In this Quick Clip, I'll be showing you how a supercooled soda is transformed into a slushy "slurpee" in under 4 seconds. I was inspired to do this little soda trick by The Super Effect's video on YouTube from a few years ago.

Don't panic the next time you pull an empty tub of butter from the fridge. If you have some heavy whipping cream, save yourself a trip to the grocery store and just make your own. When heavy cream is shaken violently for a long enough duration, it turns to butter—and if you're doing it by hand, it also feels like your arm turns to jello.

While Siri's integration with the iPhone is becoming increasingly substantial, restrictions with the intelligent personal assistant are apparent when it comes to third-party apps like Google Maps, Netflix, and Spotify (unless your iPhone is jailbroken, of course). As an avid Spotify user, it's distressing that I can't use Siri to navigate through the music streaming service's extensive library. In the car, I use Spotify about 90% of the time and it can become increasingly frustrating to chang...

Here's how to make a simple form of a slow burning fuse from materials around the house. WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of this video content is at your own risk.

One of the biggest downsides to the iPhone is that it isn't as easy to customize as other smartphones. It's true that this makes Apple products more secure in some ways, but it also means that you have to jailbreak your phone and void your warranty if you want to change certain things.

Cooking isn't something that interests me much, unless it results in a fast burning fuel and a successful rocket launch!

Planning on getting the iPhone 5, but want to keep your SIM card? The new nano-SIMs that manufacturers are adopting will be even smaller than the micro-SIMs that most of us currently use. It's fairly easy to cut a regular SIM down to a micro-SIM, but because the nano-SIM will be thinner as well as smaller than the micro, cutting it down to size will require a little more work. Photo by Tech Digest

The worst part of moving into a new place is, well...moving. It's tedious, a lot of hard labor, and it can take forever, and don't even get me started on all those labels. It's also one of the only times in your life when everything you own can be stolen at once, since it's sitting in a movable container. Rather than risk losing everything, try this DIY Moving Truck Alarm System by Tim Flint that lets you know when the loading door is opened so you can catch would-be thieves red handed.

Motorola launched a new webpage on Friday that tells Android users how to unlock the bootloaders on a limited number of new Motorola smartphones and tablets. This new 'Unlock My Device' page helps demystify the process and make it easier for users to customize their phones.

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

Assuming that you are living north of the equator, ‘tis the summer season for brewing your own sun tea. Unlike the conventional method of dunking tea bags in boiling hot water for several minutes, sun tea is brewed over the course of several hours through the natural heat of direct sunlight.

Looking for ways to hack your favorite games without having to take the risks of Cheat Engine? This video shows you how you can hack the web game Swords and Sandals 2 without having to rely on any program at all.

Doing electrical work is one of the most intimidating tasks for a novice home repairman. But if you know what you're doing, the risk is pretty minimal. In this clip, Mark Donovan of HomeAdditionPlus.com shows us how wire a combo outlet with power.

If you're new to DreamCoder for PostgreSQL, one of the first things you may want to know how to accomplish is to connect to a remote PostgreSQL database. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a connection between a given PostgreSQL database and the DreamCoder for PostgreSQL, take a look!

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is to connect to a remote MySQL database securely via SSH tunneling. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a secure connection between a given MySQL database and the DreamCoder for MySQL, take a look!

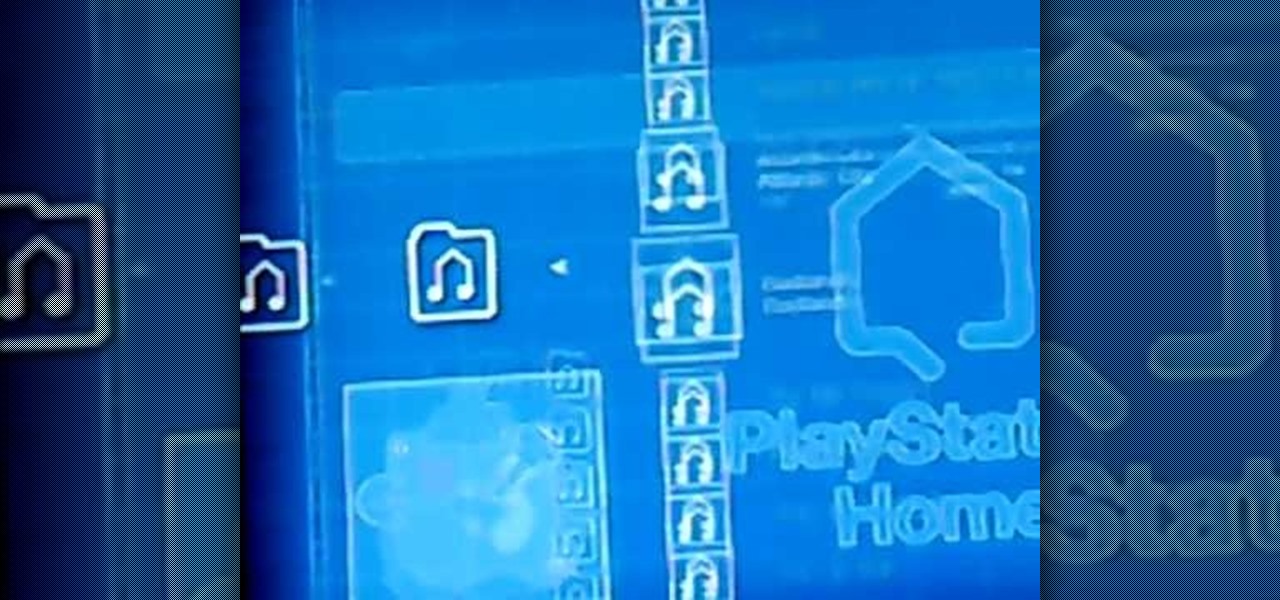
This video will show you how to connect your Playstation 3 to your Windows computer via WiFi, which will allow you, in turn, to stream media from your computer to your television. Watch this how-to for a step-by-step walkthrough.

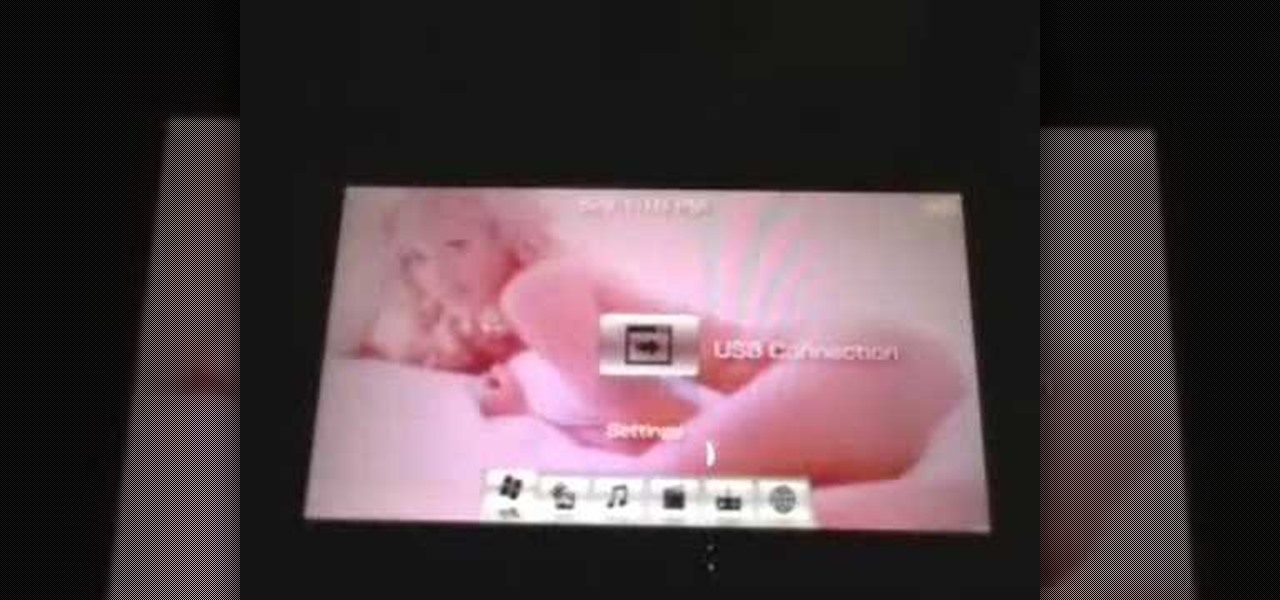
If you’re having trouble getting games on your memory stick, this video will walk you through the steps of just what you will need to do to compress files onto a thumb drive. There are a variety of steps you will have to follow and you’ll have to have a little bit of time to wait for your game to compress but the effort is well worth it.

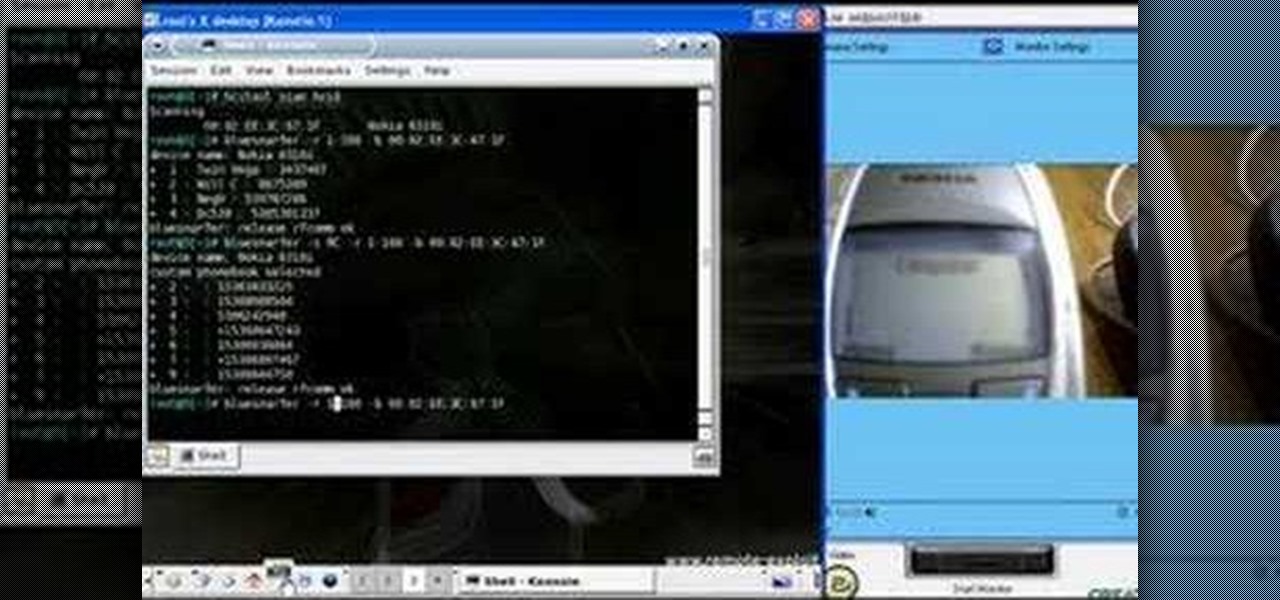
Check out this video tutorial to see how to bluesnarf a Nokia 6310i handset (cell phone). What is Bluesnarfing exactly?

These days, everything is connected. No, really — we mean everything. Your phone, your smart speaker, and even appliances like stoves and refrigerators can be connected and communicate with one another. Welcome to the Internet of Things, the start of our interconnected future. It's projected by 2027 that there will be more than 41 million internet-connected devices in use around the world.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

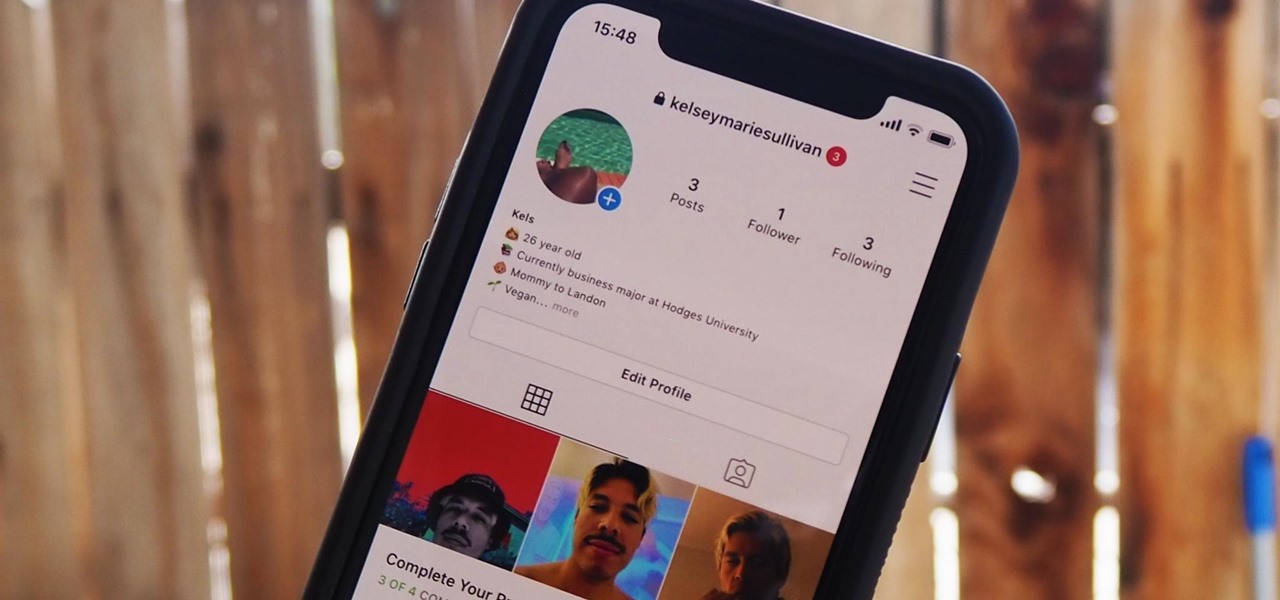
Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

Without an available browser, it is challenging to enjoy media on your Nvidia Shield outside of the apps on the Play Store. It is because of this limitation that file transferring is vital, as only then can you enjoy your movies and music.

Ever since Microsoft sunset Windows Phone, they've been working with Android to tap into the growing mobile device market. The tech giant has uploaded over 80 apps to the Play Store for any Android user to download, but some features Samsung has hoarded for themselves.

With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected.

Android 11 won't be available as a beta update for Pixel devices until May 2020. Until then, the only way to try the latest Android version is by manually installing it. Usually, this means carrier models are left out since their bootloaders are locked, but there's still a way to get it done.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Although the Health app mostly focuses on fitness, Apple has slowly added features to help with other aspects of well-being, including hearing. In iOS 13, there's now a headphones volume tracker in Health that monitors audio levels and lets you know when your music, podcast, movie, or whatever else is too loud.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

One of the biggest reasons to go with an iPhone over an Android device is Apple's interconnectivity. iPhones, iPads, and macOS devices are all connected in a way that allows seamless transition between devices. Android lacks such a feature by default, but that isn't the end of the story.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

While the portability of mobile phones makes gaming convenient, it isn't a perfect playing experience. With touch controls, small screens, and limited specs, smartphones lack the comfortability of dedicated gaming devices. But with a few tips, you can enjoy games as if you were playing on the Nintendo Switch.

When it comes to the business of augmented reality, companies that aren't already introducing new products or apps are focused on producing the AR technology of the future. But in the realm of real products and apps, Magic Leap continues to show off what its headset can do, this time via a new app that transports users to the ocean's depths.

For the first time, you can officially use a computer mouse with your iPhone, thanks to Apple's new Accessibility settings in iOS 13. It works for all types of Bluetooth mice, so if you have one, it'll already work. Plus, those with wireless receivers and even wired mice are supported by using a USB to Lightning adapter.

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.

If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true.

Extra hardware buttons have become a trend with smartphones lately. Often, these are unmodifiable buttons designed to launch a voice assistant. That isn't the case with the BlackBerry KEY2. Making a return from the KEYone is the Convenience Key, which also received an upgrade.

Earlier this year, with the Developer Preview, we got a tantalizing glimpse of Google's upcoming Android 9.0 Pie and a whole slew of new features that comes along with it, such as iPhone X-like gestures and improved security features, to name a few. With its announcement at Google I/O, Android Pie just got a lot more accessible.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.