It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

A few years ago I went hog-wild trying to achieve a zero-waste lifestyle. I didn't succeed, but the experiment taught me that we throw away things we could—and should—be using more.

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.
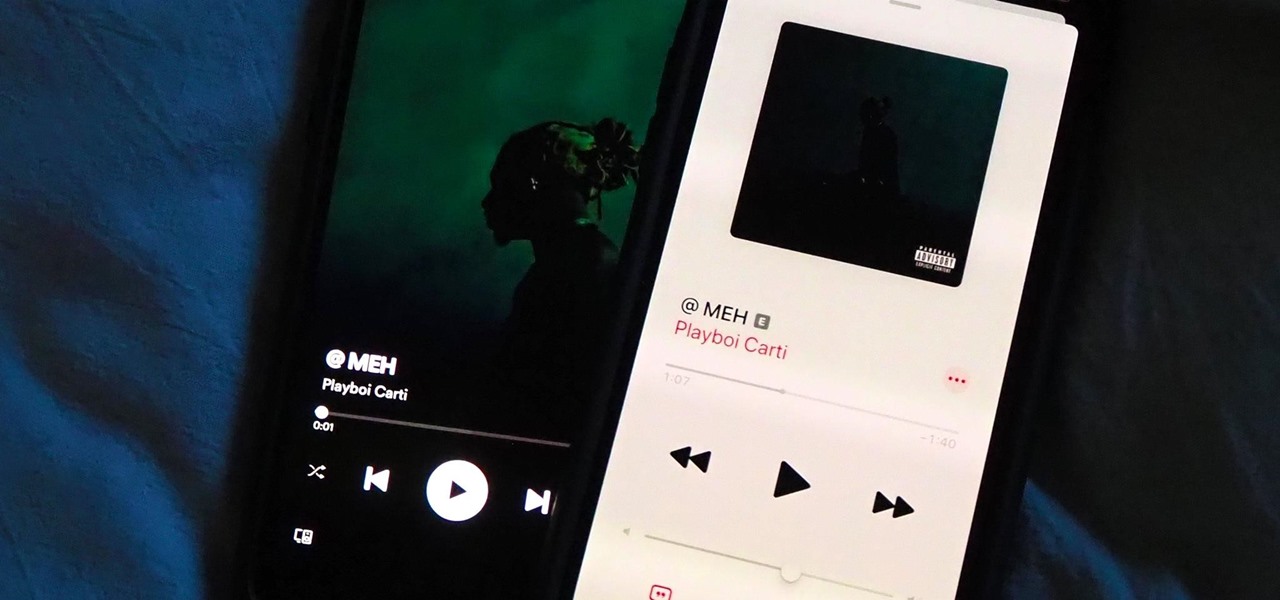
To share a song or album to family and friends, it's as easy as copying its link in the app and pasting that into a message. However, not everyone uses the same music streaming service, so a link to an Apple Music song won't do a Spotify, Tidal, Pandora, Deezer, or YouTube Music subscriber any good. If you're on an iPhone, though, there's an easy way to convert links from one service to another.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

So you've been playing Call of Duty Mobile for some time but can't seem to get MVP at the end of the battle. Well, since the game is a competition of players and bots, you're in an uphill battle. But you don't have to languish at the bottom. With the help of these tips, you might just nab your first MVP.

Many people don't realize much better audio can sound on their phones. While it's solid to begin with, Samsung has included several options in the Galaxy Note 10+ that will upgrade your listening experience to profound status.

The hugely successful S10 series of flagships may be a tough act to follow, but Samsung has proven that it's up to the task with the Galaxy Note 10. The latest phablet bearing the Note name is the first of its line to come with an even larger variant, and boasts an eye-pleasing design with impressive performance to boot.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

One feature in iOS you're likely underutilizing is 3D Touch, a highly useful, unique tool for iPhones ever since it first appeared on the iPhone 6S. Apple's pressure-sensitive interactivity gives iOS an extra layer of functionality, which can be clearly seen across the entirety of your device. From the lock screen to the home screen to the apps in between, there are plenty of ways to use 3D Touch.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Word games can expand your vocabulary skills in all sorts of exciting and creative ways. Because of this, both the iOS App Store and the Google Play Store are awash with word games, making it hard to differentiate between good and bad titles. This is especially troublesome if you're looking to purchase a game, as everyone hates to waste hard-earned cash.

Since its debut, retro thriller Stranger Things and its characters have become ingrained in our popular culture — especially the telekinetic Eleven. For cosplayers, it didn't take long before they grabbed their boxes of frozen Eggo waffles, blonde wigs (or bald caps), and pink smocked dresses to transform into El herself.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

It's Earth Day, which means that nonprofits, individuals, and brands are making a concerted effort to raise awareness of environmental issues and how to change behaviors to reverse impacts of pollution, deforestation, and suburban sprawl, among others.

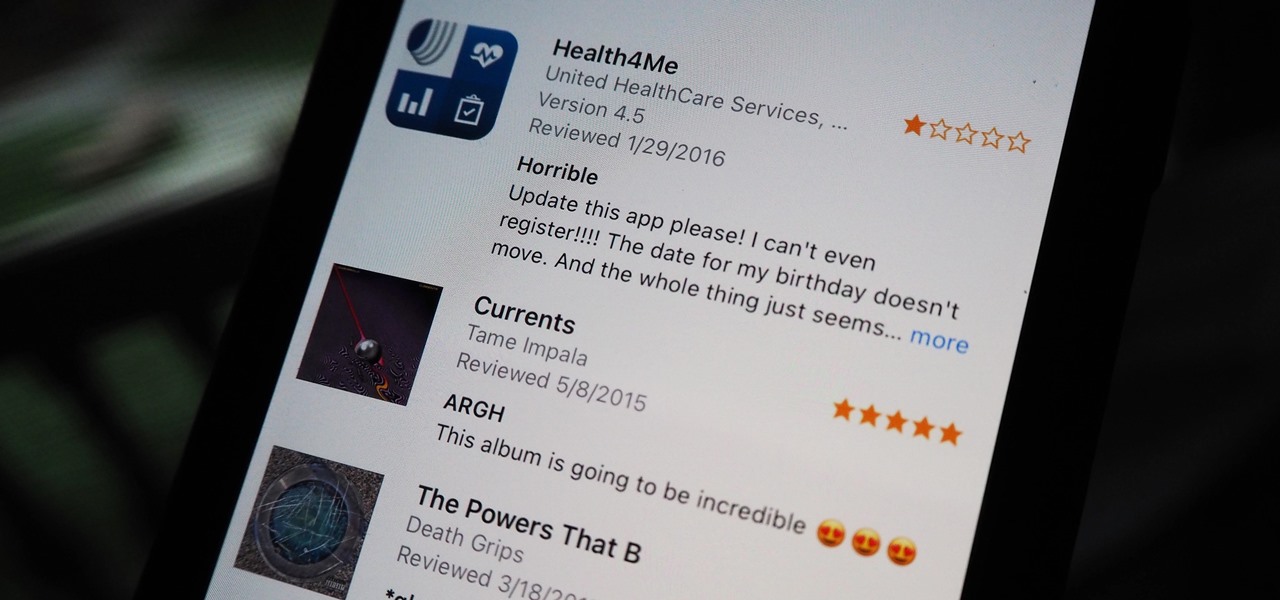
Voicing your displease with a shoddy third-party app or professing your love for an album you've just bought is normal, which is why we have ratings and reviews. You hate something, you write something. You love something, you rate it. But feelings change over time, so your ratings or reviews may need to be updated.

After shipping a redesign of Google Photos and adding a neat new Map View feature for exploring photos, Google has made another change to manage the volume of photos and videos the app is handling during the Social Distancing Era.

In a bold move, Samsung has decided to forgo the Galaxy S11 moniker and jump straight to the S20. Perhaps it's marketing for the new 20:9 aspect ratio and 120 Hz display, or maybe it's just the fact that it's releasing in 2020.

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they released a phone that's nearly perfect on paper.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Your Pixel's Now Playing song discovery tool received a few updates in Android 12, and the feature is finally comparable to other music recognition services.

The standard way to sort your notes and to-dos in Reminders has always relied on you putting them in the correct list and group. Then came smart lists for flagged and scheduled tasks, followed shortly by a smart list for tasks assigned to you. In iOS 15, Apple brings yet another way to find your reminders more easily — tags.

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

GTFOBins and LOLBAS are projects with the goal of documenting native binaries that can be abused and exploited by attackers on Unix and Windows systems, respectfully. These binaries are often used for "living off the land" techniques during post-exploitation. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Apple Watch owners know there's a built-in way to remove water from the device's speaker. However, even though modern iPhones are IP67 and IP68 water resistant, there's no official way to deal with water-clogged speakers that can muffle audio and cause prolonged damage if not ejected. Older iPhone models have it even worse, but there are some easy things you can do to get that water out.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.