A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

In the Western world, the only time you'd associate food with cockroaches is health code violations. And while other cultures and countries are more open to cooking with and eating these and other little buggers, insects are probably not a food trend that will be adopted by the West anytime soon.
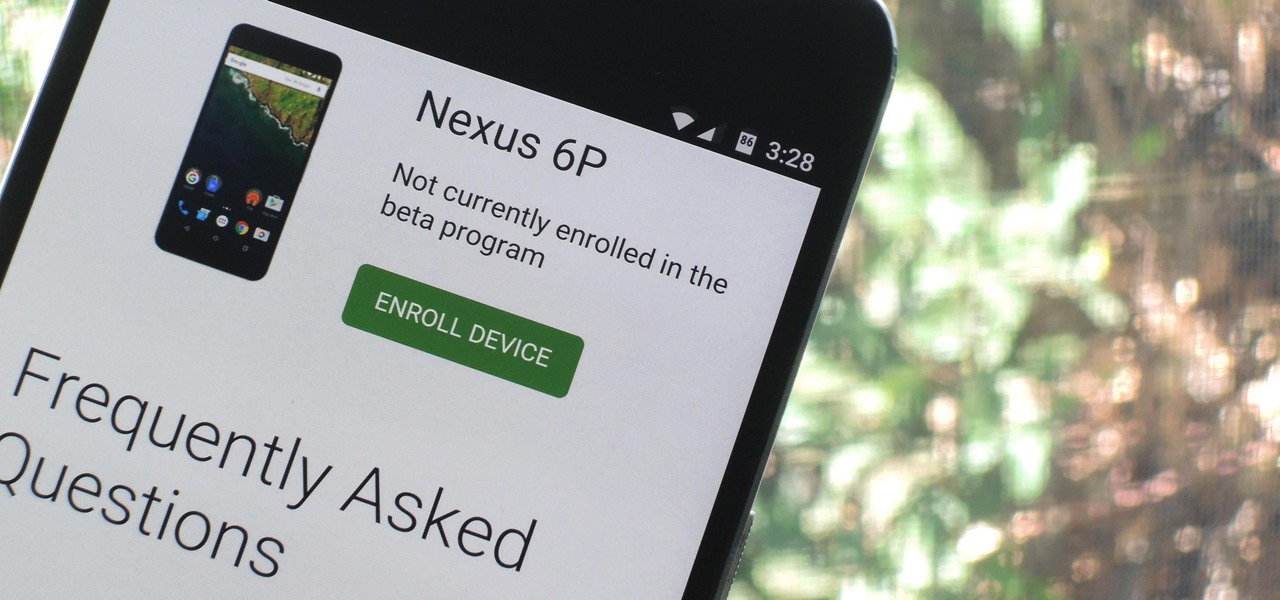
Google just released Android 7.0 Nougat, and as usual, they're doing a staged rollout. This means that most users won't actually get the update on their Nexus devices for a few weeks—that is, unless they take matters into their own hands.
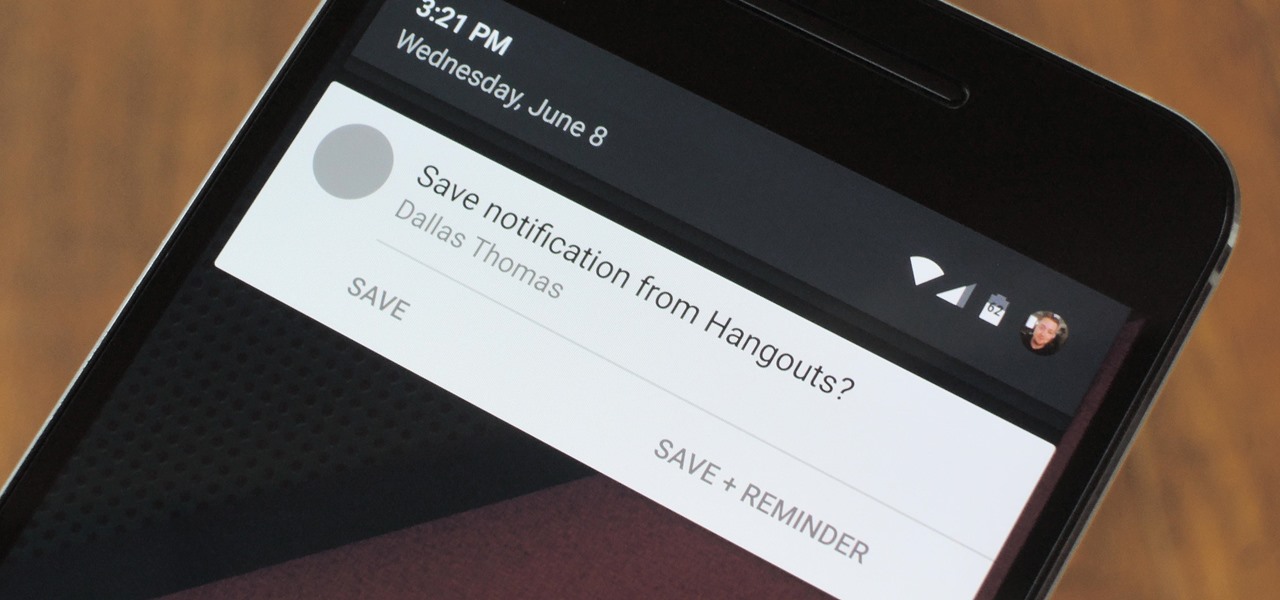
These days, there's almost an expectation that you have to deal with messages as soon as you get them. But that's not always the best way to handle things—sometimes, you're preoccupied with something, and it would be better if you could deal with a new message when you have a chance to give it your full attention.

Google seems to be growing tired of the way links appear in its Search results page, because they're currently experimenting with a color change (that's already causing lots of controversy).

As exciting as it can be to crack open a beer, there's nothing fun about wandering around a party and asking other partygoers for a bottle opener.

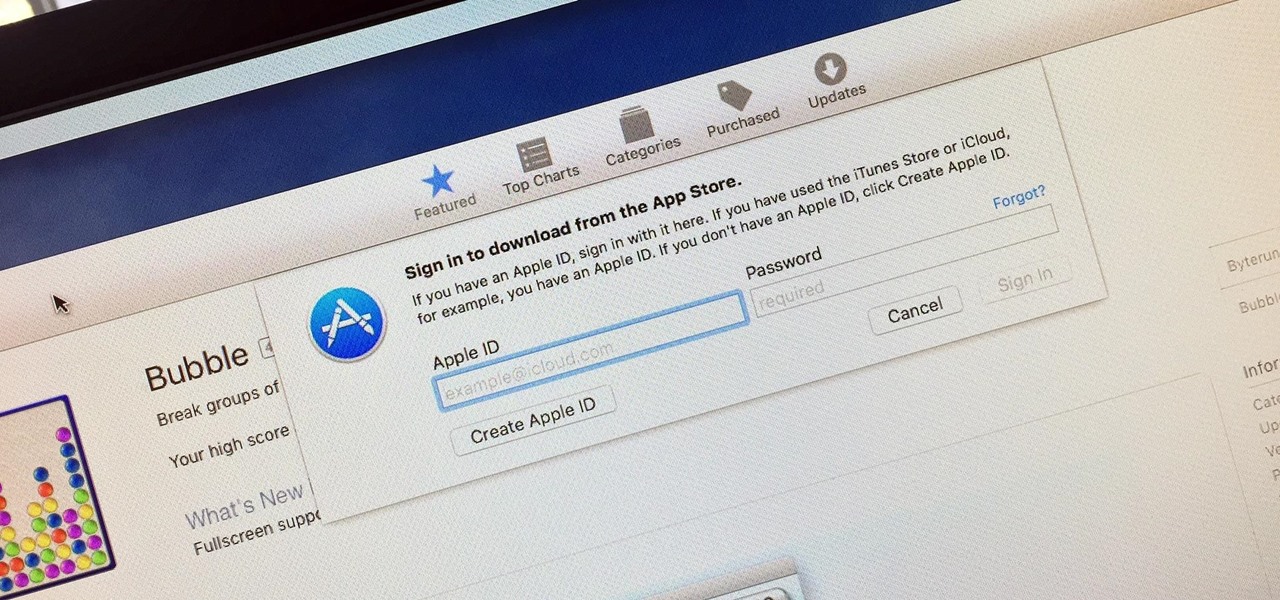
Whether you want to edit photos, compress files, play games, or DJ your next party, there's a free Mac app that can help you out. But things can get annoying real fast if you download a lot of free apps from the Mac App Store, since you have to type in your Apple ID password each time.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Mobile data is expensive. The internet connection that comes with your cell phone plan is generally limited to a certain amount of gigabytes that can be downloaded before your monthly cap kicks in, at which point you run the risk of incurring costly overage fees.

Video: . For the first prank you're going to need an empty container, preferably black, a smoke bomb and a lighter. I gotta say though this prank is not for just anybody so prank at your own risk. Let me show you how its done, first apply some hot glue on the bottom of the smoke bomb, then stick it inside the container.

When we were kids, Saint Patrick's Day was a green-hued holiday that promised green eggs in the morning and green mashed potatoes in the evening... along with some traditional corned beef and cabbage, of course.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

So you dropped your smartphone and the screen cracked. Again. Just the thought of sending it out for repair or buying a new phone is driving you mad.

Unless you're in law enforcement, you won't usually have a flashlight on hand for those rare moments when you need to sift through the dark. However, it is very likely that you will have your phone on you, so you'll have fast access to a bright light with just a few easy taps.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

When you have some form of lock screen security enabled, Android makes sure that you don't have to fumble around to enter your pattern, PIN, or password before you can call 911 in an emergency. It does this by adding an "Emergency Call" button to the bottom of the screen—but as handy as this may sound, most of the time it's more trouble than it's worth.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Many home chefs are deterred from whisk-intensive recipes such as mayonnaise because they seem to require more than two hands—which is obviously the maximum number we possess. One hand is required to stabilize the bowl, another must be whisking constantly... and a third hand is needed to pour a steady stream of oil.

Slowly but surely, Microsoft seems to be steering Windows in the direction of Google's Android. First, they released Windows 10 as a free upgrade, mainly because they wanted to cash in on the revenue that they hoped would come when more users had access to the Windows Store. Then, they included tons of tracking "features" to help populate Bing with targeted ads, which has always been Google's primary method for monetizing Android.

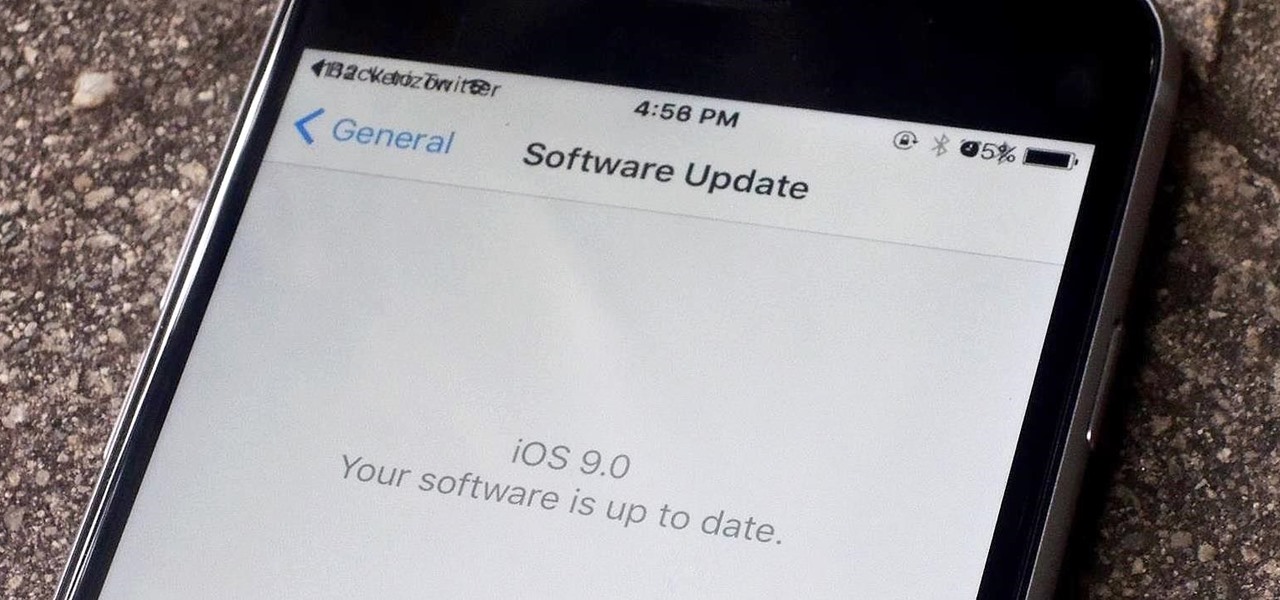
Apple's unveiling of the iPhone 6S, iPhone 6S Plus, Apple TV, and iPad Pro dominated the news today, but at the end of their special September 9th event, they quietly released the final version of iOS 9 to developers, called the Gold Master (GM) build.

The increased sophistication of smartphones and apps have allowed us the luxury to never leave our homes. Everything from coffee to food to dry cleaning can be delivered straight to your door without ever leaving your couch, which can can be a godsend during the winter months when you'd rather not risk leaving your warm bed. But during the summer, you gotta ditch the comforter and go enjoy outdoors.

There are many apps and features on your iPhone that you may never use, and therefore don't need. A great illustration of this is the Apple Watch app. You might have no interest in ever getting an expensive smartwatch, yet you're stuck with the Apple Watch app on your home screen.

It would be an understatement to say that Supercell hit it big with Clash of Clans. The game has topped both Google Play and the iOS App Store for years and shows no signs of ever slowing down.

Welcome back, my hacker novitiates!

When you have a parent who cooks—and has you act as sous chef—the kitchen automatically becomes a less intimidating place. In other words, kids who know their way around the kitchen will most likely become adults who cook for themselves, which also means that they'll eat more unprocessed whole foods, save money, and maintain a healthy weight.

Starting with the original HTC One and now present on the new Nexus 6, dual speakers allow for smartphones to pump out true stereo sound. OnePlus, however, kept their speakers on the bottom of the device and use different sound drivers for each to produce great sound quality, although it's still mono. While there are mods out there that can further increase the volume of the OnePlus One, none of them can produce true stereo sound.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

Sometimes, it helps to be prepared before jumping into a new relationship; look before you leap! To have a healthy relationship with someone who has an STI, it is advisable that you enter the relationship knowledgeable about sexually transmitted infections and what your risks might be.

Baking soda is a powdery miracle. Not only is it the secret ingredient to making mashed potatoes fluffy, it can help you make authentic-tasting soft pretzels at home and caramelize onions in half the time. It's actually got lots of surprising uses you might not know about, and one of them is that a pinch or two can correct sour and bitter tastes in your food.

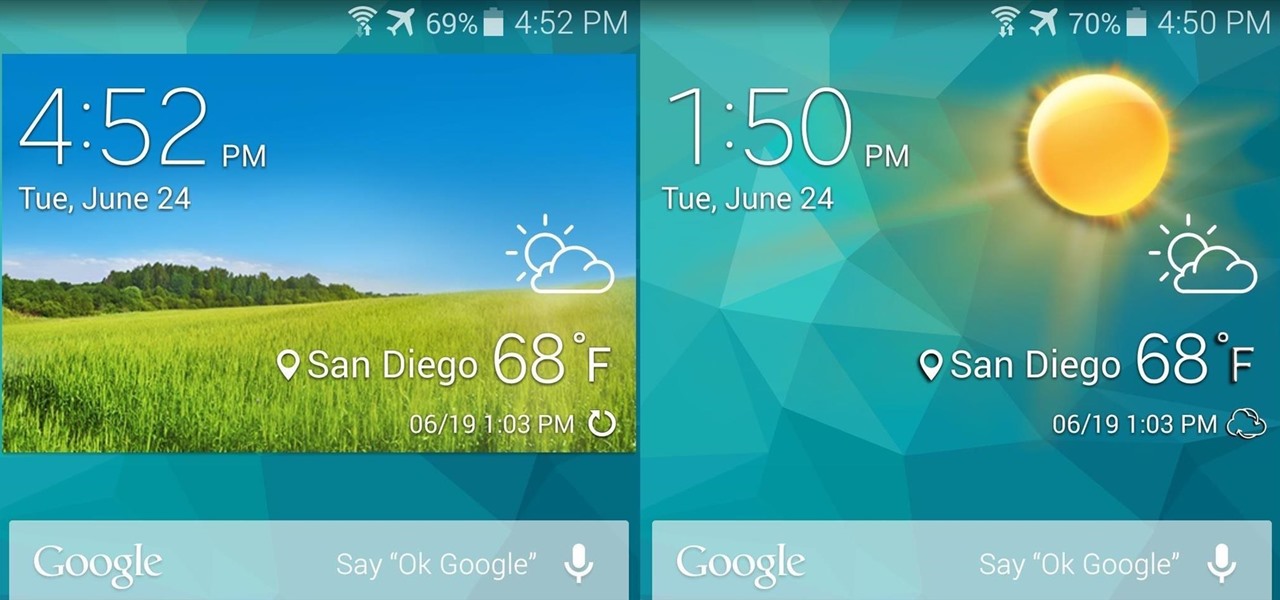
The weather widget on the main home screen of a fresh-out-of-the-box Galaxy S5 is meant to show off the screen. Super-high contrast and crisp definition on the individual blades of grass in the background let you know that the phone you're holding has one helluva display.

As a parent, navigating smartphone usage with your children can be a perilous journey as you hand them that new device they've always wanted, or even your older hand-me-down phone or tablet.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

Fresh off the heels of their latest agreement, Google and Samsung may soon be further aligned in their mobile technology outlook. The two tech giants signed a cross-licensing patent agreement, but that doesn't mean that Samsung was just going to start putting out stock Android devices. Quite the opposite really, as we saw from leaks of its new Magazine UX. The new user interface was shown during Samsung's presentation of it's latest Galaxy tablet at this years CES, and as reported to Re/code,...

If you've got a birthday party to plan for a young budding scientist coming up, a little nitrogen should do the trick. In this project, I'll show you 10 "super cool" tricks with liquid nitrogen that you could try, but probably shouldn't!

When you're using vacuum power, moving water, or compressing air, it's more than likely being done with some sort of pump. I'll be needing a pump for some of my future projects, so in this tutorial, I'll be showing you how to make your own customizable PVC hand pump that will let you do all three.

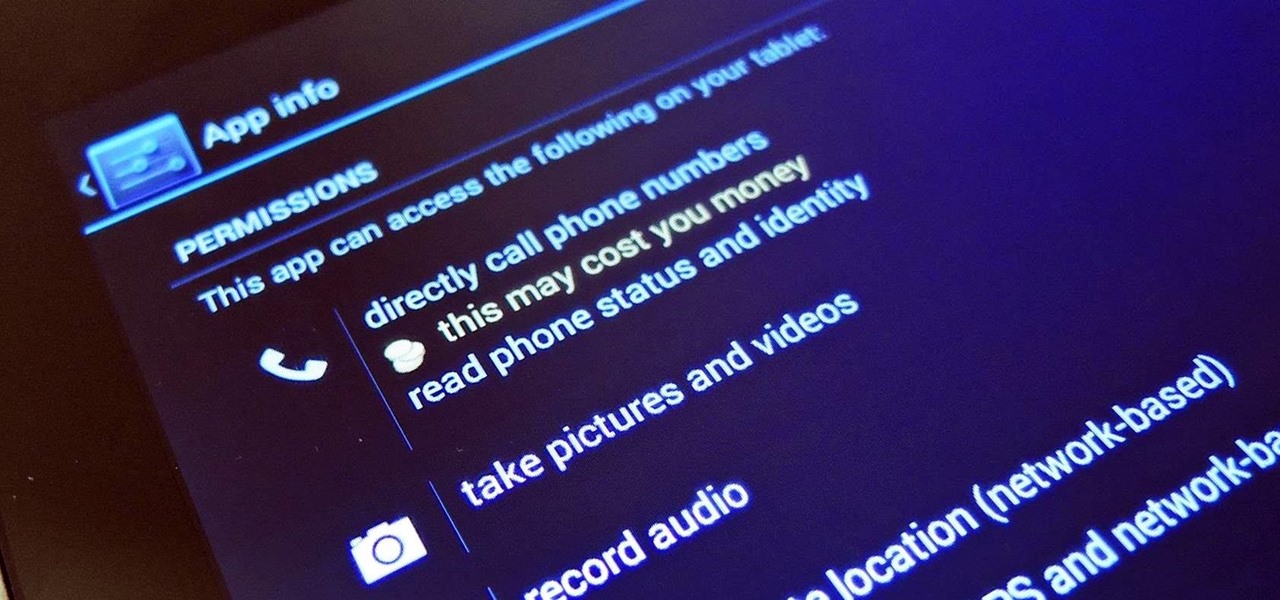
Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

Are you a messy burger eater? Ants and fruit flies invading your home? Hate drinking warm drinks? Find out the quick and easy DIY solutions to these problems with these 10 amazing tips and tricks for the summer.

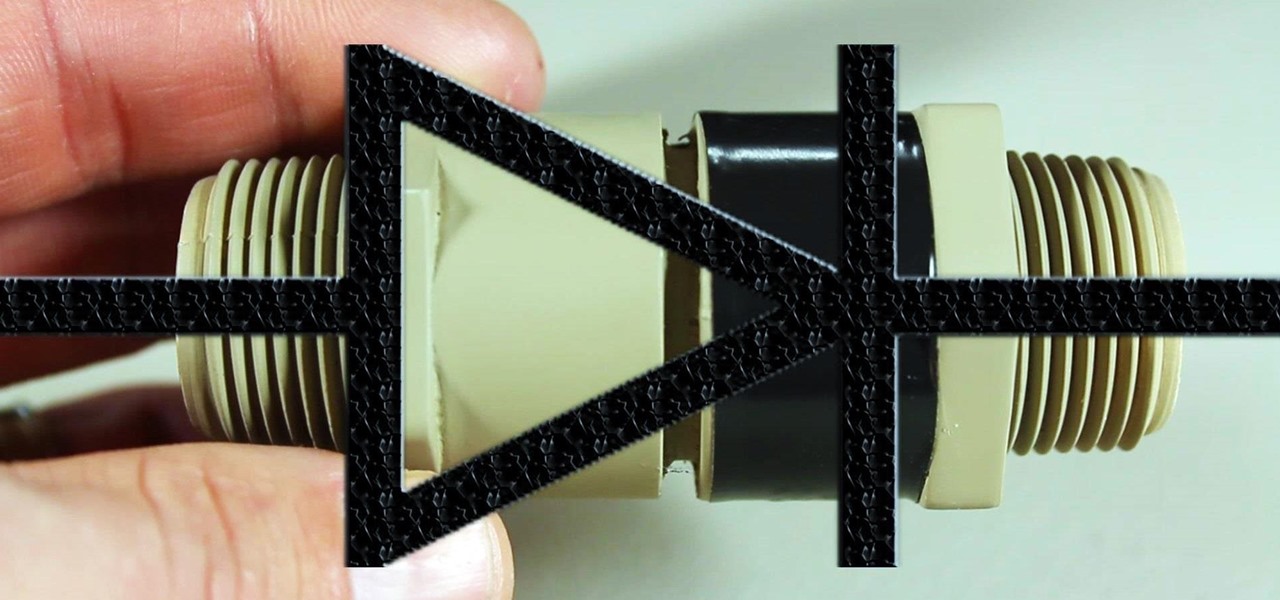
If you're going to build yourself a water gun to cool down this summer, or maybe just a useful water pump, you'll need some check valves. However, the most expensive parts of a water pump or DIY super soaker are usually the check valves. So, let's make some from scratch for as little as $0.35 each.