Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Many of us are guilty of sacrificing a delicious breakfast for a few extra minutes of sleep in the morning during the busy work week. Grab-and-go breakfasts are definitely timesavers, but granola bars and other packaged items often lack the fresh breakfast feel that makes the first meal of the day so great.

How much you've actually spent and how much you think you've spent are usually two completely different results, and is especially true on Amazon when it's so easy to click and buy. You might think you've given Amazon a couple thousand over your lifetime, when the fact is that it's three or four times that amount.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.
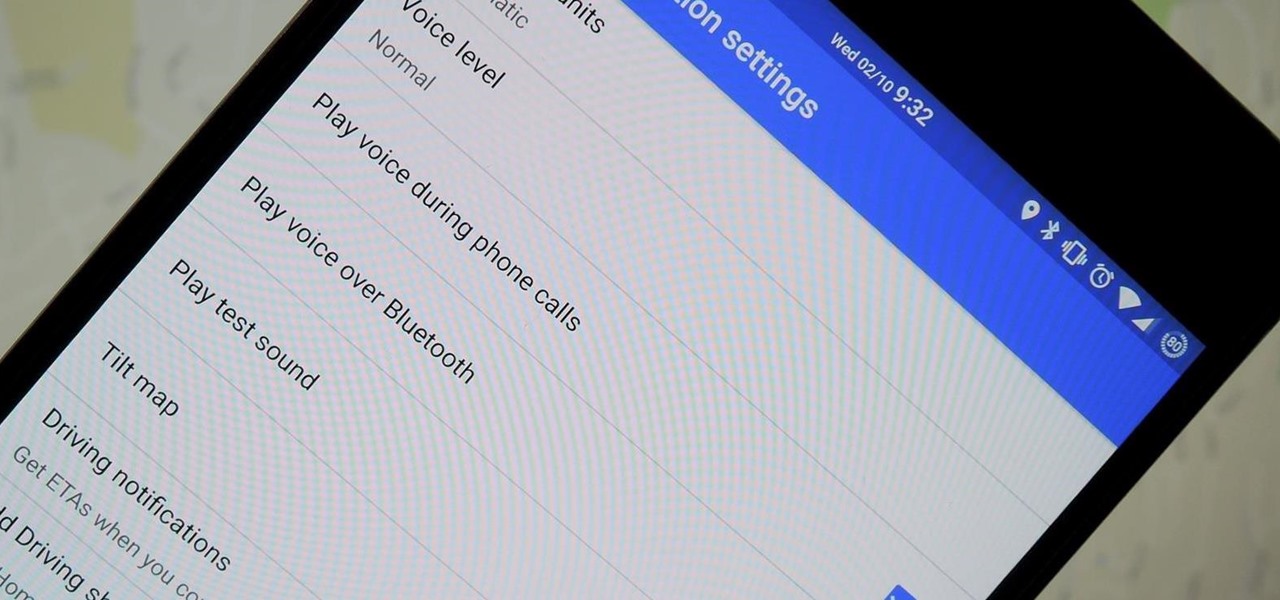
We've all been there. You're driving along with Google Maps pointing the way when you get a call from your friend asking you how much longer it'll be until you show up. You try to offer some lame excuse about how something came up last-minute, but you're interrupted, quite rudely, by Maps's voice guidance. The voice butts in again, and again, and again, to the point that you consider having Maps navigate you to the nearest cliff so that you can drive off it.

Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PHP instead of C#).

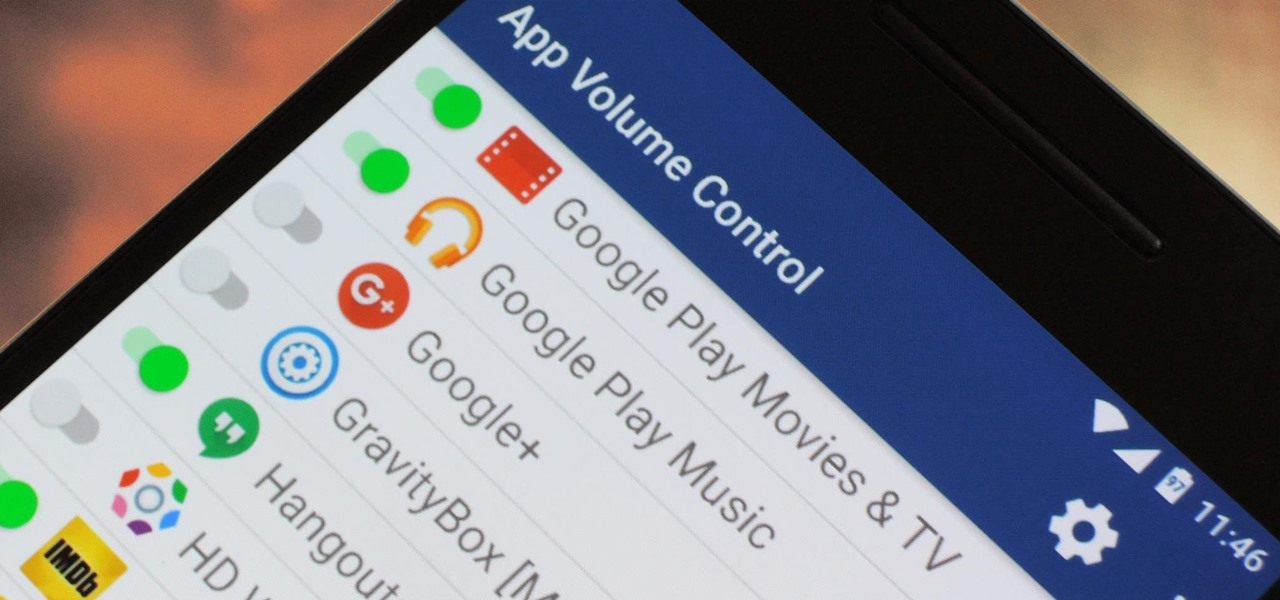
You can do practically anything with a modern smartphone or tablet, so it stands to reason that the apps you have installed may serve vastly different purposes. Picture a game and a video player sitting right next to each other in your app drawer—odds are, you want the sound turned up while you're watching videos, but would prefer that the game was muted or a little lower. As a result, we're constantly tweaking volume levels to get the best experience.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

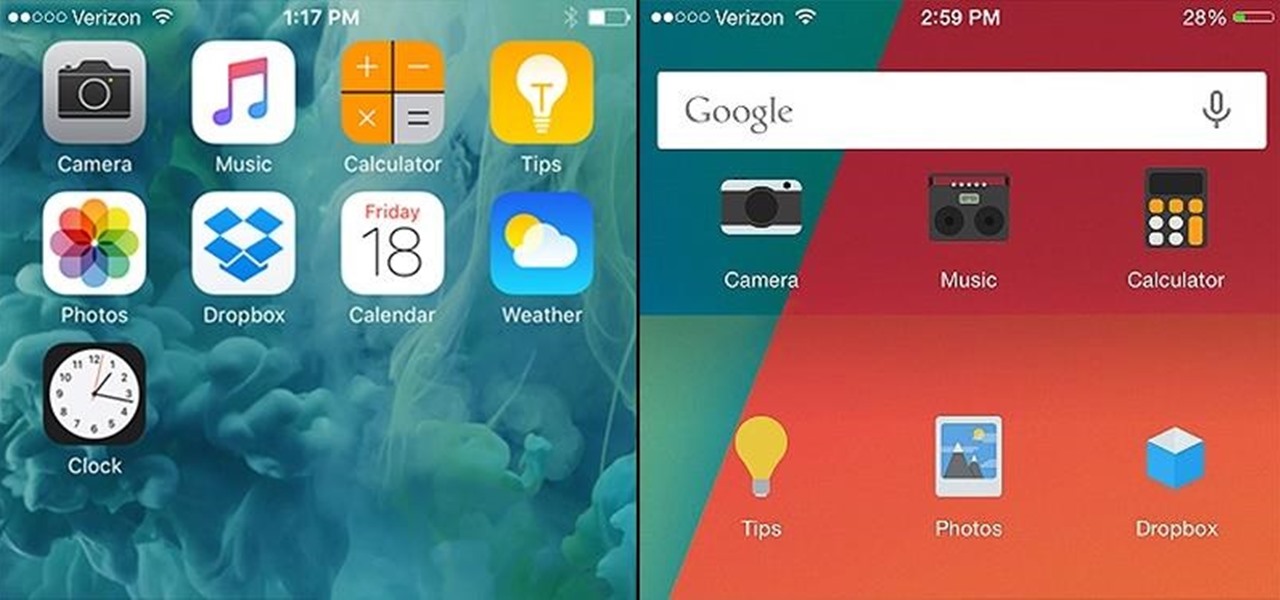
The competition between iOS and Android is fierce. Each operating system offers unique and powerful features, so it can be hard to choose which one you want. However, for iPhone users, a little tweaking and some themes can give your iPhone some of the key features and aesthetics of an Android.

Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.

Manufacturers like Samsung and LG have added their own implementation of multi-window features to Android for years now, but with the release of version 6.0 Marshmallow, Google has finally gotten around to working the same feature into stock Android.

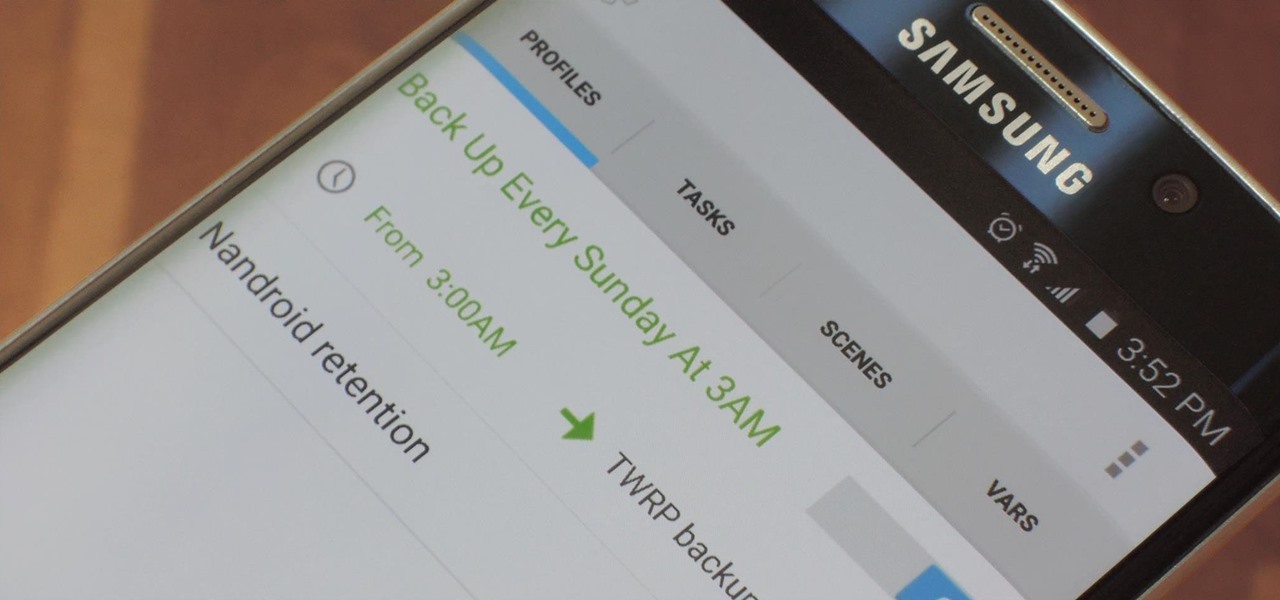
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom ROM, you can restore your NANDroid backup to get everything back to normal.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

When it comes to news, updates, and arbitrary nonsense, it's hard to find a better source than Twitter. And for some of us, the best way to consume Twitter is through the web (versus a mobile app). But as much as I prefer the standard browser version, it's easy to make it better, faster, and more convenient using a few Chrome extensions—and here are my favorites.

As mobile devices become more and more popular, service providers have unfortunately resorted to capping data. What this means is that, depending on the plan you have with your ISP, you could have limits placed on how much data you can use for a set period of time. Once you've hit the limit, your ISP could drastically slow down or throttle your internet speed or charge you outrageous overage fees.

Sushirrito offers burrito-sized sushi rolls that are on the cusp of becoming the trendiest handheld snack to hit the foodie world. According to its website, Peter Yen created the Sushirrito brand, trademarked it in 2008, and opened his first restaurant in 2011 in the Bay Area with Ty Mahler, executive chef.

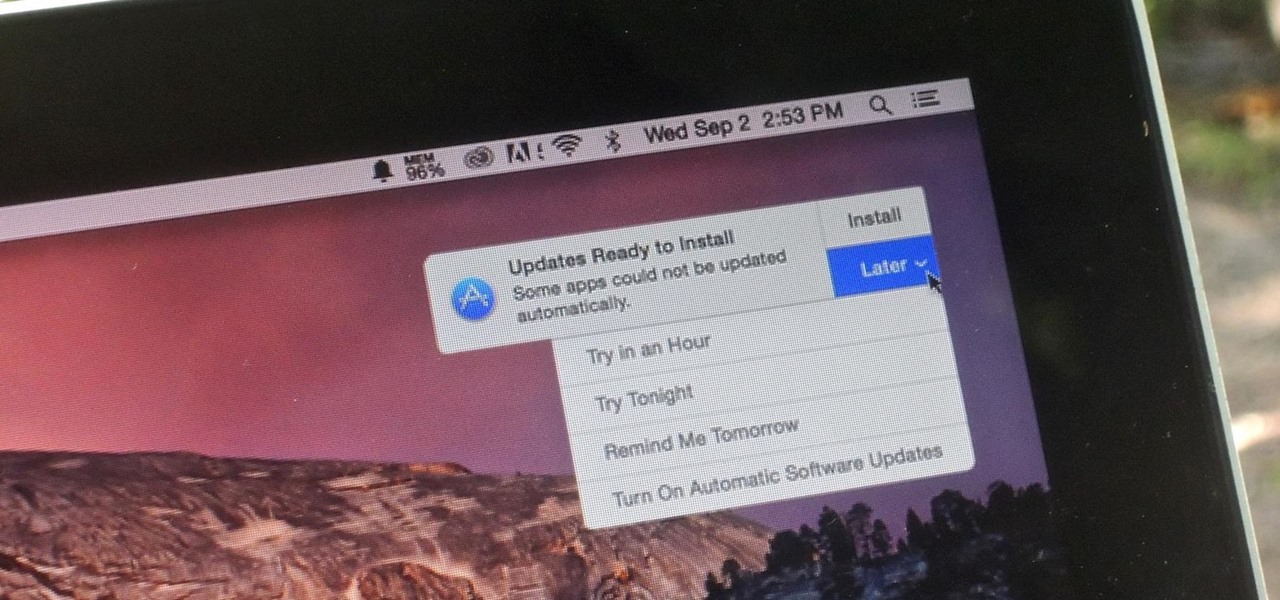
Software update notifications are meant to be a reminder to keep your operating system and apps up to date, but that doesn't mean that they never get annoying.

ADB and Fastboot are probably the most essential tools for any Android aficionado. They can do everything from backing up your device to unlocking your bootloader with a few simple steps. This paves the way for many new tweaks and customizations that weren't possible before. The required platform works with the three most popular computer operating systems, too, which is good news for everyone.

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.

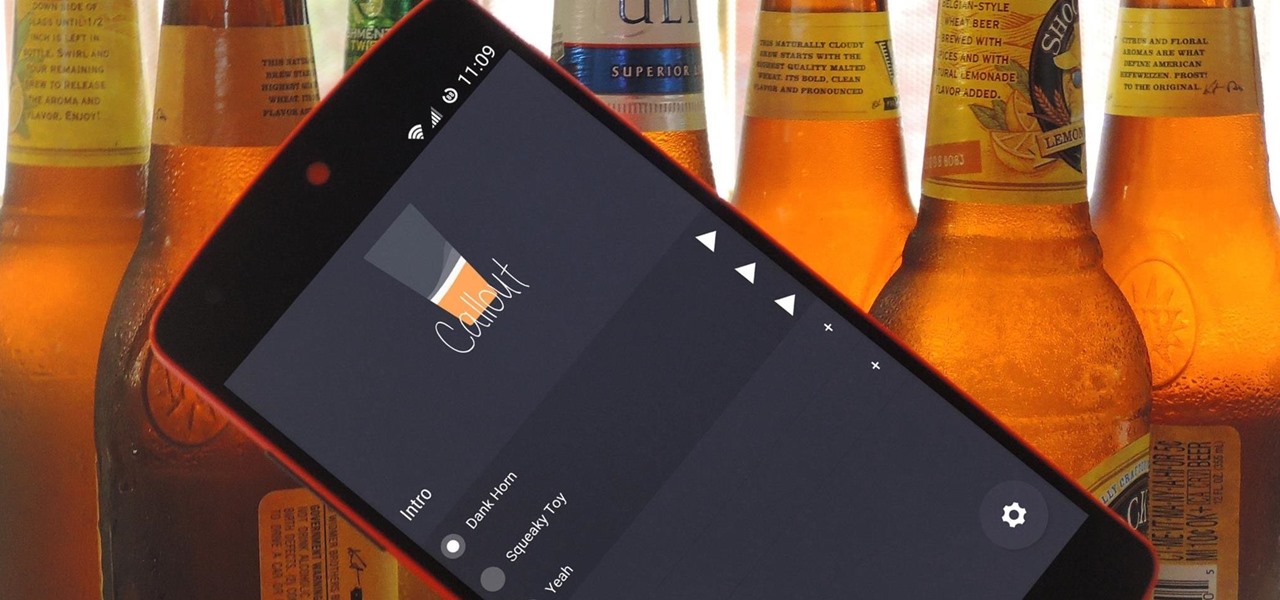
If you ever need to spice up a party, drinking games can really get things started quickly. The objectives are generally to complete tasks or challenges, but it's really all a thinly-veiled excuse for increasing everyone's alcohol intake in a hurry while testing levels of inebriation.

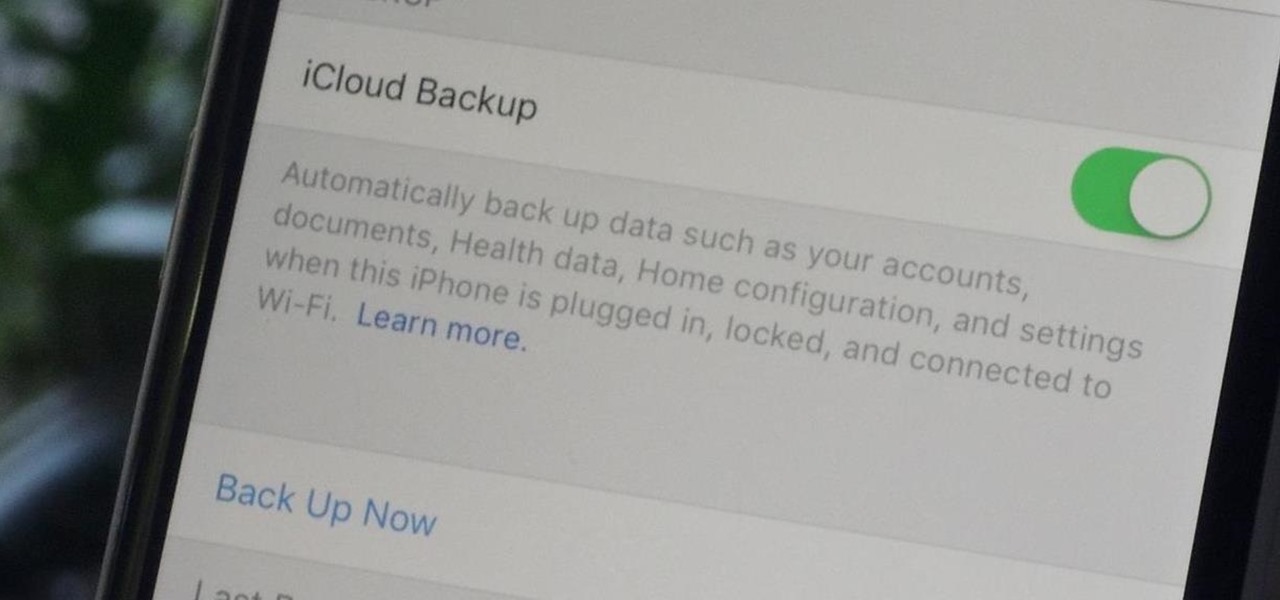
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.

The grill isn't just a place for burgers, dogs, and corn anymore. Fresh fruit has made its way into barbecue territory, with results so good, you'll think twice about settling for fruit salad. While some fruits are common enough on the grill (like pineapple), these six are more off the beaten trail: peaches, watermelon, strawberries, mango, and pears.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

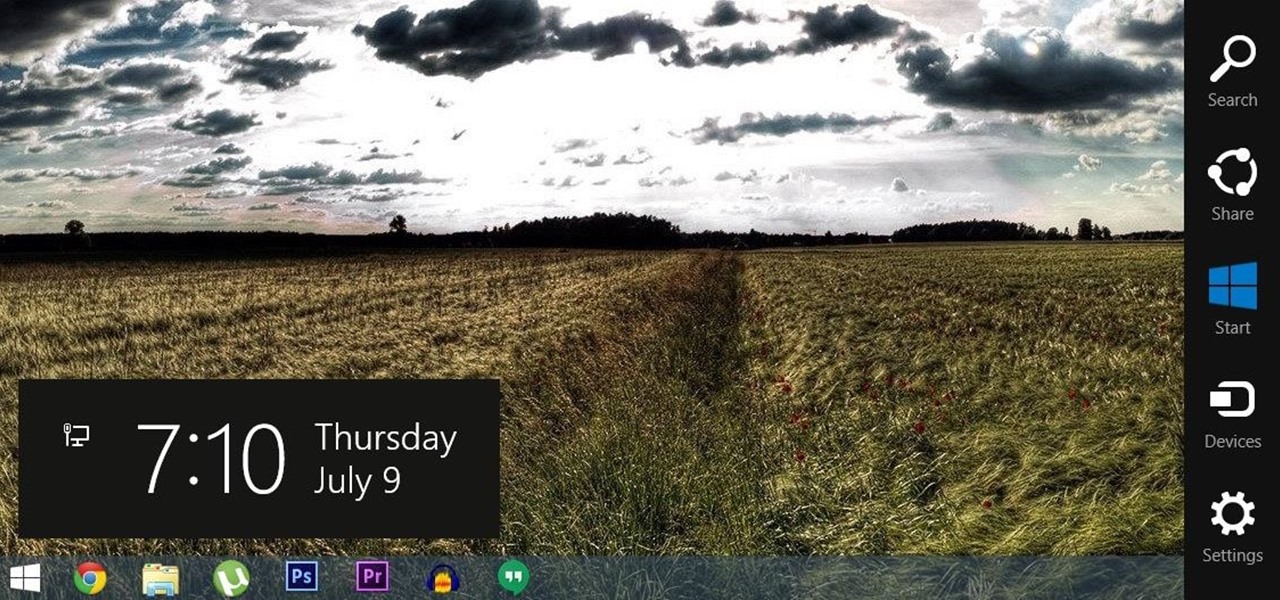
For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the screen.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Remembering keyboards shortcuts can prove difficult, especially when there are so many to remember, not to mention that they differ from app to app. While tools like CheatSheet can make them easier to use, today I'm going to show you how to enter them without using your keyboard at all.

Make no bones about it—having an "undo" option is a freaking godsend. Whether you accidentally deleted an entire essay, screwed up the shading on a Photoshop job, or sent an email that wasn't quite ready, having the option to undo a click or button-press can definitely be a lifesaver.

The next time you're out camping, whether it's outdoors in the wilderness or right outside in your own backyard, try this hack out for an effortless campfire all night long. While there is definitely some prep work involved, it's well worth it if you don't need a huge bonfire, and more so if you plan on cooking meals over the flames.

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

It would be an understatement to say that Supercell hit it big with Clash of Clans. The game has topped both Google Play and the iOS App Store for years and shows no signs of ever slowing down.

Not to be outdone by the announcements of Mac OS X El Capitan and iOS 9, the Apple Watch is also getting a much needed software update. Some of the notable new features we can look forward to on watchOS 2 are Nightstand mode, additional screens for friends, email replies, and other improvements we probably should have already had.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

Tomatoes are the perfect barometer for kitchen knives and knife skills. If you've ever watched an infomercial for a set of knives, you've surely seen the enthusiastic host waxing about how well the knives cut tomatoes. And if you've ever had your knives sharpened, you've most likely tested them out on a tomato.

When I was in college, I invited a girl over for a date. It was a glorious spring day, and I thought it would be the perfect time to fire up the unused barbecue that had been sitting on my patio all school year. I prepped all the food, chilled all the beer, and then I realized I had no way of lighting the coals for the barbecue.

Smartphones don't generally play nice with tripods, so videos taken with our handheld devices make terrible source material for time-lapse photography.

Many Android utilities use Android Debug Bridge, or ADB for short, to send commands from a computer over to your phone or tablet. This enables such utilities to run terminal commands that, in some cases, wouldn't be possible on Android without root access.