As of today (January 18, 2012) many websites have "blacked" out their content for the day, one of the more notable websites is Wikipedia.org. As this can be a small compromise as an act of protesting against the heinous bills going through the United States' Congress. A lot of these websites are using a type of Java-Script or JS for short, and others are using simple little Pop-Ups to block the sites. Through the use of some clever addons everyone that cares about their online security should...
Battlefield 3 officially comes out tomorrow but people have figured out a way to play it today if you have it downloaded (digital pre-install). All you have to do is fake an ip to make it look like your timezone is ready to play. I'll try this when I get home, in the meantime:

A proxy is a server that lets a client to connect to it and forward its traffic. This enables a certain "layer" of protection by masking your IP. An IP address can be used to learn your location and track you on the Internet, thus eliminating any form of anonymity that you may have.

One of the most exciting new features announced by Google+ was the ability to broadcast hangouts live via YouTube, which was recently demonstrated with the very first Google+ Hangout On Air with +will.i.am of the Black Eyes Peas.

I was going to update the first list of 15 Brilliant Google+ Female Photographers to Circle, but then I kept coming across so many amazing women that I decided to create another post highlighting their work. I received many great suggestions from +Kelli Seeger Kim (who takes some beautiful pictures herself), +Suzanne Haggerty, Google+ Photos Community Manager +Brian Rose, and many others.

Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by amateur and wannabe hackers who want to have a little fun, but don't want to learn how to actually "hack" anything.

The use of unmanned aerial vehicles (UAVs) has been widely used by the military for surveillance and reconnaissance missions—even armed combat. But there are other beneficial applications of an unmanned aircraft, such as search and rescue operations, scientific exploration, locating mineral deposits, transporting goods and even filming bikini models. But drone development can be pretty pricey, unless you just happen to have a 3D printer...

Age doesn't matter in the world of programming, only skills, and recent high school grad Jack Eisenmann definitely has them. He recently built a homebrew 8-bit computer from scratch, calling it the DUO Adept. A worn television makes up the monitor and speaker system, an old keyboard acts as the input controller and the actual computer itself is housed inside a clear Rubbermaid container, consisting of 100 TTL chips and a ton of wire.

Firesheep caused quite a stir when it was released last October, giving both hackers and non-hackers instant access to people's account information when on a public Wi-Fi connection. When logged into an insecure website on the same network as someone with Firesheep, you're giving them access to the cookies that keep you logged in. This is called session hijacking, and grants them easy access to your accounts, like Facebook, Flickr and Twitter. Now, there's an even easier way to do this—a mobi...

Fujitsu Limited has developed what they call the world's smallest Windows 7 PC, which will become available shortly on NTT DoCoMo, Japan's predominant mobile phone operator. The dual-boot device acts as both a smartphone and a portable personal computer that runs the Windows 7 operating system.

I'm not much for politics, but I do like to keep tabs on our elected government officials from time to time, since I am a registered voter and believe that every one should vote (unless they're just voting to say they voted). This pretty much means I pay attention to my local and state officials, the presidential candidates, and of course, any political scandal that makes me chuckle.

In my previous post, I wrote showed you how to install Ubuntu 9.10 (Karmic Koala) on your PC. This time we'll be doing an upgrade from that to Ubuntu 10.04 (Lucid Lynx).

According to PlayStation Network @ Home, a new app may allow hackers to ban or unban anyone they please from PSN.

The exile is officially over. Let the good times roll. Unequal Technologies has just signed Michael Vick as its corporate spokesman. They have applied for 50 patents that largely employ the Dupont-created Kevlar for "shock suppression". Formally speaking, this is his first product endorsement deal since his arrest in 2007.

If you would like to restrict what appears on your Facebook page, here's a novel way to retain ultimate control, coined the "super-logoff" method:

I guess I must still be sad that Dennis Hopper died, while searching his name I found this amazing project by a group known as Mashed in Plastic.

Lifehacker provides a helpful guide for Facebook addicts everywhere. How does one get around an employer's website blocker? The trick is to set up a local web server running from home, from which you can use a proxy to access any site you please.

Working from home is already challenging. Add the threat of a cyberattack into the mix, and the situation gets even hairier.

Figuring out the Wi-Fi at a new location is challenging enough. Connecting to said Wi-Fi should be as easy as possible. Unless someone you know is already connected on their iPhone, you're probably used to the usual routine of heading to the Wi-Fi page in the Settings app to get yourself online. Luckily, there's now a much better way to do so.

Audiophiles should know Pandora has an option to increase its sound quality. Change one simple setting and you'll enhance your experience with high fidelity audio. Even if you're not an audiophile, who wouldn't want the best possible sound?

One of the coolest features we've come across so far in iOS 10 is a parking spot reminder. Go for a quick drive (making sure to take your iPhone with you), and when you arrive at your destination, you'll get a notification that tells you where you parked.

Welcome everyone Today i will show you a simple but very useful way to stop your ip leaks . In order to stay anonymous on the web you HAVE to do this.

As softModders, several of our guides dealing with modifications involve connecting our smartphones to a computer, allowing us quick and complete access to our device.

Earlier today, @DesignGears leaked an unofficial KitKat build for the Galaxy Note 3, and now they've dropped one for our Galaxy S4s, too. How to Install the 4.4.2 Build

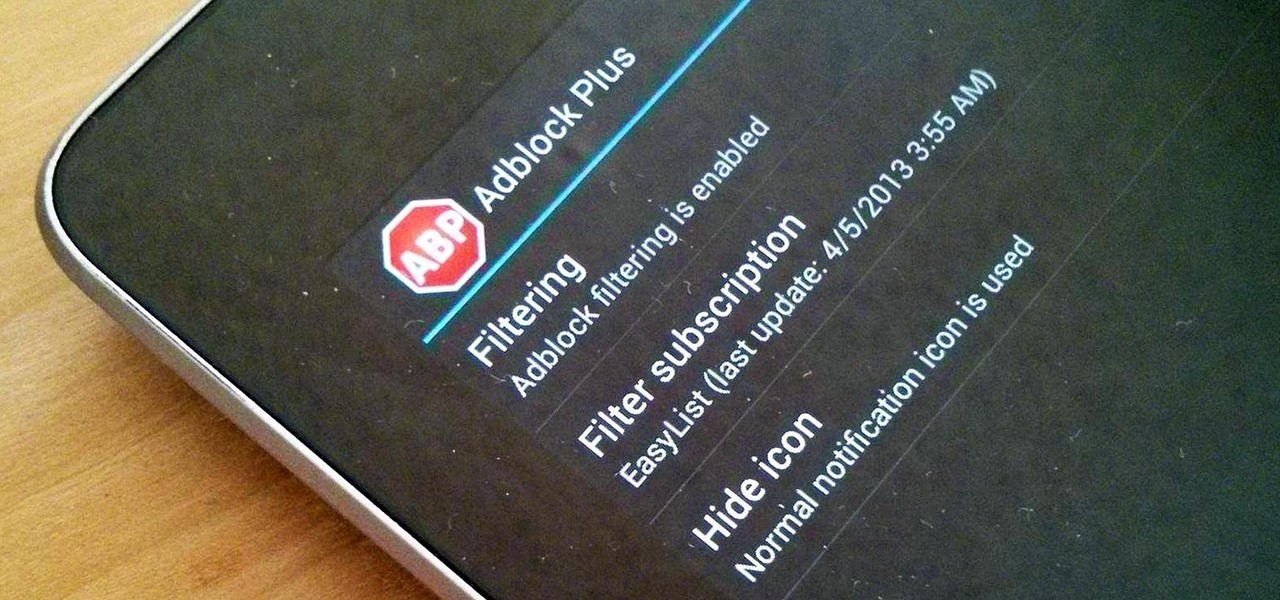
Adblock Plus is a well known add-on for Google Chrome and Firefox that eliminates all of those annoying and obtrusive advertisements on the webpages that you visit.

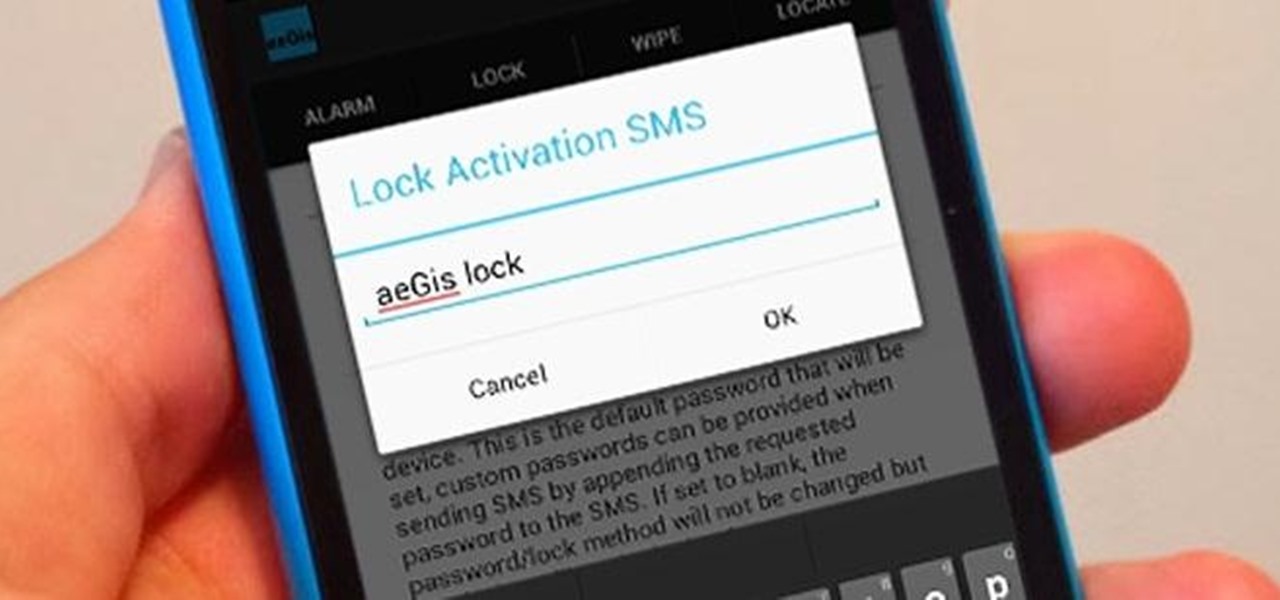
The great thing about security apps (other than the obvious) is that there is an abundance of them littered throughout the Google Play store. Cerberus, Got Ya!, Avast! Mobile Security, Norton Security & Antivirus, and Android Lost Free are just a few of the gems you can find in the plentiful sea of security apps for Android. Once in awhile, though, a new security application comes along that stands out from the rest, like AeGis.

The connection between self-control and glucose is not unique to humans. A bunch of trained dogs were divided into two groups. One group was instructed to sit and stay for 10 minutes. Dogs in the other group could run around and do whatever they wanted.

Firefox's hidden advanced menu gives you several ways to tweak the way it works under the hood. Here are a set of settings to change to get it to browse faster than ever.

No exaggeration in today's headline, design student Anna Schwamborn has actually designed a jewelry line made from the hair and cremated ashes of dead loved ones. Human hair sure makes a nice accent to the black bone china (note the word "bone" - human ashes are mixed in).

Swedish advertising company, Rolighetsteorin, recently created musical stairs reminiscent of Tom Hanks and Robert Loggia's beloved FAO Schwartz piano scene in Big. The campaign is for Volkswagen, though I'm fuzzy on the connection between the two.

We assumed the novelty of the Apple iPhone would have worn off by now. We were wrong. It could get better than TapTapRevolution and Shazam.

PDF is a convenient format for documents that can embed text and pictures and can be read by almost any device—personal computers, laptops, smartphones, etc. However, PDFs are mostly read-only files, so sometimes it's necessary to convert them to JPG images, a universal format for pictures. JPGs can be modified by software such as Adobe Photoshop or posted on Facebook.

3 Effective Techniques for Following Up With Leads The follow-up phase of the sales cycle is like having a goldfish for a pet, in that it's easy to forget about it, especially compared with the excitement of finding new sales leads. This is unfortunately, though, because you can outperform your competitors by following up with leads and encouraging them to choose your business.

Computer viruses are terrifying. They are undetectable, dangerous, and operate constantly right under your nose. For the average computer user, there are only a few repair options. You could buy expensive antivirus software that causes more problems than it fixes, you can wipe your hard drive clean and lose all of your important data, or if all else fails—just switch to Linux.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

Watch this video tutorial for troubleshooting dishwasher problems. Check the following: are you over loading on detergent causing soapy residues? Have you stacked your dishes badly? Is the seal around the door old and worn? Do you have a dodgy pipe connection? Worst case scenerio is not good though, old machines corrode at the bottom and if this is your case then I guess it's time for a new one.

So your washing machine is on the blink? Dirty clothes piling up? You're embarrassed of your smalls and can't face the launderette? Watch this video tutorial to save your blushes and get your machine up and running again in no time...

Remember the arcades? Were you saddened when they closed up one by one, leaving no outlet to actually go out and socialize while you played video games? With all the home consoles and internet connectivity, gaming has evolved, but the social factor has been eliminated. Sure we can play against others, but they may be miles and miles away. Remember back in the day when you could go down to the corner store to play your favorite game and show off your skills in front of a crowd? Well, all is no...

Ive noticed when Im drunk I SUCK HARD. By that I mean I give some serious hickeys. Not a little romantic pink mouth size thing. Im talkin some major black, blue, purple, red broken blood capillary, teeth included, raping the whole side of a neck type shit. It looks majorly brutal and takes months to go away.

Moms, don't get stuck in a clothes rut. Shop in your own closet for new looks. Here we show you four outfits that this mom came up with. Casual everyday