Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

We've heard the rumors for months, but it's finally official: The iPhone 7 will not include a traditional 3.5 mm headphone jack. Instead, you'll need to hook your favorite headphones up with a Lightning adapter (or use ones with a Lightning connector built-in) and connect to your phone using the same port that your charger occupies.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

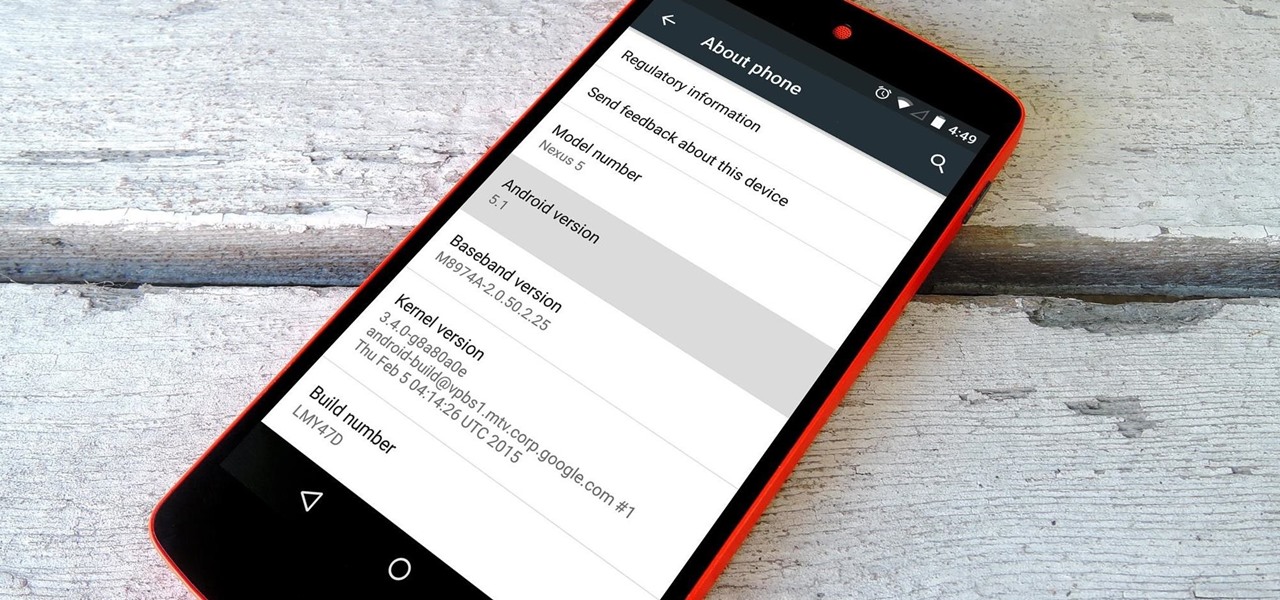
Google inconspicuously announced an Android update yesterday, and while it's not quite the overhaul that the initial Lollipop release was, version 5.1 brings plenty of bug fixes and new features.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

As the Chromecast becomes more and more popular (it's even available overseas now), the market has seen an avalanche of Chromecast-compatible apps. We can play games, cast TV stations, and even mirror our screens, but today I'm going to show you a multifaceted tool that'll do everything from broadcasting your camera to displaying your documents.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

For those of us living in any of the 49 states other than New York on Thanksgiving Day, checking out the famous Macy's Thanksgiving Day parade at New York is more a dream than reality. While the parade airs every Thanksgiving on television, it's also possible to catch the festivities online.

First of all you need to know that there are different types of Martingale Fit. In this tutorial you are first shown a running Martingale Fit. It is attached around the neck by wrapping it. You have to make sure to wrap it around the neck in such a way that it fits to come exactly in the middle of the horse’s chest. Here you have to make the connections. Now you have to go underneath the legs and attach it to the girth. You shall notice two rings hanging over from the chest. You have to attac...

I hope you haven't updated past here if you want to jailbreak your iPhone. Jailbreaking gives you access to many open ended applications and games. This video will demonstrate exactly how to jailbreak and unlock your iPhone 3G/3GS firmware 3.1.2 and 5.11.07 baseband.

This video tutorial instructs you on what a key logger is and how to make a key logger which records your computers key strokes for later review. There are software or hardware based key loggers that intercept the connection between the keyboard and computer. Hardware key loggers consists of a micro controller for data logging. Software key logger is a script that runs in the background then processes and saves the key strokes to a text file. To make a key logger you'll need to know a program...

Vanae goes over some tips on how to successfully ask a girl out in this video tutorial. The first tip offered in this tutorial is building a connection between yourself and the girl. This means talking and getting to know the girl before asking her out. The next tip is figuring out what she likes as far as restaurants and movies. The third step is to decide where you want to take her. For example, if there is a new restaurant that just opened up, Vanae suggests asking the girl if she wants to...

This video describes how to solder a wire. The first thing you have to remember is that the wires should be cleaned, shiny, and bright. Then trim about 1/2-inch of the insulation of the wires and then make a secure mechanical connection. Next, put some soldering pencil clean and shiny 60/40 rosin core solder. Do not use 50/50 core solder. Start by making sure that the soldering iron is tint. Put the soldering iron underneath the joint. Heat tends to rise and then touch the solder to the joint...

Tying It All Together presents a video on the Etyszkiety knot, a decorative Polish knot worn by mounted brands. This knot also has connections to other cultures, where it is called the prosperity or the prolong knot.

This video shows you the proper way to clean your spark plug to ensure it is working efficiently. A step by step written guide.

Ouch! Is your baby's bottom red and sore? Say goodbye to diaper rash with these tried-and-true remedies.

Sure, you can go online and send the first flowers you see, but a little thought and planning will go a long way toward impressing her. Sure, you can go online and send the first flowers you see, but a little thought and planning will go a long way toward impressing her. You will need a friend or relative of the recipient. Send her favorite. If she’s ever mentioned a favorite flower, buy that. You’ll get bonus points for listening to her. If you have no clue, ask a friend or relative of hers ...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

Learn how to do a cable triceps press down drop set. Presented by Real Jock Gay Fitness Health & Life.

Try out this beautiful and sexy makeup look with smokey eyes and neutral lips. Watch this instructional cosmetics video to create a romantic makeup look using tones of gold and brown eyeshadow with a subtly pink lip gloss combination. This makeup style creates a quintessential soulful look that compliments darker skin.

For this who want to create an easy romantic hair style, then this is the video for you. Our host will show you how to create soft spiral curls using velcro rollers and a curling iron.

In this video maniactive teaches how to embed a YouTube video in PowerPoint 2007. You must have a live internet connection to do this. Make sure your Developer tag is turned on in your ribbon. Click on the PowerPoint logo on top left , click PowerPoint options. Under popular click show Developer tab in the ribbon. Click OK. Now in the Developer tab you'll see a toolbox in the toolbar. Scroll all the way down to where it says shockwave/flash object. Draw where you want the video in your PowerP...

Staying organized with your digital music library can be frustrating, especially when you're downloading songs on different devices. Transferring music files to one central location doesn't have to be hard though, even when you download music on your Android mobile phone. So how do you get that music off the phone? Best Buy has answers. The Best Buy Mobile team explains how simple it is to transfer music files from your Android enabled cell phone to a Mac or PC computer.

Carolyn Dickerson teaches viewers about the connection between pink eye and makeup! Your pink eye may first start off and seem like a cold in your eye! Sometimes you may not know which pink eye you have. If the week progresses and your pink eye does not get any better, then you do not have a viral pink eye! It will continue to get worse if your eye does not drain properly! First, you can use sulfur based drops but this may be too much. You can also use a oral antibiotic! Swelling, draining an...

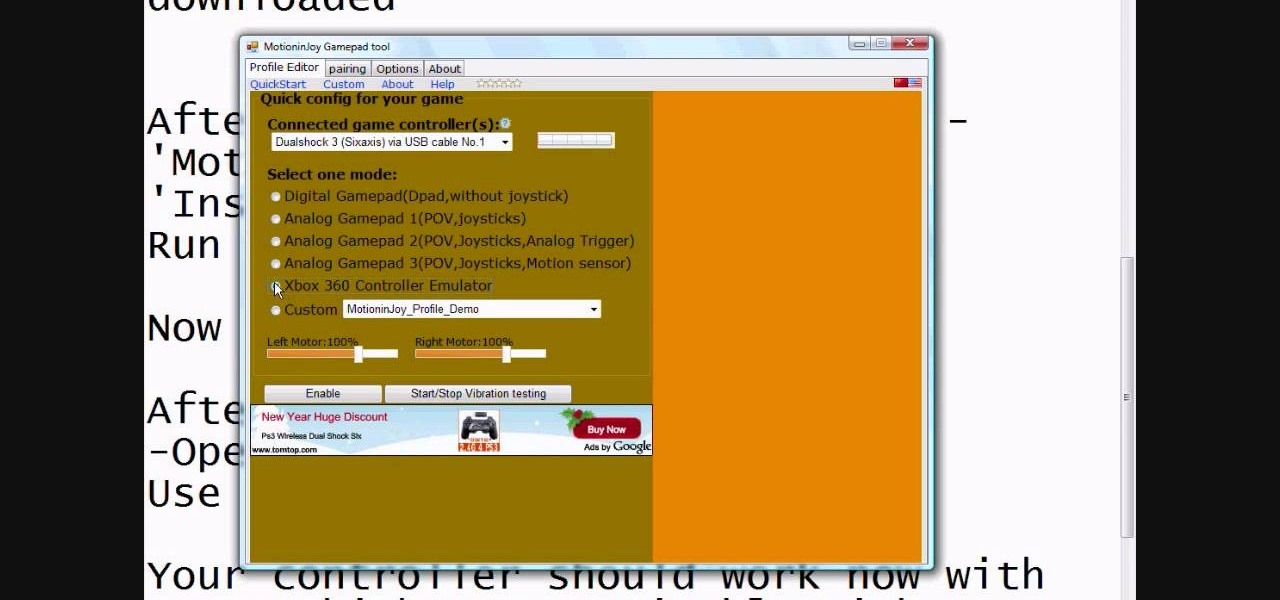
This video tutorial from radeon4350 shows how to connect dualshock PS3 console controller to PC. First, download driver software from here: http://www.motionjoy.com/download

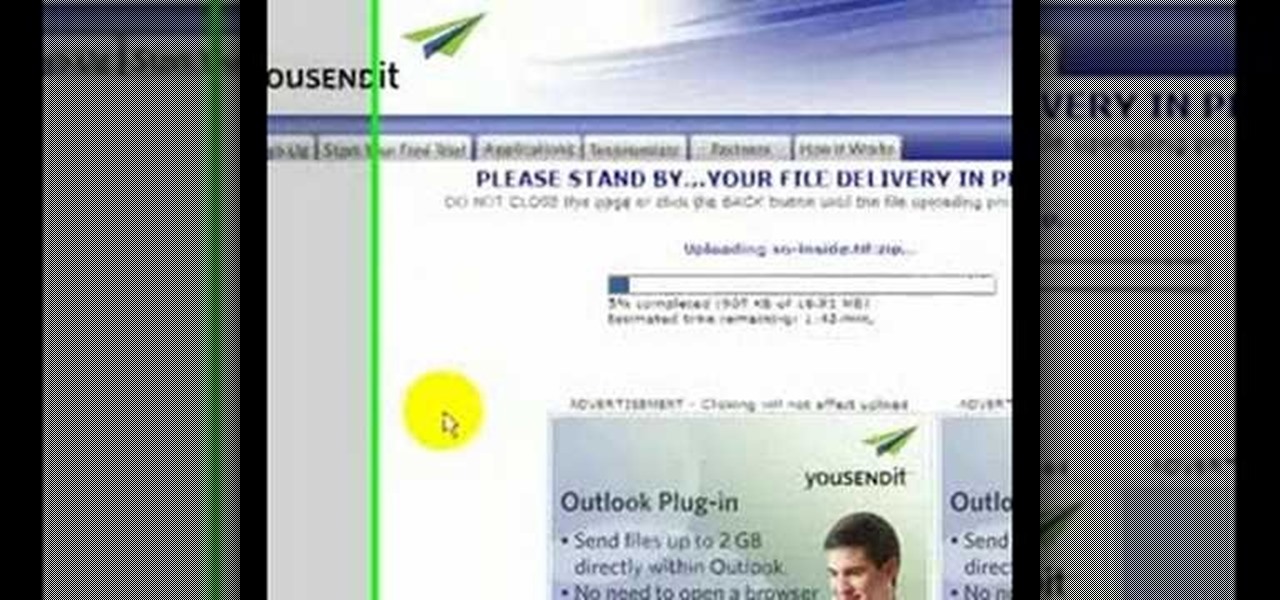
This video shows you how to use the online file delivery service YouSenditIt.com to send a file to someone. There are two ways to do this. One is to register for an account and send a file, and the other is to do it directly from the interface that you'll find on the website. You don't have to register, but generally if your file is going to be larger than 20 MB the person on the receiving end will need to register. But in this video we're shown how to send a file from the interface you're pr...

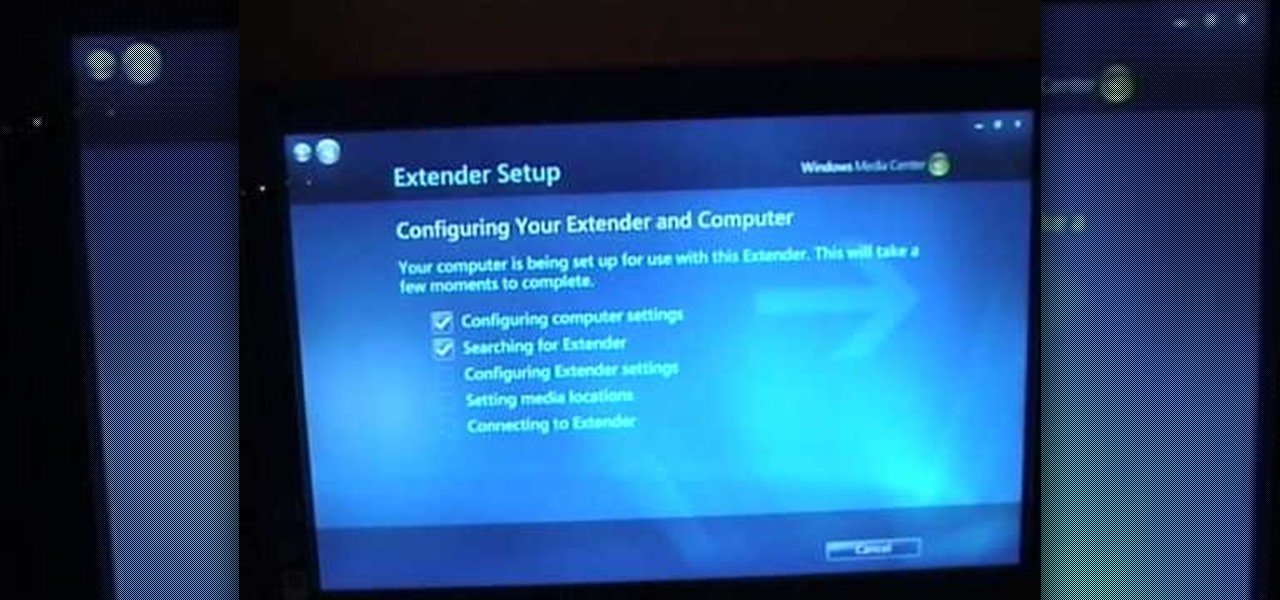
With Windows Media Center, you will have the ability to watch videos, live TV, and listen to music on the XBOX 360 without having to use your computer. You’ll need to have the following things: A PC equipped with Windows Media Center, your XBOX 360, and a fully functional high speed home network. On certain Windows 7 or Vista machines, Media Center is already included. (If not, it can be downloaded from Microsoft) A wired network is preferred for the best connection, although a wireless netwo...

Check out this awesome tip from CNET on getting FREE eBooks of the web and onto your Amazon Kindle for easy and cheap reading. They show you the exact process for getting free ebooks for your Kindle, so watch and learn. It's worth it!

HighQuality Tutorials demonstrates how to change your iPod Touch alpine default password. Changing the default password is useful when using your iPod Touch in a public setting to make it less vulnerable to hacking. To change the default password, first open up your internet connection and search for Putty. Download the Putty program. Open and run the Putty program. Your host name will be your IP address for your iPod Touch. Select port 22 and SSH and open up the program. Log in as root and c...