Apple gave us the ability to invert colors on the screen a very long time ago. Then they gave us grayscale mode in iOS 8, Night Shift in iOS 9, and the red screen filter in iOS 10. While the long-awaited "Dark Mode" finally appeared in iOS 13, iOS 11 and iOS 12 both have a decent placeholder for it you can use on your iPhone.
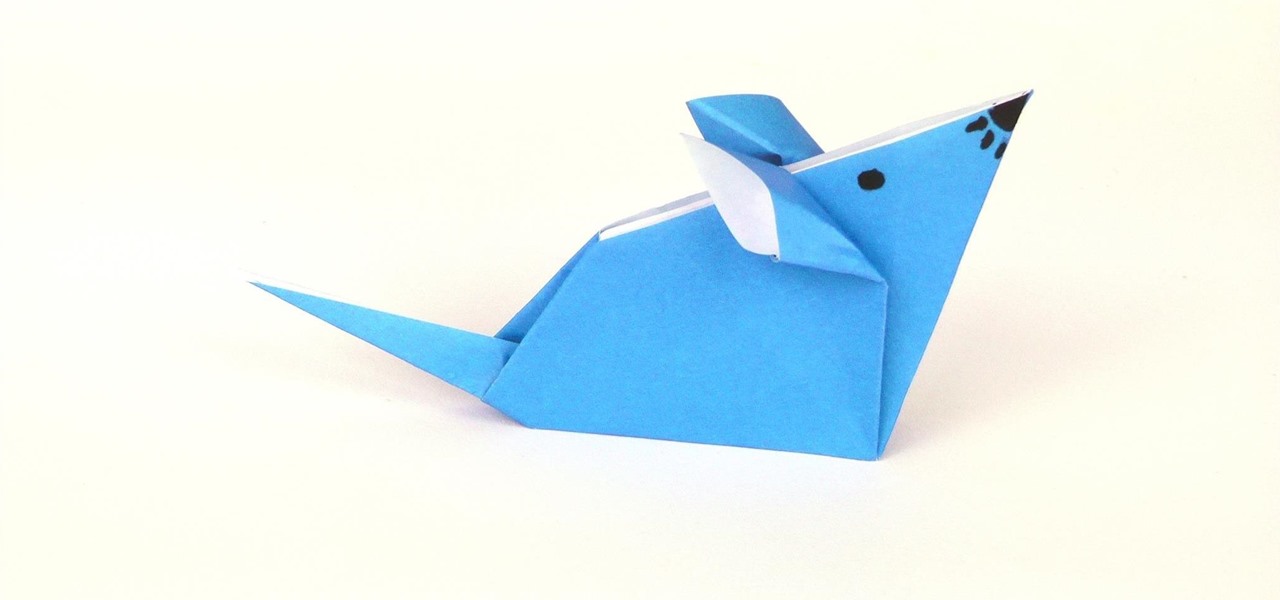
This tutorial teaches you how to fold an origami mouse with an ordinary sheet of paper. This model is suitable for beginners and children. Origami is great for small kids as the only material needed is paper, no scissors or glue that could do harm!

In this video we learn how to change a flat tire. If any tire of the car is flat you should not drive it further as it can be dangerous. Hence you should immediately bring your car to a side and start off your hazard button. Next you should take out your jack and put it in the right position below the car so as to lift your car and enable you to take the flat tire out. Once the tire is lifted above the ground, take out the spanner and unscrew the tire screws. They might be very tight so you w...

Many of the iPhone 15, 15 Plus, 15 Pro, and 15 Pro Max features were carried over from last year's models. Still, quite a few capabilities are exclusive to the 2023 lineup, and some may be worth the upgrade.

Apple Maps keeps getting better and better for all the hikers in the world. The latest update gives you access to thousands of detailed trail maps within U.S. national parks and topographic views, but it also lets you create your own walking and hiking routes.
Following someone on Twitter is an investment. You virtually agree to have their opinions, tirades, and hot takes spewed across your timeline. It can get annoying real quick if they're known to post controversial comments periodically. However, there are other ways to stay updated on someone's tweets without you having to hit the follow button and go all in.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Google Lens is a fantastic addition to Google Photos for Android and iOS that allows your smartphone to identify a number of things in your pictures, like landmarks and contact info. Using this power, you can even find out how to buy almost any product you've taken a photo of — you don't even need the barcode.

Mobile World Congress 2018 is here, and with it, Samsung has officially announced the highly anticipated Galaxy S9 and S9+. While we already knew much about the new phones, Samsung's presentation officially filled us in on what to expect from the S9's cameras, including dual aperture, two cameras, and super slo-mo.

The trick in the video is that the magnets are made of a conducting material and they connect the battery terminals to the copper wire, so the battery, magnets and copper wire make a circuit that generates a magnet field just in the vicinity of the battery. The geometry means the two magnets are automatically at the ends of the generated magnetic field, where the field is divergent, so a force is exerted on the magnets.

Now that Hangouts is Android's default messaging app, it's given us a lot of cool new features. A bouncing ellipsis lets you see when the other party is typing, and an indicator shows you whether they've read your message or not. You can even answer the age-old question of "Where you at?" with a tap of a button, sending a map of your location.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities. But don't wait—start submitting your own projects to the most appropriate World now!

Video: . Recycle your hard drive into a hidden flash memory device that only you know how to turn on and use in secret. This DIY hack project allows you to recycle your broken hard drives back to life and turn them into something useful.

With portable devices being a necessity in modern everyday life, they may be subject to overuse, improper charging, or normal wear and tear. For those people who carry around their smartphone or iPod with them all of the time, how many times have you been out and about just to have your portable device die on you?

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

It takes talent and training to drive a semitrailer. See if you have what it takes to operate one of these rigs on the open road.

With the Kodak Zi8, the power to capture razor-sharp, full 1080p HD video fits in the palm of your hand. Its easy, one-touch operation and incredible versatility make it the perfect camera for beginners, experts, and everyone in between.

A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it comes to helping you stay fit.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

To shine light on the future of the relationship between humans and viruses, a team of researchers from the University of Oxford looked into the dim and distant past.

The presence of certain bacteria can indicate whether the vaginal tract is healthy or not. It could also impact the likelihood of acquiring certain sexually transmitted diseases, like HIV, a new study suggests.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Two years ago, driven by a good friend of mine i decided to give it a try on timelapse photography. I had a DSLR camera but didn't had an intervalometer, so i assembled a small electronic circuit on top of an Arduino Uno, made some basic code and did my first timelapse movie. The result was awful, but for some reason I was hooked.

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

I love making beeps and bloops with the Arduino pitches library, but sometimes archaic 8-bit tunes just don't cut it. Whether you want your robot to terrify your enemies with a demonic synthetic voice, you just need a pocket boom box on the go, or you want to a miniature guitar amp, a simple LM386 amplifier can crank up those signals loud enough to play through any speaker.

The Galaxy S20's Wireless PowerShare is a must-use feature. With even the base model packing a 4,000 mAh battery, you have more than enough juice for all your Qi-enabled devices. The default settings make it so that in certain situations, you may have to choose between your phone or wireless earbuds, but you can change that.

Samsung simplified the interface in its Camera app for the Galaxy S20. It's easier to use for the most part, but now you have to go digging to access certain camera modes. To make up for this, One UI now lets you rearrange the tabs in the Camera app.

Is it just me, or are the thumbnail in the Samsung Gallery app a bit small? I spend quite a bit of time looking through rows of images, one at a time, to find the right photo. Wouldn't it be so much easier if the thumbnails showed the entire image instead of a cropped square? Well, there's a way to do just that.