Veronica Belmont from Tekzilla shares a tip for finding lost podcasts without unsubscribing and resubscribing to the feed. To do this by a simple keyboard combo fist close the disclosure triangle so that the individual episodes are hidden, then hold down the 'Option key' in Mac or 'Shift' in Windows and toggle the disclosure triangle as shown. The iTunes feed will refresh and all the past episodes will reappear. Combine this with the "Get All" button to find lost podcasts.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

Ex-Pro keepers show how to warm up before a match. This specific to keepers. This is a light warm-up for early high school players. It is not rigorous by any means and is made to get goalkeepers using their finger tips and getting loose on their toes.

Looking to drop a few pounds? The grapefruit diet has worked for many. Investigate to see if this citrus-based diet – which started back in the 1930s – is the weight-loss plan for you.

This episode of Full Disclosure demonstrates how to hack/crack MD5 password hashes. MD5 (Message-Digest algorithm 5) is a hash function commonly used by websites to encrypt passwords. MD5 is a one-way hash; therefore, to crack the password you most try every possible dictionary word and if that does not work, every possible letter/number/symbol combination. The programs used to crack the passwords are Cain and MDCrack-NG.

If your children are actively involved in things like gymnastics, cheerleading and dance, then they'll be dealing with a lot of rigorous movement, so stretching is key to prevent injuries. This video will show kids how they can do some great warmup stretches to increase flexibility for trampoline, gymnastics, dance, cheerleading, skating, ballet, tumbling and other children's sports.

In this video, we learn how to kick start a new fitness routine with Kung Fu. This exercise is a workout that you will not get bored of. You are always doing something new with Kung Fu and it burns a ton of calories. These workouts are rigorous and combine strength training, endurance training, and really work out your body. The classes start out with yoga, then they start getting your heart rate up by working out hard. If you can't get to a class, you can do this at home by doing loose kicks...

In this video, Becca explains and demonstrates how to walk in high heels. Becca is neither a model nor has been professionally trained. The tips and tricks shown in the video are her own techniques after rigorous practice and experience. She suggests to start with a very short pair of heels. She explains about the weight factor when walking on heels, which can affect the posture. She says that a lot of women go wrong when they try to walk on heels as if they were walking flat footed. She also...

Clouser's approach to fly design begins and ends onstream, with a lot of time spent in between at the workbench. Careful observation of the behaviors, habitats, and physical features of the foods fish eat is essential to developing a fly that looks and acts like the real thing. But the pattern must also pass rigorous standards of durability, ease of casting, and most importantly, consistently catch fish before it can be called a winner.

This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.

Power yoga is the one of the more rigorous yoga workouts. Learn how to increase strength with Power yoga poses in this video clip. Take Action: gain strength, tone every muscle, and reach toward Divine. Cindy Mastry, the instructor of this how-to video, has practiced yoga since the age of eight, and also has a background in Jazz and Ballet. Active in the fitness industry for nearly twenty years, she teaches aerobics, kickboxing, and yoga at many fitness centers in the Tampa Bay area. Cindy tr...

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

Self disclosure forms friendships with active listening and sharing, telling others about yourself, your thoughts, fears, and goals. Learn how to improve self disclosure and trust in this free communication video series.

Sushi aficionados and Simpsons fans alike know all about the joys of fugu. Known also as blowfish, it's reputed for being tasty if sliced from the correct part of the animal and many even say they experience a "fugu high" after eating the fish. Alas, if you have an unskilled chef, fugu is famous for being deadly.

Pilates is fantastic exercise. If you are a beginner, though, it can be confusing to choose the right type of class. Check out this tutorial before you head to the studio and ensure you get the most out of your exercise routine.

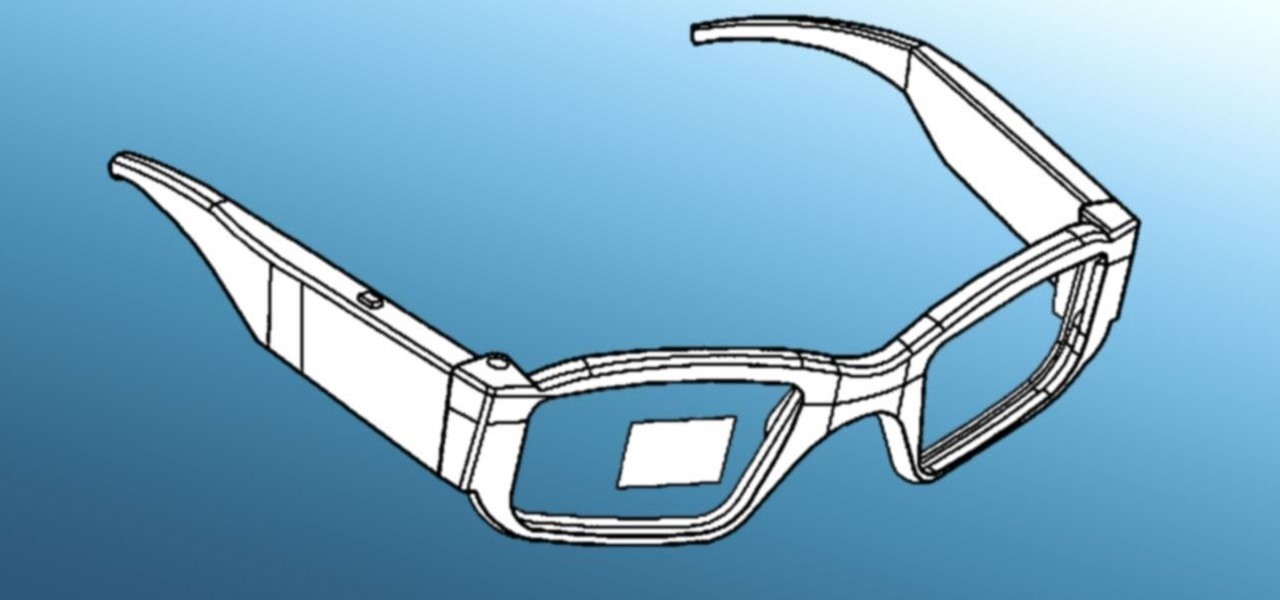
Last week, we told you about one of the first pairs of augmented reality smartglasses to get Amazon Alexa functionality, and now we're finally getting a look at how it works.

Want a smokey eye look but only have a single type of eye shadow? This home beauty video tutorial will teach you how to create a classy, imperceptibly gradiated eye look using that single shade of eye shadow.

There is a lot of stigma around prenuptial agreements but they can be a good chance to work on difficult issues as a couple and make sure you're on the same page. Prenuptial agreements don't have to be a horrible experience and can give a soon to be married couple some peace of mind.

Although Magic Leap's founder Rony Abovitz has a lot to say about his product, what people really want are visuals, and it looks like we're about to get a lot more of those in the coming weeks. In a post on Magic Leap's official announcements forum page, the company revealed that it plans to begin a monthly livestream series on Twitch.

Flying under the radar during Magic Leap's big week at the Game Developers Conference, the company settled a potentially ugly lawsuit with a former employee.

Kazendi, a London-based HoloLens development and rapid prototyping studio, just released a new iOS app in Apple's App Store that lets developers stream HoloLens applications live from the headset to an iPad or iPhone. It's called HoloStream, and is the first iOS/HoloLens crossover app we've seen so far.

In recent light of Obama's assertion of executive privilege over important documents concerning the Fast and Furious operation, here's a brief article concerning this controversial power.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

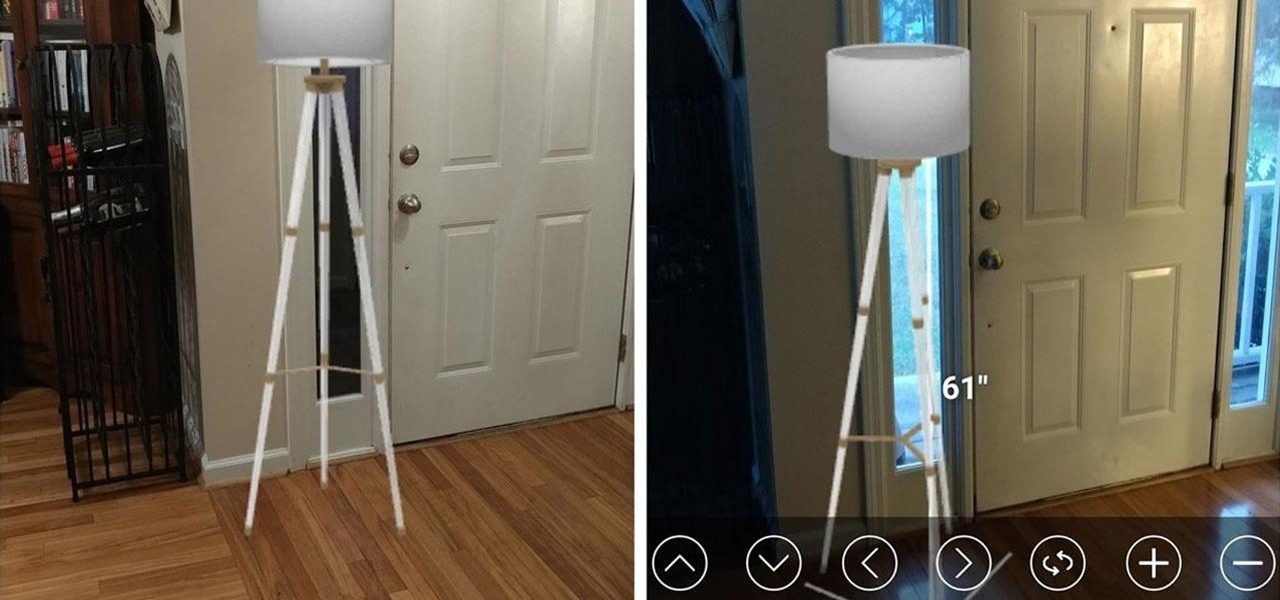
Historically, patents have never been a rock-solid source for uncovering the future of a company's product pipeline. However, sometimes, the images you find in the patent application search archives are so convincing you have to pay attention.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

Last week, Magic Leap CEO Rony Abovitz teased his Twitter followers with some "fun and cool stuff" to share in the coming days. On Monday, he made good on that promise, sort of.

While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.

Over the past eight months, ten infants at UC Irvine Medical Center tested positive for the same strand of methicillin-resistant Staphylococcus aureus (MRSA). Despite the danger of this superbug due to its high resistance to most antibiotics, this information was only released to the public on Thursday. Thankfully, all ten babies survived and are currently healthy.

Last month, Dr. Sung-Hoon Hong, Vice President of Samsung Electronics, announced at the Virtual Reality Summit in San Diego that Samsung would be moving into the augmented reality market. According to a recently published patent application, that move has begun.

Netflix has become the subject of heavy buzz this week, and not due to the latest season of Daredevil (which gets two thumbs up, btw). The online video entertainment provider is drawing fire over its admission that it has been throttling video streams for its AT&T and Verizon customers for years.

For the most part, Xbox Live is amazing, but there is one thing that has been annoying for pretty much everyone, to say the least. Microsoft Points.

Osterhout Design Group just announced the upcoming release of the newest addition to their smartglasses lineup, the R-7HL, short for R-7 Hazardous Location. ODG worked directly with customers who work in extreme environments to come up with a durable solution that fits their needs; These smartglasses can not only survive but function well in many areas that would otherwise be considered too harsh for augmented reality tech.

Uh oh. With millions of devices already sold, Apple's latest blunder is bound to upset the owners of some of their brand new iPhone 7 Plus phones.

With Adobe Photoshop on your computer, it's super easy to change or adjust the skin tone of somebody in a digital photo. The process uses some basic selection and color adjustment tools, and it's a fun way to make a friend's face nauseously green or lessen the effects of overly strong, sometimes even orange, makeup.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

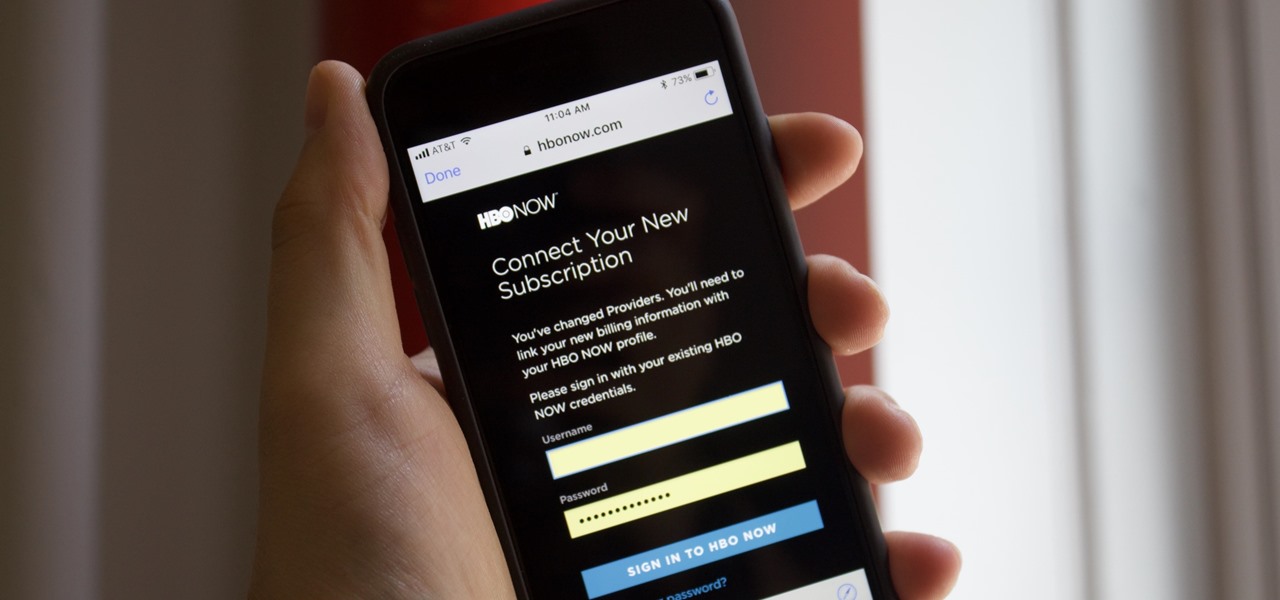
Update: HBO discontinued this service. Your best bet for transferring your data from one account to another is to save a record of your watch list. That way, you can add your titles back manually with your new account.

It looks like all the unregulated fun and games we were having promoting products on Instagram is about to get, well ... regulated. According to a new report by Mediakix, 93% of celebrities on Instagram are not in compliance with the Federal Trade Commission when it comes to posting paid content.