If you like to shop online then it is extremely helpful to have a PayPal account to safely make your online purchases. Help reduce your risk of identity theft by using protected methods like PayPal when your credit card information is involved.

While there's an art to surviving the all-nighter, there's also an art to staying awake throughout the day when you're operating on little to no sleep. In 1964, the record for sleep deprivation was set by 17-year-old Randy Gardner, who stayed awake for an incredible 264 hours and 12 minutes. Now while we're not out to challenge Randy for his title, we can certainly look to him for inspiration in beating back our own fatigue.

This lobster claw isn't the same one you'd be cracking during dinner. This lobster claw is a clasp for jewelry making. Great for necklaces or bracelets. If you've perfected the meticulous and dexterous art of jewelry making, than this should be simple. This demonstration video will help walk you through the process of attaching a lobster claw clasp to your work of art.

You’re munching away on walnuts and, oh no, you notice you have a scratch on your wood floor. You already have the solution in your hand. The oil in nuts will fill in and make scratches on a wood floor disappear.

Don’t wait for your next headache to pull out that bottle of aspirin. Aspirin can be used as a topical home remedy for some medical problems, and as a handy fix to remove stain, keep your flowers fresh and even start a car battery.
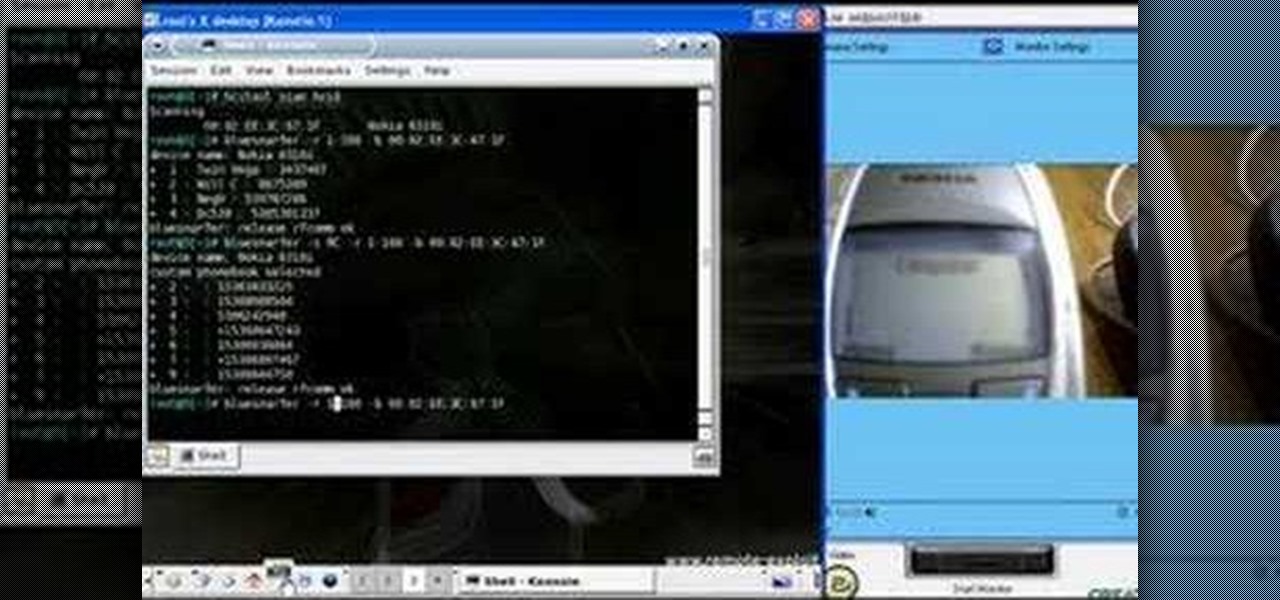
Check out this video tutorial to see how to bluesnarf a Nokia 6310i handset (cell phone). What is Bluesnarfing exactly?

Whether you're at work or just away from an outlet, nothing is more annoying than suddenly having to go through your day with a dead phone.

With everything the last year has thrown at us, the odds are good that you've had to start working from home, complete with all-new challenges both for you and the technology you use.

Every mainstream Android home screen app looks and behaves almost exactly like Google's Pixel Launcher. It's the trendsetter, like the Nexus Launcher before it. But when all your options are modeled after the same thing, that really takes the "custom" out of "custom launcher."

Next year, fans of Mario Kart will be able to experience the game in real life with the assistance of augmented reality.

Instead of using a single APK, YouTube Vanced recently started being distributed as a bundle that requires a third-party app to install. Some fans found this too difficult, so the Vanced developers decide to make the process easier.

Every state has begun reopening in some capacity. While there are important steps for everyone to get back to work and begin socializing, precautions will be in place for some time, especially with an expected second wave coming this fall. The virus is not over.

Since Apple launched iOS 13, we've seen four major updates for iPhone, each of which added some cool new features. Between iOS 13.1, 13.2, 13.3, 13.4, and all the minor updates in between, there's never been a better time to be on iOS. And now, we've got even more positive changes with the iOS 13.5 update.

In previous Android versions, you lost about an inch of screen real estate to the status bar and navigation bar. But if you enable Android 10's new navigation gestures on your Samsung Galaxy, you can regain the bottom part — and with the help of ADB, you can reclaim the top portion as well.

The original iPhone SE was, for some, the perfect iPhone. It brought back the popular one-handed form factor of the iPhone 5 but packed in the internals of the then-new iPhone 6S. Now, the second-generation iPhone SE is here for 2020, but can it live up to what made the first-generation iPhone SE so popular?

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

With the nation facing a shortage of ventilators for COVID-19 patients and no apparent ramp-up in the production of new ones, engineers, medical resistents, and do-it-yourselfers are sharing plans for homemade versions.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?

The World Health Organization has declared the new coronavirus a pandemic, and the Centers for Disease Control and Prevention recommends video visits with a healthcare professional to reduce the risk of being exposed to the coronavirus that causes COVID-19. If you are experiencing mild flu-like symptoms, virtual doctor visits may also prevent you from endangering others.

Amid the coronavirus chaos, two companies at the forefront of augmented reality technology took starkly different approaches to their upcoming developers conferences, as Facebook has canceled its annual F8 conference and Magic Leap plans to invite a limited number of attendees to its Florida headquarters for LEAP Developer Days.

Congratulations, you've made it deep into the middle of flu season! If you're reading this, you're either a very smart preemptive sick day prepper, or already in the throes of fighting off a cold or flu situation.

Is the augmented reality magic fading down in Plantation, Florida? That's the first question some may be asking following a casual revelation over the weekend that Magic Leap, the maker of the Magic Leap One, has assigned much of its patent portfolio over to JP Morgan Chase as collateral.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

Filmic Pro has a superb suite of professional settings — bit rate, frame rate, and mic choice, to name a few — which can enable you to capture the best footage possible. But different shots require different setups, and it can be frustrating to change settings on the fly. Filmic Pro lets you skip that whole process by saving your favorite settings as presets for quick and easy access.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

When Google finally gave us a dark theme for YouTube, it was a bit disappointing. They didn't use a pure black background, reducing some of the battery savings you'd get with an OLED panel. But with the help of another app, we can fix this, and not only get a real dark mode, but other colors as well.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

The iPhone XS, XS Max, and XR aren't the newest devices from Apple Inc., but all three have a serious problem in Messages. When sending a friend an SMS/MMS text rather than an iMessage, the phrase "Number changed to Primary" appears in front of every message. What gives? If this issue is driving you mad, there are a few tricks that may exterminate the bug until Apple gets around to issuing a patch.

There's more to recording calls than just protecting yourself against liability or an angry ex — oftentimes, this feature is the perfect tool to save momentous calls like breaking news of your recent engagement to loved ones. And with the prevalence of video calls, you can even capture memorable video chats such as your mom's first glimpse of your newborn on your mobile, courtesy of Skype.

This week, Next Reality published its annual feature on the leaders in the augmented reality industry, the Next Reality 30. So it's no coincidence that the companies represented in the top four spots of the NR30 also made business headlines in AR this week.

Although the Magic Leap One: Creators Edition is currently officially available in only six US cities, those living outside of Magic Leap's designed US cities now have a roundabout way to order the device.

UPDATE: The ported APK covered below is now obsolete because Fortnite beta is officially available for all Android devices!

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.