Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

You've probably used Google to search for recipes, or to find out what the heck that mystery food on the ingredients list is. But with all its built-in features, there are plenty of other ways the search engine can help you out in the kitchen.

Nokia's recent foray into the world of Android brought a plethora of goodies along with it. The Finnish smartphone manufacturer offers a slightly different take on our favorite mobile operating system, with customizations ranging from ringtones to its very own app store.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.
Netflix is more popular now than ever, but it still has a ways to go before satisfying everyone. Whether it's a lack of availability, buggy or unattractive apps, or just not being able to find anything to watch, lots of people have their complaints.

Once you have the skills to bring your ideas to life, the hardest part is coming up with ideas. What do you do when you can't think of something to make? What happens when your well of inspiration runs dry?

Driving a car equipped with a manual transmission is the topic of this video. There are 3 pedals on the floor. From left the right, the three pedals are clutch, brake and gas. Study the diagram on the top of the gear shift. It looks like a three legged "H". Gears 1,3,5 are on the top. Gears 2,4,reverse are on the bottom. The cross in the "H" is neutral. Make sure the park brake is engaged. Press down on the clutch pedal and move gear shift to neutral. Start the car. Put the shift in first gea...

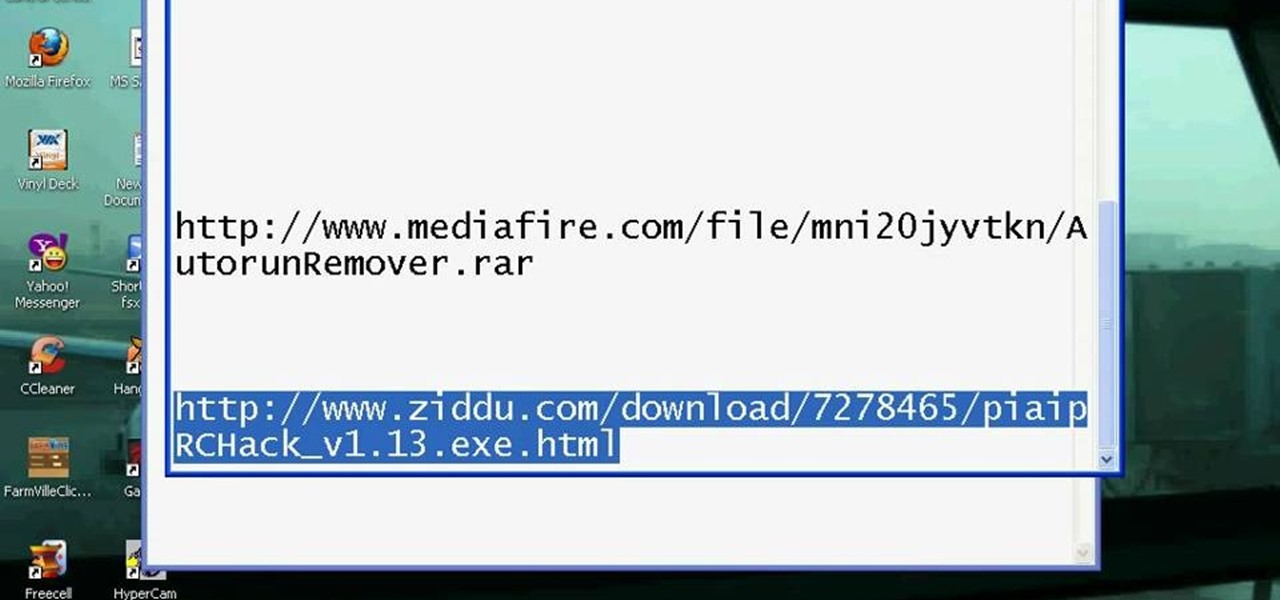
Want to start hacking Restaurant City, but don't want to use Cheat Engine. Well, try out Piap's RC Hack. This tool is simpler and easier to use.

Learn the trick to drawing a Ferrari, but not just any old Ferrari, the Ferrari 599 GTO, the mother of all Ferraris. It's the car any man or woman would love to own, and it has some serious power built into it. Not only does this car have beauty, but it has brains and muscle, too. DragoArt has this video tutorial on how to draw a Ferrari 599 GTO animated car. Get more detailed instructions on the step-by-step cartoon drawing here.

Want to improve your car drawing abilities? Walk you’re way through these steps and you will have the tools to sketch your very own car. You can make it into a cheerful cartoon car or keep it looking sharp and realistic. Rev your drawing engine and get ready to learn how to use basic shapes to sketch your favorite car.

In these videos on automobile maintenance you’ll learn how to check all of the major fluids which keep your car operational. Expert Jon Olson demonstrates how to locate the dipstick to check your engine oil, how to check your transmission fluid, brake fluid, power steering fluid, windshield washer fluid, and battery fluid levels. He’ll also show you how to check all of these components for leaks, and how to troubleshoot mysterious fluids that might appear on the ground under your vehicle. Tak...

Not all Kickstarters are created equal. Some take forever to get their products to supporters, and when the product does arrive (usually much later than promised) it's often very rough around the edges.

Niantic first unveiled its AR cloud back in 2018, using it to enhance the immersive capabilities of its gaming portfolio.

As Apple prepares to potentially introduce its (mostly) secretive AR headset for possible introduction later this year and launch next year, the company has made a strategic investment to ensure its supply chain can support it.

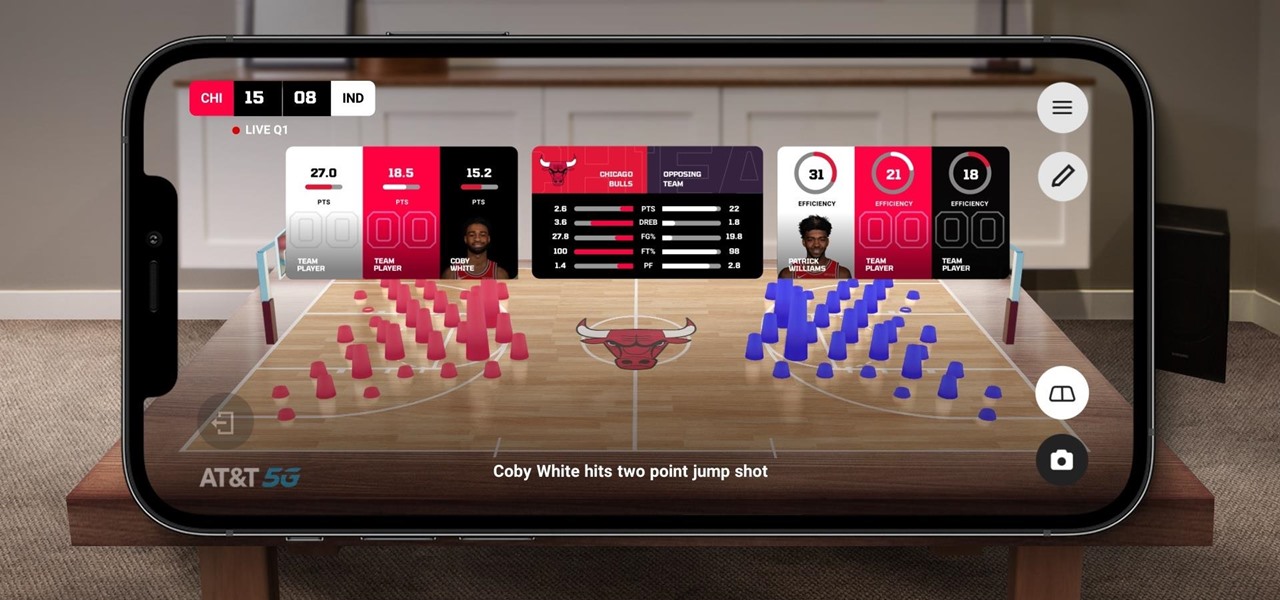
The Chicago Bulls may not be very relevant in the current NBA standings, but they do lead the league in one other area.

The concept of Metaverse, otherwise referred to as AR cloud, where a digital twin of the real world filled with virtual content anchored persistently for all to see, has been a sci-fi dream of futurists for years and an aim for most tech companies who are serious about AR.

The past year has revealed a gaping hole of opportunity in the world of business called virtual meetings. Some existing players like Zoom hopped on that opportunity, while others like Skype seemed stuck on the sidelines, and Google Meet just managed to catch up in time to snag some of the shift in remote work.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

If there's been one signature design element for Apple's iPhones, it was the circular Home button. It served as the "everything" button for each iPhone model until last year's iPhone X, but now, it's completely absent from the iPhone XS, XS Max, and XR. Should you be worried? Short answer: No.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

From Farmville to selling a company to Google, Amitt Mahajan has been through the startup ringer. Now, as managing partner with Presence Capital, he's funding the future of augmented and mixed reality.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us to do everything that an MP3 player could do and then some.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

Checking the weather ranks among the most mundane but essential tasks you can do on your smartphone. Thankfully, both the iOS App Store and Google Play are loaded with weather apps that add some much needed spice to this daily routine, giving you less of a reason to be caught unaware.

If you've been to a farmer's market during tomato season, chances are you know that heirloom tomatoes are pricier (and funnier-looking) than their hybrid counterparts.

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

As NASA nears the launch of another mission to the Moon in 2024, and a subsequent mission to Mars in the 2030s, augmented reality is increasingly being woven into the normal space operations to test various capabilities.

After receiving $100 million in funding in 2018, smartglasses maker Rokid is going the crowdfunding route to finance its latest product.

Billionaire Richard Branson did his part to advance space tourism this weekend by beating Elon Musk (SpaceX) and Jeff Bezos (Blue Origin) to become the first among them to travel into space.

When you're talking about collectibles, in 2021 it's heresy not to include the world of sneakerheads. Nowadays, a single, limited batch of newly designed sneakers from Nike can quickly sell out and then go on to be resold for many thousands more than they were purchased for at launch.

Apple's first release candidate for the iOS 14.3 beta came out on Dec. 8, but there must have been a serious bug in the system because iOS 14.3 RC 2 followed it just two days later on Dec. 10. These builds highlight everything that you should expect to see on the stable version very soon.

If you're a hacker, pentester, or any other type of Null Byte reader, and would like to create a website to showcase your services and skill set, you may not have the time or energy to do it the long way.