The top five apps of the 2010s were all social media apps of some kind, and the fact that's not surprising to you says a lot. We may use them for other reasons here and there, but our phones are social media machines at their cores. The thing is, some make better machines than others.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

Spam calls are one of the most annoying things to happen in the world of smartphones for more than one reason. Not only are they bothersome, but they can also be dangerous to people who don't know any better. Google has come up with a crafty solution known as "Call Screen" to let the Google Assistant handle the call for you while you listen in on the caller like a stealth ninja.

Apple has packed a lot of new features into the iOS 13 update, and practically no core app has gone untouched. The Messages app, in particular, got plenty of love, including new ways to dress and use your Memojis.

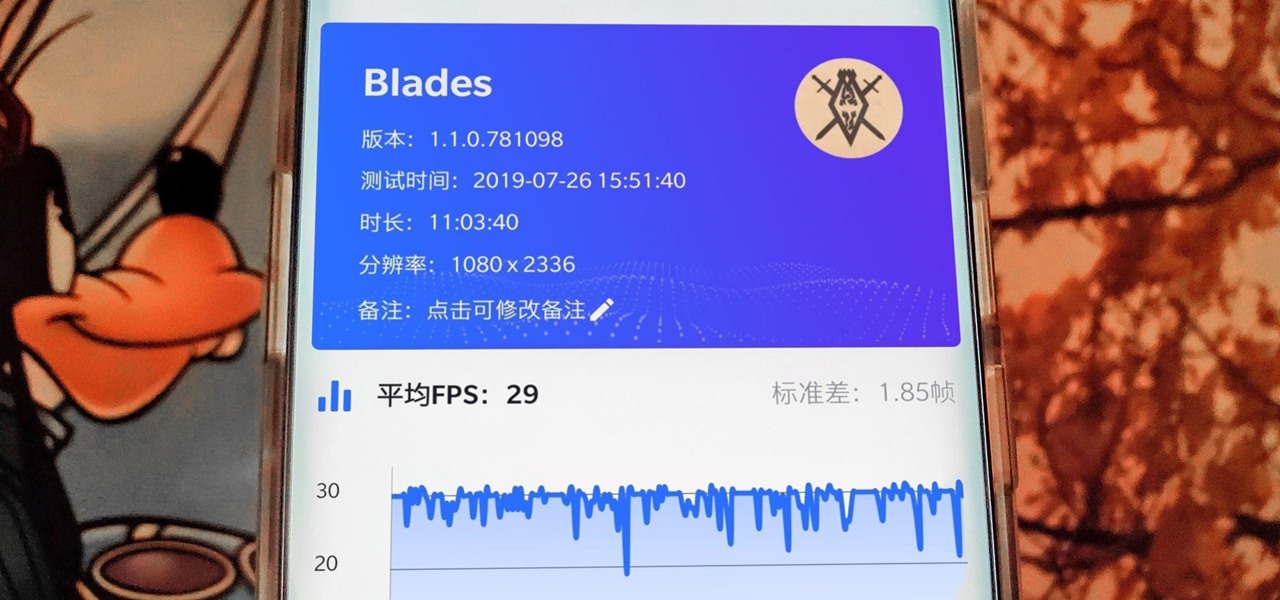
When you're gaming on your Android phone, does it sometimes feel "slow" and you can't figure out why? That means a drop in performance, which is when the frame rate dips, causing some noticeable stutters and lag. There's not really a way to know what's wrong unless you made the game yourself. But on the bright side, you can check any game's FPS with a simple tool.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

For those with small hands, smartphones have gotten out of control as of late. Nearly every flagship phone is over six inches in length, so many are forced to use phones that are too big for them and hope they don't fall. Well, thanks to one developer, using these phones can be a lot easier.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

If you have ever wanted to mod your Android device, your new best friend is easily going to be Team Win's TWRP custom recovery. This gives you access to file flashing on the fly, which can include such things as Magisk for root access, or even a custom ROM to replace the stock firmware that came with the device.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.

If you haven't heard, another big OEM has decided to drop the headphone jack. OnePlus, the hero of the people, has just announced that the OnePlus 6T will not have the popular port. With this decision, audiophiles and others are limited to just three big-name options.

All phones (yes, iPhones too) slow down over time. As your device gets bogged down by various apps and you begin to run out of storage, it's just an inevitability. That doesn't make it any less frustrating ... I mean, is there anything more annoying than a slow phone? My answer: No. Of course not. It's the single most annoying thing ever.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

On Wednesday, the tech world woke up to fairly shocking news with the announcement that AT&T would be the exclusive wireless carrier for the forthcoming Magic Leap One, as well as an investor in Magic Leap.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

Whether it's for your company, your professional image, or just your personal account, making a poll on Instagram is a great way to reach out to followers, friends, family, and other users to measure their thoughts and opinions about any given topic. Instagram for Android and iOS makes it fun and simple to do so, offering the same tools to professional and personal users alike.

TouchWiz might not be the Android skin of choice for hardcore aficionados, but the Galaxy's OS still has a ton of great features up its sleeve that help provide one of the most enjoyable smartphone experiences out there. Many of these are relatively hidden and overlooked features that you may not be aware of.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

The reveal of Magic Leap One: Creator Edition brought with it some insight into the path the device took from prototype to "final" design.

Whether you're new to Android or you just haven't kept up on the app scene lately, we hand-picked over one hundred essential apps that are all designed to improve your experience. From custom launchers and icon packs to weather apps and file explorers, there's something for everyone in this list.

There are a lot of Android phones out there, and chances are that someone in your life is looking for one this holiday season. Well, there also happens to be a lot of Black Friday deals on Android phones this year. So we've rounded up the best deals taking place on Black Friday weekend to help you save big.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

The Pixel 2 is a solid upgrade when compared to the 2016 model, but we've reached a point where the latest generation of a smartphone is never leaps and bounds better than the last. It's hard to justify dropping nearly a grand on a phone when it doesn't improve your situation much — especially when a few software tweaks will give you most of the upgrade for free.

So you spent all day customizing your phone. You tinkered with all the settings, searched the web high and low for the perfect wallpaper, and found an ideal icon pack to complement the color scheme. You go to sleep, proud of the work you accomplished when the unspeakable happens — your phone freezes and tech support is telling you to do a factory reset to fix the problem.

On June 11, 2016, an Arizona woman died from what appeared to be several infections, including pneumonia. She likely caught at least one of these from her dog.

Type 1 diabetes is an attack on the body by the immune system — the body produces antibodies that attack insulin-secreting cells in the pancreas. Doctors often diagnose this type of diabetes in childhood and early adulthood. The trigger that causes the body to attack itself has been elusive; but many research studies have suggested viruses could be the root. The latest links that viruses that live in our intestines may yield clues as to which children might develop type 1 diabetes.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

That soil under your feet is not just dirt. It is teeming with life that may not change as fast as we would like when challenged by global warming.

Food is both a necessity and a joy. Many people enjoy exploring, cooking, eating, and learning about foods from around the world. But the picture isn't always rosy. A new report from the Centers for Disease Control and Prevention (CDC), highlights the ways and whereabouts of food that make us sick.

There's no debating that the Galaxy S8 and S8+ are top contenders for the most beautifully designed handsets of 2017, but the same can't be said for their TouchWiz interface, which has been met with lukewarm reception at best.

Being a city dweller does not mean you cannot save the planet — or your food scraps. Climate change and resource management are big issues. Composting in any size space is not only possible, but it gives you a chance to reduce greenhouse gasses and reuse food scraps. Right now, about 40% of all food in the US goes to the landfill. In addition to planning meals and using your food in creative ways to reduce the amount that goes to waste, you can compost.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

The OnePlus 5 just made its official debut, so we now have all of the juicy details. From the announcement, this device definitely sounds like it's going to be another flagship killer, following in the footsteps of its predecessors.