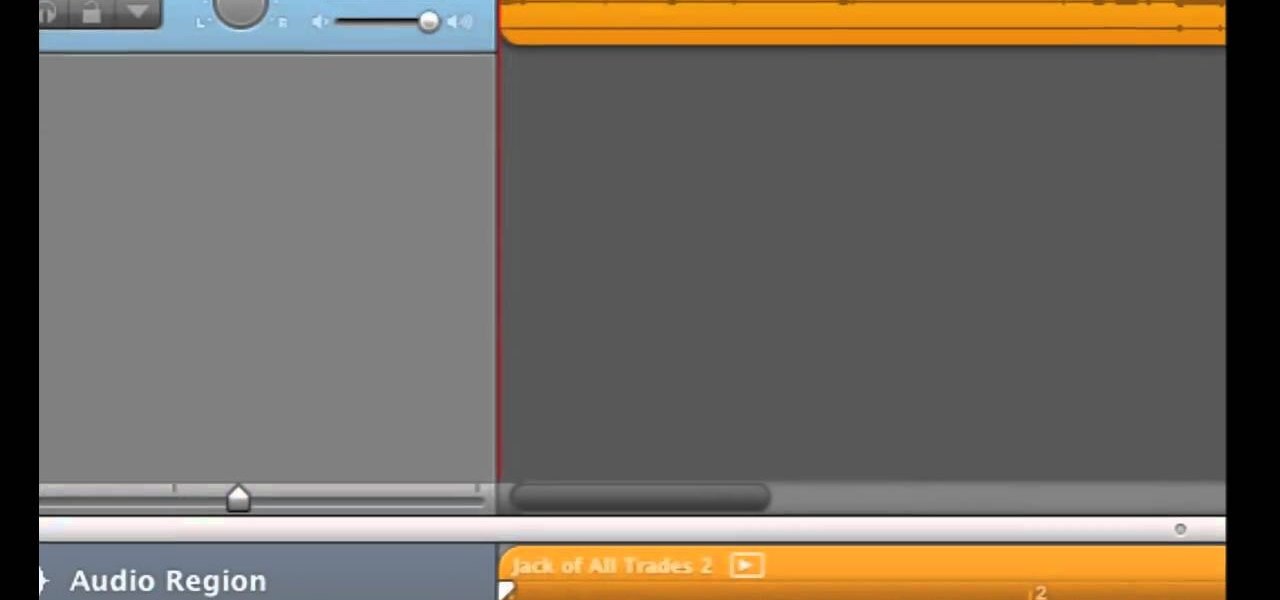
If you've just exported your masterpiece from GarageBand and found that your volume on the song is too low, then you're going to have to fix it. And increasing the levels on your "too quiet" song, you just need to get back into GarageBand and make some adjustments.

Millions of laptop batteries have been recalled because of the risk of FIRE. Get some tips from CNET to learn how to keep your laptop battery safe and secure. First, make sure your battery hasn't already been recalled. Second, don't leave the laptop constantly charging because it heats it up. One way to save your battery is to remove it completely when you plug in directly. Third, treat the battery as fragile. And finally, four, avoid buying knockoff batteries.

This is something every pilot should know: tailstrikes. What are they? It's when the tail of your aircraft smacks (strikes) the runway, either during landing or takeoff. During takeoff with a fixed-wing aircraft, it could happen because of a pilot pulling up too rapidly. During landings, it could happen when a pilot flares too aggressively. Either way, it needs to be avoided.

Installing and managing ROMs on your rooted Android phone can be a pain. You have to connect phone to computer a lot, and every time you load a new one you run the risk of it not working and having to start all over again. Fortunately, there's even an App for that! This video will show you how to use a cool App called ROM Manager to handle all your ROM-related tasks, from getting and loading new ones to maintaining and editing them. Never load a ROM manually again, buy this App!
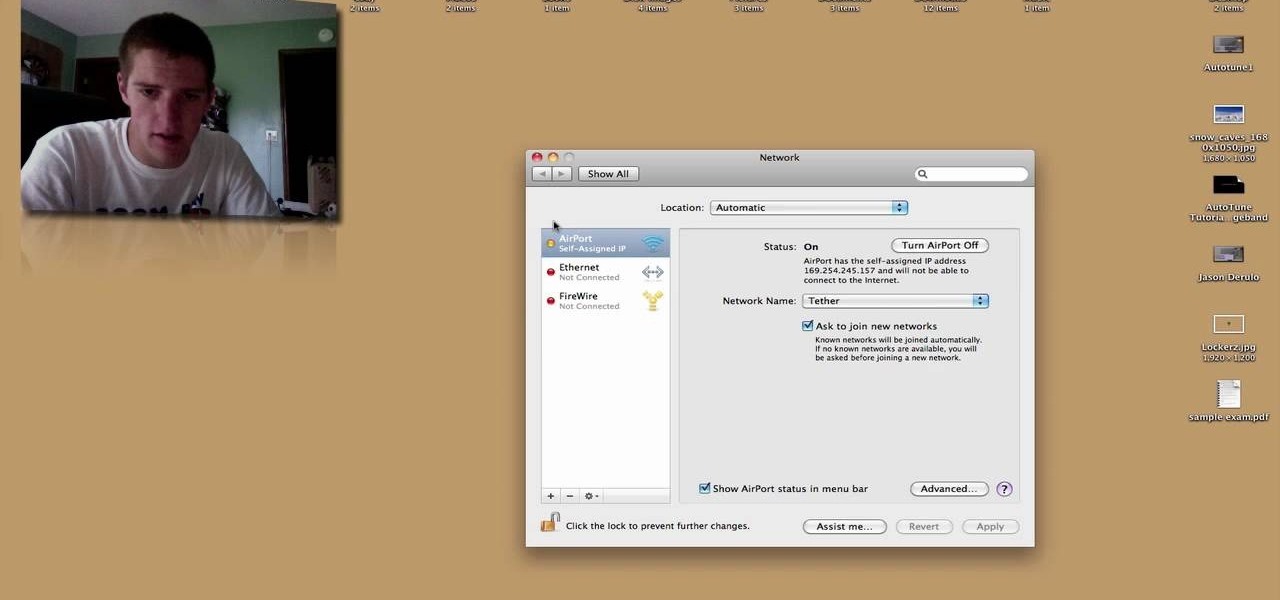
If you ever wanted to tether your iPhone but found your carriers’ prices ridiculously high, then meet HANDYLIGHT. This $0.99 iPhone app has a nice hidden feature. It will allow you to connect to the internet using your iPhone (i.e. tether). There’s no guarantee that this app will stay in the app store much longer (or even on your phone after you purchase it), so use it at your own risk.
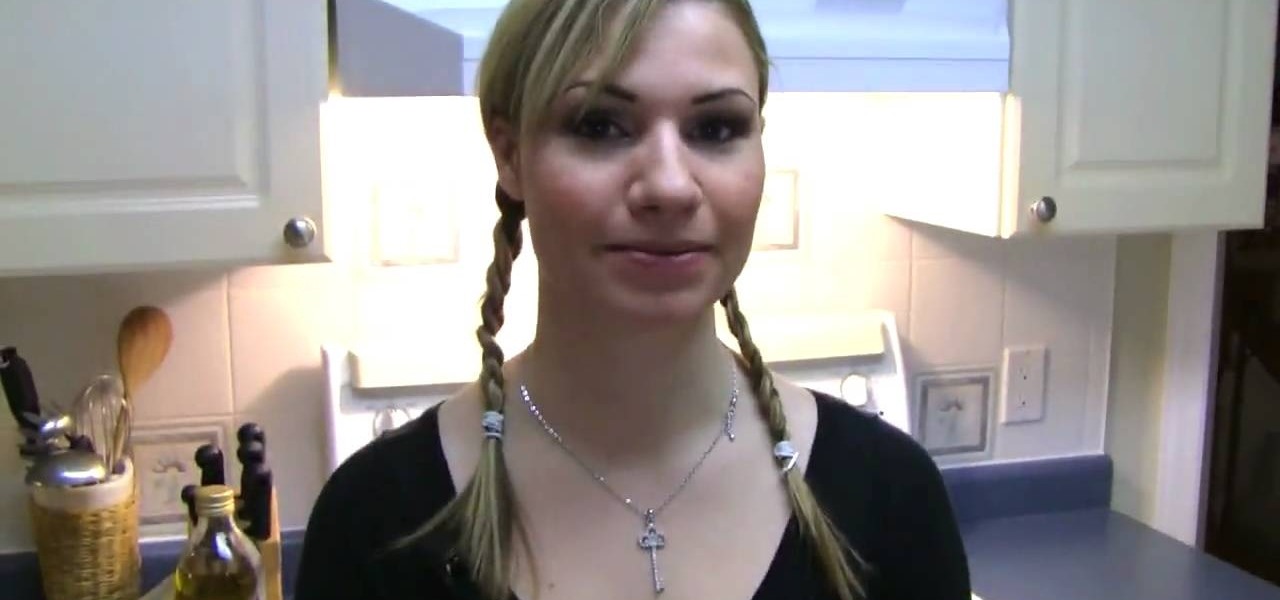
You know the brown sugar facial scrub from Fresh? Well, this DIY facial scrub is pretty much the same thing, minus the cancer-causing parabens. Exfoliate and nourish your complexion without putting yourself at risk for some nasty side effects by making this brown sugar and olive oil facial scrub.

Complete your knight costume - or damsel in distress who's really a kick ass swordsman in disguise costume - with this cardboard Medieval sword. Sturdier than paper and much safer than the metal of a real sword, this version can be used by kids without risk.

Kissable lips are quite the oxymoron, because though kissble lips look bright, glossy, and plump, thereby attracting suitors to their whims, all the products used to make them look kissible actually prevent anyone from actually wanting to kiss them (unless they're willing to risk the lip gloss slobber and pink mouth staining).

In this video, you will learn how to install a fan on your XBox 360 power brick. In order to do that, just follow these steps exactly like in the video: The first thing to do is to buy an 8mm fan and to clear the power brick. Now make a hole in the power brick case and glue the fan to it. Connect the negative and the positive wires like in the video and turn it on. If you follow these steps right, you will get the correct result. Your power brick will get more cold air and the risk of a RROD ...

YourTango presents relationship expert Rachel Greenwald, who breaks down why he didn't call you back. She takes us through the process of learning why men do not call women back after first dates. Find out if you are the type of woman who is at risk of not getting a call back, and it begins with "the blahs", a woman who gives the one word answer to standard questions. Next, see if you suffer from iPod repeatability, the Oprah eyes, or how men call it the Park Avenue princess. If you follow th...

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. In this episode, you'll learn how to make ice cream in udder a minute, using the wonders of liquid nitrogen. (You will also learn how to do this safely, so you don't risk giving your fingers a case of instant frostbite.)

John Park from Make Magazine hacks a Nintendo Wii controller and turns it into a personal flight recorder that can sense and measure the stomach-churning G forces of roller coasters and other high-speed, high-risk activities.

Okay, so first things first: the con presented in this bar trick video is illegal since you're basically stealing money, so perform at your own risk!

Fresh sautéed spinach will help wash the taste of 14 consecutive nights of pizza out of your mouth. You will need:

The multiple award-winning card game Sixteen is packed with head-to-head action. If you can you count to 16 and take calculated risks, then you can force your opponent to bust. But play your cards defensively at the right time or the tables will turn! Win the most sets and you'll win the game. It sounds simple (and it is), but Sixteen's unique strategy and cribbage-like counting will hold the attention of even the most seasoned game players.

More prescriptions for antibiotics are written for ear infections than any other type of infection. A new study comparing the incidence and causes of ear infections in children between the ages of six months and three years found that the incidence of ear infections over the last decade has dropped significantly since the 1980s.

As if the swollen, painful joints of rheumatoid arthritis weren't enough, the disease is the result of our immune system turning against cells of our own body. Ever since this realization, scientists have worked to find the trigger that sets the immune system off. Scientists believe that gut bacteria may have a role in initiating the abnormal immune response. Now, a team of researchers from Boston has figured out how that might occur.

Colorectal cancer — cancer of the colon or rectum — is the third most commonly diagnosed cancer in the US. To reduce the chances of a diagnosis we are all urged to stop smoking, keep our weight down, decrease our intake of alcohol and red meat, keep active, and get screened for colon cancer. But, new research has found something that participates in the development of colorectal cancer that might not be as easy to control: A strep bacteria that promotes tumor growth.

Listeria monocytogenes bacteria don't play fair. Healthy people can usually handle the food-borne infection, but the bacterial infection hits pregnant women, fetuses and cancer patients very hard. Interestingly, a new study found that other bacteria may help prevent Listeria infections in those people.

Lyme is a growing threat as we move into warmer weather in the US. Researchers have said this year could be one of the worst for this tick-borne disease, as a skyrocketing mouse population and warmer temperatures increase the risk.

According to the National Safety Federation (NSF), pet bowls and toys carry coliform bacteria, including Staph bacteria, yeast, and mold. Additionally, an (unscientific) survey from Petco found that almost one-third of pet owners do not know the extent of contamination that their pet toys contain.

So, you want to cause a little mischief, do you? Here are six super-easy pranks to help you make the most out of April Fool's Day (or pretty much any other day of the year). There's something here for everyone—TV fiends, magic trick lovers, fruitoholics, and even spam companies.

A lot of my hacks use salvaged parts from an old microwave, with the microwave oven transformer (MOT) being the most useful component.

I use Google Chrome every day for my browsing needs, and I had no idea they were hiding something from me. So, I was pretty surprised to see that Chrome has an entire hidden experimental add-ons section. There are add-ons that work for Mac, Windows, Linux, and Chrome OS, so there's something for everybody.

Yesterday, we pointed out that hackers could remote-wipe certain Android-based Samsung smartphones like the Galaxy S III using a USSD exploit. All they have to do is hide a small code into any webpage or text—even barcodes—then once you click on it, the phone resets to factory settings in a matter of seconds. The video below shows just how easy it is.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

In this video, we learn how to use secure online passwords. There are a ton of things to consider when creating a password. A weak password is something that someone can easily guess. If you are using a birthday, common dictionary word, child's name, or something common then you are at risk. Your password should combine letters and numbers, and be at least eight characters long. It should also be completely random and have upper and lower case letters. You can use a password assistant if you ...

Most Rubik's cubes are not well-made or well-taken care of. They creak and turn slowly, acting like the cheap pieces of plastic that they for the most part are. There are ways though, even for cheap cubes, to make them work much more quickly and smoothly than they do out of the box. This video will show you a great method for breaking in your Rubik's Cube. It bears some risk of breaking your cube, but if you're careful your cube should be in better shape than ever when you're done, allowing y...

Simon Solotko outlines the steps necessary to get a desktop PC up and running from scratch using AMD Dragon platform technology. Fragon technology is a combination of AMD Phenom II processors, ATI Radeon HD graphics and AMD 7-Series chipsets. This technology allows you to build incredibly powerful PCs for multimedia entertainment, gaming and advanced multitasking.

In this tutorial, we learn how to use Nikon digiscopes. This means taking digital pictures with a digital camera through a lens. You can use two different versions of lenses with the Nikon Coolpix camera. You will need an eyepiece to use the camera with these lenses. You can get up to 75x magnification while using these, but risk of camera shake is greater. First, mount the camera on the triPod and apply the lens adapter, then the Coolpix camera. After this, use the view finder to see through...

Disabling your opponents legs is the fastest way to make sure that you can get away from a fight situation without killing your opponent. Attacking the pressure points associated with the large blood vessels and nerves in the legs is an effective way to do that. This two-part video features an extensive walkthrough of the legs pressure points and ideas for attacks that can be used against them to get your fight over with as quickly as possible without risking killing someone.

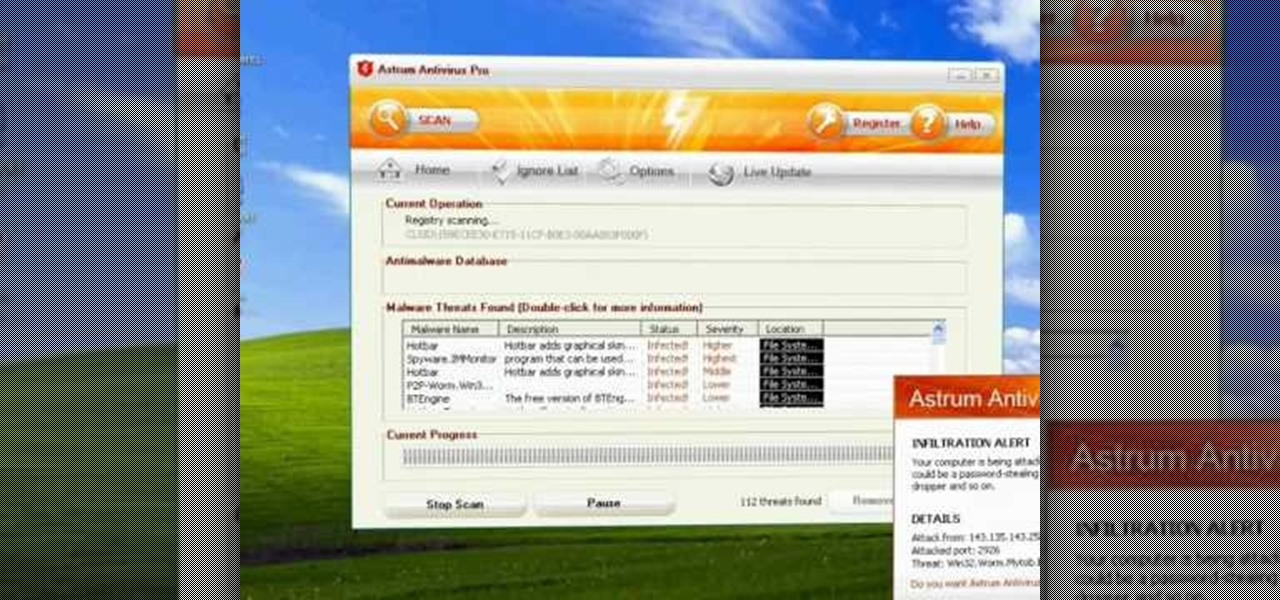
Astrum Antivirus Pro is a rogue anti-spyware application and a clone of VirusTrigger and Antivirus Trigger. Astrum Antivirus Pro is often downloaded and installed by a Trojan or through browser security holes. Astrum Antivirus Pro may generate large numbers of popup adverts. Astrum Antivirus Pro will also display notifications of imaginary security risks in its attempts to get the user to purchase the full version. Astrum Antivirus Pro may run a fake system scanner and then display fake syste...

Learn how to use depth of field with help from this photography tutorial. Although it may seem that depth of field is a confusing factor in photography, it's actually quite easy to understand & adjust once you've gotten the hang of it. Depth of field (or, DOF) is a great way to experiment with your photography & improve your skills as a beginner photographer. When taking your photograph using DOF, it is imperative to remember that the shutter speed and aperture (or F-stop) need to change at e...

Do your presentation skills need a little work? Being in front of a crowd or some potential clients may be one of the hardest things you will ever do, but staying confident makes all the difference. Losing any bit of confidence will result in your presentation falling flat and killing your self-esteem, and perhaps even risking your job. So, being confident is a must.

The Master Cleanse is soooo yesterday. Here are the best new ways to drop pounds fast. You Will Need:

For winter weather you should always carry tire chains. In the mountains of California one must carry tire chains or risk getting a ticket from a police officer. Buy chains at Walmart. They come custom fit to your vehicle and are easier to put on than the old ones that required you to drive over the chain. Don't drive in winter weather or snow without chains unless you have 4 wheel drive, 4wd, or all wheel drive AWD.

Is sleep deprivation threatening your sanity? Before you fall apart, try a few tricks that have worked for other new moms. You will need breast milk, a willingness to share your bedroom, power naps and help. Warning: Talk to your doctor before bringing your baby into bed with you. There are risks associated with this practice. Watch this video for tips to help you through those early, sleepless months with your newborn.

Listen closely or risk ending up like Jack Nicholson in The Shining, minus the whole crazy axe part. Learn how to dress properly for a snowstorm.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

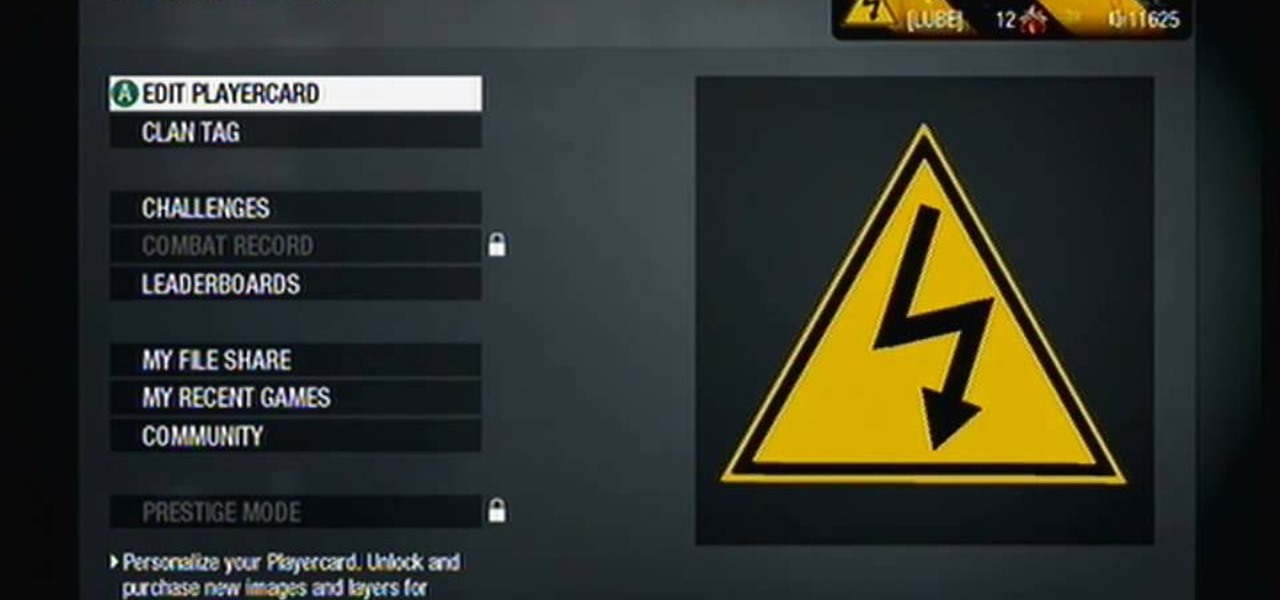
In this clip, you'll learn how to recreate the iconic high-voltage hazard sign as your Call of Duty: Black Ops playercard emblem. Learn how to create a electrocution risk symbol in the Black Ops Emblem Editor!