
How To: Revive a dying plant
Don't throw out your wilting plants! There's a chance you can bring it back from the dead. Your wilting plant can be spared and revitalized with a little help & these easy steps.


Don't throw out your wilting plants! There's a chance you can bring it back from the dead. Your wilting plant can be spared and revitalized with a little help & these easy steps.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

Pythagoras was a smart man, so smart that his mathematical theory is named after him and still used today, more than 2,000 years later: the Pythagorean theorem. It implies that the square of the hypotenuse of a right triangle is equal to the sum of the squares of the other two sides. The Pythagorean theorem is a cornerstone of geometry. Here’s how to use it.
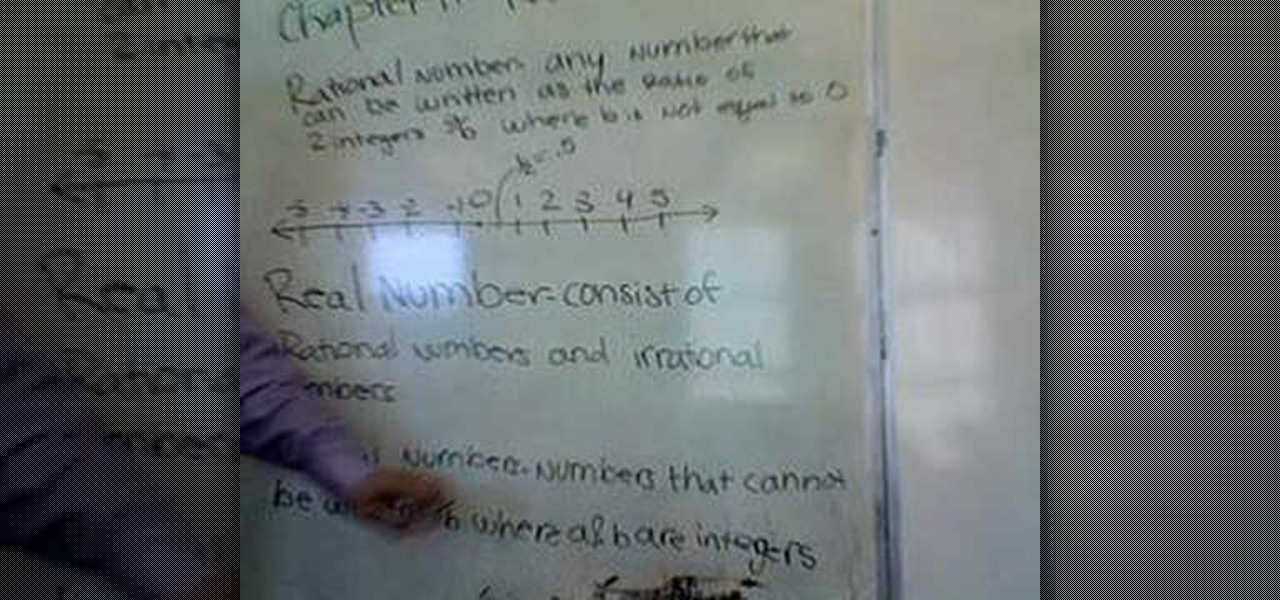
In this video the instructor explains the concepts of rational and irrational numbers. Multiplying a number by itself gives the value of its square. If you apply the square root to that squared number it returns to you the original number. This square root is also called a radical. A square root of a positive number can have two values. For example the square root of 81 is either 9 or -9; this is because when you multiply 9 with itself the square is 81 and even when you multiply -9 with itsel...

Concoct soda at home—over time, you'll save a bundle by not using the store-bought stuff. Plus, it's fizzy fun!

Are you obsessed with bobs now after watching bombshell actress Olivia Wilde donning one (albiet it was a wig) in the futuristic action film "Tron"? If you're serious about taking the plunge into short hairhood, then check out this video for your introduction to cutting and styling an A-line bob.

In this video xylophone lesson for aspiring mallet percussionists, we learn how to play a two-chord ostinato on the xylophone using three mallets. The chord progression is a simple one, commonly heard in popular music. It moves from the root or tonic (I) to the subdominant (IV) to the dominant (V).

Interested to know why certain people experience seizures? In this brief health-minded video tutorial from ICYou, we learn about seizures and their basic etiology. For details, and to get started learning more about the root causes of seizures yourself, take a look.
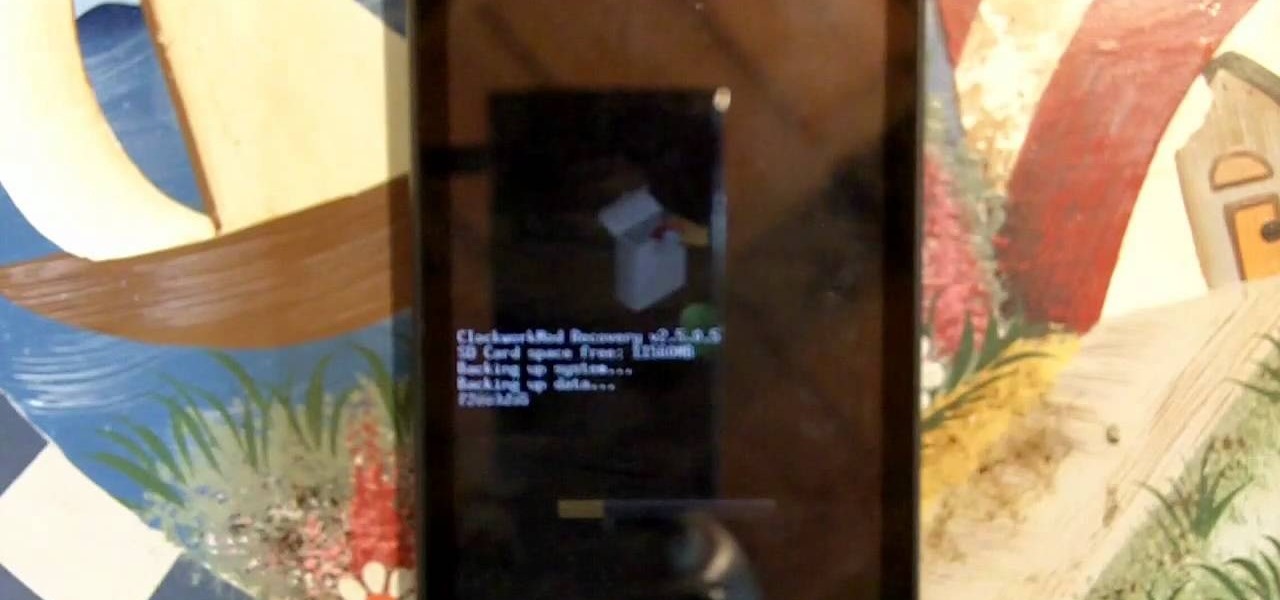
First, you'll need to download the Bootstrap application from the market (it costs about two dollars). You'll also need a phone with root access. Then, once it's installed on your phone, you can use to set up the custom recovery features!
Favicons are cute little icons which appear in the browser bar when your website is open. Having this icon adds a little extra branding to your website. You can create your own favicon in Photoshop using the right plugin, and then save it into the root of your site.

Learn how to factor perfect square polynomials and how to solve equations using the square root property. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test).

When you are using Linux or Ubuntu, it is smart to back it up. This tutorial will show you how to use a program called Remastersys to clone and backup your Linux distribution including root, home, other partitions and all personal, custom configuration to a fully deployable, shareable, bootable live CD or DVD.

To SSH into an iPhone or iPod Touch, follow these steps: Download WinSCP 4.2.7 from:
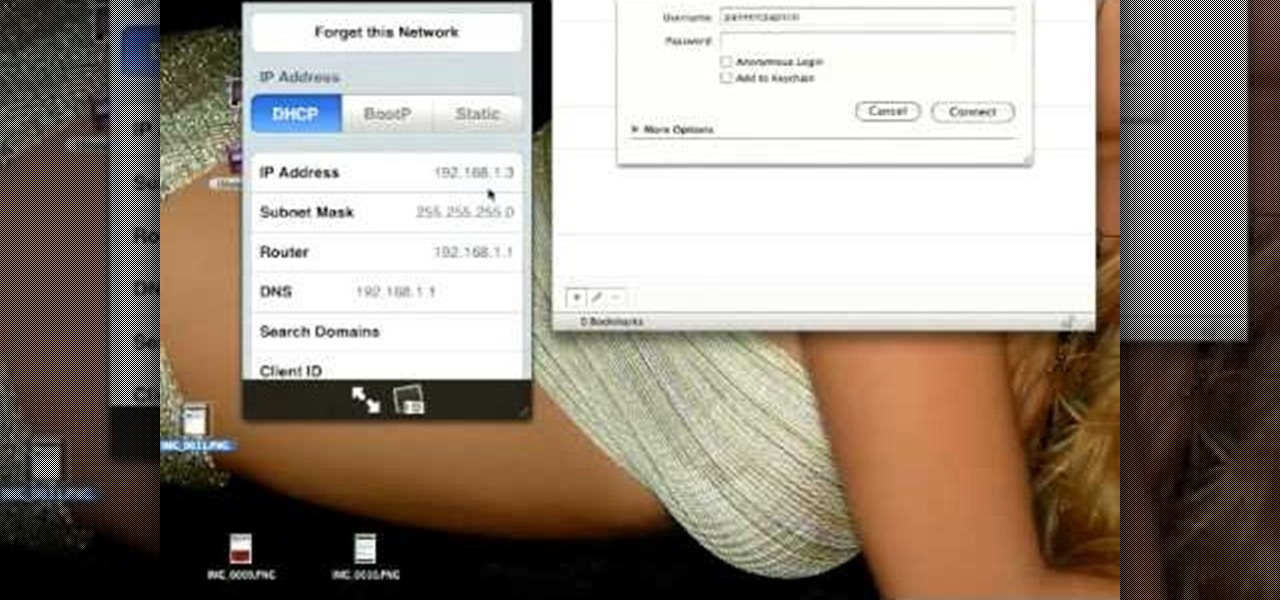
Curious about all those jailbreak videos and what they mean when they say "SSH into your phone"? In this video, learn how to SSH into either an iPhone, iPhone 3G, or an iPod Touch. Additionally, learn how to download videos from Cycorder on an iPhone and iPhone 3G with Cyberduck. Links & codes you will need:

For those who don't know, a gerund is a noun whose root word is formed from a verb. Anyone interested in brushing up on their grammar skills should view this video by Yossarian on how to diagram gerunds and gerund phrases. Yossarian uses various sentence examples to break down the subjects and verbs to find gerunds and gerund phrases. Learn how to break down the components of any sentence to find the gerund and gerund phrases by following this video tutorial.
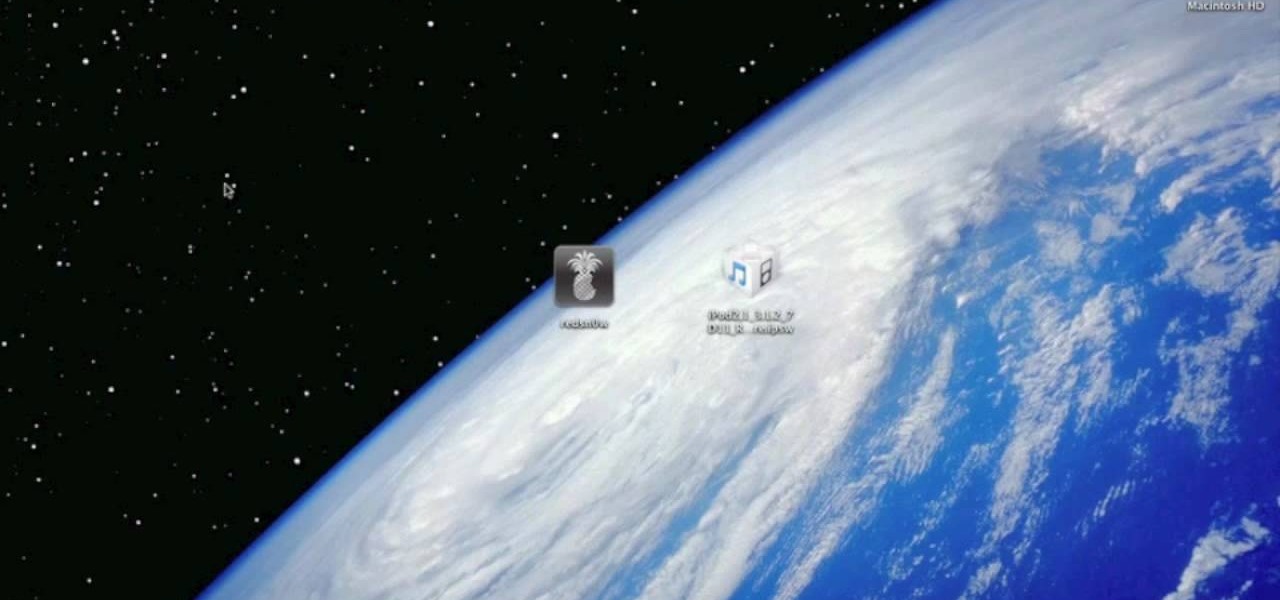
If you want to run homebrew apps on your second-generation iPod Touch or, as a moral issue, believe you should have root access to a computer that you yourself own, jailbreaking is the key. And this guide from Everything iPod Touch will show walk you through the jailbreaking process for a 2g iPod Touch running the 3.1.3 build of the firmware.

The Unlockr shows you how to root your Sprint HTC Hero. This quick jailbreak tutorial enables you to fully customize and optimize your phone. It also bypasses the phone carrier's restrictions.

This video tutorial will show you how to SSH file share on your Apple iPhone or iPod Touch, SSH meaning Secure Socket Shell. This is how you going to access your files on your iPhone or iPod, like videos and pictures. You will want to install the application OpenSSH in the system category on your device, and then download...

Drawing light-colored hair requires accenting the highlights with darker shadowed areas along the root line. Render light-colored hair in graphite with tips from a professional illustrator in this free instructional video on drawing. If your favorite cartoon character has light colored hair, then you need to know how to draw it!

What better way to learn how to mix a drink than from a hot girl! This bartending how-to video teaches a cocktail recipe for a Mad Hungarian. You will need spiced rum and root beer. Follow along with this video mixology lesson and find out how to make a Mad Hungarian cocktail. Get your (alcoholic) drink on.
Take a look at this instructional video and learn how to install the Twilight hack for you Wii. The twilight hack is an exploit that reads a elf file off the root of your secure digital (SD) card. To start up this hack, you'll need to load the Zelda: Twilight Princess game before you can run any unofficial software.

It only takes one day to feel the results from this amazing easy to make raw organic blended breakfast. What this how to video to learn how to make a raw breakfast of champions. All you need for this raw breakfast drink is: pear, apple, lemon, ginger root, and kale.

The subtle spicy peppery-ness of the aromatic ginger root marries beautifully with the gin, cranberry and orange flavors in this delightful cocktail. You will need ginger, lemon juice, gin, triple sec orange liqueur, and cranberry juice. Watch this video mixology tutorial and learn how to make a ginger cosmo martini.

Watch this piano tutorial video to learn how to play triads and inversions along with fingering in the right hand and apply this knowledge to the first few bars of "Let It Be" by the Beatles. This lesson assumes that you have the knowledge to play and spell out every major and minor triad in root position. You'll be able to apply triads and inversions to anything, particularly the Beatles' "Let It Be," after you've watched this helpful how-to video.

Learn from Green Deane about duck potatoes, a wide-spread highly-esteemed root vegetable.

Learn from Green Deane about Spurge Nettle, a root that can be eaten all year round.
There has been an update with the NES emulator, so you have to put the ROMs in the /var/mobile/Media/ROMs/NES folder, and not the /var/root/Media/ROMs/NES folder.

Sadie Nardini teaches an arm balance sequence for any level to help you learn the foundation of all arm balances and then an advanced series of poses that branch off of the root.

Protecting a new or young tree by staking it enables it to grow the strong root system it needs to secure itself in the ground. We will showyou how to stake a tree.

Unless you're a high-schooler building a nuclear fusion reactor, the hardest part of a science investigatory project often is coming up with a good idea. You want it to be cool yet feasible, novel but still useful.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.
So, you want your terminal to be customized with awesome script every time you fire it up, huh?! Well, look no further because I am here to answer this calling!

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.
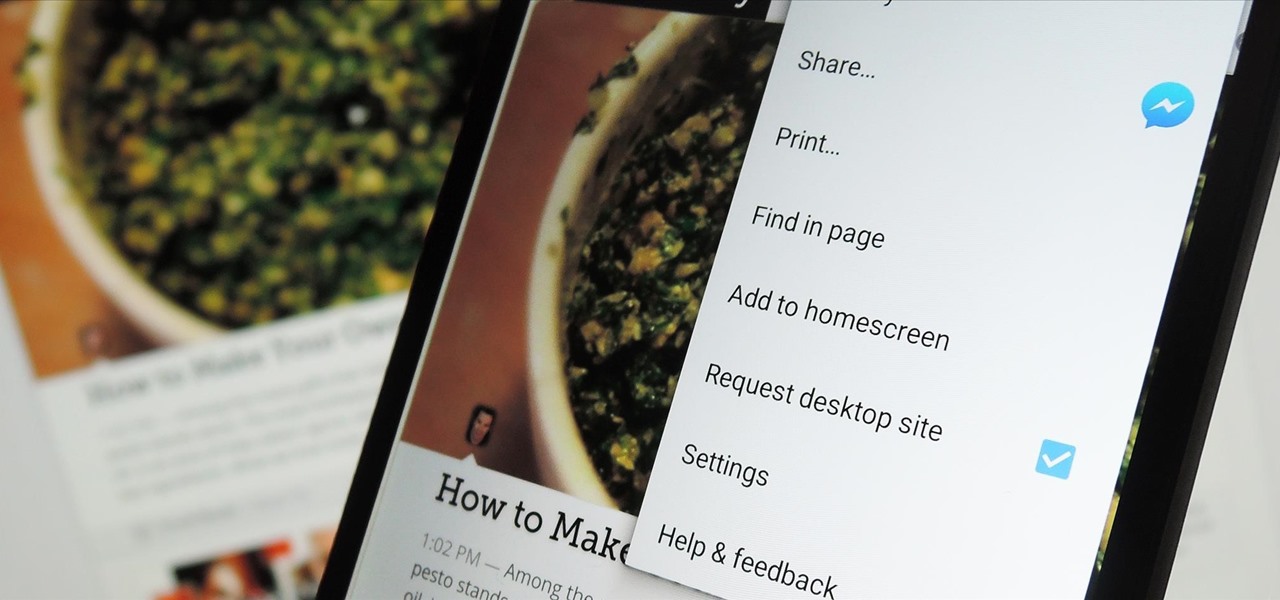
The majority of Android web browsers carry a "desktop mode" feature that makes mobile websites look like normal computer versions. Mobile versions are designed to work faster and more efficiently on smartphones, but sometimes the desktop version looks better on large displays or has additional features not included in the mobile one.

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

In this tutorial, we learn how to curl your hair perfectly with a flat iron. First, brush your hair out and then spray in some heat protector to all of it. From here, you will section your hair off into small sections and then heat up your iron. Now, clamp the iron to the root of the hair and then twist it 180 degrees. Slowly pull the iron down from the hair. The slower you pull the hair, the tighter the curl is going to be. When you release it, curl the hair with the finger and then move on....

In this video, we learn how to use a curling iron to curl your hair. First, blow dry your hair with a large round bristle brush to give it a lot of volume. Then, section your hair off into pieces and heat up your curling iron on medium. Then, put the iron into each section at the bottom and wrap it around into the root of the hair. Leave it in the hair for several seconds until the hair is hot, then release the hair from the iron. Let it out of the barrel slowly and the curl will stay togethe...

In this tutorial, we learn how to curl your hair with perfect curls using a flat iron. First, pull your hair up so you are just left with the bottom area of the hair. Next, take a small section and place the straightener into the top of the piece. Wrap the hair around the iron and then pull the iron straight down to the root. Repeat this for all of the sections of your hair, until you have curled all of the different pieces. Take the top section down and then curl that. From here, you will be...