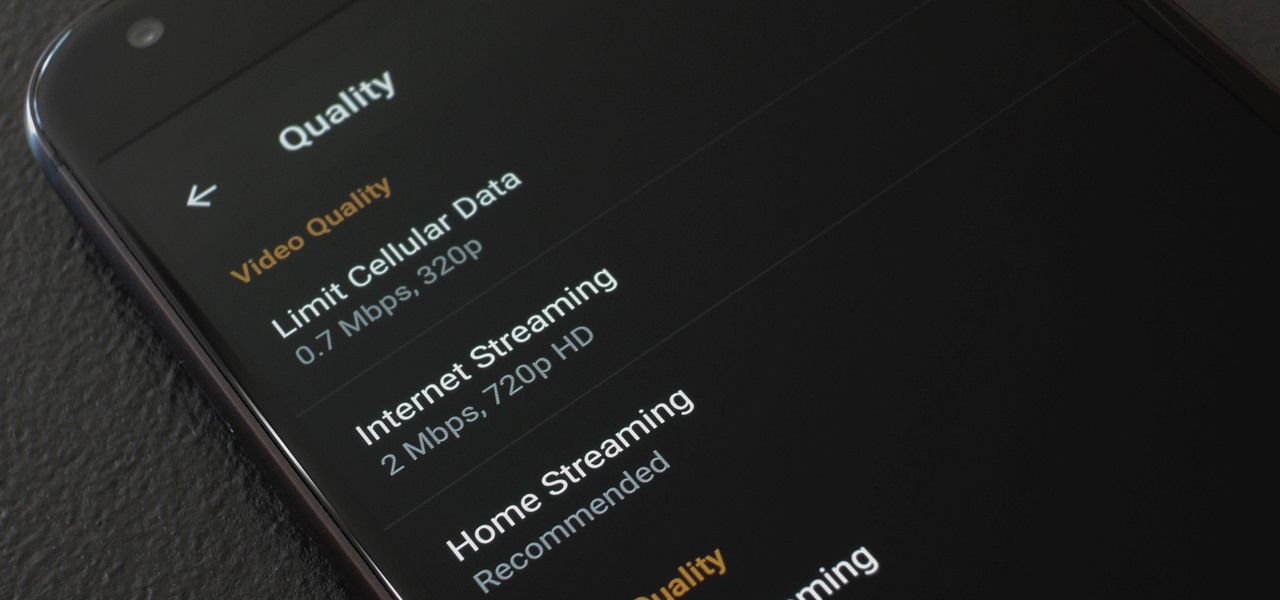
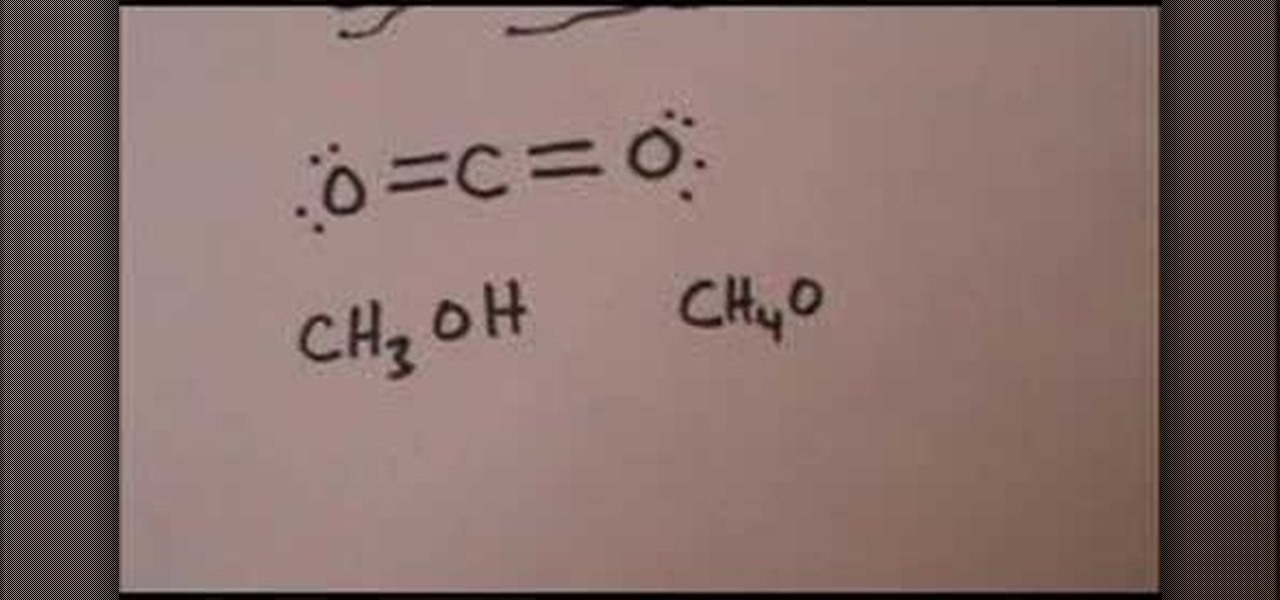Chromecasts can make for some fun nights. Whether you're setting up a collaborative YouTube watch list, letting everyone add to a giant party playlist, or playing games like Cardcast and Big Web Quiz, Google's streaming media stick is a hit by all accounts.
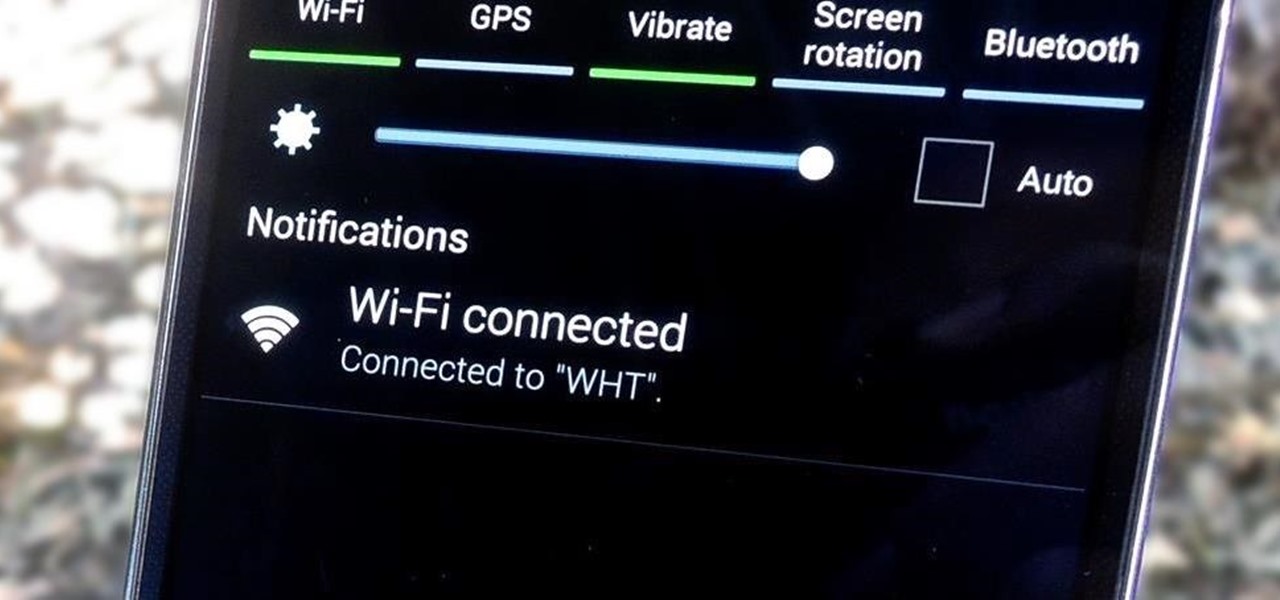
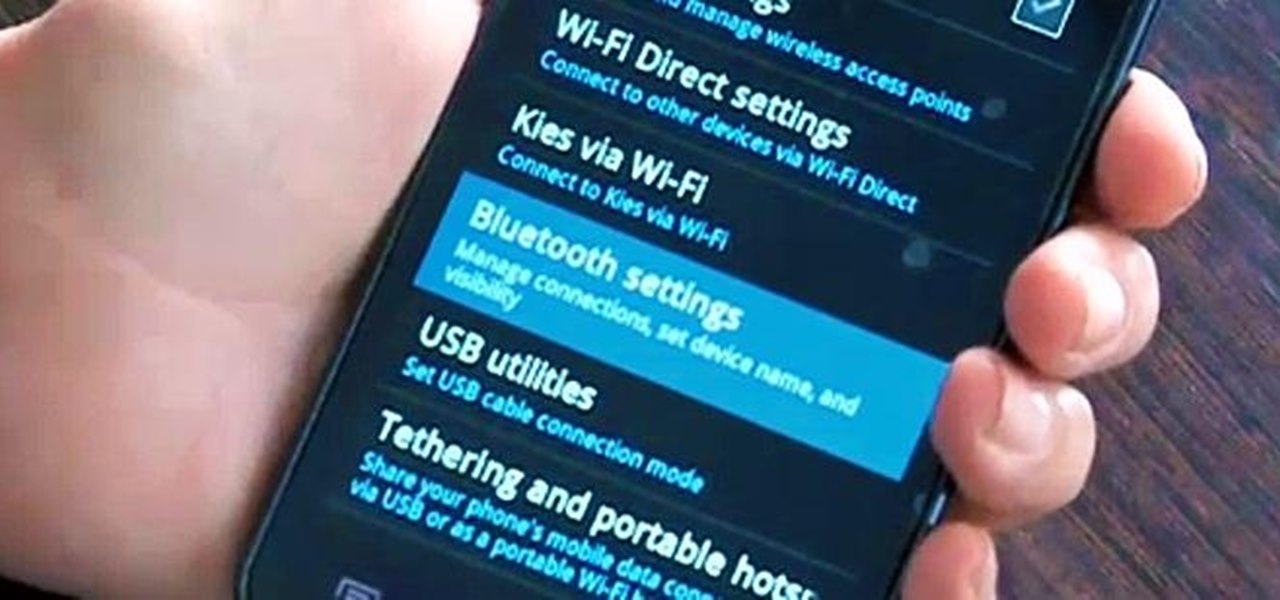
Call it OCD if you will, but I make it a priority to have a clean Notification panel. Like a chalkboard that isn't wiped spotless, I get an unsettling feeling that something in the universe isn't complete when there's unnecessary clutter in the drop-down. For this reason, I loathe the fact that I can't remove the "Wi-Fi connected" tile from my "Notifications."

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

Samsung is helping photographers in getting more utility out of their cameras with their new Samsung Smart Camera App. With it, your device becomes a powerful viewfinder for your Samsung camera, allowing you to not only frame shots, but control multiple aspects of the camera, right through your phone.
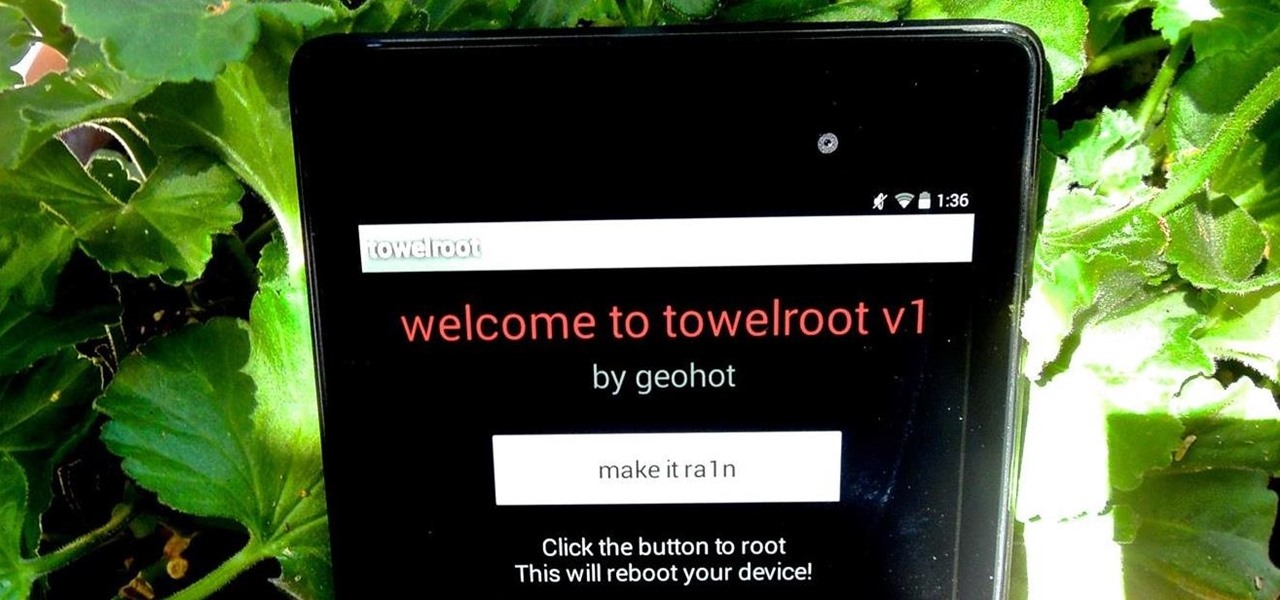
Rooting your Nexus 7 tablet is now easier than ever. Previous rooting methods required connecting your tablet to a computer and using any one of a number of programs and/or ADB commands. Now, it's as easy as downloading an app on your phone and tapping one button.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give it a try, I'll show you how it's done right now. All you need to is a Wi-Fi network and a specific Android app to control your computer with your Android tablet.

No matter how much of a gamer you are, typing with your PS4 controller is a bitch. Let's just be real. Having to move left, then right, then down, for every single letter can make writing a message very time consuming; so much so that I usually avoid messaging altogether.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

A deck of cards may be a magician's best way to demonstrate his or her's sleight of hand, but for the prankster, it's the perfect way to deliver a shocking 300 volts of electricity! And that's exactly what I'm going to show you how to do today. Stuart Edge used it in his "Electric Shock Kissing Prank" to show the ladies how a man can really put the sparks in a kiss.

I've had this idea in my head for almost a year now. I knew what I wanted to do, but wasn't sure if it would work. After a long time of armchair-engineering, I decided that the best way to test my idea was with a soldering iron and a screwdriver.

Google Now is an extremely intelligent personal assistant that automatically updates and prepares the most pertinent information for you on your Android device. Traffic updates, alternatives routes, weather conditions, and other important data is constantly being monitored and updated for you.

MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consumed, and of course, whether they've paid or not.

The reason that Facebook is so popular is because it connects us to people that we could have never been connected to before. When people log on, they look for messages, comments, likes, and any other notifications that connect us to those people. These same notifications, though, distort our view of Facebook. We tend to appreciate statuses (I prefer stati) that have more likes. We're geared towards people that have more friends, so we tend to like pages that already have hundred of thousands...

Several people have been reporting Wi-Fi problems after updating to iOS 6 on both iPads and iPhones. The connection might work sometimes, but it usually cuts out or takes forever to connect to anything, only to time out shortly after.

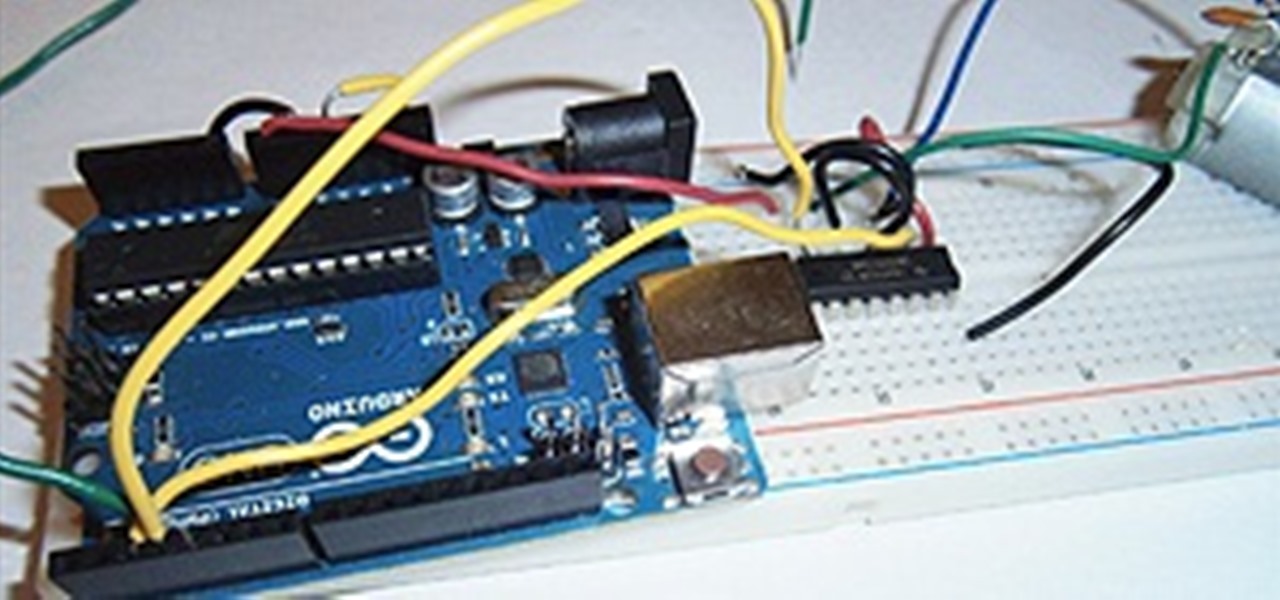
Drinking games just got a little more sophisticated (kind of). Startup SmartThings built this awesome Arduino-based machine that automatically pours a shot whenever the US wins a medal in the 2012 Summer Olympics. Goldschläger for gold, Cuervo for silver, and Jack Daniels for bronze.

I love robots. They have the potential to evolve into Asimovian destroyers of the human species, but have only just mastered the art of cleaning my rug. They have an ever increasing cool factor and a growing number of cheap and simple components that let the hobby roboticist reach for the burning miasmas of plasma. But to get to the stars, we need to start with the basics.

First of all you have to check the breast collar which is attached and hanged to the saddle. You have to maintain safety by not ducking under the horse neck. It is better for you to go around and do your job. Keep your head away from the horse head while attaching a collar. Ask your handler to hold the horse for you. Now pick your breast collar up and reach around the horse. Don’t duck under the horse head, but bring the collar belt to your side and then attach it to the ring on the saddle. N...

Design your own clothes by making sewing patterns, but pay attention to the details. You Will Need

The docking accessories available to owners of the Motorola Droid Bionic unlock several different functions dormant in the Android smartphones. The Vehicle Navigation Dock allows you to easily access Verizon's GPS system on the go, or give vocal commands so that you stay safe and handsfree with the Droid Bionic. The HD Station Dock allows you to connect your smartphone to a TV and view photos or use applications on the big screen. This guide by Motorola shows you how to access the different f...

What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden emergency HDD can only be controlled by your key, regardless of how many people use your computer.

In this video we learn how to make a purse or handbag out of duct tape. Start out with your duct tape and a flat surface. each piece needs to be 8 inches long and laid out in front of you. Then, stick these on top of each other. Once you do this with two, take your other pieces and overlap them, then connect them together. After you have the four strips together, use a different color around the edge of this, making it with the same process. Now you will have a pouch, which will be your purse...

So you've watched this video, done your research, and decided that you want to flash the firmware on your XBox 360 with a LiteOn DG-16D2S rev. 7485 disc drive. Good for you! This video will walk you through the whole process. Be very careful, as messing up in small ways at any point can ruin the results which, when done properly, are really awesome.

If you have never dealt with wire color-coding then Old64goat takes you through a very elementary tutorial that will give you the helpful aid needed to deal with common household wires. The first cord that is reviewed is the three pronged cord. The color wires contained within it is the green wire which is the ground prong, the white wire which is neutral, and the black wire which is the heat. Old64goat then demonstrates where the wires are connected to on the prong. He even gives out helpful...

In this Education video tutorial you are going to learn how to draw the Lewis structure for carbon dioxide & methanol. Carbon dioxide is CO2. Oxygen atoms don’t bond together. So, carbon atom has to be in the center. Oxygen has 6 valence electrons and carbon has 4. Hence, carbon wants to form 4 bonds and each oxygen atom wants to form 2 bonds. So, two each electrons of carbon will bond with 2 electrons of each oxygen atom. The Lewis structure for CO2 will be ( …. O=C=O….). The 4 dots within t...

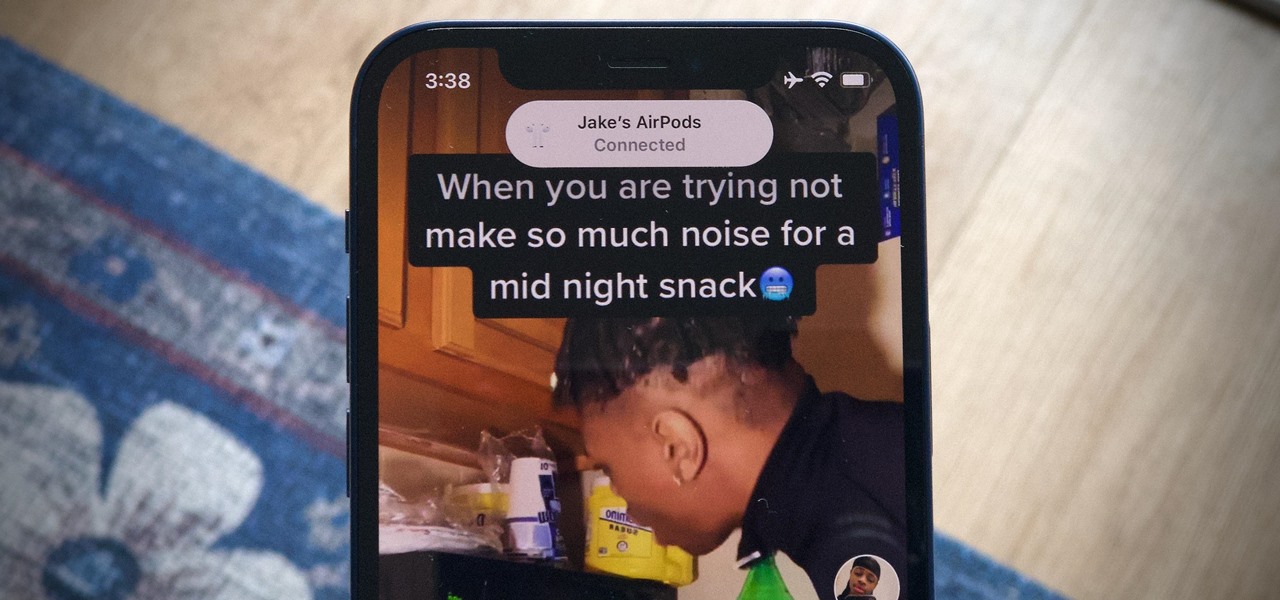
You're watching a YouTube video on your Mac, then go to check something on your iPhone. Of course, because you had a video queued on iOS, your AirPods automatically switch from your Mac to your iPhone. Now, your Mac's YouTube video is playing out loud, and you have to reroute your AirPods back over to macOS. Luckily, there's a hidden setting you can change that fixes this whole issue.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

True home automation doesn't require interaction from the user. But let's be real, no system is going to be 100% autonomous. You'll always need a manual override for situations programming can't account for. So what's the best manual override system? I'll tell you right now, it doesn't involve yelling at Alexa or Google.

With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

When you're on the go, Plex makes sure your media always stays with you. Just install the server app for Mac or PC and enable remote access, then you can stream movies and TV shows from your computer to your phone over the internet.

Young girls, especially those who live in areas where HIV is epidemic, like sub-Saharan Africa, are particularly vulnerable to becoming infected with HIV. A vaginal ring containing the antiviral agent dapivirine has been shown to decrease the chance of developing HIV-1 in adult women over 21 and now in the first step for use in adolescents, the ring has been shown to be safe and well-tolerated in that younger age group.

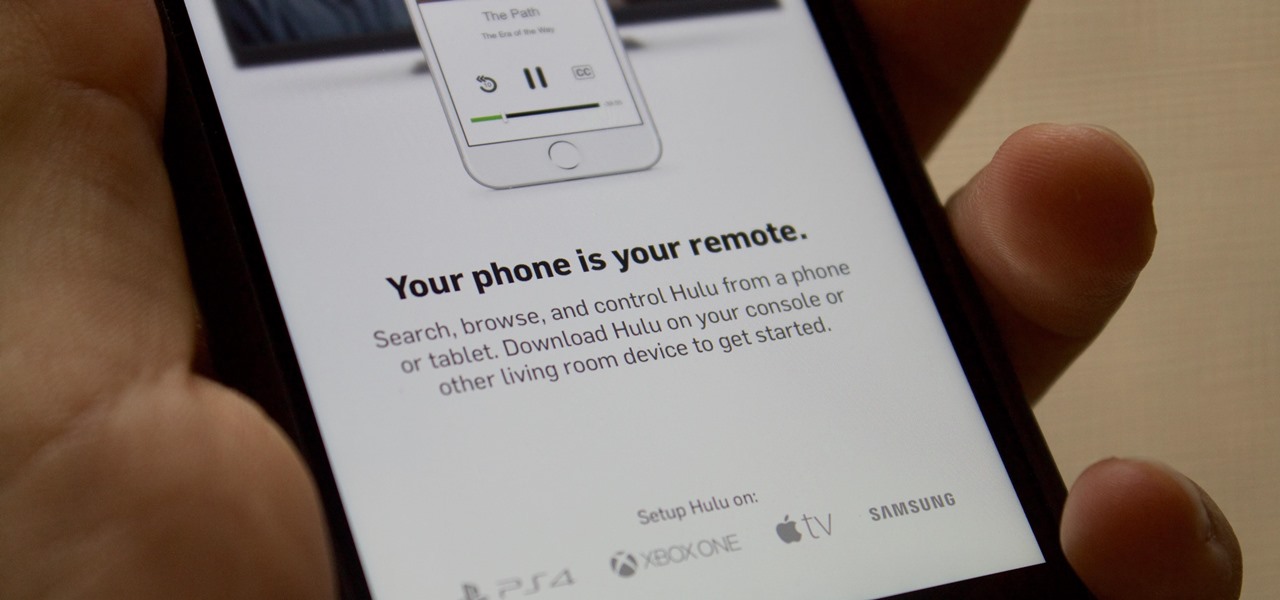
Your smartphone is the perfect place to watch Hulu on the go. Whether you're looking to catch up on your shows in a hotel, or your phone is the only screen available, mobile streaming can be a lifesaver. But what about when you have access to a TV? Wouldn't you rather watch your favorite Hulu Original on the big screen than on your comparatively tiny smartphone?

Killing more than 29,000 people each year, infection with Clostridium difficile (C. diff or CDI) is the most common healthcare-associated infection in the US. In a disturbing development, new research reveals recurring cases of the infection are soaring.

Type 1 diabetes is an attack on the body by the immune system — the body produces antibodies that attack insulin-secreting cells in the pancreas. Doctors often diagnose this type of diabetes in childhood and early adulthood. The trigger that causes the body to attack itself has been elusive; but many research studies have suggested viruses could be the root. The latest links that viruses that live in our intestines may yield clues as to which children might develop type 1 diabetes.

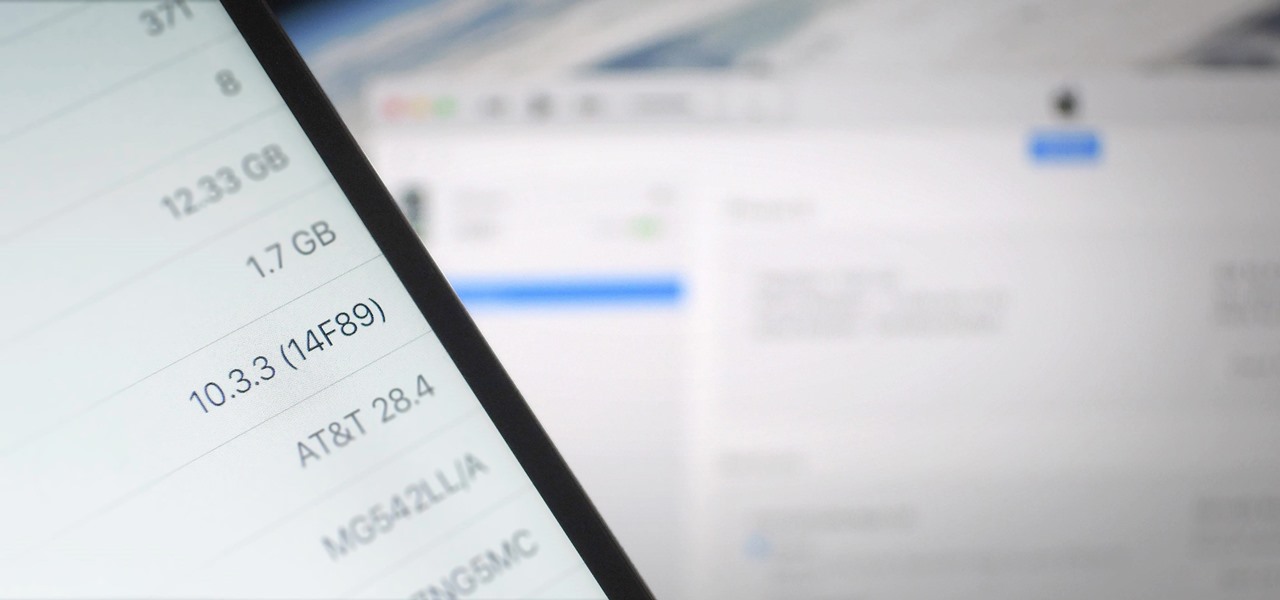
There's lots of new stuff in iOS 11, but just because things have changed doesn't mean they're better. So if you've updated to Apple's latest OS and decided it wasn't for you, you'll be happy to know that you can still go back to iOS 10.3.3.

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.