Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

General Motors (GM) seems to have gone to great lengths to avoid lawsuits as it launches its first hands-off driving system in its soon-to-be-launched Cadillac CT6.

Results of an early-stage clinical trial of an HIV vaccine could mean a hoped-for breakthrough in the battle against AIDS.

Tesla founder and CEO Elon Musk offered some insight into how hackers might seek to turn driverless cars into zombie fleets, but remained upbeat about what can be done about it.

"Valar morghulis." Don't know what that means? You should probably download Duolingo for Android or iPhone.

A new case of the still-mysterious Bourbon virus was confirmed in Missouri, likely originating within the state, local authorities said in a June 30 press release.

Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield.

The Galaxy S8 and S8+ come equipped with all of the hardware needed to access live FM radio, but this feature was never really advertised or even spoken about. Thankfully, though, all you need is an app to enable it.

The company that brought us a BB-8 droid controlled with the Force — okay, just a high-tech wristband — is releasing its take on Spider-Man. Toymaker Sphero collaborated with Marvel to release an app-enabled Spider-Man toy equipped with numerous features, as well as games for your smartphone.

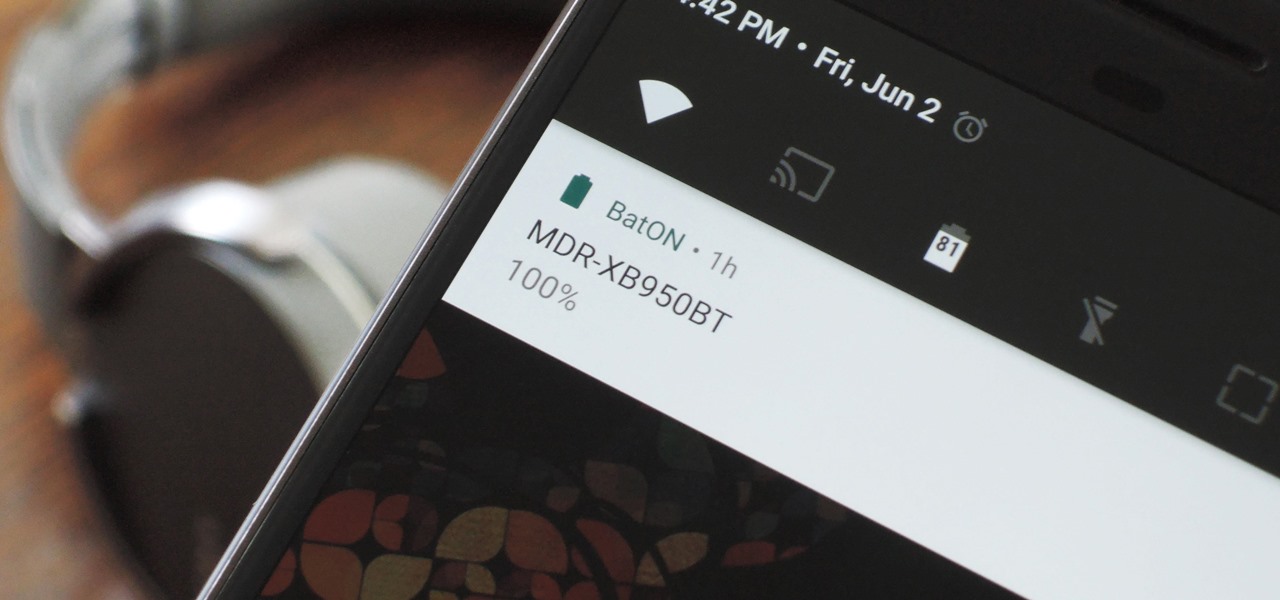
The iPhone has a feature that lets you see how much juice is left in your Bluetooth headphones, but most Android phones are lacking this ability. Thankfully, there's a simple app that'll close this gap in functionality.

The common thread between this week's Brief Reality stories is that augmented reality is beginning to prove its worth as a technology that improves workflows and processes. From customer service to healthcare to manufacturing, augmented reality is helping companies improve productivity.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

How can bacteria that lives in the throat of 10%–35% of people—without causing an infection—cause life-threatening meningitis and sepsis in others?

Overweight kids often become overweight adults. New research suggests a couple reasons why and suggested that there may be ways to intercept that fate.

Antibiotic use in infants has been associated with a host of childhood conditions later in life. Yet when an infection is suspected in a newborn, usually a sample of their blood is drawn to check for the presence of bacteria and 5 to 8 percent of them receive antibiotics while the diagnosis is pending.

There are already a few ways to use your home computer on the go, but none of them feel very natural when you're out and about, and are clunky options at best. Samsung wants to change that with Monitorless, their upcoming augmented reality smartglasses, which offer remote desktop viewing capabilities as well as the ability to switch between augmented and virtual reality modes using electrochromic glass.

We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

Microsoft's HoloLens may the coolest new advancements in technology we've seen in quite some time, and anyone (with deep pockets) can buy one right now. But so far it's been an isolated platform where you experience mixed reality alone and others watch you air tap nothing but air. Developers are working to change that, and we're seeing the first examples crop up online already.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

We've been hearing rumors for months now that suggest Apple will be getting rid of the 3.5 mm headphone jack in the iPhone 7, which will presumably be replaced by an adapter that connects your earbuds directly to the Lightning port. But finally, thanks to Vietnamese site Tinhte, we now have some hard evidence to back up this claim.

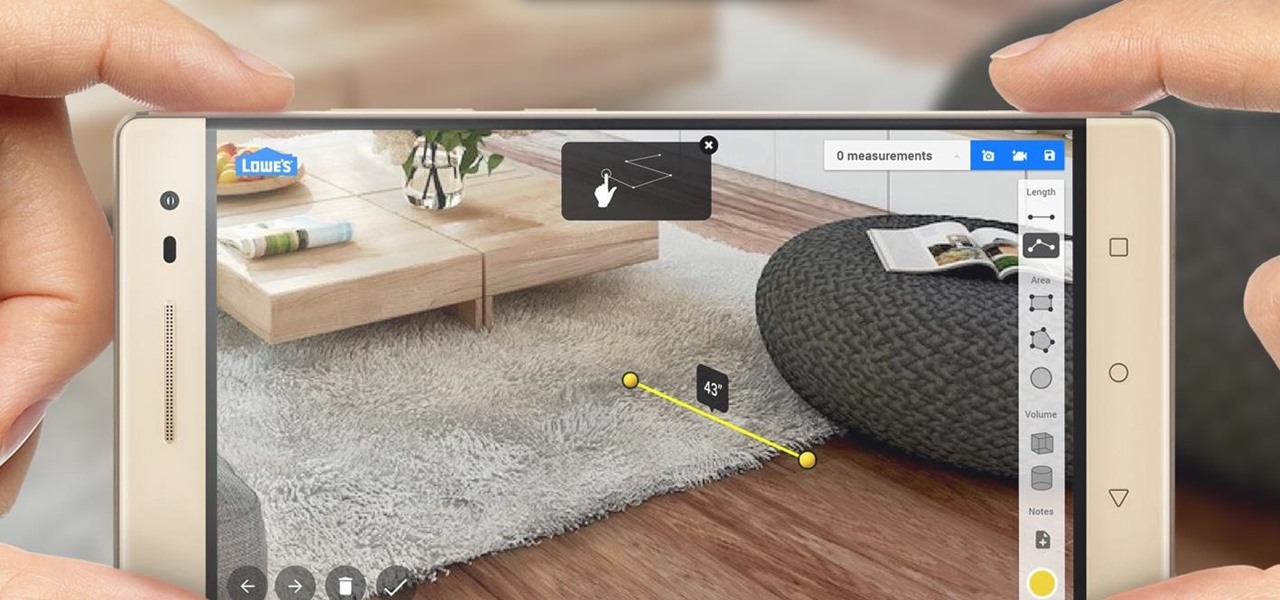
Augmented reality began on smartphones but technical limitations have prevented further development. Google's Tango (formerly Project Tango) aimed to change all that, and with Lenovo's help, they now have their first device.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

If you already have speakers that you love, you don't need to ditch them for an expensive wireless set for convenience's sake. With products like Chromecast Audio, you can turn any set of wired headphones or speakers into wireless versions for much less, and stream music or audio to them from pretty much any device connected to the same Wi-Fi network.

Apple has finally addressed and issued a fix for Error 53, a "safety" mechanism that would prevent your iPhone from booting if you had certain repairs done outside of Apple's official channels.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

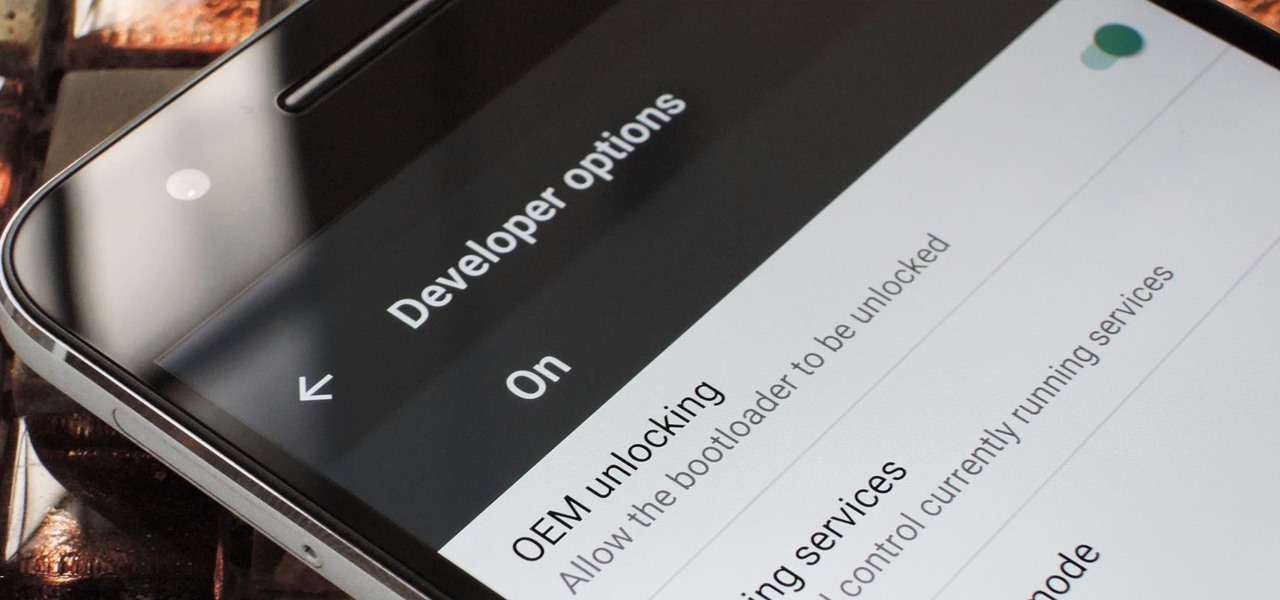
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.

Some of the best images I've seen were shared via Snapchat, but once they're expired, they're gone forever, with no way to view them again unless I want to take a screenshot. But that will, of course, alert the sender.

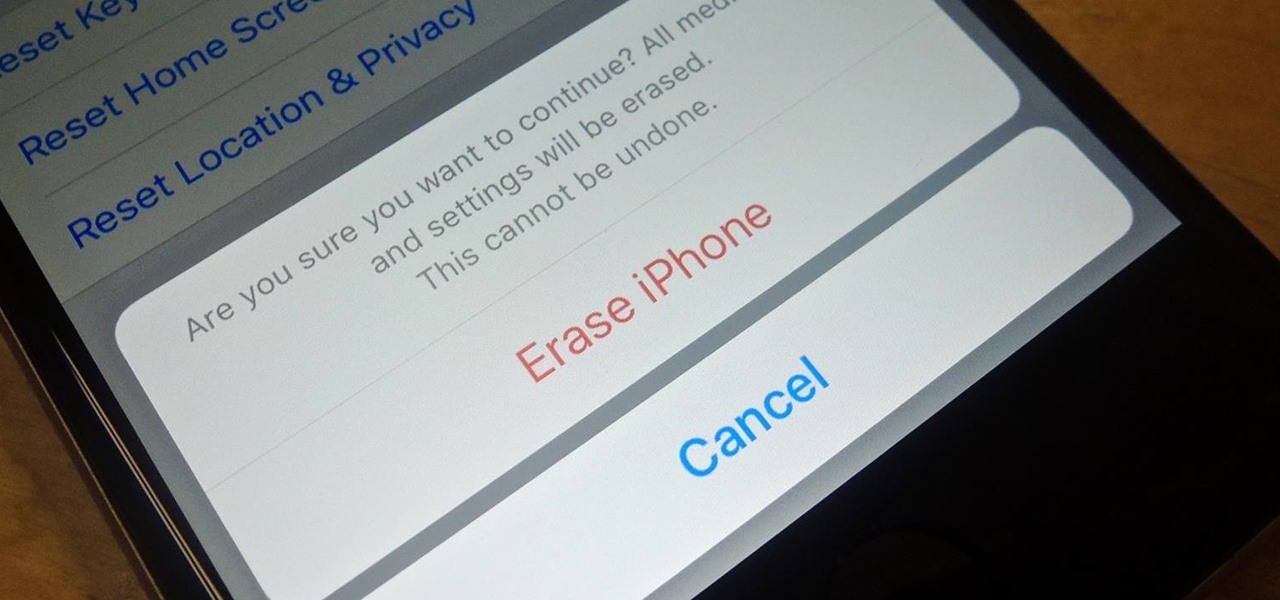
Before you sell your old iPad, iPhone, or iPod touch to a buddy or a company like Gazelle, it's vital that you wipe the entire device of all its content; including sensitive material like contacts, messages, pictures, and videos. There are two easy ways to wipe your iOS device, so let's show you how to do it using iTunes or directly from the device itself.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

Most primary cocktail ingredients just sound delicious. Lime and tonic water? Yes, please. Bitters and simple syrup? Sign me up. Egg whites and... wait... egg whites? In a cocktail?

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

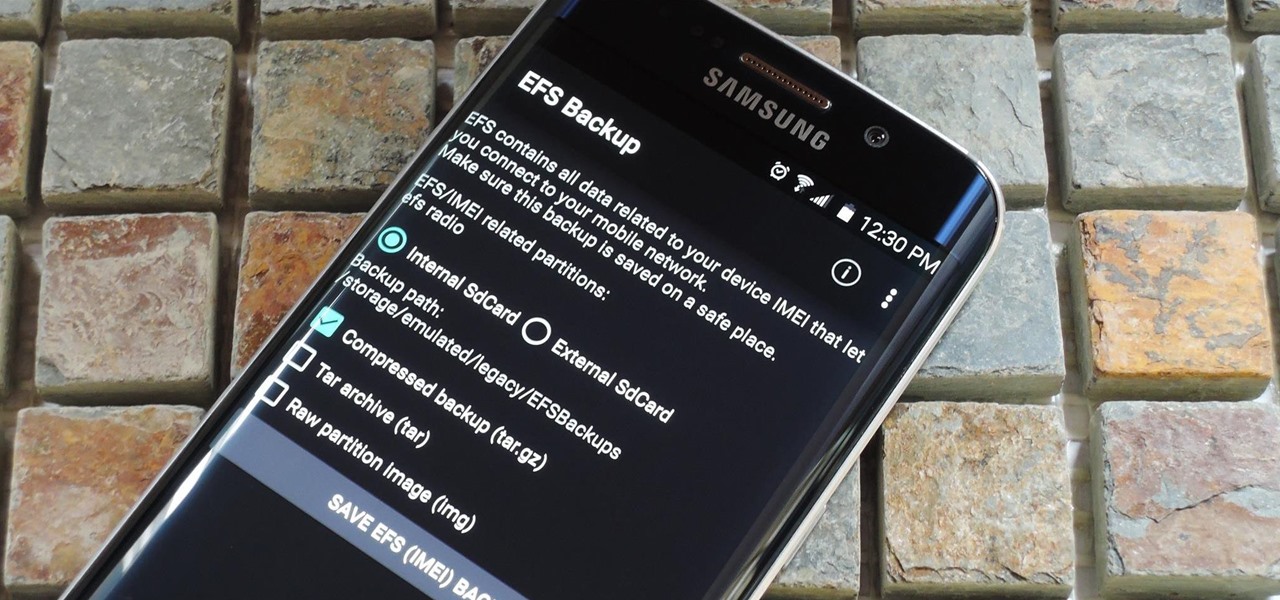
The EFS partition on modern Android phones houses the unique IMEI for your device, which is essentially an identification number that lets you connect to mobile networks. But sometimes, when you're flashing ROMs or restoring backups in custom recovery, the EFS partition can become corrupted, which will prevent your phone from connecting to any type of mobile network.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

These instructions are applicable to both bObsweep models. Follow the video or text descriptions to replace the disinfecting UV lamp on your automatic vacuum.

As someone who loves to run around my neighborhood, the Apple Watch feature that excited me the most was the ability to go out and exercise while listening to music, all without having to lug my iPhone around.

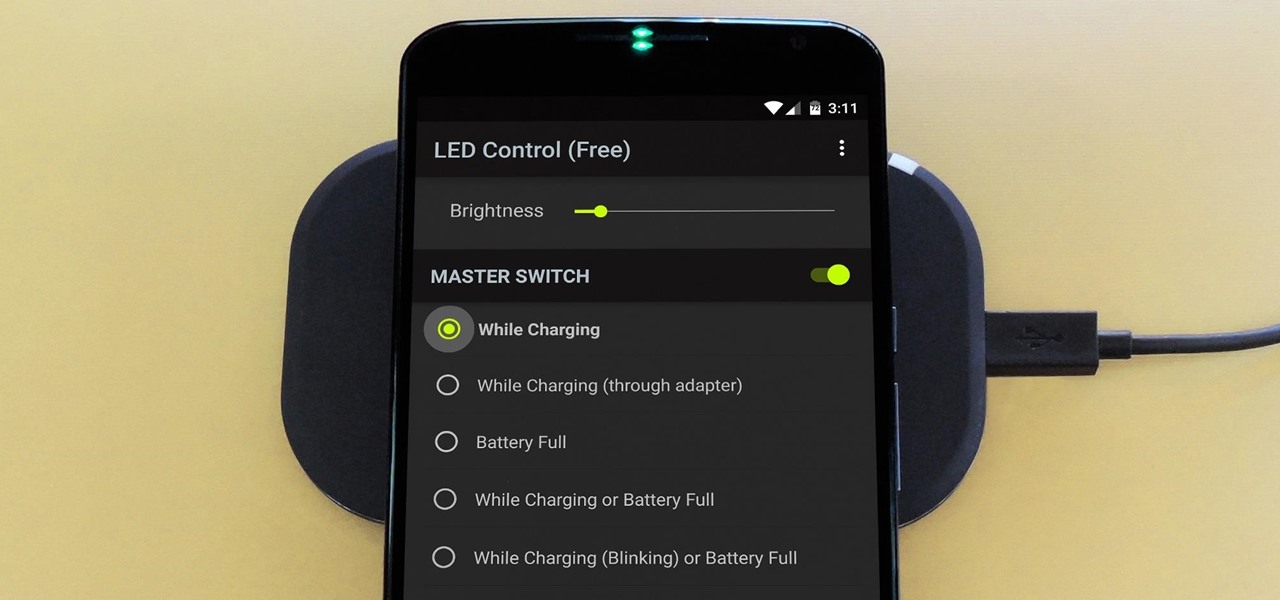
The Nexus 6 has an AMOLED screen that uses virtually no power to display black pixels. To take advantage of this feature, Google included an Ambient Display notification system that shows a black and white version of your lock screen when you get a new message. As a result, the Nexus 6 doesn't use an LED light to notify you of new incoming messages like most phones.

Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.