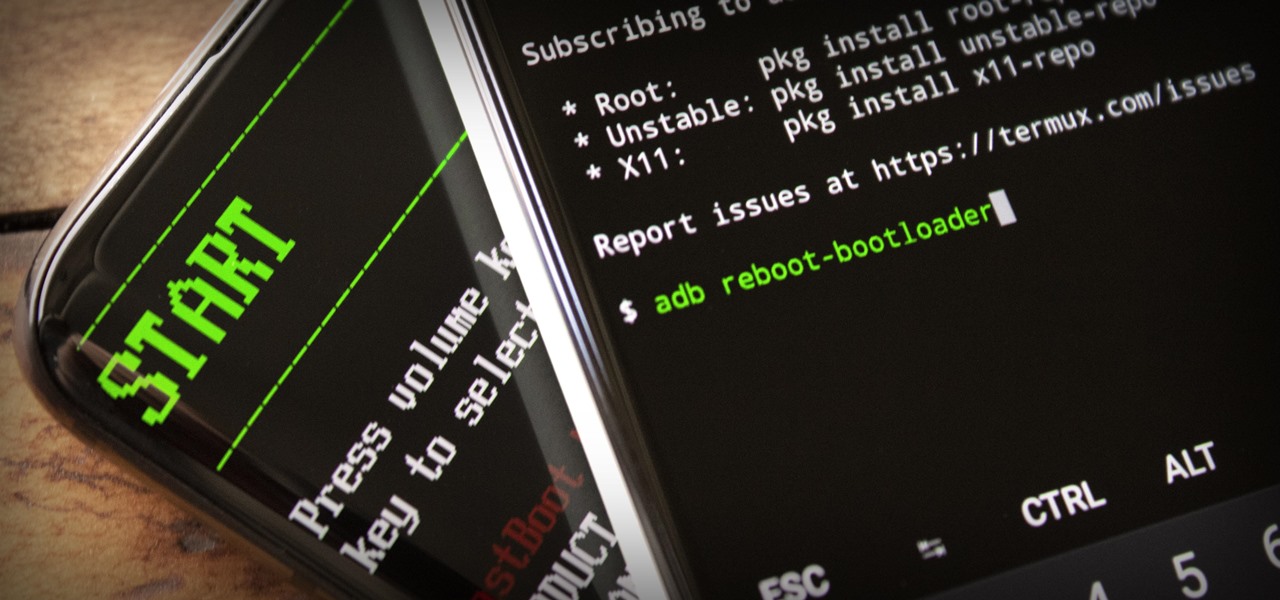
As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Recently, many manufacturers have started offering phones with a clean, stock Android UI. Motorola, Essential, Nokia, and OnePlus are probably the biggest names that have listened to user feedback and shifted more towards AOSP. But if your phone still has a bloated OEM skin, there are a few things you can do about it.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Most of us lead busy, work-filled lives, often clocking in a 9-to-5 five days a week. And when that clock signifies the hour to leave, the last thing on anyone's mind is: "Time to go to the grocery store to pick up more fresh produce!" (Well, to be fair... maybe more people are psyched about this, but I know with certainty that I am not one of them.)

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You paid for it, so you were free to use it for whatever you wanted. Unfortunately, those days are long gone.

Google recently updated the camera software for the Nexus 5, and in doing so, made the app available to all devices running Android KitKat. This means that not only do we get a nice new camera interface on our phones, but we also get the benefit of an expanded development community.

If you're reading this, chances are you're a softModder, someone who doesn't let anything stand in his or her way from ultimate customization.

In this tutorial, we learn how to dye your hair at home for blondes. First, purchase a couple boxes of hair dye that are the right colors for your hair. After you do this, take all of the products out of the boxes. Now, pour the small bottle into the large container and put the rubber gloves on. You don't need to use both containers, you can just use one if your hair isn't that thick. Snip the top off the container, then start to shake up the container until it's well mixed together. Now, sta...

Micro misters allow for low volume of water over a wide area. They give good moisture coverage. Systems can be pulled up, changed and made into what you need it to be. Keep potted plants separate from other plants. They should have their own system. There is a system to encourage growth of root systems of various plants. Shrubs get two emitters in case one clogs up, the plant still has moisture. Having the water at the base of the plant limits weed growth. There is a temporary system to get t...

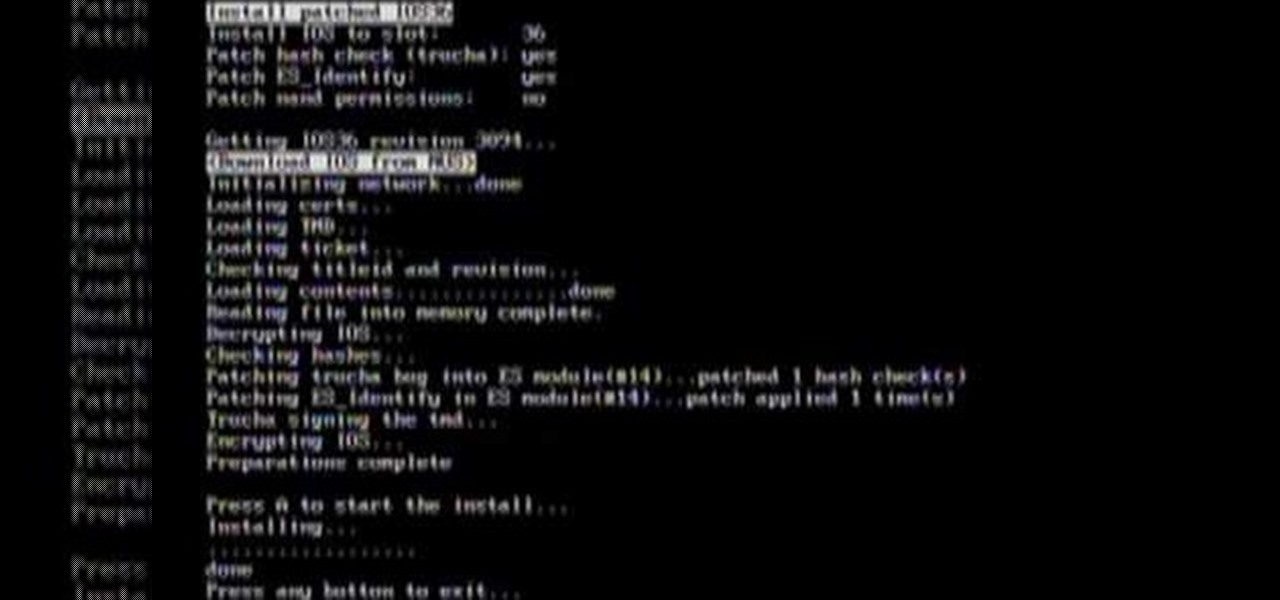
Trucha Bug Restorer is a powerful piece of homebrew software that you can use on your Wii to make sure that it is formatted properly in order to play burned games and use other hacks. This video will show you how to use it to set up an installation of cIOS on your Wii, which is the program that allows you to play burned backup copies of games.

Cajun Cooking TV shows viewers how to make a Cajun pot roast in your crock pot. First chop up turnip roots, baby carrots, shallots and garlic. First, cut several holes into your steak and stick garlic into each hole. Now season the meat with all purpose season on all sides! Now, place your meat in the slow cooker with 1 tablespoon of olive oil. Now on top and on the side of the meat add in all of your vegetables! Put in about 1 cup of water into the slow cooker, you don't want to put too much...

Master Gardener Rosamarie Maddox asks John White, Doña Ana County Extension Agent, about problems facing her pecans, grapevines, and native shrubs. An unidentified insect found on her pecan tree is identified by John White as a Twice Stabbed Ladybug. This ladybug is a useful insect that often over-winters on the tree and helps takes care of the aphid problems faced by pecans. Pink fuzzy coating on pecan nuts is also brought up. The coating is normal for pecan and contains bitter tannin. Too m...

In this segment of Southwest Yard and Garden, John White and Bill Alford are going to be talking about fruit production and how to harvest figs in southern New Mexico. Bill starts off by talking about his nine year old Black Turkey tree. He says he digs holes and arbor each spring, then uses half a cup of fertilizer per hole. The roots of a fig tree usually grow out past the outer parts of the tree so it's important to make sure you plant has adequate room to grow correctly. A person can mayb...

This video shows you how to draw a dog house in Adobe Illustrator. In this video, first the scale is selected, and with the help of a air brush tool, a square is being made as a front of the house, then a top is drawn and then the back. Then the entrance is drawn. This is done by selecting this object, then select the paint bucket tool, select color and then this object is filled with color. Then secondly, using marquee tool, two large spots are made in the middle of the door object to make i...

It doesn’t matter how long ago your last geometry class was, you can still impress your friends by finding a geometric mean. The geometric mean can be used to find the average of numbers with out unusually high or low results effecting the result.

Your quick and easy guide to styling side swept bangs within 2 minutes. After blow drying your hair, take a round brush and roll your bangs up, under and to the side that you want your bangs to sit. Comb your bangs down over your forehead, then comb your bangs to the side. Using some styling product, such as molding gunk, paste or wax, take a small amount of product and rub between your hands to ensure even distribution. Using your fingers, work the product through your bangs, starting at the...

Enjoy a delicious Korean dish called Bibimbop with a Japanese twist! Join Gwyneth Paltrow and Chef Lee Gross in Paltrow's GOOP kitchen to learn how to make bibimbap (mixed rice, or roughly translated to "mix it up").

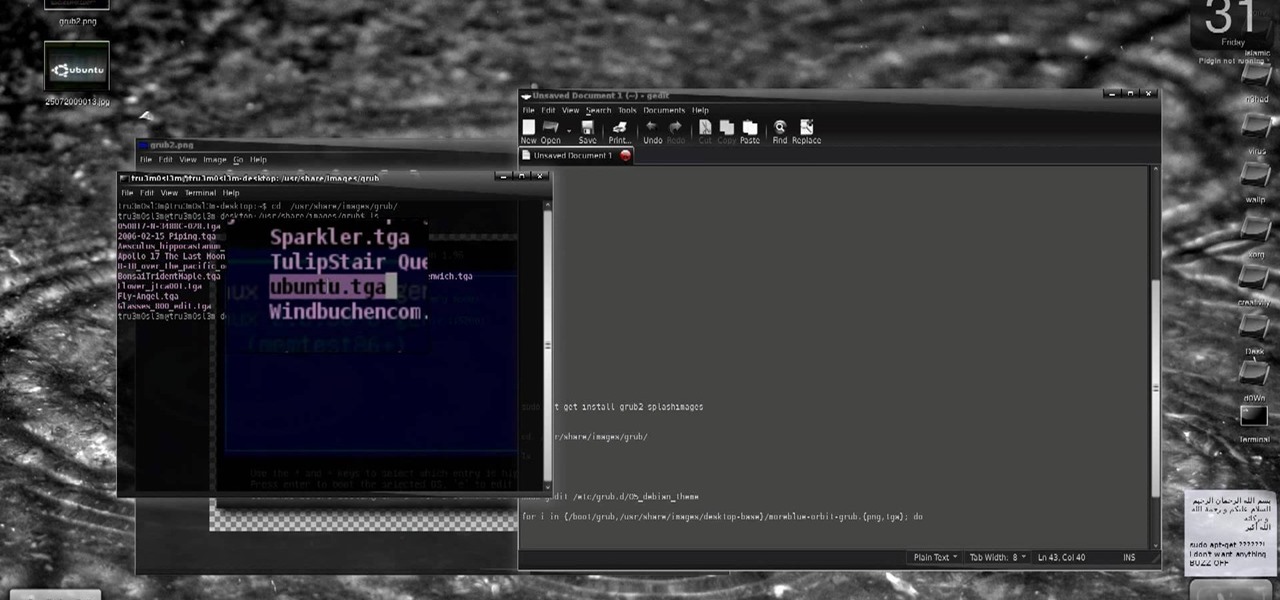
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install GRUB 2 and apply themes on Ubuntu Linux.

This video will show you how to record video on your Apple iPhone 3G for free! This is a complete guide to installing the iPhone Video Recorder on your iPhone 3G, which also works on the First Generation iPhone.

ADB and Fastboot are powerful tools that have always required a computer. But with the right setup, you can now send commands to a phone using another phone.

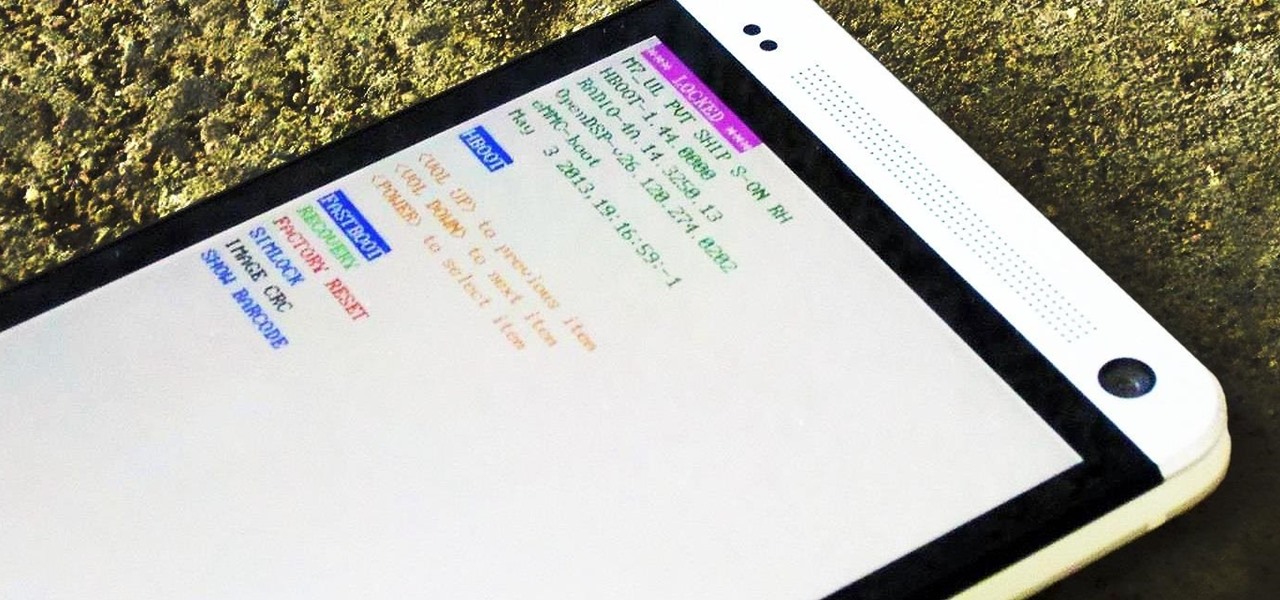
OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

Stadia is a lot like an Xbox or PS4, except there's no console — the games just stream from Google's servers to your phone, computer, or TV. But Stadia is limited to Pixel phones for right now, and when Google does expand support, it will still only be for select phones. Thankfully, there's a workaround for that if you're rooted.

Whether you love Motion Sense or think it's a gimmick, one thing we can agree on is that its functionality is limited. It's currently limited to switching tracks on a playlist, snoozing alarms, silencing calls, lowering the volume of alerts, and checking notifications. But a new mod will help you do so much more with it.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

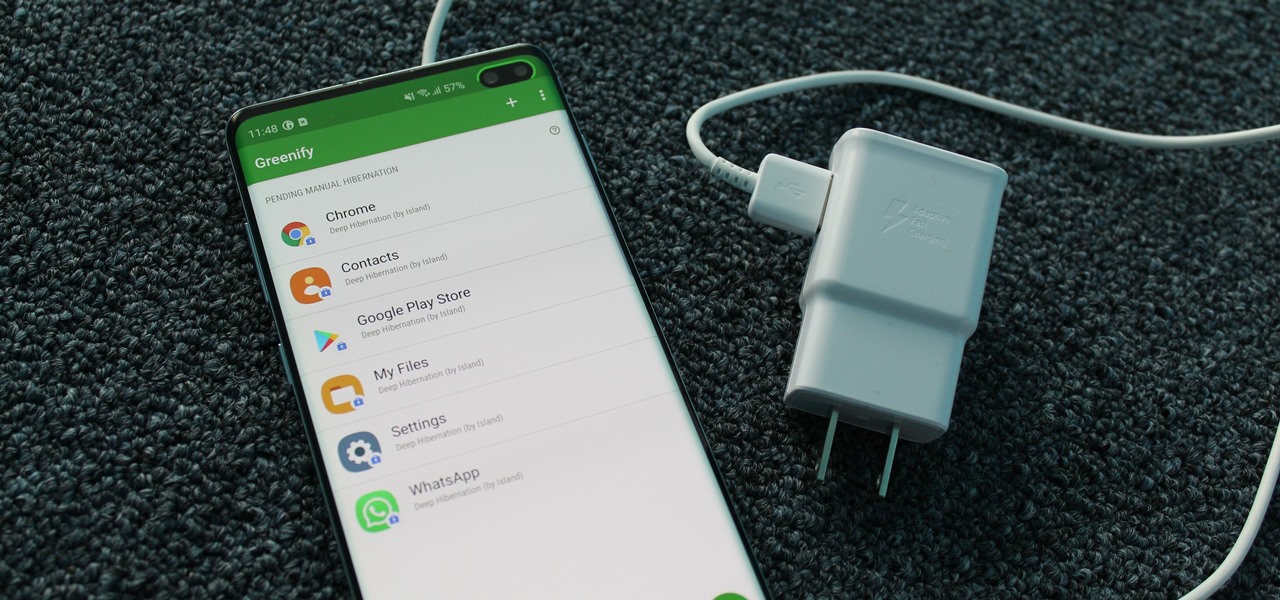
Despite newer phones having larger batteries, after a few months, my battery life drops significantly. I started researching solutions after my third phone. No matter who I asked, the most recommended solution was always Greenify. And unlike other solutions, you don't need root to use it.

With the new navigation gestures in Android 10, you reclaim a lot of screen real estate that used to be occupied by the back, home, and recent apps buttons. But there's still a small bar on the bottom edge of the screen, and in most apps, it still sits atop a black background. Thankfully, an easy hack will give you true full-screen without breaking the new gestures.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

The Google Phone app is one of the best dialers for Android today, especially with all of the unique and exciting features it brings to the table. Unfortunately, without owning a Pixel phone, you are unable to officially download the app, making a modified version your only option. However, this version of Google Phone is missing a few key features, such as spam protection and business search.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Haptic feedback and vibration of our smartphones have come a long way in recent years. These features are much more premium now than they once were, but most users are still unable to adjust the intensity for notifications or phone calls. Most higher-end devices make less noise on surfaces than in the past, but adjusting these values can still come in handy even today.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.