Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, a tool that builds upon Nmap, offering an automated way to enumerate networks and services quickly.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

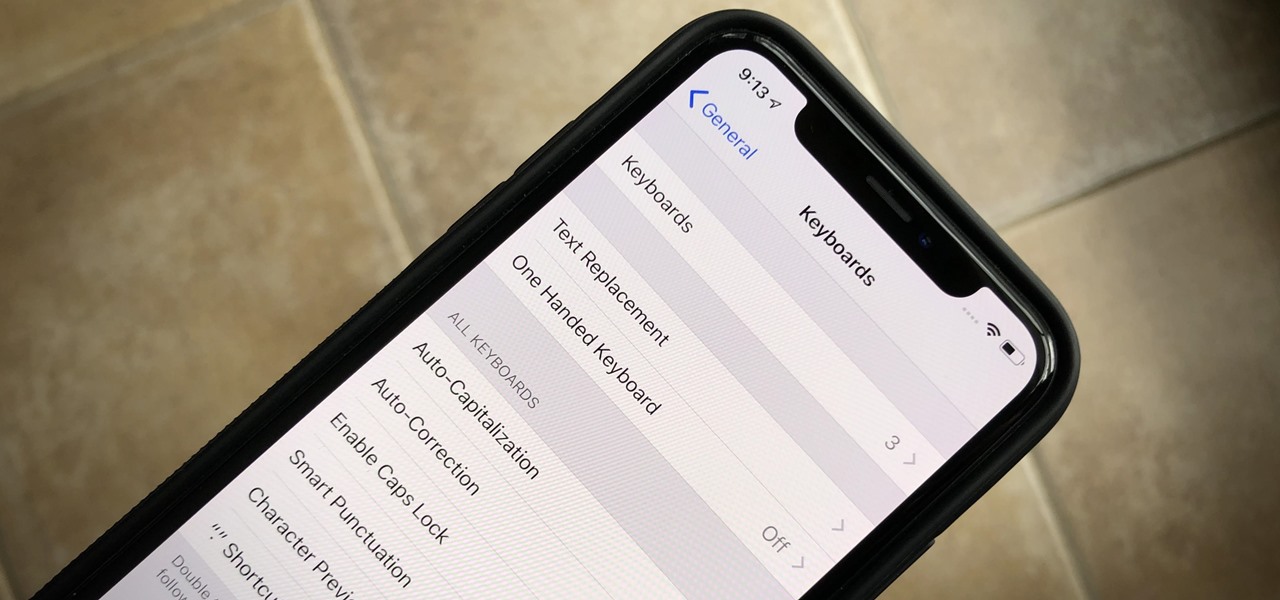
For years, iPhones have had haptic feedback, but Apple didn't incorporate it into the stock iOS keyboard until iOS 16. To use keyboard haptics in iOS 15 and older — or as an alternative to the default keyboard's in iOS 16 — you can take advantage of third-party keyboards like Gboard.

Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Unlike VR, when you're talking about augmented reality, describing what an experience is like can be incredibly difficult — primarily because the experiences are even more contextual than relatively static virtual worlds that don't involve real-world settings.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

Three new iPhones means you have to make a choice: Do you go with the smaller iPhone XS, the larger iPhone XS Max, or the cheaper iPhone XR? There's lots to like about each model, but if you want to make an informed decision, it's time to learn what each has to offer. Here's what the iPhone XS Max brings to the table.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Word games can expand your vocabulary skills in all sorts of exciting and creative ways. Because of this, both the iOS App Store and the Google Play Store are awash with word games, making it hard to differentiate between good and bad titles. This is especially troublesome if you're looking to purchase a game, as everyone hates to waste hard-earned cash.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

This article is a guide for making Chainmail Armor from start (simple wire) to finish (a finished chainmail shirt). We will be using the European 4 in 1 weave, as this is the most common weave. This is the weave that you usually see in movies. There are several sections to this guide: Materials, Making the Rings, Weaving the Rings, and Making the shirt.

The new iPhone 16, 16 Plus, 16 Pro, and 16 Pro Max are worth upgrading to, but if you want more advanced features, especially for the camera, you may want to take a closer look at the iPhone 16 Pro and iPhone 16 Pro Max.

In less than a month, WWDC, Apple's Worldwide Developers Conference, will reveal the company's plans for the upcoming iOS 18 and iPadOS 18 software updates. But we already know what accessibility features will be hitting iPhones and iPads later this year, and many of them will be helpful to everyone, not just users with accessibility issues.

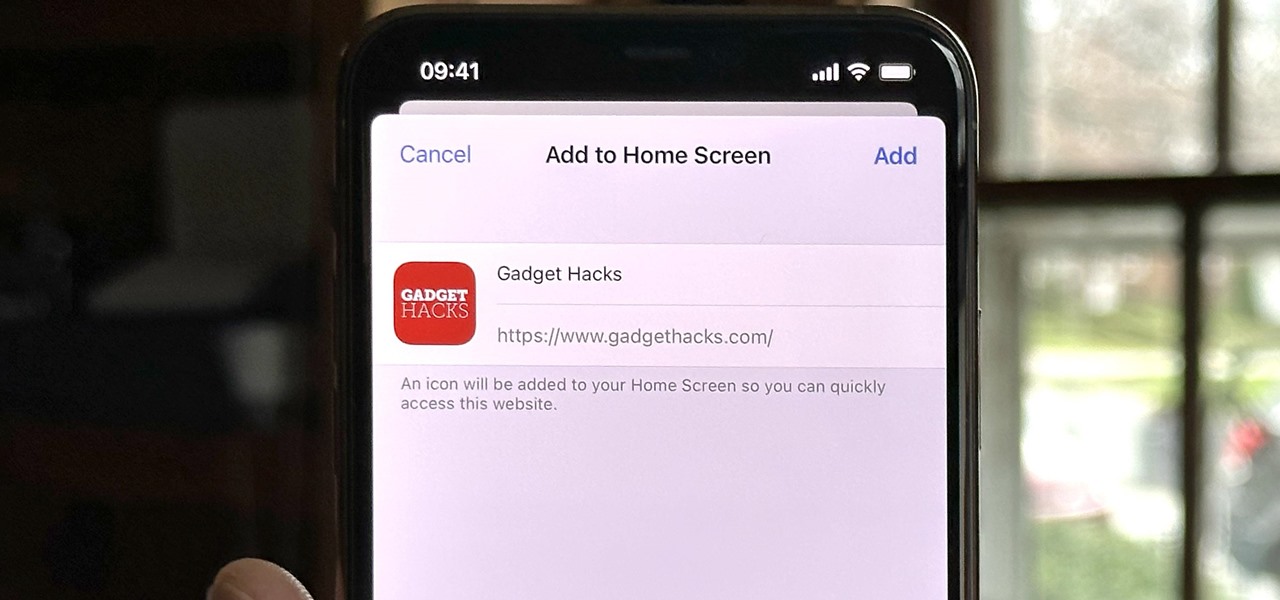
Safari isn't the only web browser on your iPhone or iPad that will let you add icons to your Home Screen for progressive web apps and website bookmarks. Apple gave developers the key to its "Add to Home Screen" feature, and your favorite iOS or iPadOS web browser may already support it.

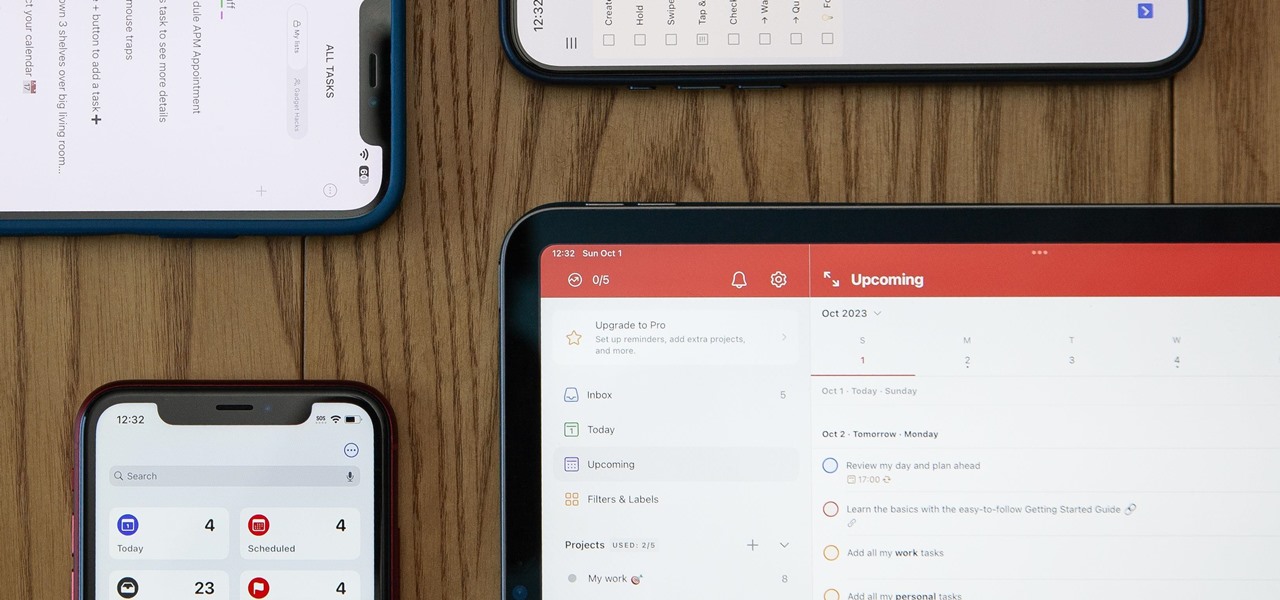
When you want a helpful task manager on your iPhone or iPad, any of the nine apps in this guide should be at the top of your list. But we'll review each app's features to help you determine which one might be best for your workflow.

Now that Vision Pro, Apple's mixed reality headset, has been announced, Apple can free up some R&D resources to commit to its upcoming foldable iPhone, which has been rumored for just as long as Vision Pro has. Will it be a flip-style or a larger foldable? Let's see what all the industry experts and Apple leakers have to say.

Generative AI, or GenAI, is the hottest thing in tech at the moment, particularly for its ability to create content,p including essays, images, and videos. After Microsoft added its own GenAI tool to its Bing web search engine, Google is eager to follow suit, and you can be one of the first to try out Google's new GenAI search tool.

Apple's upcoming iOS 17 is expected to include many new features first seen on Android, but there are also some exciting, unique features that Android needs to steal pronto.

Facebook's earnings calls are generally focused on numbers—revenue and user growth. But this week the company's founder and CEO, Mark Zuckerberg, carved out a significant portion of the call to elaborate on Facebook's plans for immersive computing.

The tech world was taken by surprise this week with the unexpected unveiling of Snap's augmented reality Spectacles smartglasses.

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

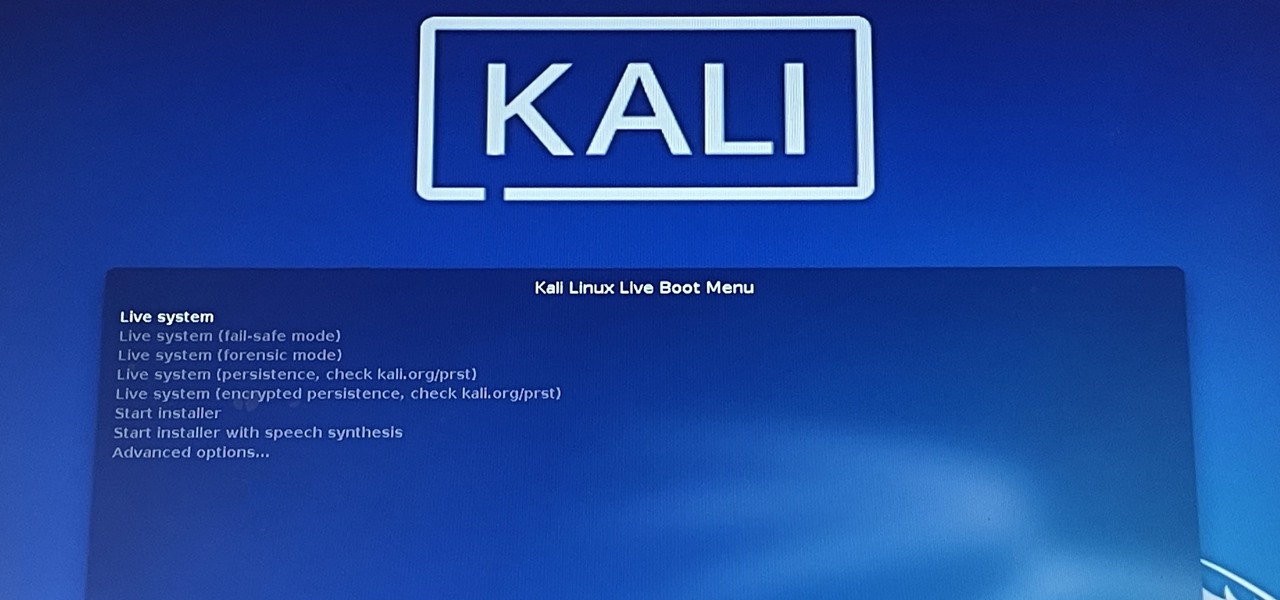
Kali Linux is the go-to Linux distribution for penetration testing and ethical hacking. Still, it's not recommended for day-to-day use, such as responding to emails, playing games, or checking Facebook. That's why it's better to run your Kali Linux system from a bootable USB drive.

When life hands you lemons, make lemonade. At Magic Leap, the lemons are the COVID-19 pandemic, and the lemonade is a new solution for virtual meetings born out of social distancing.

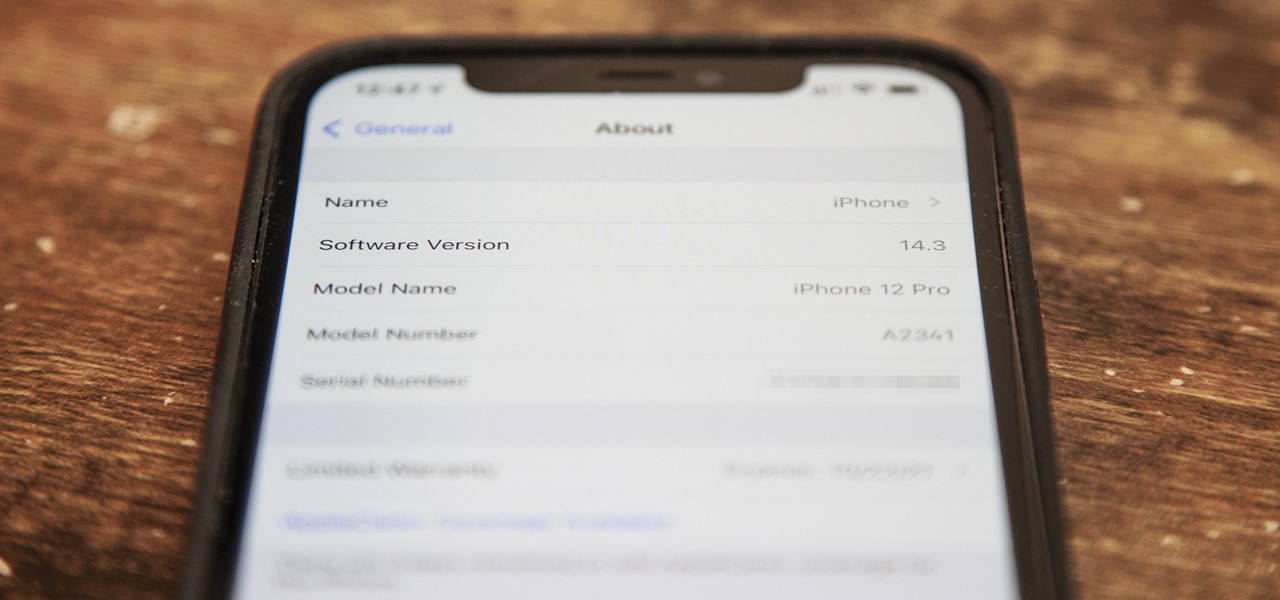
Just as expected, Apple pushed out iOS 14.3 to the masses on Monday, Dec. 14, which coincided with the pumped-up release of Fitness+, Apple's subscription workout service for Apple Watch users. It also came one day before the new AirPods Max hit buyers, and the iPhone needs iOS 14.3 to use all of its features.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

Apple's latest big update to iOS 14 has a lot to be excited about. While iOS 14.2 had some fun new features, such as new emoji and wallpapers, People Detection in Magnifier, and a Shazam control, iOS 14.3 brings on the heat. There are new Apple services and products that are supported, ApplePro RAW is ready to go, the TV app makes searching better, and custom home screen app icons work even better now.

In the realm of social media, all roads lead to one destination: cracking the code of continuous partial attention dopamine hits. We learned this back in the days of Vine, before Twitter foolishly killed it. And I pointed my lens at the emerging trend back in 2016 when I highlighted Musical.ly for Mashable, just before it was snapped up by China's Bytedance for $1 billion and merged into what is now TikTok.

Whether you're using your iPhone to add graphics to a document, edit a photo, or sketch an idea, color plays a vital role in making your work look great. Apple's iOS 14 update introduces a system-wide color picker that lets you pick the exact color you want, save it to your favorite colors, and use it across a variety of apps to add that special touch to your work.

The Snapdragon version of the Galaxy Note 20 and 20 Ultra — the one sold in the US — can't be rooted. Without root, the level of customization is limited. Such a large group of Android users shouldn't miss out on mods, and they don't have to.

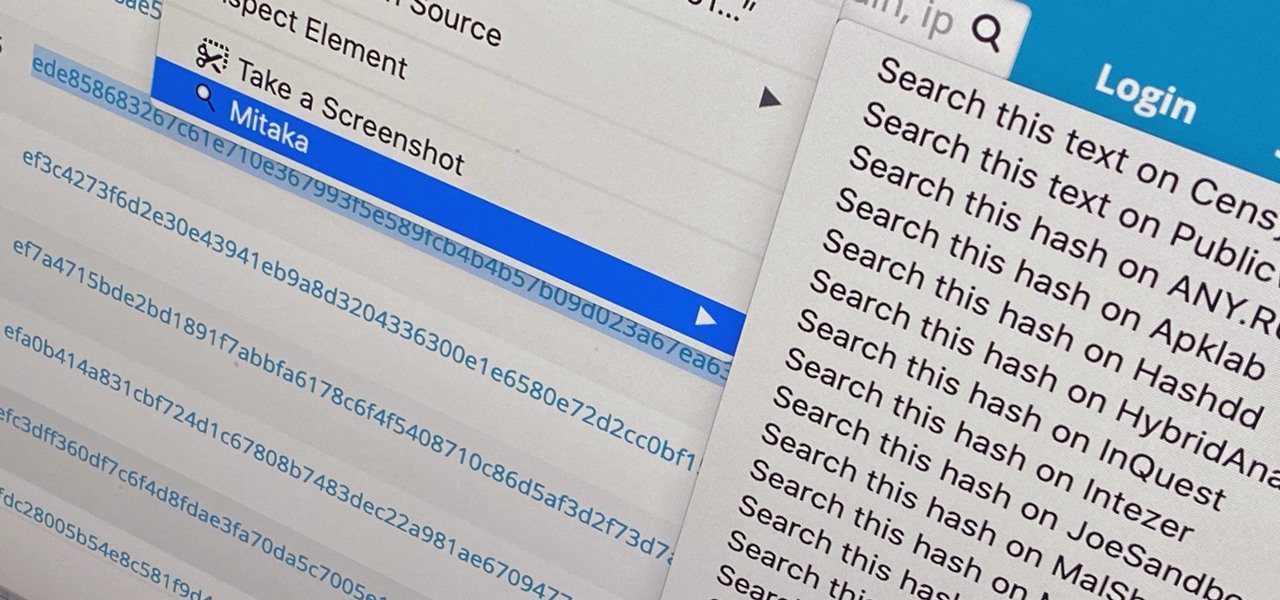
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

Samsung's stock Galaxy Themes system leaves much to be desired with its restrictive and expensive theme packs. Back in the day, the gold standard for Android theming was CyanogenMod Theme Engine. And while it no longer exists, a successor has emerged to fill the void.