
How To: Do dumbbell walking lunges
Learn how to do dumbbell walking lunges. Presented by Real Jock Gay Fitness Health & Life. Benefits


Learn how to do dumbbell walking lunges. Presented by Real Jock Gay Fitness Health & Life. Benefits

Let's start with the bike: The most important thing on your bike, is your brake system, you will need the brake lever on your handle bars. When performing a wheelie, this will help you control speed and prevent you from falling on your butt. Your rear brake has to function properly or you will face the risk of falling.

Connecting your Nokia N900 smartphone to a wireless hotspot or your home wifi network is just a few quick taps away! Take a look at this tech support video from Nokia that will tell you exactly where to find the available internet connections on the phone and select the one you wish to connect to.
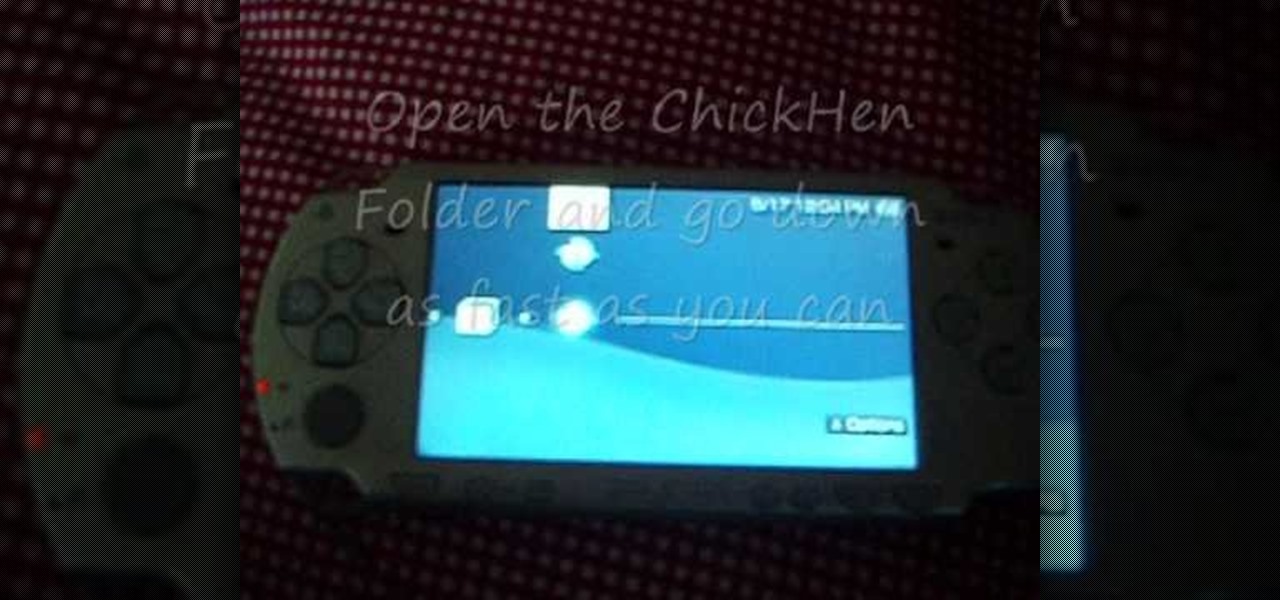
This is part 1 of 2 on how to hack a PSP without a Pandoras Battery using ChickHEN. You will need to ensure that you have firmware version 5.03 ChickHEN R2 in order for this hack to work.

Unless you have unlimited cellular data, you probably connect your iPhone to every Wi-Fi network you come across. It could be a local coffee shop, public library, or just a friend's place. Wherever it is, you'll need to ask for the access point's password if it's a secured network, and that can be a hassle if the place is busy or the owner forgets the credentials. Luckily, Apple has a solution for this problem.
PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

In this post-3.5 mm world, Bluetooth is the most universal option. But a lot of older electronics still don't support wireless audio. Welp, now there's a dongle for that.

After stealing the show at the HoloLens 2 launch and starring in Qualcomm's unveiling the Snapdragon XR2, holographic video conferencing app Spatial has landed a leading role in Magic Leap's second act with the enterprise segment.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.

Apple's update for iOS 13 is not without bugs and other issues, and if those problems become annoying or impede your ability to use your iPhone like usual, you may want to downgrade. Hundreds of new features may not matter if you can't use your iPhone like it's meant to be.

Augmented reality can be more than simply a way to enhance navigation, or superimpose virtual sunglasses onto your face. It can also be a platform for shining a light on important social issues.

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

Ever since Facebook announced Spark AR at the 2017 F8 Developer's Conference, the social media giant has been looking for ways to implement its mobile augmented reality camera platform in the lives of everyday users.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.
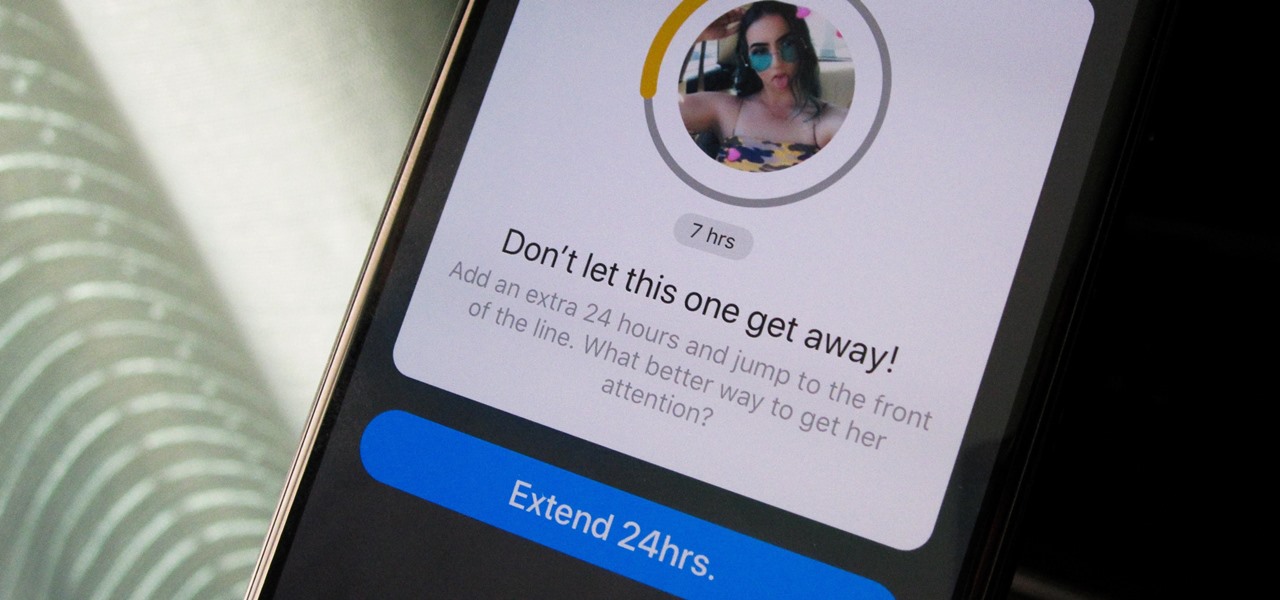
On Bumble, you only have 24 hours to connect with a match. If no message is sent, your match disappears and your chance of a connection is gone, but that doesn't necessarily mean that the other person isn't interested. If they lose their phone or don't receive notifications, they might miss your message on accident. Life happens, so what can you do if your 24 hours to connect are almost up?

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.

Samsung emphasized its goal of streamlined user experience with the unveiling of the Galaxy Note 9, highlighting the flagship's capabilities of seamlessly connecting with other devices. The Note 9's DeX mode makes it easier than ever to interface with a wide array of displays and monitors.

Less than four months after Snapchat introduced its Snappables platform, Facebook has met the challenge with its own AR gaming feature that surpasses the originator.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.
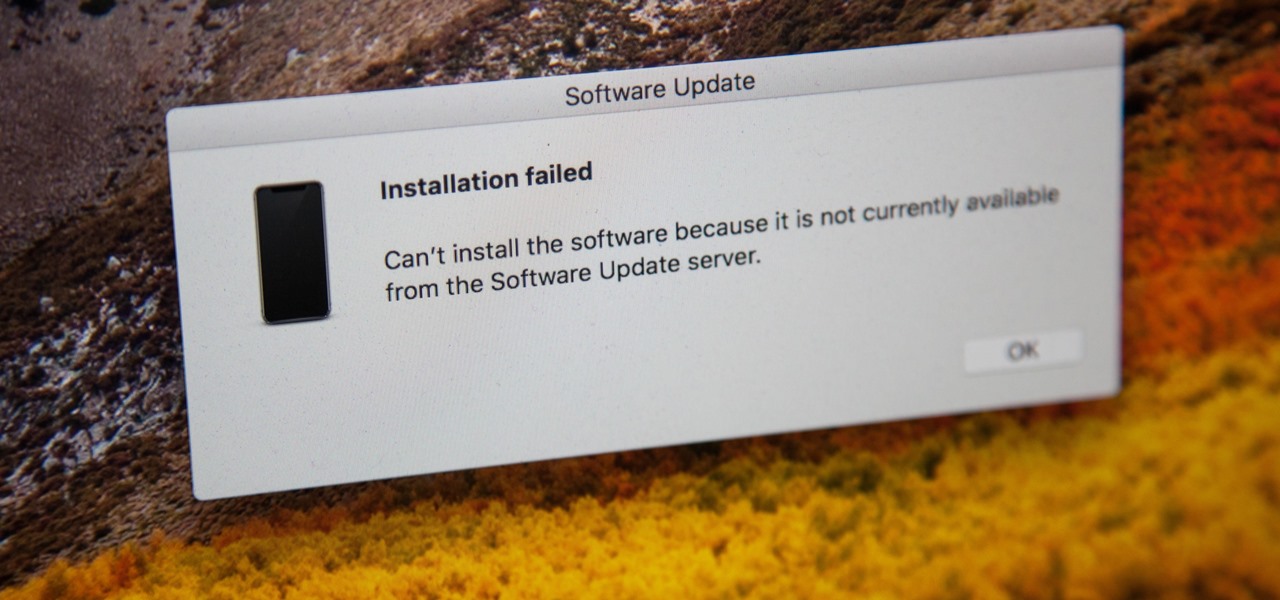
If you're currently running macOS 10.11 or higher on your Mac and connect your iPhone to sync with iTunes, you may get an alert saying that "a software update is required to connect to your iPhone." Here's everything you need to know about what that means, how to update your system, and what to do if updating doesn't work.

When you want to post a breathtaking landscape or picture-perfect portrait that you just took with your DSLR camera to Instagram, Facebook, or some other social platform, there's an easy way to do so — even if you don't have a computer handy, which is typical when you're out and about.

If you have an Apple Watch, you might know that the activity awards you earn can be shared with your friends as iMessage stickers on your iPhone. However, you first have to earn achievements in order to use them as stickers. That changes somewhat with iOS 12, as Apple added animated activity stickers for all Apple Watch users, whether they've earned award badges or not.

Kitten Planet, a spin-off company that grew up in Samsung's C-Lab incubator, has developed a connected toothbrush that teaches and motivates children to brush their teeth better via augmented reality while tracking their performance.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

While Magic Leap may have plans to eventually introduce sign language translation for smartglasses in the near future, students at New York University have demonstrated that such a feat is possible today with a smartphone and a prototype app.

It's human nature to wonder if the grass is greener on the other side. This is no more true than for people who use iPhones, and those who use Galaxy S phones. While iPhones were initially the gold standard for smartphones, Samsung's phones equal them in many ways and surpass them in others. If you use an iPhone and you're on the fence, here's the case for making the switch to a Galaxy S9 or S9+.
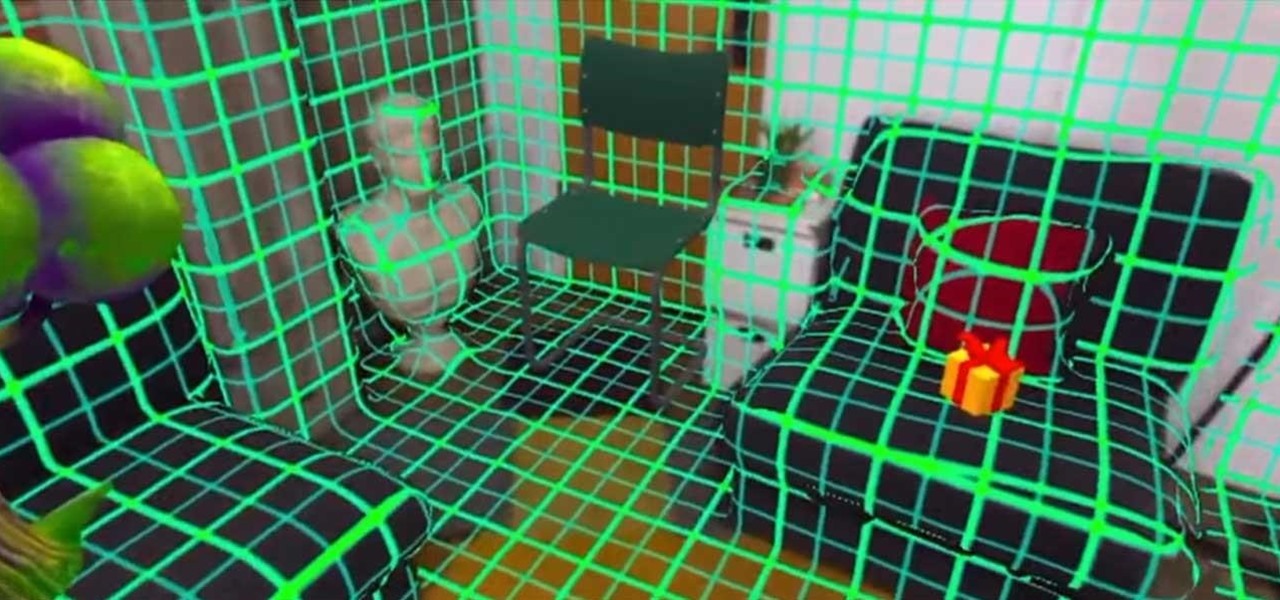
San Francisco-based 6D.ai is preparing to launch a beta of its AR cloud platform that's capable of constructing a real-time dense mesh from crowdsourced data for use in 3D mapping and multi-user AR experiences.

While the consensus among some in the augmented reality community is that the Microsoft HoloLens is the best device available at present, it also remains the most cost-prohibitive option, with the development edition costing $3,000.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.
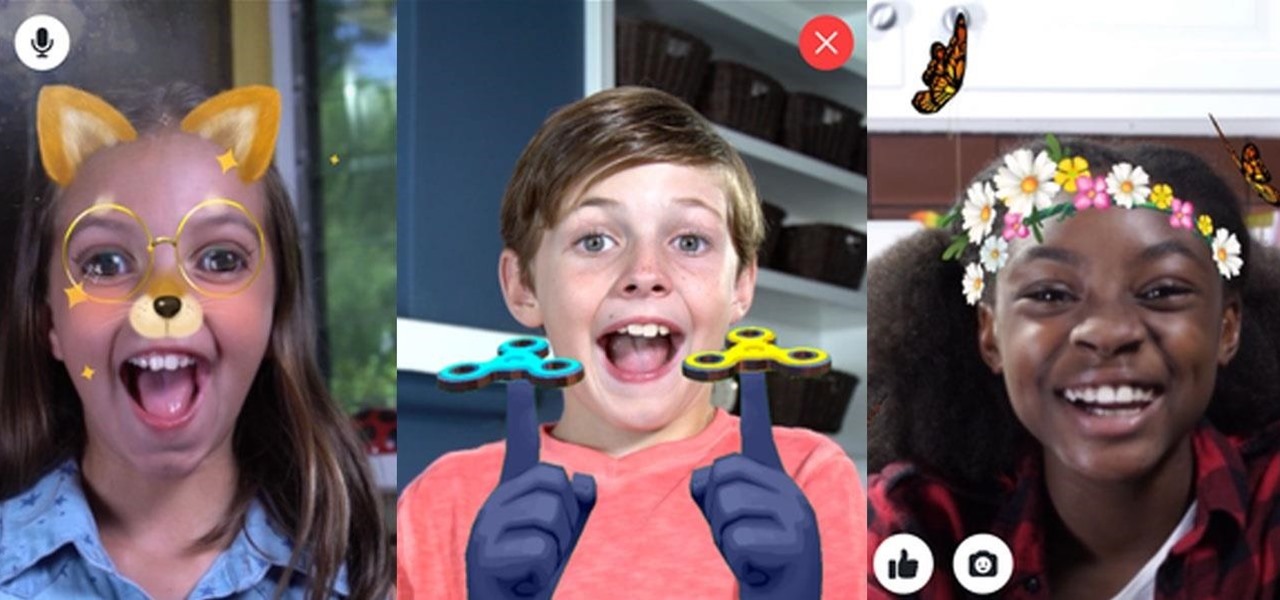
Next to millennials, one of the groups most coveted by brand marketers is "Generation Z," the consumers of tomorrow who were born between 1996 and 2010. On Monday, Facebook established a beachhead with that demographic in the realm of augmented reality by launching Facebook Messenger Kids.