Baking extraordinaire Lily Vanilli has made some just-slightly-too-realistic-to-look-yummy bleeding heart cakes for people to give to their respective beaus on Valentine's Day. While it's pretty tricky to get your hands on one made by Lily herself, you can make one yourself if you've got the heart. Check out A Lot on Her Plate's video with Lily to see how to make this so-called "anti-Valentine's Day cake," which also works well for Halloween. To follow along with them, check out the full reci...

If you are looking to improve your classical piano technique then this three part how to video is the place to start. You will learn how to practice and study Chopin's nocturne number 20 in C# minor. This detailed lesson goes over where to place the accents, analyzes the dynamics and legato playing technique. This piano tutorial teaches you the best way to practice it so you can Chopin's nocturne no.20 quickly and easily. This piece is not for beginner students, this lesson is directed to adv...

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.
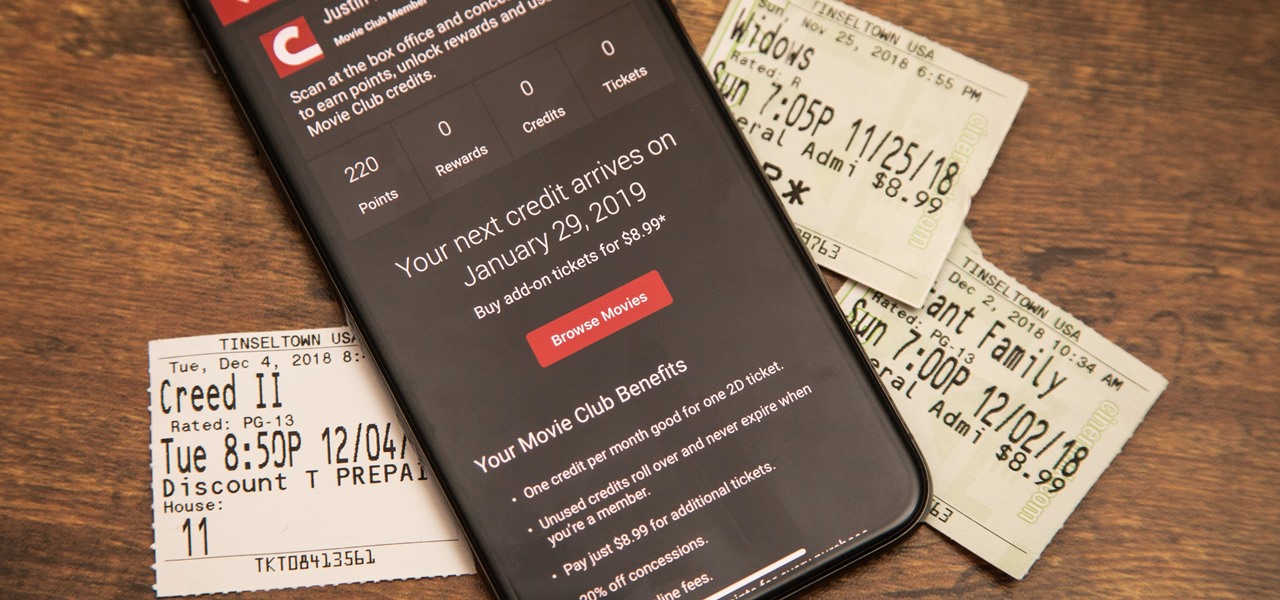
Cinemark may not be as big as AMC Theatres, but it also has a subscription if you want cheaper access to movie tickets. There aren't as many theaters, but if there's no AMC around you, there will likely be a Cinemark to save the day. But is the price of its Movie Club plan worth it?

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Sometimes you've gotta take your shirt off fast, whether it's a romantic night, a quick jump in the pool, or for extinguishing someone on fire.

Today, I'm taking a short break from my usual secret tips to share some exciting news with all of you. As some of you may already know, my first published book "I Think I Am in Friend-Love with You" will be released in bookstores next month.

If you’re having trouble getting games on your memory stick, this video will walk you through the steps of just what you will need to do to compress files onto a thumb drive. There are a variety of steps you will have to follow and you’ll have to have a little bit of time to wait for your game to compress but the effort is well worth it.

What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden emergency HDD can only be controlled by your key, regardless of how many people use your computer.

Want massive, Arnold Schwartzenegger-worthy shoulders? Well, you'll have to work for it, but they're achievable with a few strategic exercises. Building muscle, especially big muscles like your biceps, requires heavy resistance.

Listening to Beethoven's "Moonlight Sonata," with its moody minors and grab bag of sharps, is like turning through page after suspenseful page of a forlorn Romantic era novel.

Part of the process is to create plans to follow when making the cabinet for the arcade game. when cutting the wood you need to allow for the 1/8th of an inch that the band saw will be cutting. You will also need a piece of plexi glass to give the game an authentic feel, spray paint the piece of plexi. You will also need joysticks and buttons, which you can get at happcontrol.com. You need to cut a square hole in the plexi so that the buttons can be mounted in it. To integrate the buttons you...

How to instantly bond with anyone and persuade them

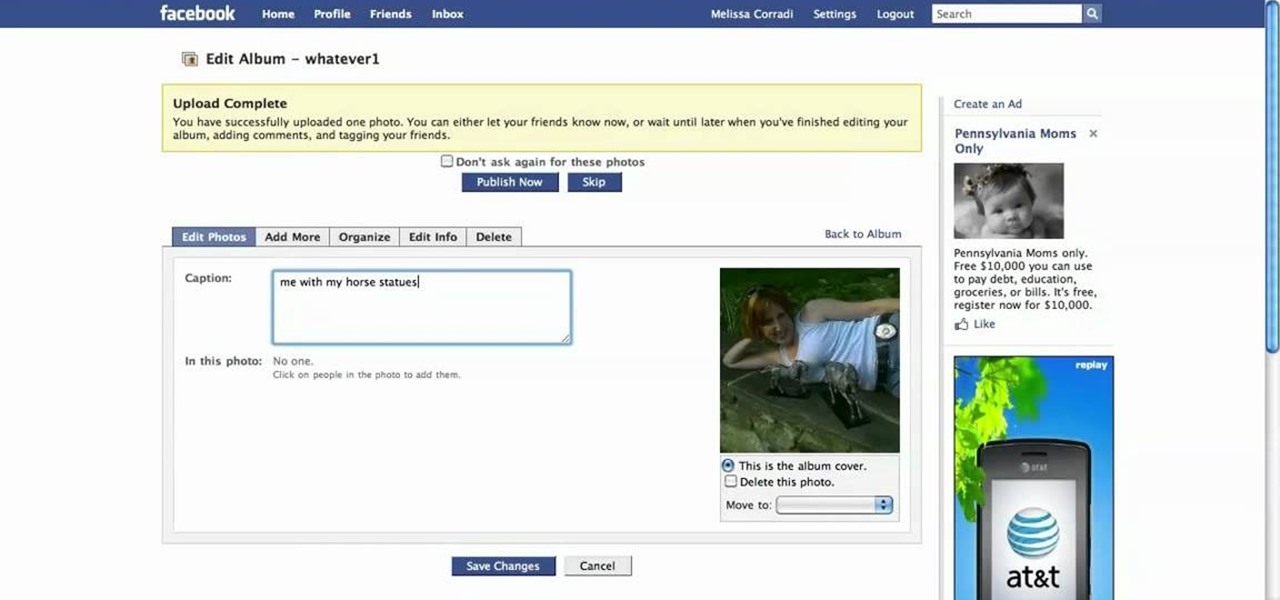
First log into your Facebook account and sign in. Then when you sign in click under your "profile". You will be redirected to another page. This will be your main page, with all of your information that you have put in and what not. Next click on 'Photos'. It will take you to another page. Once in your in there, you will click on 'create a photo album'. You need to name the new album and then create album. Next it will ask the location of the files. It will be located on your computer. Usuall...

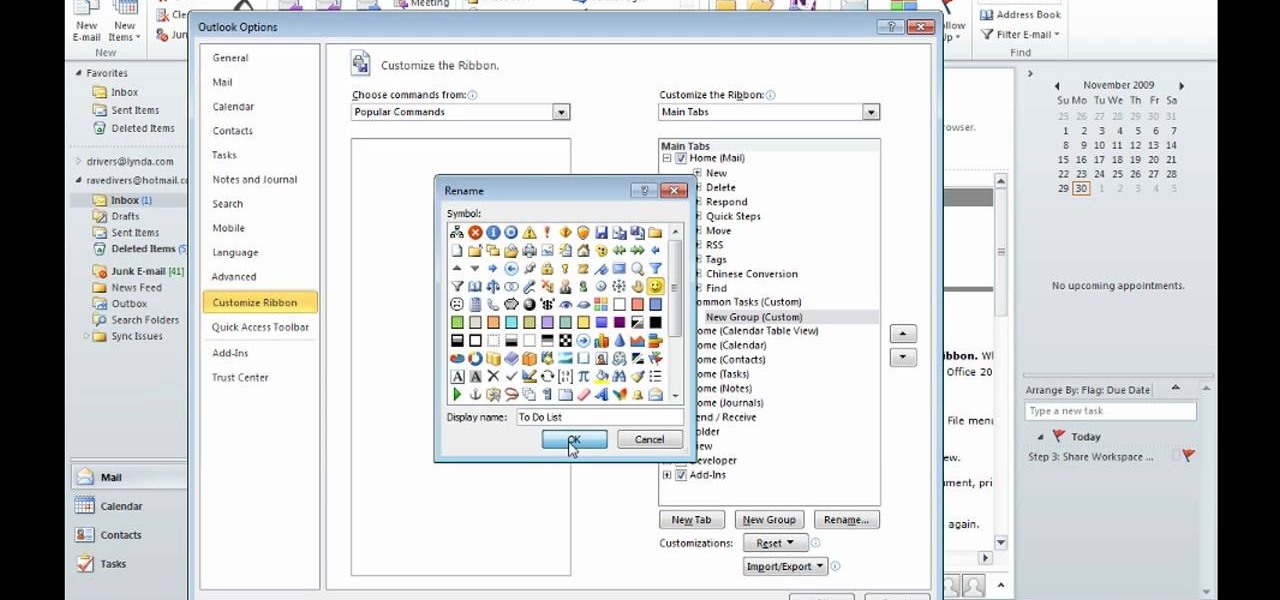
After you launch Outlook 2010 in your computer, you will see the Ribbon strip immediately in the main window. The button for writing a new e-mail is separated from a button for creating new items in the calendar, contact list or task manager. An independent Quick Steps section offers functions allowing you to move a message into different folders, to save it into a calendar as a meeting reminder, to quickly forward it to a chosen person or to more people and to forward it with a FYI note. If ...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

This is a great solution if you need to get something off your computer, but you are not home. Want access to your files stored at home? How about hosting a home web server? Static IPs are expensive, if you can even get one. We set up Dynamic DNS instead!

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Let us help you install your JVC Everio software and hook up your JVC HD Everio video camera to your computer. Just select your operating system.

If you have a limited mobile data plan on your iPhone, you know how tricky it can be to stay within your given allotment. Large app installs and updates, 4K resolution videos, and photo backups can waste precious data resources in no time. And apps like Apple News, Facebook, Mail, and Netflix eat data like it's candy. But you can nip the problem in the bud by restricting data hogs from your cellular network.

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

No one likes in-app advertisements, especially in mobile gaming, but they're necessary because they offer developers a way to make revenue without having to charge you to play. In some games, in-app purchases give you the chance to remove ads, but what can you do about apps that don't offer the option to kill ads?

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

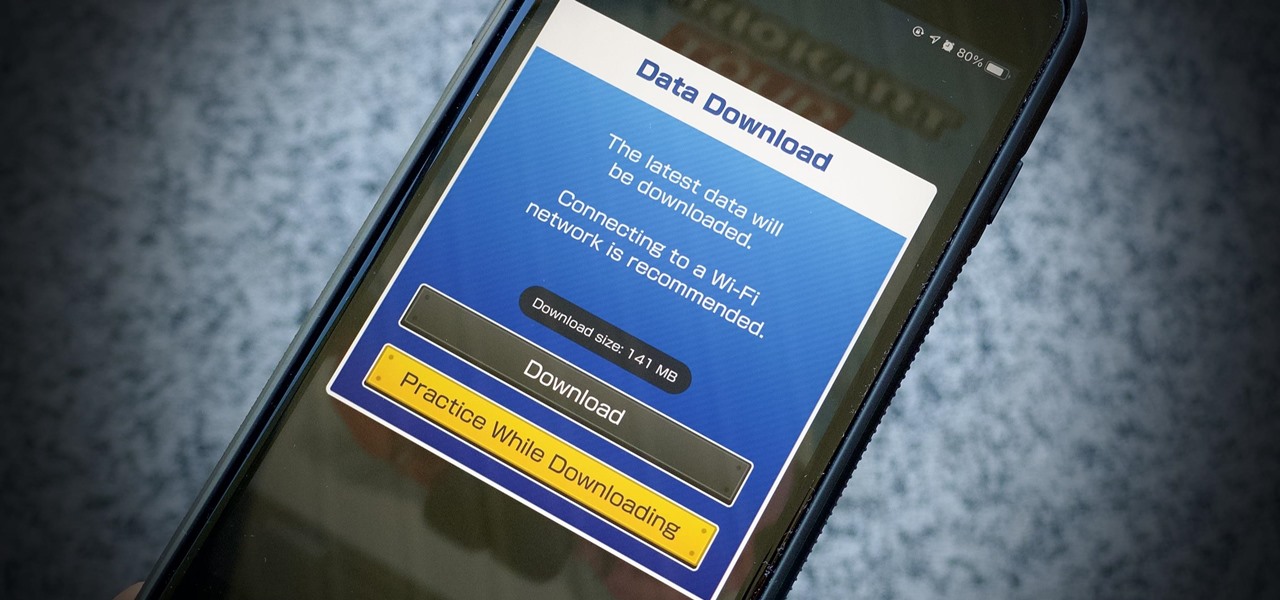
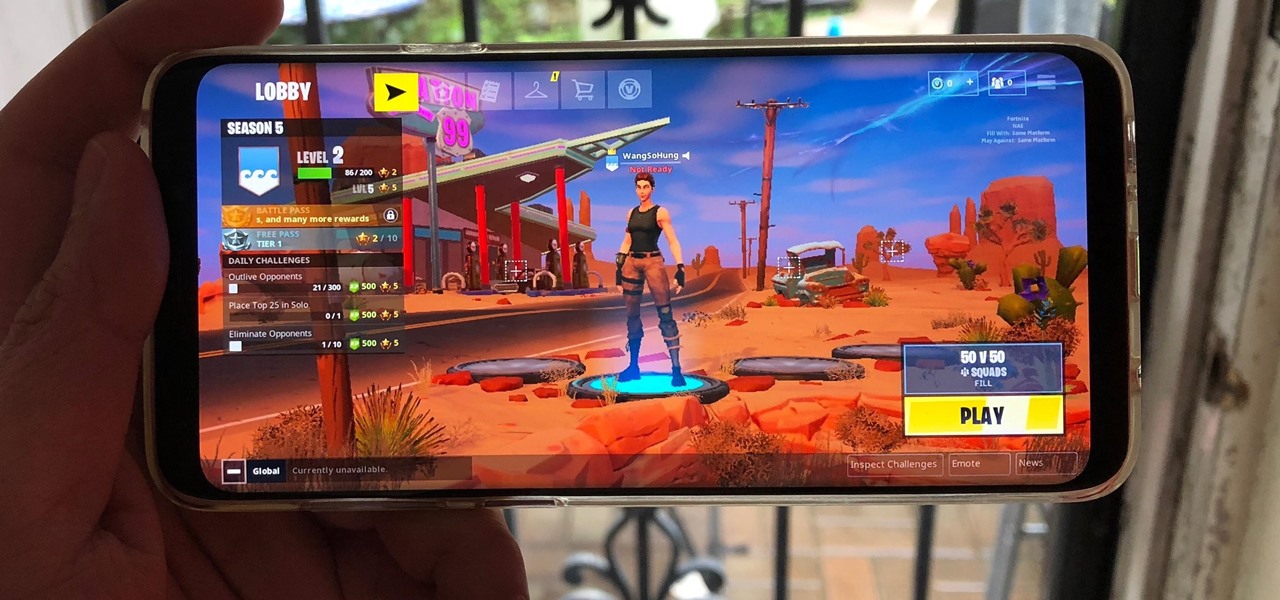
Fortnite's long awaited arrival on Android has ramped up excitement among gamers who are installing the beta version in astounding numbers. With so many midrange and budget devices running Android, however, it's important to stay on top of your device's performance to ensure smooth and uninterrupted gameplay.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Realizing there's no voice to guide you while using your iPhone to navigate can be problematic, causing serious headaches from getting lost to unscheduled pit stops or worse. And while this problem can hit Apple Maps like other navigation apps out there, there are a number of fixes you can try to get navigation audio working again.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plug it into your vehicle, you'll just need a good app to help you make sense of all the data it can gather.