This step-by-step guide will show you how to make moonshine. To make moonshine you will need the following: A pot with a lid, beer, a big bucket, ice, a jug, and a lot of copper tubing. Put the pot on the stove and fill it with beer. Place the lid on the pot and attach the copper tubing to the lid. The tubing needs to go up about 1 foot and bend at 90 degrees. Bend some of the copper tubing into a spiral. Place it into the bucket with one end coming in, and another going through a hole at the...

In this economy being competitive for a job means your application must stand out above the rest. Here's how to write a cover letter to successfully introduce your resume. Make sure your cover letter follows business letter format. Your name and address must be written at the top left corner. The employer's name and address are written just below. The letter should be addressed to a specific person within the company. Paragraphs in a business letter are not indented, but instead are left just...

One of the coolest features on a Blackberry is BBM or Blackberry Messenger. BBM allows you to talk to anyone with a Blackberry, anywhere in the world, absolutely free! You can send messages back and forth and you phone will even keep a record of the conversation in case you need to reference something later.

This video shows you how to get a really cute Alice in Wonderland look. The steps are simple to follow.

Even if you're a master at the grill, dealing with the tank can be a little intimidating if you've never done it before. But there's really not much to worry about. Exchanging or refilling your gas grill tank is easy to do.

This four-part video tutorial is furnished by the (FCC) Federal Communications Commission shows you how to get ready for the digital television transfer. Is your television ready for digital? By February 17th, 2009 TV stations will stop broadcasting in analog and broadcast only in digital. Your TV needs to be ready so you can keep watching. Digital television, also known as DTV, is here, and after February 17th, TV stations will turn off their analog signal. The FCC wants to be sure you are r...

The Department of Biological Sciences at the University of Alberta brings you this video tutorial specifically relevant to your student laboratory courses, specifically microbiology. If you're a student at any school of biology, this information will be helpful for learning how to mix gradients with a gradient mixer in the lab.

In this fitness how to video Lucas Rockwood, demonstrates Sun Salutation A from the Ashtanga-Vinyasa & Power Yoga traditions. The breath is meant to synchronize with the movement so that entire practice is like one long breathing exercises. Inhales are expansive, strong breathes while exhales are relaxing and opening.

When you're sharing a printer, dealing with cables and networking can be a hassle. Having a printer with built-in wireless or using a wireless conversion kit for standard printers, allows easy sharing of your printer with multiple computers.

Ham radios are a form of amateur radio that anyone can use. This is a great video series for anyone looking to connect with other random people through wireless means.

Why pay for a movie when you can get it for free? Thanks to Movies Anywhere, you can claim and download a video for your digital film collection right now at no cost. And getting your freebie flick couldn't be any easier.

Keeping the books in order is one of the great challenges every business owner faces. Having a great product or service is one thing, but managing the minutia of invoicing can trip up a lot of small- and medium-sized businesses.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

If you're trying to learn a new skill, you wouldn't want to waste your time learning from someone with sub-par experience. No, you'd want to learn from the very best of the best to ensure you're getting a quality education.

Your Galaxy's lock screen already lets you know there's no SIM card installed if it's missing on your device, so there's really no need to have a persistent icon for it on the status bar. If you want to hide the pesky symbol and accompanying notification for good, there's a nifty app you need to check out right now.

Communication is an essential skill for successfully launching products. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

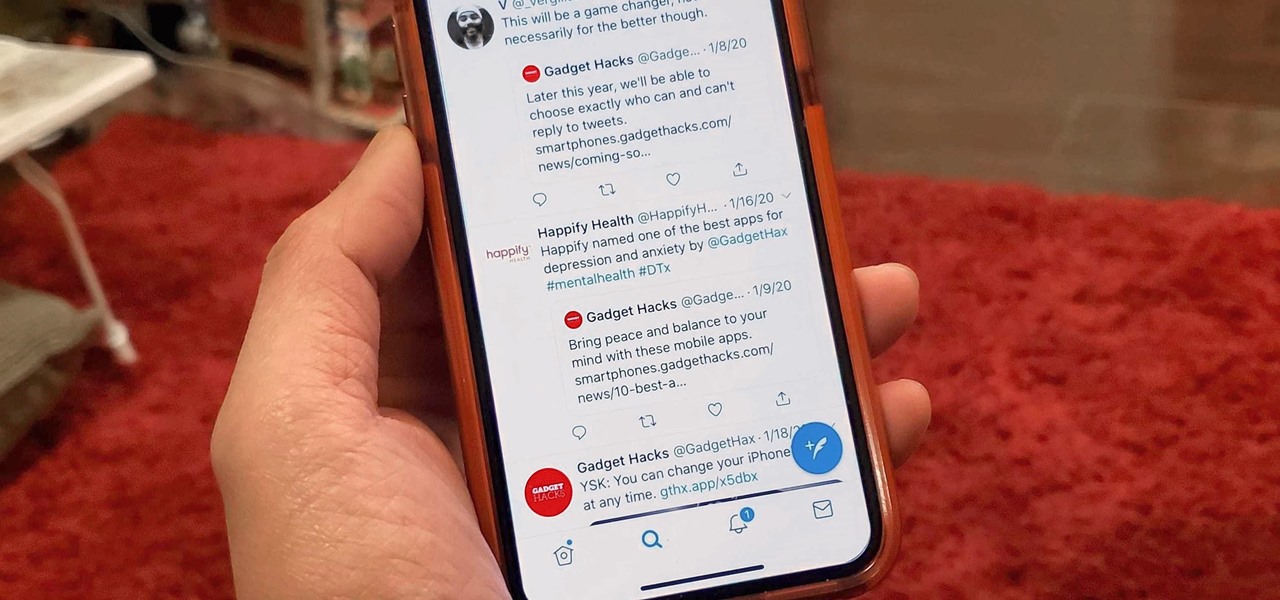
If there's an influential tweet, you can see what people are saying about it by reading its comment thread. But what about quote tweets, aka tweets someone posted on their own timeline that quote the initial tweet? These don't show up in comment threads, but there is a way to find them.

Whatever it is you're into, Facebook Groups are a great way to connect with others that share your interests. And beyond matching you up with like-minded people, Groups also give you access to deals on items, help you organize play dates with families in the same area, and so much more.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

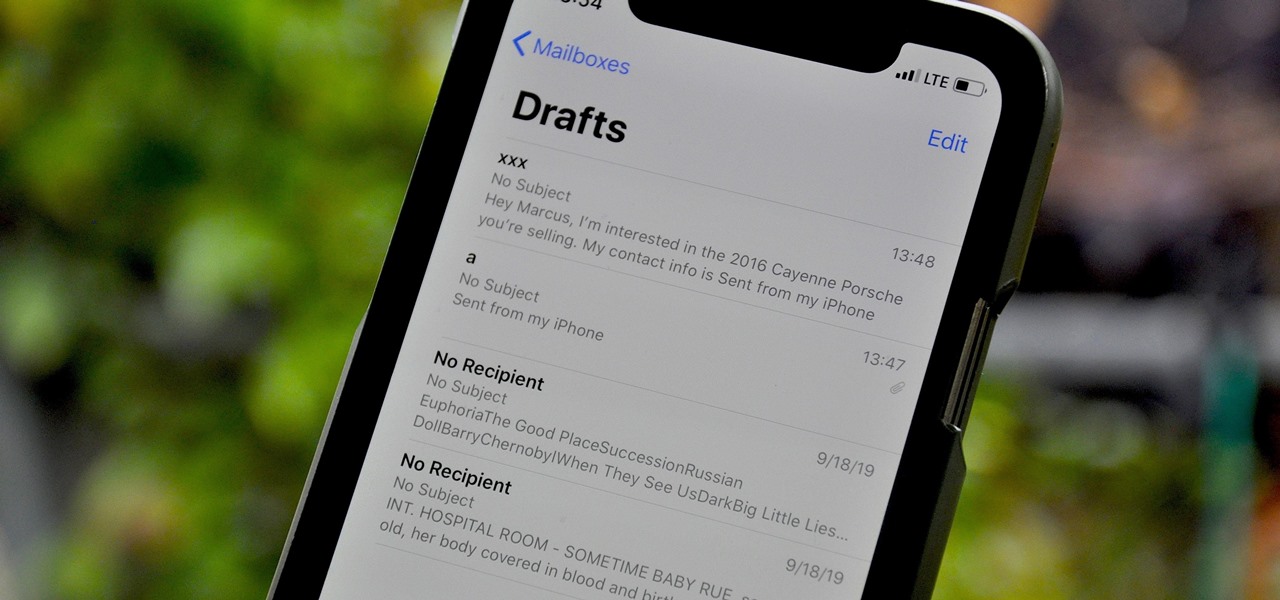
All of your partially written, unsent emails live in your "Drafts" folders, in limbo until the day they are sent off or deleted. In Apple's Mail for iPhone, you can access all drafts from all accounts in a combined "All Drafts" folder from the app's main Mailboxes list — but only if you added it manually. But there's an even better way to access all of your drafts in Apple Mail in iOS; it's just not obvious.

After drawing attention from nostalgic Gen Xers for its Motorola Razr reboot with a foldable screen, Lenovo has a new augmented reality smartglasses concept that the company hopes will also turn some heads.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Most of us have had a cloud-connected address book for years now. The result of this is an ever-growing contact list that will continue to get harder to navigate and manage. With the increased size of our contact lists, it becomes more important to sort contacts in a way that works best for us.

Apple might be a secretive company, but it's showing its hand these past few weeks. The release of iOS 13 was met with much excitement for its hundreds of new features but also frustration over the numerous bugs. Apple soon released iOS 13.1, then iOS 13.1.1, as a patch for some of those bugs, but clearly they weren't enough. How do we know? The company just released iOS 13.1.2 today, Monday, Sept. 30.

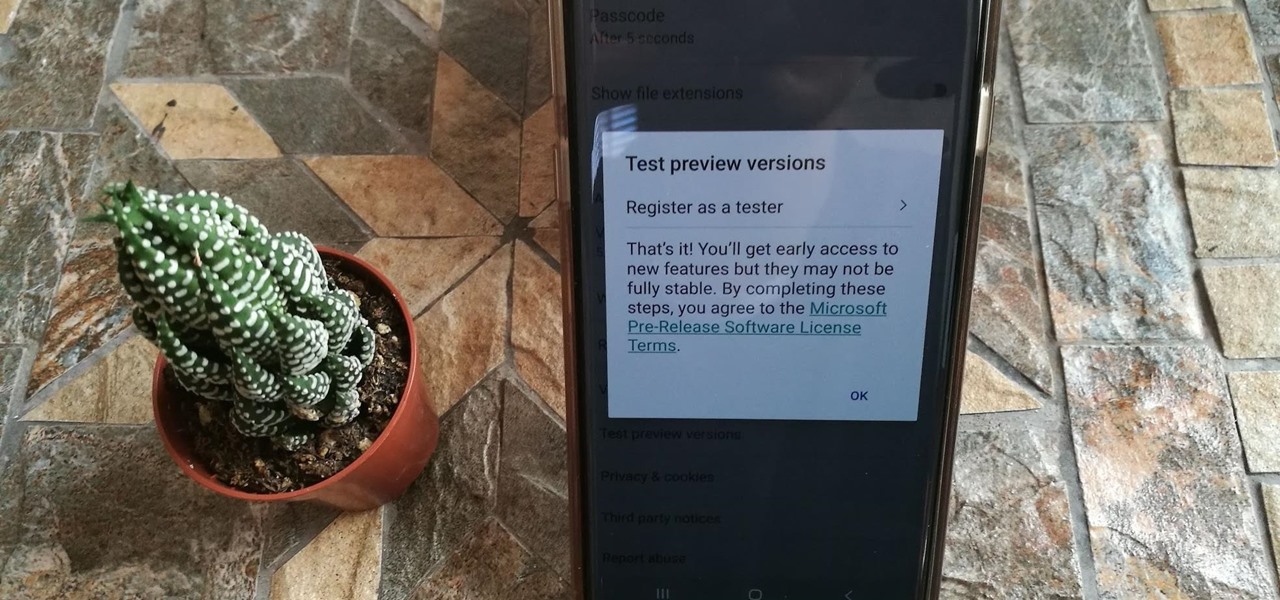
OneDrive has some really cool features, like being able to lock your files with a fingerprint. If you want to be on the forefront of these new features, you can sign up to the OneDrive beta testing program to get new feature before anyone else.

The mobile augmented reality war for dominance between Apple and its Asia-based rivals is in full effect.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

To build hype for the HoloLens 2 among developers, Microsoft is borrowing a page out of Magic Leap's playbook.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

A week after reducing the base price of its Focals smartglasses by nearly 50 percent, wearables maker North is now reducing its workforce.

Simulated training can help soldiers and sailors learn how to use their weapons safely, but simulations can sometimes lack the stressful environment of a real firefight.

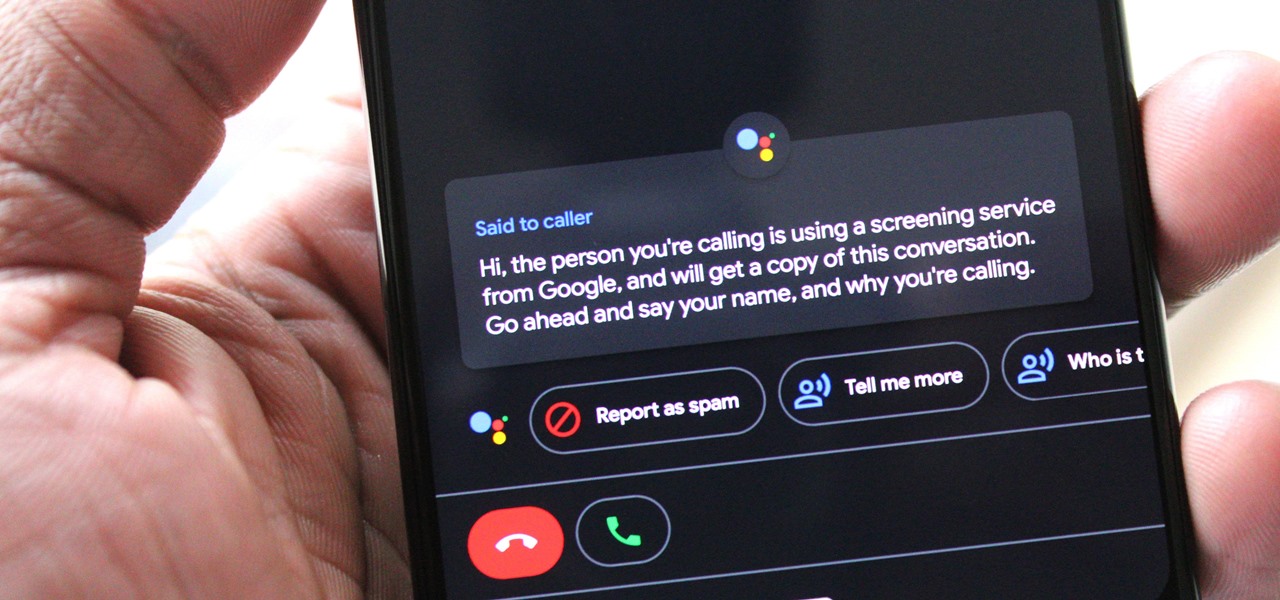
One of the best features on Pixel phones is the new call screening. Any call received on your Pixel device can now be answered by your Google Assistant, allowing you avoid spam calls, wrong numbers, or even exes. But what many don't know is that you can listen to the caller during the screening process.

The wildfires that spread across Northern California for two weeks in November were among the deadliest and most destructive in the state's history. Ultimately, the incident claimed 85 lives, and hundreds of people are still missing in the wake of the disaster, which impacted over 154,000 acres of land.

The augmented reality smartglasses future that Snap founder Evan Spiegel has teased for so long may be closer than many realize.

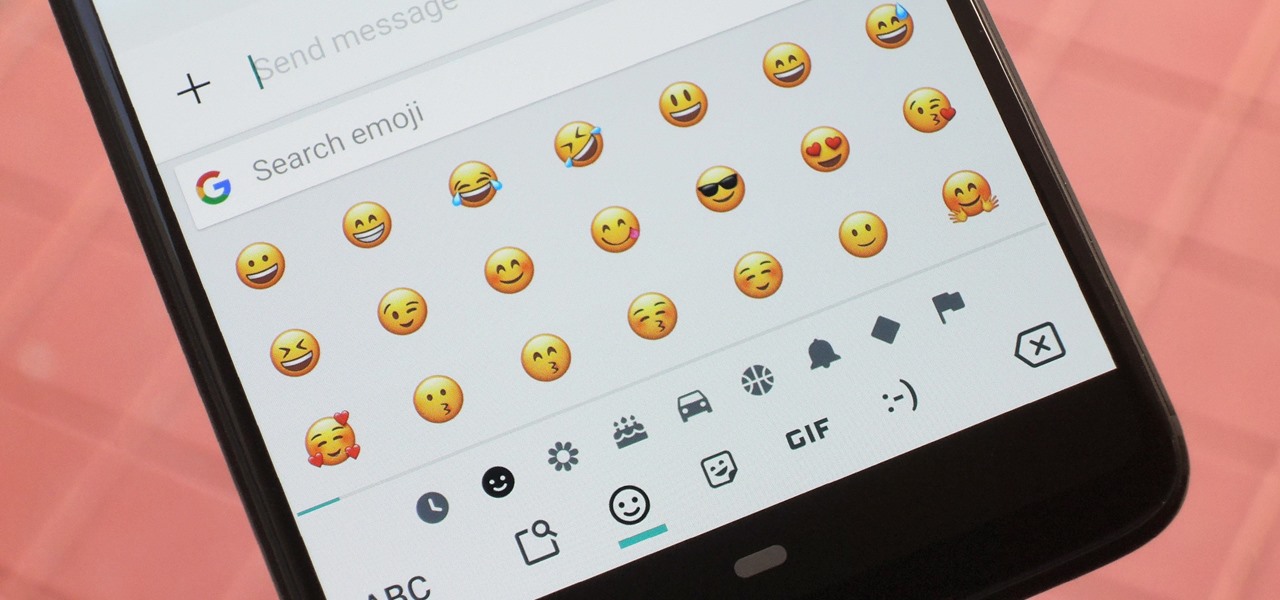
There's been a lot of fanfare as iOS 12 rolls out, and as an Android owner, you might be feeling left out. There's no need to feel that way, though. You don't have to choose between running out to get a new iPhone or being stuck with only your Android's features — at least when it comes to emojis. This is one of those rare times in life when you can have it all.