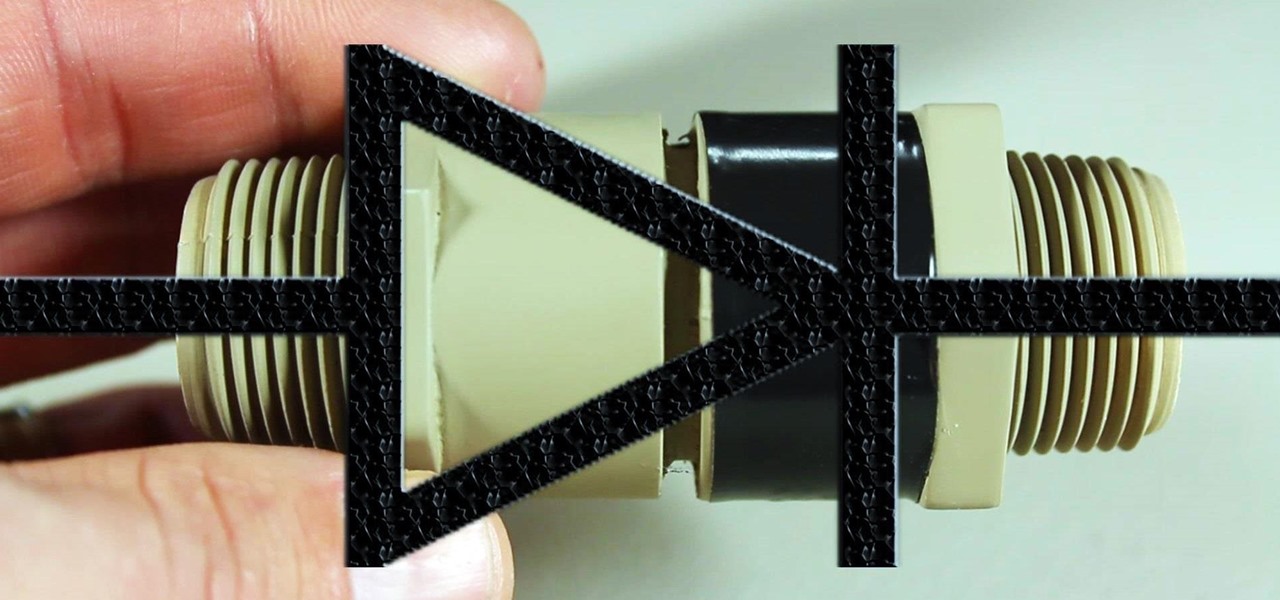
If you're going to build yourself a water gun to cool down this summer, or maybe just a useful water pump, you'll need some check valves. However, the most expensive parts of a water pump or DIY super soaker are usually the check valves. So, let's make some from scratch for as little as $0.35 each.

The iPod changed the music and electronics industries when it was first introduced way back in 2001. It is credited with ushering in the age of "connected devices," and has held a huge market share of around 70% for years. At the height of its popularity, the iPod made up almost 50% of Apple's revenue. Now that the smartphones and tablets we use every day have the ability to store and play music, the iPod's glory days are over. Nevertheless, there are millions of people who still use them, an...

Video: . Optimize your Marketing with a Mobile Website

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.

Microsoft's first venture into the tablet market, the Surface RT, combines many of the capabilities of a normal Windows 8 laptop into a super compact tablet, whose super-thin touch cover and kickstand can transform it into a functional mini-laptop, small and light enough to go anywhere you want. But like most tablets, the Surface comes with a rather limited amount of storage space. The tablet comes in either 32 GB or 64 GB, but we all know that's not the actual amount of storage space you can...

In the first part of this two-part guide, I covered cutting, grooving, beveling, making holes, and stamping/tooling. I hope you enjoyed that part, because we're pushing the accelerator to the floor and moving ahead at full speed!

Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone.

It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing auroras. The solar storm that produced the electromagnetic pulse and caused all this mayhem is known as the Carrington Event, and storms like it happen about about once every century.

War leaves a lot of stuff behind. Torn families, delegitimized institutions, mass graves, and unexploded ordinances litter the post occupation landscape. Whether or not you have driven the imperialist out, or are still in the phase of armed resistance, you will need the ability to safely diffuse bombs. My bomb defusing Silvia-bot can do it all. She can catch grasshoppers, cut wires, collect samples, tase enemies and even play chess! Materials

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

Need a quick repair job for your HP iPAQ Pocket PC RX3100, 3115, 3400, 3415, 3417, 3700, or 3715? Well, this video tutorial will show you how to disassemble the phone after it's been damaged. You'll see exactly how to take it apart, then simply reverse the instructions to put the HP iPAQ RX3100, 3115, 3400, 3415, 3417, 3700, or 3715 back together.

In this video series, you will get a glimpse of the beautiful town of Budapest, Hungary at night. Tour guide and local expert, Sarah Satmari, offers travel tips, destination ideas, and history. You will learn what do in Budapest if you are single, how to have a romantic evening, where to meet local girls and boys, how to dress, and where to eat.

Chakras represent a connection of spiritual energy between the human body and the mind. Discover information on chakra symbols and meanings with tips on alternative medicine from a spiritual healer in this free video series on alternative healing and chakras.

Ready to try and sew-in your own weave? It's a big decision. As with everything that concerns our hair, we struggle with the pros and cons and often dwell on what could go wrong. Pixie cut. Perm or not? New shade (of pink, purple, or blue). These are all major decisions because ... well, it's our hair, and hair is such a big part of our style. To get a weave or not calls for careful consideration, and to sew one in yourself, that's an even bigger internal debate.

Apple Maps keeps getting better and better for all the hikers in the world. The latest update gives you access to thousands of detailed trail maps within U.S. national parks and topographic views, but it also lets you create your own walking and hiking routes.

It's no secret that Apple's Notes app supports attachments such as photos, videos, and web links, as well as other file types like PDFs, word documents, spreadsheets, locations on a map, and audio tracks. While images, videos, and document scans are simple to add on an iPhone or iPad, other file types aren't as easy — at least until you know how.

Whenever your iPhone's ringer is on, you'll hear Apple's iconic "Connect Power" chime every time you connect it to a wired or wireless power source, which lets you know that charging has started. There's no way to disable the sound without turning on Silent mode, but there is a way to make Siri automatically say whatever you want after a successful connection.

Your iPhone's Mail app has a lot of fantastic productivity features, such as unsending emails, follow-up reminders, opening drafts from almost any view, the snooze option, bulk-selecting messages, and the formatting toolbar, but one of the most helpful ones might just be the one you're not using.

Digital artist Beeple's $69 million NFT art auction at Christie's has a second act called Wenew, and includes attempting to open the digital art floodgates to mainstream collectors and artists alike by using physical goods.

Not all Kickstarters are created equal. Some take forever to get their products to supporters, and when the product does arrive (usually much later than promised) it's often very rough around the edges.

If you buy an Android phone from any of the big US carriers, it will come with several extra apps in addition to any apps the manufacturer preinstalled. It's all in the name of profit, of course. Some of these apps are from companies that paid the carriers to distribute their software, and some are from the carriers themselves, usually aimed at upselling you or perhaps collecting a little data.

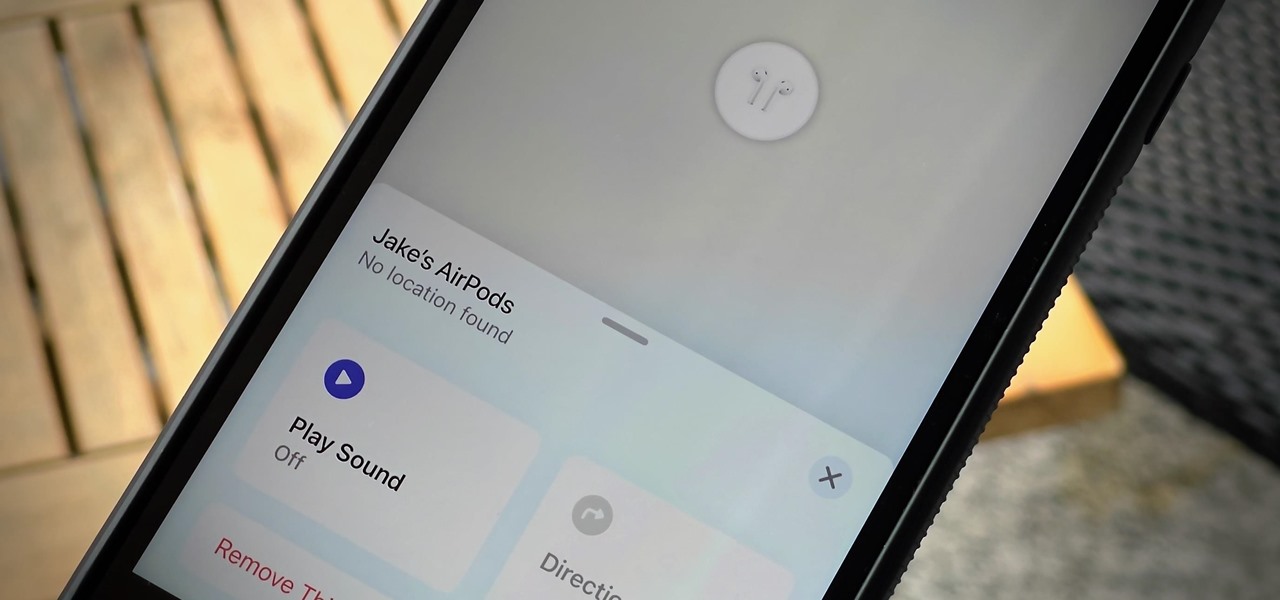
If you lose your AirPods, AirPods Pro, or AirPods Max, you can turn to Find My to locate them. But sometimes, things don't go according to plan, and many things can go wrong. For example:

The COVID-19 pandemic has increased the demand for virtual and remote collaboration, and Microsoft has a solution that may serve as the catalyst for more such apps for augmented and virtual reality in the near future.

The average business person likely recognizes Epson for its printers or even its projectors, not the futuristic AR wearables.

Despite the unfortunate social media-driven association of Corona beer with the virus behind a global pandemic, beverage maker Constellation Brands has pushed its marketing forward like a lime through the mouth of a beer bottle.

Ever since China's Nreal unveiled its Light smartglasses at CES two years ago, an army of look-alikes have emerged from the Asian nation.

It's Black Friday time, and in 2020, that means a lot of online deals to make up for more stores closing on Thanksgiving, as well as everyone avoiding in-person shopping because of the coronavirus. But while you may wish to grab a better 65-inch 4K TV, the new PlayStation 5, or some hacker hardware on sale, Black Friday is also the best time to invest in your programming and cybersecurity education.

One of China's largest smartphone makers, Oppo, just took the wraps off its new design for augmented reality smartglasses called AR Glass 2021.

Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Samsung decided to jump into the foldable category early, announcing the Galaxy Fold in February 2019. After a major hiccup, Samsung released the phone four months later to praise. But Samsung's not finished with foldables, as the new Galaxy Z Flip is just on the horizon.

Back when I worked in the music industry, I never imagined there would be a day that I'd be able to sit in a room surrounded by virtual album covers while listening to beats, but that day is really here.

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.