If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .
When the Galaxy S6 hype-train was building momentum ahead of the phone's release, many reports had Samsung cutting back on its much-maligned TouchWiz skin. In the end, these reports were either highly exaggerated or entirely fabricated, because while not as egregious as previous devices, Samsung's signature bloated UI and duplicate apps are definitely present on the Galaxy S6.

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

Protein powder is a fad in the same way that Justin Bieber's music is: you either love it, or you hate it. Everyone I know has a strong opinion about protein powder, ranging from "daily necessity" to "utterly useless."

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

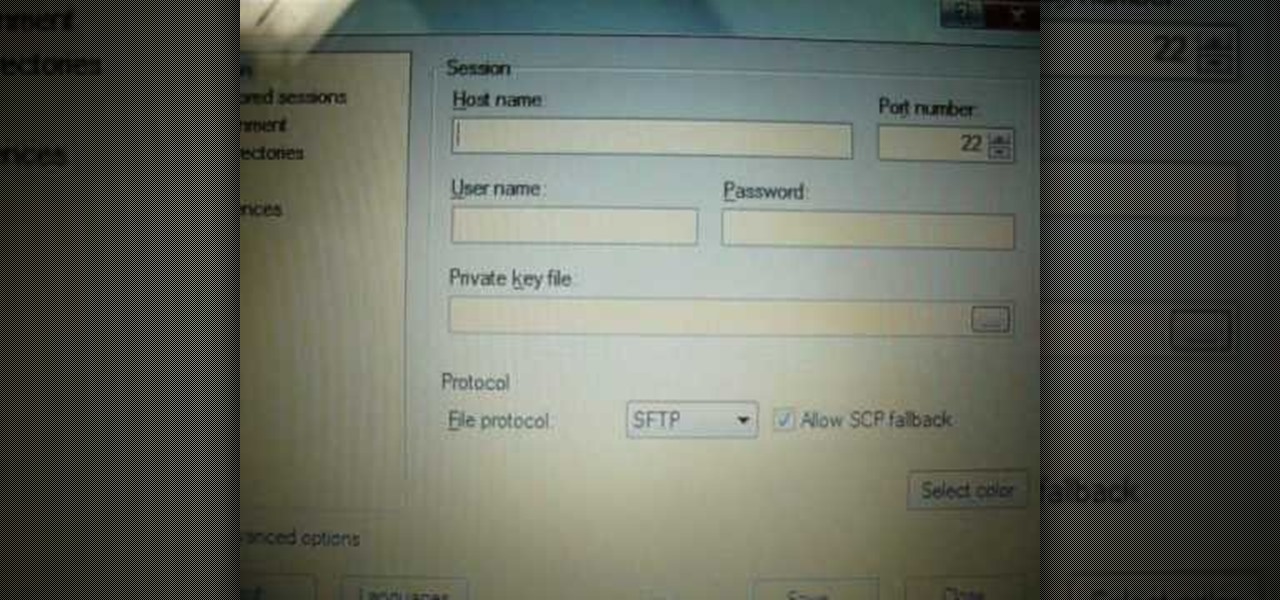
Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

When it comes to dictating what happens when the Galaxy Note 3's S Pen is detached, the stock settings that Samsung provides are severely lacking. There are only two measly options: launching Samsung's own Action Memo app, or displaying the Air Command menu.

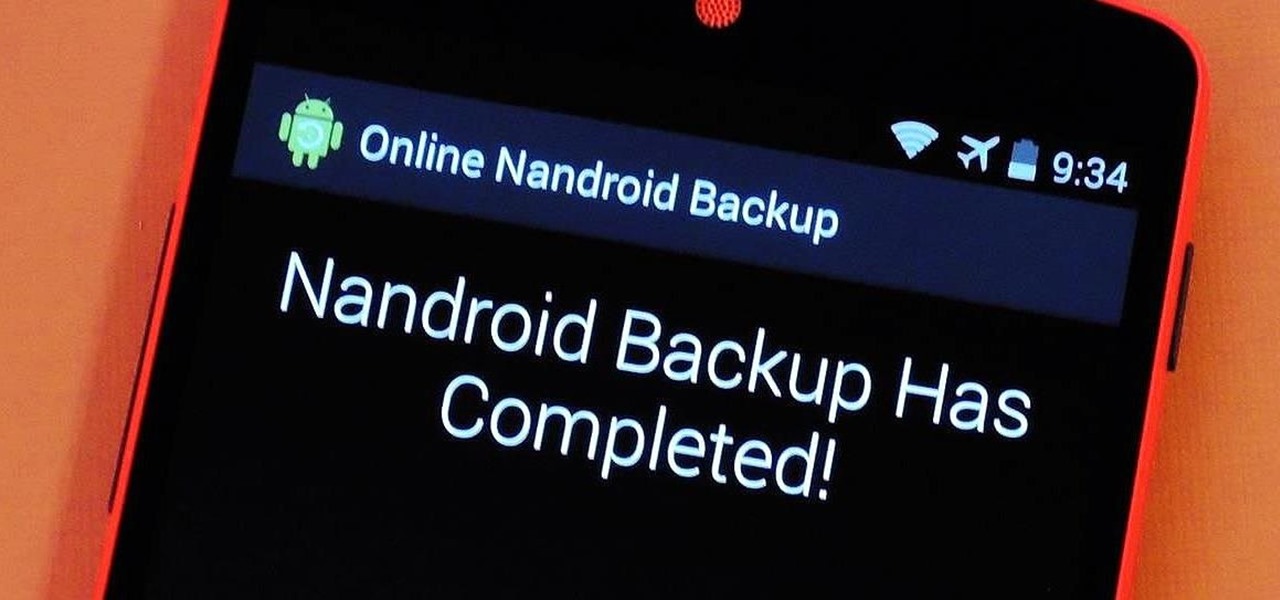
If you have a custom recovery installed on your Android device, the first thing you should have done as soon as you finished installing it was to create a Nandroid backup. But if you didn't, I'm not here to judge—I'm here to show you a much easier way.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

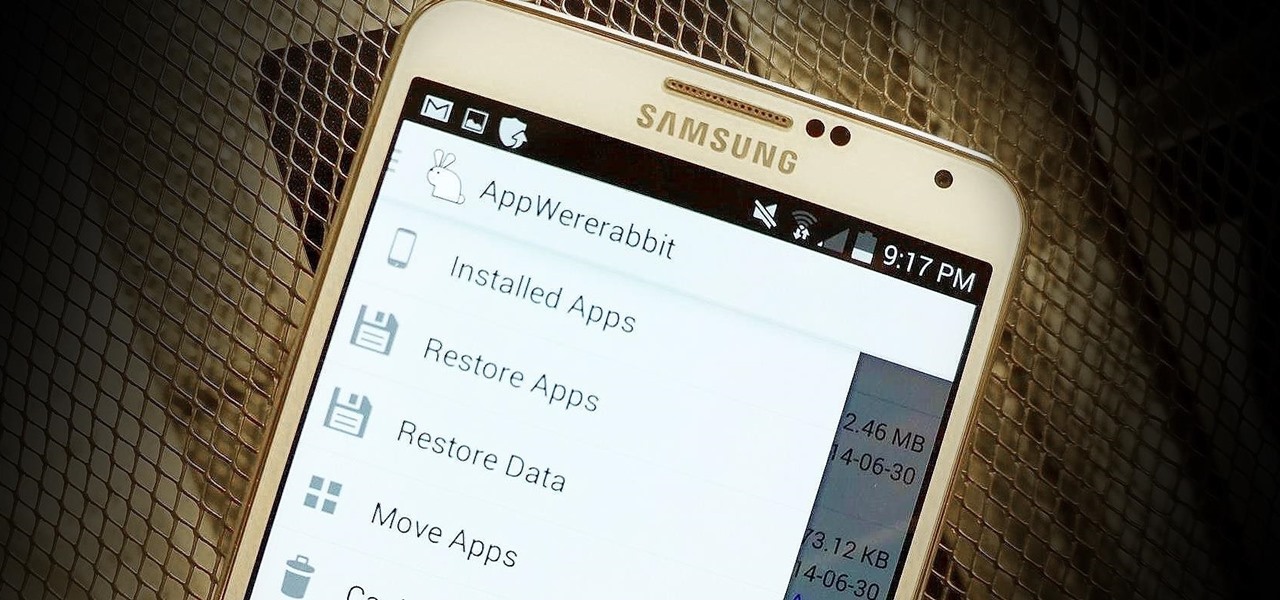
There are over 60-something Android apps cluttering my app drawer. While I'm constantly on the look out for new mods and apps to install, the default way of managing them is cumbersome and just feels unintuitive. I mean, who on Earth would wants to individually manage each app on their device?

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

The Nexus 5 has a known issue with its display. Affecting all models from the first manufacturing run and most models thereafter, this display issue is easiest to notice on something with a white background. A yellowish tint, most noticeable when compared to other devices, seems to emanate from the Nexus 5's screen.

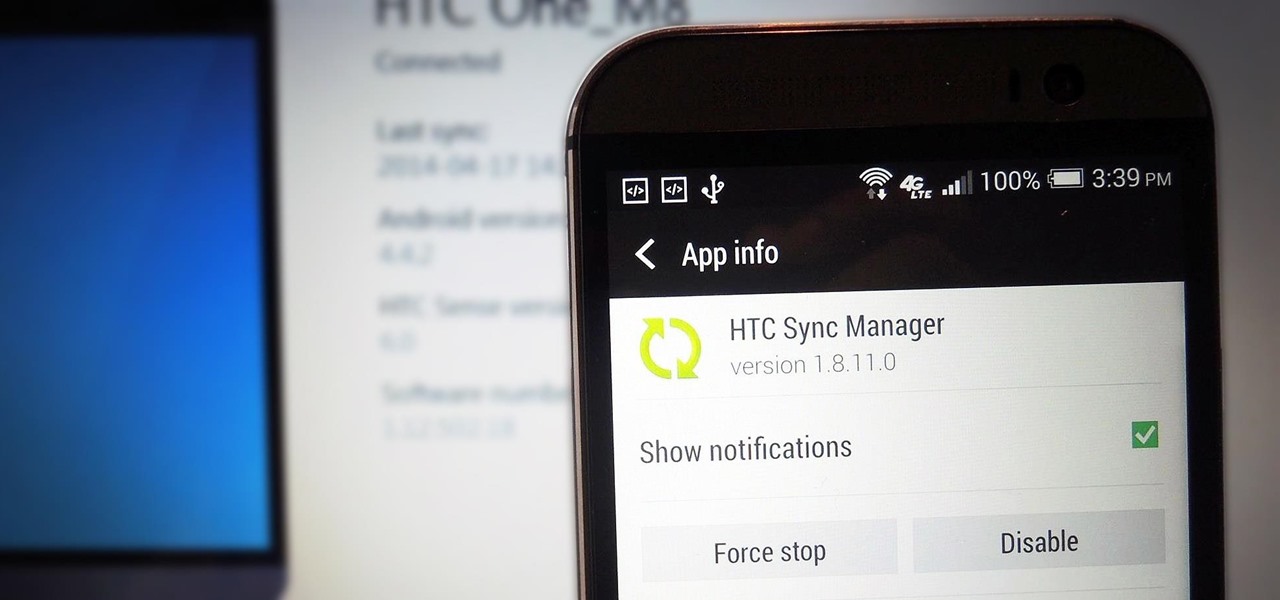
If you've just upgraded to an HTC One M8, chances are you've got some media files you want transferred over from your computer or previous phone. Even after you've done that, there will be times when you want to transfer content back to your computer for safe keeping.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

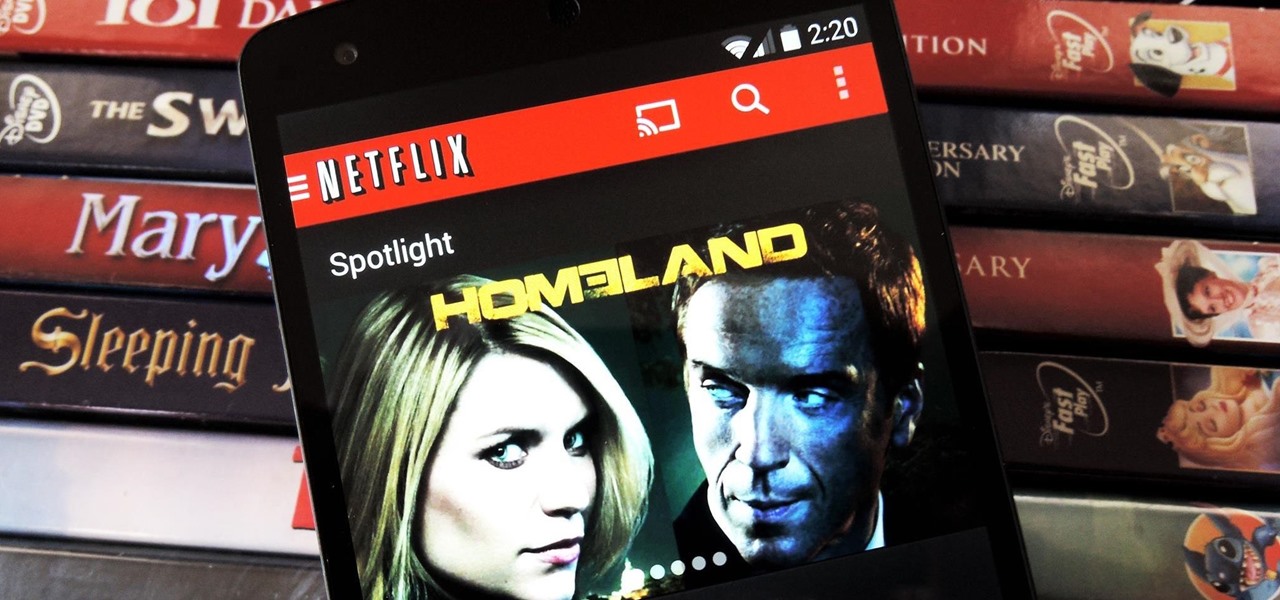
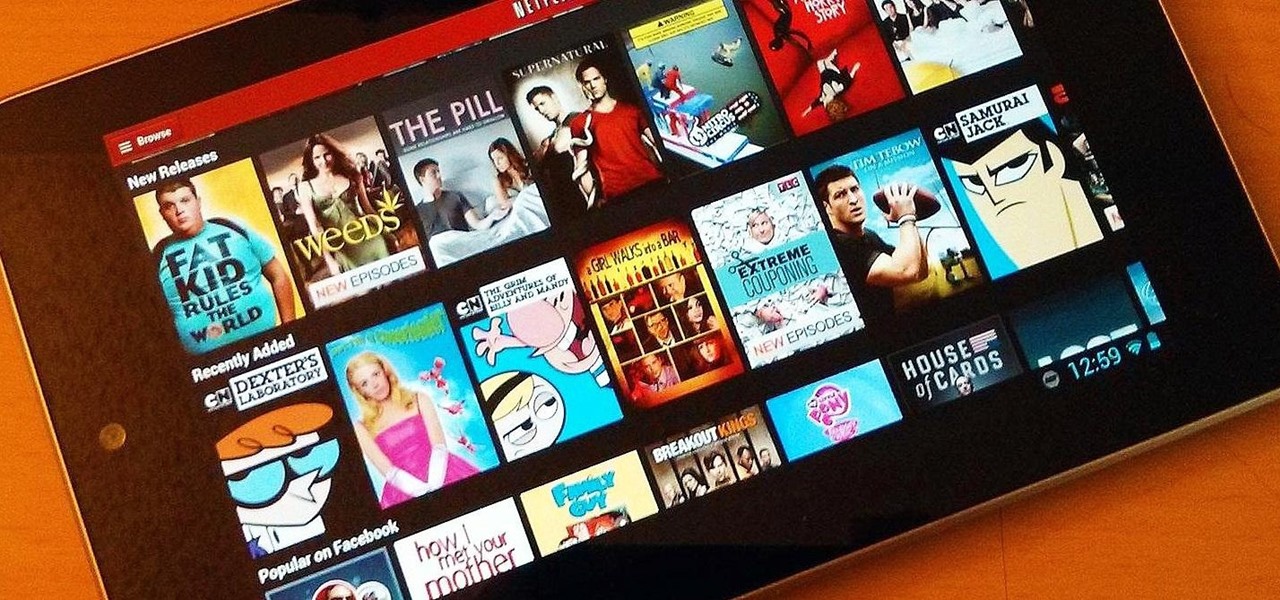
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

The new Google Now Launcher has hotword detection and one-swipe access to Google Now, but personally, it's not enough to convert me away from other launchers like Apex or Nova. Just because it's Google's official launcher for stock Android doesn't make it better than all the rest.

Pretty soon, every restaurant and store you walk into will know exactly what you're doing. Retail analytics companies like Euclid, ShopperTrak, RetailNext, and Prism Skylabs have penetrated hundreds of food shops and retail stores across the country, installing sensors that track and log customers' moves while they dine and shop.

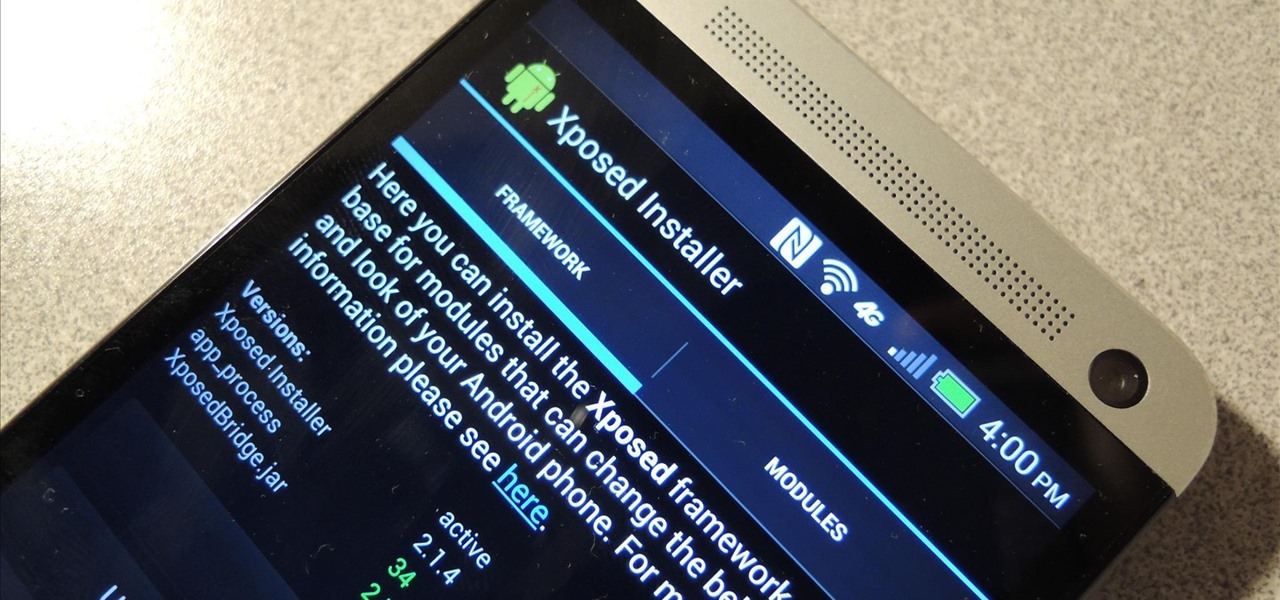
Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!

If you don't want to wait for Android 4.3 Jelly Bean to hit your HTC One, you don't have to. Android developer LlabTooFeR released his MaximusHD ROM, which includes a leaked copy of HTC's own 4.3 update, complete with Sense 5.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

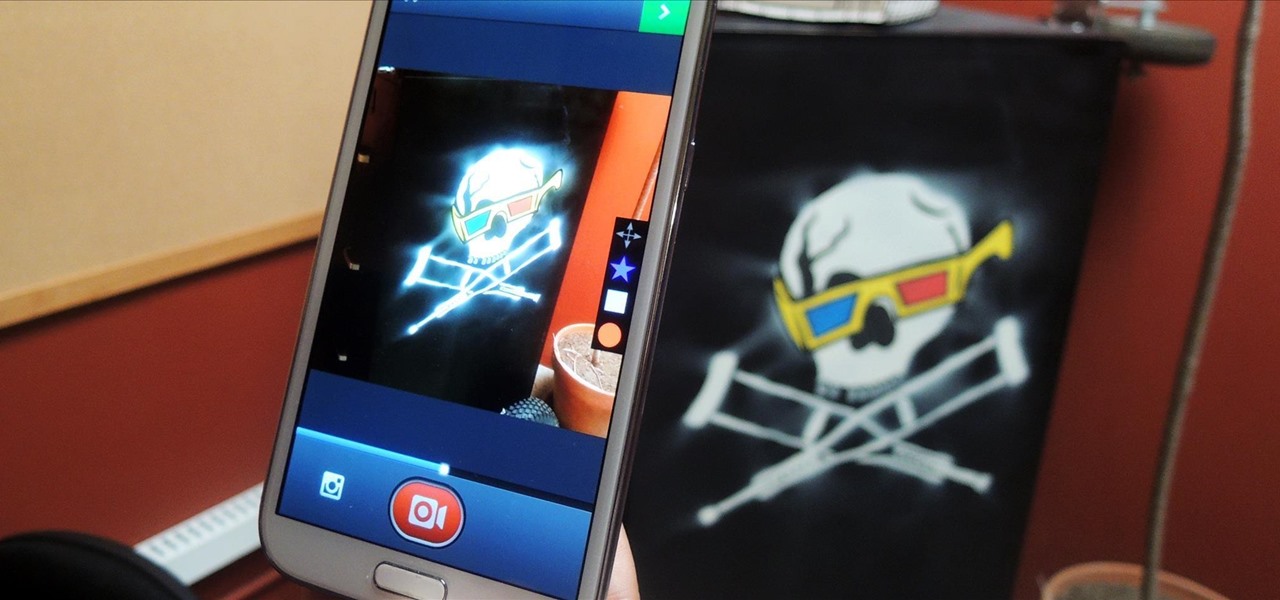
With the introduction of Vine and the subsequent Instagram update, abbreviated video sharing has come to the masses, to be experimented with in an unprecedented way.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Ever use Nexflix and YouTube on Your Nexus 7 tablet? It sucks! The menus are too big and not enough videos are shown on the screen. What gives?!?

If you're an avid PC gamer, then you're probably well familiar with the term overclocking, which is basically just tweaking your computer hardware to run faster than it was originally intended.

You may or may not have heard the term "greebles" or "kit-bashing" before, but if not, they may sound like nonsense. Particularly 'greebles', which sounds more like the name of a small, gremlin-like creature. However, I assure you that they are very important in prop-making, and if you can master them both, you'll be able to make intricate, great-looking props in hardly any time!

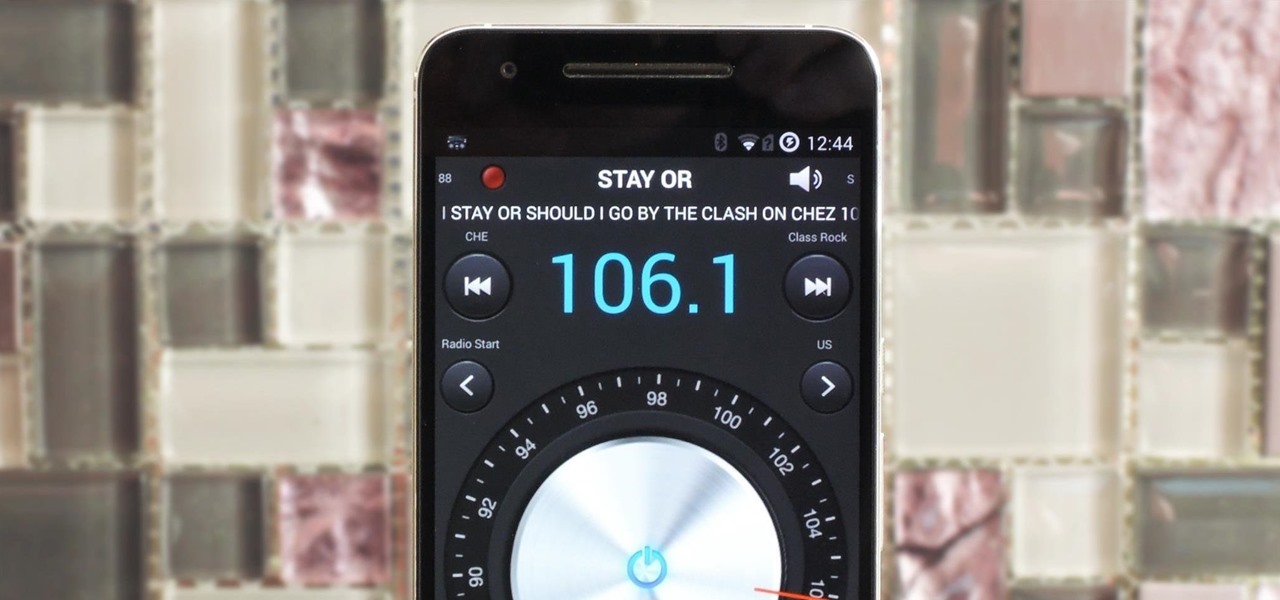
Android smartphones have all sorts of connectivity chips built in, including Bluetooth, Wi-Fi, GPS, NFC, and mobile data. But what about AM or FM radio, two of the most common methods of wireless communication?

In this how to video, you will learn how to convert DVD movies to AVI or any other type of file for free. First, you will need to download DVDx 2.1 and the install it. Next, open the program and insert the DVD disc you want to copy. Go to file and click DVD root. Find the video and select the video_ts folder. You will see the IFO files. Look for the one with the longest time. Click on this one and press select. If you have a DVD already ripped on your hard drive go to file and click open IFO....

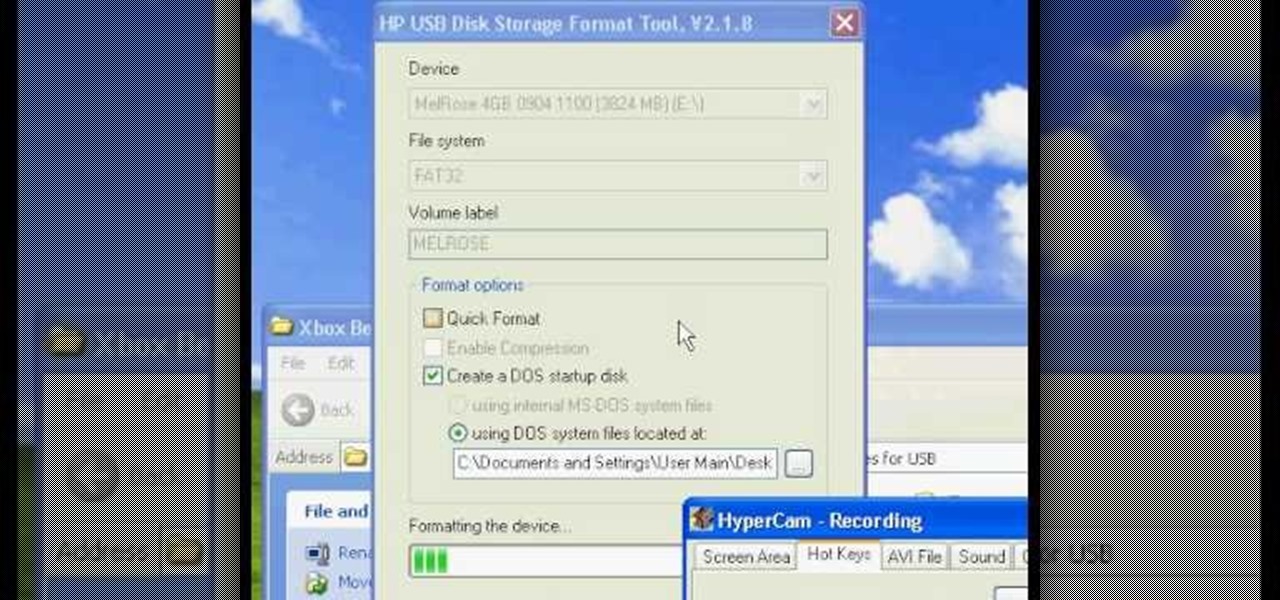
Have you ever wondered how to prepare a USB drive to flash an Xbox 360? Here is the how-to -video on how to create an USB drive for flashing your Xbox 360 benq drive. To make a bootable flash drive and to prepare it to flash XBox benq drive you have to download the “Xbox benq flashing files for USB” folder from the below mentioned link.http://www.MegaShare.com/1721713

iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...

Start with a totally bare eyelid to create the base for the winged eye. It's important to go for a gel eyeliner. This allows you more precision than liquid eyeliners. Pull the skin taut at the outer eye, look down & using a flat brush, apply liner into lash line itself on top eyelid, in between root of lashes. Taking the line from the inner corner of the eye, put color in lash line all the way to outer corner of eye. Close eye; pull lid towards ear so skin is taut. Repeat base step; this time...

This rich soup – served cold – combines leeks and potatoes to create a culinary treat for your tastebuds.

You're standing right in front of us, but your voice sounds like it's coming from over there! Color your friends impressed by learning the fine art of ventriloquism.

Sure, they have personal trainers and chefs to help them shed their postpartum pounds. But here are a few of their other secret weapons.

To grow beautiful flowers and plants in an outdoor garden, you need to feed your soil the right plant food – a fertilizer that will help your plants thrive. Watch this video to learn how to choose plant fertilizer.

Watch this video tutorial to learn how to color your hair at home. You'll save a bundle using a coloring kit instead of heading to the salon every six weeks. Plus, dyeing your tresses at home has never been simpler.