, an extremely powerful and popular mobile video editing tool for iOS, lets you quickly and easily add audio from your iPhone and the cloud, but things can still get a little confusing when you have a timeline full of clips.

Stories are everywhere in social media today, but that wasn't always the case. In 2013, Snapchat introduced the world to these temporary windows into our daily lives. Since then, stories have infiltrated other popular apps. However, to stand out, you can't solely rely on the app where the story will be posted. Instead, you need a suite of apps that can turn your story into something special.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

In this video, we learn how to use Visual Basic to convert temperature units. To start, make two command buttons. After you have created these, make sure you label them. The first command button should say "celsius to fahrenheit" and the second should say "fahrenheit to celcius". After this, make one text box and one label box. Now you will convert celsius to fahrenheit using the formula "F=(9/5*C) + 32". and you will be able to use this to convert temperature units. Save this and use it for ...

In this video, we learn how to create an easy origami paper rose. First, take a piece of paper and fold it into a square. After this, unfold it and then reverse the fold the opposite way. Now, take the middle of the paper as you are folding and make a square out of it. Fold down the flaps from the middle down in the front and the back. Next, flip the paper over and push down all the creases. Then, fold the paper into a triangle on all sides and push the creases down. After this, pop up the mi...

In this video, we learn how to replace the exhaust manifold in a Jeep Cherokee. First, take the bolts out from the collective and set aside. Next, loosen up the collector and take out the bolts that are holding the manifold on. Then, remove the manifold from the vehicle. After this, install your new manifold in the same spot your other manifold was just in. Your next step will be to place the other parts back on that surround the exhaust manifold. Make sure all bolts are on tightly, then go i...

In this tutorial, we learn how to lose belly fat with repetition for the lower abs. The first exercise you can do is a reverse curl. You will start by laying down flat on the ground with your arms next to you, and bringing your legs into the air, raising your butt in the air. The next exercise you can do is side crunches. This will work your side abs and your obliques. You can do this on a yoga ball by crunching sideways with your arm on your head. You can also do leg raises using a yoga ball...

This video tutorial is in the Computers & Programming category which will show you how to change the keyboard on an HP Pavilion laptop. First remove the battery and then remove the 6 screws in the battery cabinet. Now remove another screw as shown in the video. Open up the laptop and remove the panel located on top of the keyboard. Now remove the screws that hold the keyboard in place, slide out the ribbon connector and take out the keyboard. Then take the new keyboard, slide in the ribbon co...

In this video tutorial, viewers learn how to cure slices by rolling the wrist. Some people hit slice shots because they strike with a underhand or reverse position. The correct way is when your hand comes back for impact, it should rotate into position with the back of the left hand facing the target. If the back of your left and is facing anywhere else, the ball will slice. A drill that users can do is to use their wrist watch as a guide. Start with it at a 45 degree angle. When you swing, i...

This is a video tutorial showing you how to walk through Poppable Cascade levels 1-20.The main object of this game is to pop all the balls that are there in the screen. The way you can pop the balls is if the balls of the same color are touching each other. Once that happens, click on that set of balls and they shall pop. In some levels, there are glass balls. These balls can be popped individually. A rainbow-colored ball can be popped with balls of any color. There is also a reverse gravity ...

Find a nice, heavy and soft mango. Inside the mango there is a large oval pit. By viewing the shape of the fruit you will be able to tell the location of the pit. Set the mango on a cutting board so the pit is vertical. With your chef’s knife cut down the side of the pit and again on the other side of the pit. With the two halves facing each other, take the knife and cut a criss-cross pattern into the meat of the fruit. Make sure you do not press your knife so hard that it cuts through the ou...

Do you need to replace your Gearshift knob? Richpin shows a very quick method to remove the gearshift knob from Saturn S series. Pull the hand break on. Place the gear into 2nd, 4th or reverse. Holding the top of the gearshift, take a rubber mallet and give the knob a few taps underneath until it comes off. To replace the knob, place the knob onto the gearshift and tap it a few times until it is firmly in place. This very short video shows how simple it is to remove your gearshift know.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

People infected with HIV take many different types of pills every day to decrease the amount of virus in their body, live a longer and healthier life, and to help prevent them from infecting others. That could all be in the past as new clinical trials testing the safety and effectiveness of a new type of treatment — injections given every four or eight weeks — look to be equally effective at keeping the virus at bay.

As a side scrolling game, performing various jumps in Super Mario Run on your iPhone or Android is as vital as eggs in a breakfast buffet.

The internet has officially been taken over by GIFs—they're everybody's favorite method of communication these days, and nary a meme would exist without them. But even with the abundance of GIF-sharing websites, and even GIF keyboards, we're still a bit lacking in regard to creating GIFs on a mobile device.

A video showing what is alleged to be the new Apple iPhone 7 has appeared online. The uploader of the video claims that it was shot on one of Foxconn's assembly lines.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

If somebody really wants to gain access to your iPhone, they'll get in. Phone thieves (and mischievous friends) can easily figure out your passcode just from looking over your shoulder or tracing over the oily smudges on the screen. And if you're using popular passcodes, birthdays, and addresses on your iPhone, you might as well disable lock screen security entirely.

This is a tutorial how to make an easy ZigZag Macrame bracelet. You can use it as a friendship bracelet. Before you start you should know the basic macrame knots. There are 2 types of knots, the double half hitch and the reverse double half hitch. These knots are very easy to make. Don't worry and let's go make these Zigzagging waves :)

Cars are quite different than they used to be. Sure, modern cars have some cool things, but repairing them are becoming difficult. Even simple things like changing a headlight bulb.

War leaves a lot of stuff behind. Torn families, delegitimized institutions, mass graves, and unexploded ordinances litter the post occupation landscape. Whether or not you have driven the imperialist out, or are still in the phase of armed resistance, you will need the ability to safely diffuse bombs. My bomb defusing Silvia-bot can do it all. She can catch grasshoppers, cut wires, collect samples, tase enemies and even play chess! Materials

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

In Telegram — as with all instant-messaging apps — threads and conversations can pile up quickly. But you don't need to stare at all of your open chats on the main screen of the Android and iOS app. Instead, you can archive any conversation you like, keeping your main chats view relevant to your day-to-day communications without needing to delete any for good.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Whether inappropriate or unimportant, some emails don't need to be viewed at a certain times of the day. For example, you might not want to see any personal emails during work hours. By default, Gmail will notify you of all emails that hit your inbox, but fortunately, there's a feature that can automatically hide certain emails and prevent distracting notifications.