Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Normally, office supplies and food don't mix, but you can use a paper shredder to make fresh pasta in your very own home (...or office). In other words, you don't have to buy a bulky and expensive piece of equipment to make fresh pasta. If you already have a paper shredder, you can simply feed pasta dough through it for perfect tagliatelle noodle strips that will taste far better than anything you can buy at the store. Step 1: Clean Your Machine

There's nothing more jarring than the sound of your morning alarm. Even hearing it on others' phones, hours after your own abrupt wakeup, can cause you to flinch in fear. Though we depend on that shrill sound to get up each morning, it's actually better to wake up naturally—so don't even think about hitting that snooze button.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

If you're one of the lucky people who received the gift of terrible eyesight from your parents at a young age, chances are you ate an awful lot of carrots growing up. Though carrots are one of the top vision-boosting foods, they don't offer fast results.

Bottled water is a rip-off. Not only is it pretty much the same stuff that comes out of your tap for free, but plastic bottles are rarely recycled and thus account for a huge amount of the waste that's overflowing our landfills. Next Up: Water Bottles You Can Eat

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

Automation applications bring the future a little closer. If you've seen Minority Report or other futuristic sci-fi movies, the intrigue of having your electronics work independently is something we can all appreciate.

There's no reason to wait for Halloween to play with dry ice. It definitely creates a creepy fog-like effect when you add a little water to it, but there are some other really cool things you can do wit dry ice. Here are just 5 non-Halloween ways to use dry ice for tricks or pranks.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

I love robots. They have the potential to evolve into Asimovian destroyers of the human species, but have only just mastered the art of cleaning my rug. They have an ever increasing cool factor and a growing number of cheap and simple components that let the hobby roboticist reach for the burning miasmas of plasma. But to get to the stars, we need to start with the basics.

If there's anything we've learned during 2020, it's that working and learning from home is going to shift the way we do business. With Microsoft announcing that its staff will be allowed to permanently work from home, expect more businesses to follow suit.

The modern remote workforce faces many challenges, but perhaps none is greater than organizing calls and syncing tasks. Many platforms are convoluted and difficult to manage. Team members get bogged down by administrative tasks instead of staying productive.

Apple always finds a way to sneak in tiny, inconspicuous features that improve the iPhone experience. And with iOS 14, there's a hidden, unannounced gesture that makes it possible to navigate apps and menus faster than ever before.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Apple's Mail app has always been a stylish yet simple way to check and send emails. Third-party apps up the ante with powerful tools and features to help keep junk and spam mail out of your eyesight. But with iOS 13, you don't need them since Apple gave the Mail app some much-needed superpowers. One of those being the ability to block senders from emailing you.

Samsung has just announced the Galaxy Note 10 and 10+. These are the latest and greatest from the largest smartphone OEM in the world. Plenty of numbers and specs have been thrown your way to showcase how good the Galaxy Note 10 is, but we wanted to simplify all this for you and key in on the most important things.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

The great thing about competition is it drives innovation. But when a company tries to one-up its competitor, it's not always with something brand new. Sometimes, one party will draw heavy inspiration from the other — but hey, it's still all good, because the consumers benefit either way.

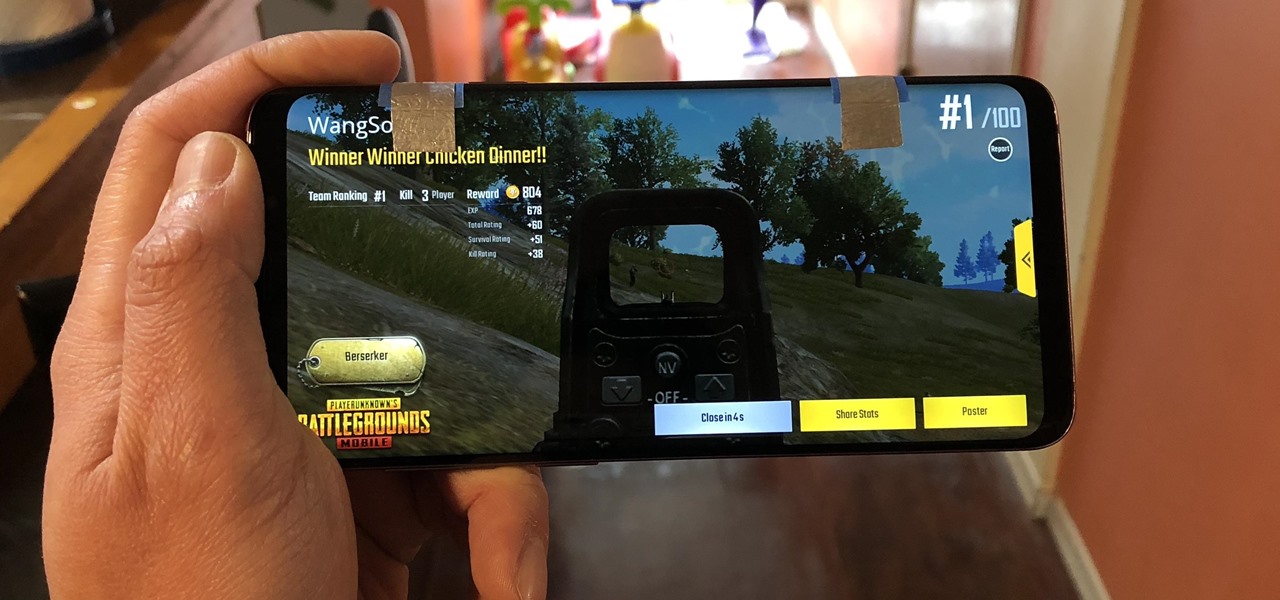
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's not exactly easy with a touchscreen.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

Google just bought a huge chunk of HTC for $1.1 billion. They're bringing in around 2,000 employees, mostly from the hardware division, and these folks will presumably work under hardware chief Rick Osterloh. There's a massive patent portfolio involved, too, so stop me if you've heard this before — Motorola, anyone?

On the airplane, in the middle of cold and flu season, your seatmate is spewing, despite the clutch of tissues in their lap. Your proximity to an infectious person probably leaves you daydreaming (or is it a nightmare?) of pandemics and estimating how likely it is that this seatmate's viral or bacterial effusions will circulate throughout the plane and infect everyone on board.

When you have an infection, a doctor prescribes antibiotics to make the bacteria that causes it disappear. Sounds like a good idea, but the disappearance of microorganisms that have inhabited humans for millennia could be driving rising numbers of serious illness and debilitating conditions.

Young girls, especially those who live in areas where HIV is epidemic, like sub-Saharan Africa, are particularly vulnerable to becoming infected with HIV. A vaginal ring containing the antiviral agent dapivirine has been shown to decrease the chance of developing HIV-1 in adult women over 21 and now in the first step for use in adolescents, the ring has been shown to be safe and well-tolerated in that younger age group.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

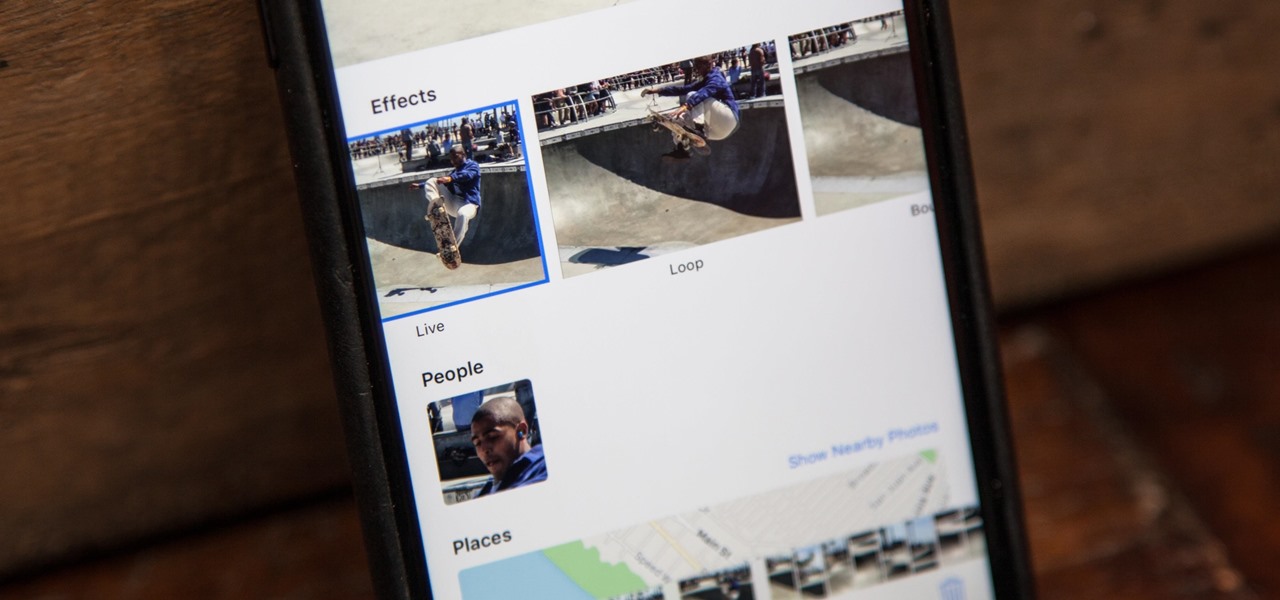
When Apple first introduced Live Photos in iOS 9, it was a big hit for those who had 3D Touch devices — but one thing this cool feature was sorely missing was editing options. Thankfully, Apple has fixed that in iOS 11 by turning Live Photos into a complete package with editing tools and new effects right within the Photos app.

Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.