Communication is the key to any healthy relationship, and when I say any, I mean human and non-human. Previously, one of the biggest culprits for not understanding what you meant was Siri, but now it looks like it has some competition with the new Kinect system, which can control practically everything on your Xbox One—if it can understand you.

I've never been much of a runner. I've tried running alone, with a partner, on busy sidewalks, and back country roads, but I just never got it. There are a few other forms of exercise I genuinely enjoy, but have yet to experience that "natural high" that avid runners are always talking about.
In any project management career, there is no such thing as a person who knows everything for each project. Many times, those who got too much confident with their jobs fail because they were not able to make things clear before and during the project implementation.

Baking extraordinaire Lily Vanilli has made some just-slightly-too-realistic-to-look-yummy bleeding heart cakes for people to give to their respective beaus on Valentine's Day. While it's pretty tricky to get your hands on one made by Lily herself, you can make one yourself if you've got the heart. Check out A Lot on Her Plate's video with Lily to see how to make this so-called "anti-Valentine's Day cake," which also works well for Halloween. To follow along with them, check out the full reci...

If you are looking to improve your classical piano technique then this three part how to video is the place to start. You will learn how to practice and study Chopin's nocturne number 20 in C# minor. This detailed lesson goes over where to place the accents, analyzes the dynamics and legato playing technique. This piano tutorial teaches you the best way to practice it so you can Chopin's nocturne no.20 quickly and easily. This piece is not for beginner students, this lesson is directed to adv...

Is there something missing from your dance relationship? This four part how to video teaches you how to communicate with your dance partner. Use these secret tips from Naomi Uyama and Andy Reid, and become a better dance partner.

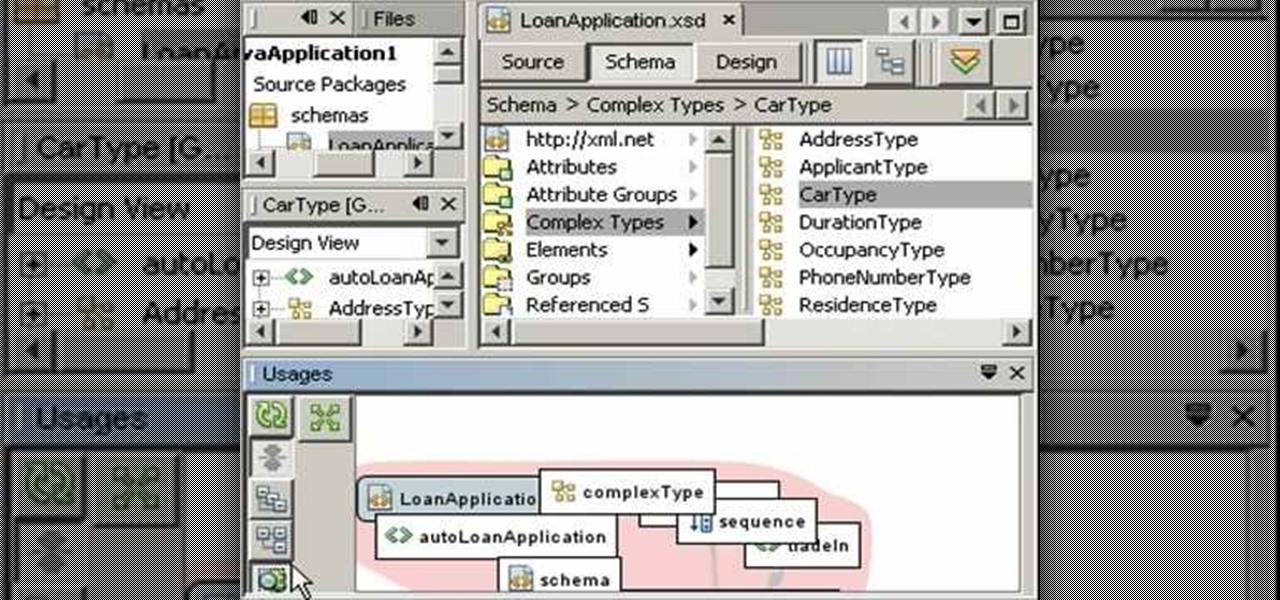
Watch this video tutorial to learn how to use the XML schema tools, which enable you to create, visualize, and edit XML schema in NetBeans 6.0. With these tools, you can visualize relationships between schema elements and use queries to find usages. You will also learn how you can easily create XML schemas by example. You will see how to navigate large schemas in the Design View, and you will learn how to visualize and edit multiple file schemas.

Sometimes you've gotta take your shirt off fast, whether it's a romantic night, a quick jump in the pool, or for extinguishing someone on fire.

Today, I'm taking a short break from my usual secret tips to share some exciting news with all of you. As some of you may already know, my first published book "I Think I Am in Friend-Love with You" will be released in bookstores next month.

Spider-Man hits the iPhone, iPod Touch & iPad! In Ultimate Spider-Man: Total Mayhem, you take control of Spidey, slinging webs and fighting crime. No longer do you have to stick to comic books, you can enjoy Spider-Man right from your Apple mobile device.

How do you raise a smart child? This video answers that question. If you want your child to be as smart as Albert Einstein when he grows up, then you have to start with the basics. Hugging and playing with your child is important. So are talking, listening, and reading to your child. Once you lay down the foundation for a great relationship, it will naturally pave the way for the smart kid you always knew you had to emerge. This video shows you what you need to get the foundation in place.

Improving interpersonal perception builds communication skills and can provide relationship help. Part 1 of 6 - How to Improve interpersonal perception.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

With any continuously active software, it can start to become fairly complex after a few years of updates. New features and revisions both get layered into a thick mesh of menu systems and controls that even pro users can get bewildered by. If you are new to a certain application after it has been around for many years, it can be downright intimidating to know where to begin.

Listening to Beethoven's "Moonlight Sonata," with its moody minors and grab bag of sharps, is like turning through page after suspenseful page of a forlorn Romantic era novel.

Try out this beautiful and sexy makeup look with smokey eyes and neutral lips. Watch this instructional cosmetics video to create a romantic makeup look using tones of gold and brown eyeshadow with a subtly pink lip gloss combination. This makeup style creates a quintessential soulful look that compliments darker skin.

For this who want to create an easy romantic hair style, then this is the video for you. Our host will show you how to create soft spiral curls using velcro rollers and a curling iron.

There a very few people who don’t like gulab jamun, as for us, we just love them. It is a perfect dessert for any occasion - wedding, birthday party, potluck or a romantic dinner for 2! Watch this how-to video to learn how to make gulab jamun, a delicious Indian dessert.

We've gathered some of our favorite pranks with the seasonally appropriate for all you college kids out there. You're more than likely cohabitating with a complete stranger, and what better way to make a good first impression and develop a strong personal relationship than subject them to a hilarious prank?

This tutorial tells how to get Keira Knightly-esque hair.

Continuity is an underrated and more importantly, overlooked aspect to multi-cut scenes. Many films, television programs and internet videos forget its importance. So this week, The Shirtless Apprentice give his tips on the subject as he sits down and has a romantic candlelit dinner with continuity.

The realm of science fiction isn't all lasers and cute green toddlers, sometimes alternate science history is sci-fi, too, as exampled by the Apple TV Plus series For All Mankind.

The still-unfolding story of China's Nreal augmented reality startup continues to develop, with each turn uncovering another unexpected wrinkle.

In the late nineteenth century, the advent of the motion picture wowed audiences with a new storytelling medium. Nearly a century and a half later, augmented reality is establishing a new frontier in film.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

While Toyota ranks as the leading automotive brand in the world, the company is a follower when it comes to augmented reality.

Smartglasses maker Vuzix has emerged with the first hardware powered by the Snapdragon XR1 chip, roughly nine months after Qualcomm introduced the chipset designed to drive augmented reality wearables at the Augmented World Expo in Santa Clara.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.

Automotive augmented reality company WayRay has set its destination for a $1 billion valuation with an estimated time of arrival of 2019, and it has just passed a major milestone towards that goal.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

On Tuesday, at the Unite Berlin developers conference, Unity unveiled new tools designed specifically for augmented reality that could literally raise the technology to the next level.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Cosmetics maker Coty is hanging an augmented reality Magic Mirror on the wall of its Bourjois boutique in Paris that will tell customers which shade of makeup will make them the fairest of them all.

The cosmetics industry faced a rude awakening on Friday as beauty behemoth L'Oréal gobbled up ModiFace, one of the leading providers of augmented reality technology to the cosmetics industry (price details for the acquisition were not disclosed).

If CES 2018 is the starting gate for this year's race to release smartglasses, then Vuzix is already racing down the augmented reality track with its Blade smartglasses.

Transparent display maker Lumus has reached a deal to license its augmented reality optical engine models to Quanta Computers for mass production of displays for consumer smartglasses.

We may have to wait a few years before they arrive, but reports of Apple's headset taking shape in Cupertino gives the tech world hope that its white knight for consumer AR is on its way.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.