Growing populations and higher temperatures put pressure on world food supplies. Naturally occurring soil bacteria may save crops in drought-stressed areas, put more land into crop production, and produce more food.
Now that Google Assistant is coming to all devices running Android Marshmallow or higher, roughly one out of every three Android users will no longer be able to access the old Google Now interface. The Assistant, which was previously exclusive to Pixel devices, takes over your home button long-press gesture and completely replaces all of the old Google voice search functionality.

KNOX is a major pain for Samsung owners who like to modify their devices. Its combination of hardware and software security measures make things rather difficult when you're trying to modify system-level files and functions without voiding your warranty.

The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?
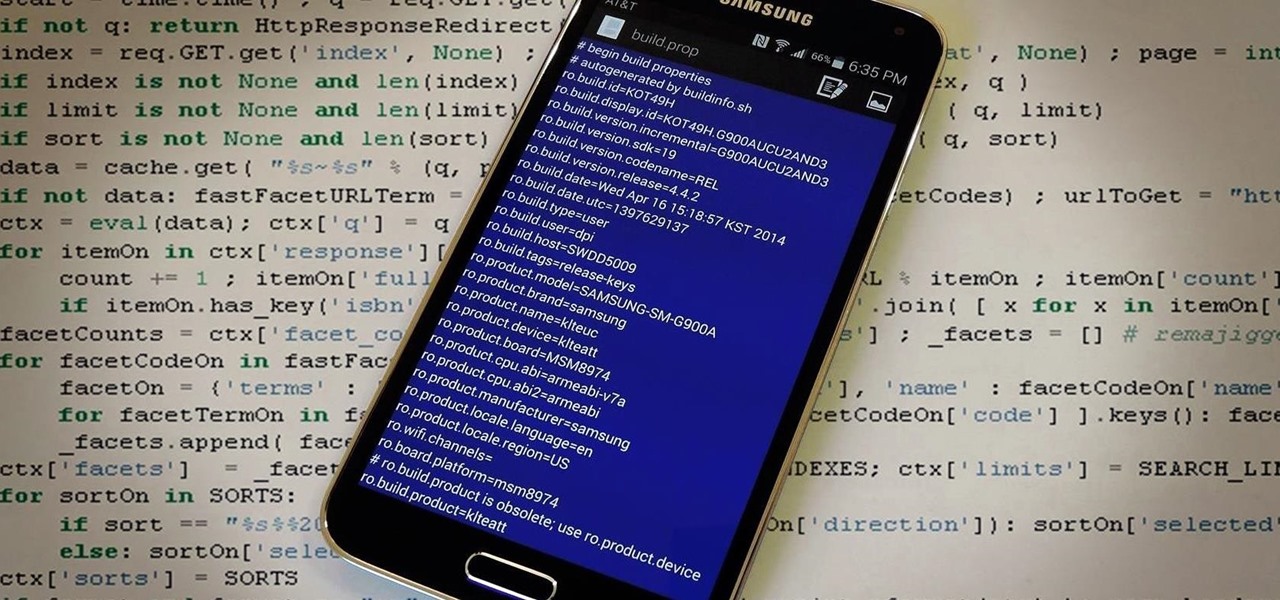
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Android has existed.

When the Samsung Galaxy S5 launched a few months ago, I was pretty envious of the new UI elements Samsung included on it, as I'm sure you were. The flatter interface provided for a more polished and less cartoony feel, bringing the device more in line with Google's design elements.

I'll give Samsung credit where it's due—the stock keyboard on the Galaxy S5 is actually pretty nice. There's a dedicated number row that resides at the top (something that the Google Keyboard needs a hack to achieve), and various settings exist to make switching between languages a breeze.

Google has finally announced the newest flavor of its mobile OS, Android L (Lollipop?), and I couldn't be more excited. While we won't see its official release until the fall, there are still some features we can get our hands on right now.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Forever Yours demonstrates how to get shiny, healthy straight hair that will last throughout the day using a hairdryer, round brush and a ceramic technology flat iron. Apply a heat protectant before beginning the process to protect the hair. Divide all hair into three equal layers, bottom, middle and top. Clip middle and top sections up high on head and begin by drying the bottom section. Dry the hair fully, divide hair into two sections and starting from one side, flat iron from root to end ...

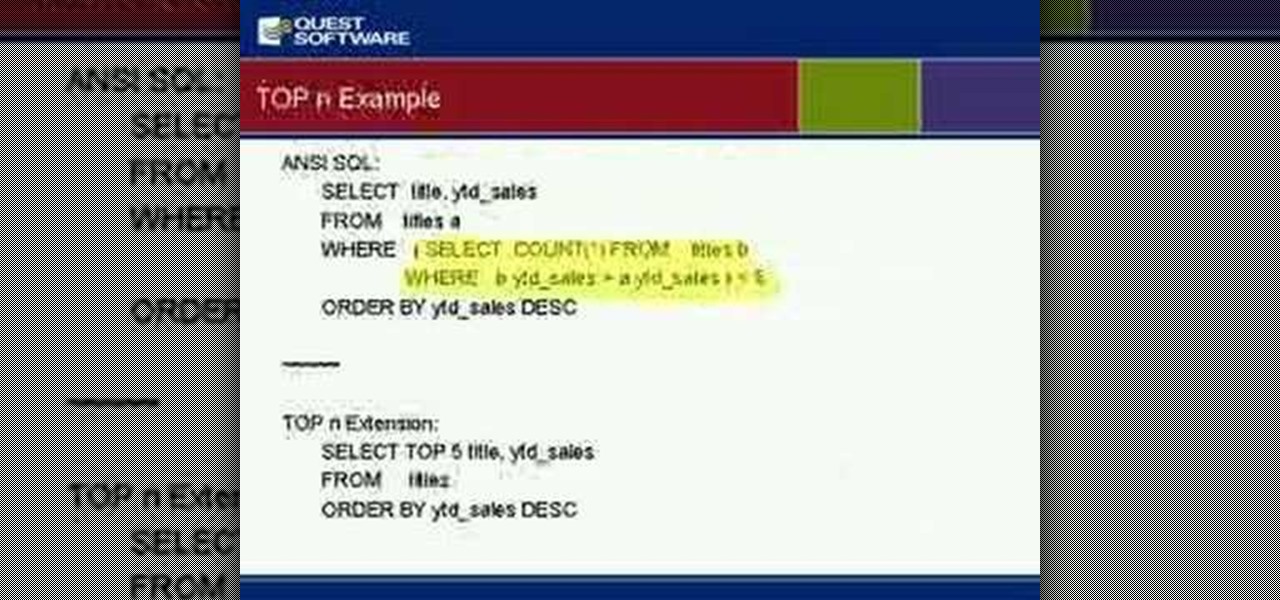
Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

After previously learning how to make the material of an object change with the focus of an object, we will build on that knowledge by adding new objects through code. We will accomplish this by creating our bounding box, which in the end is not actually a box, as you will see.

Most of us lead busy, work-filled lives, often clocking in a 9-to-5 five days a week. And when that clock signifies the hour to leave, the last thing on anyone's mind is: "Time to go to the grocery store to pick up more fresh produce!" (Well, to be fair... maybe more people are psyched about this, but I know with certainty that I am not one of them.)

Sense 6 came with a ton of new features for the HTC One, but for some reason, HTC decided to keep one of them hidden to all non-Harman Kardon editions.

Screen timeouts serve mostly as security measures and energy savers, but they can also interrupt you when you're reading a book or editing a document. There is no built-in way to manage screen timeouts on a per-app basis, but if you've got root access, you can do just that using Never Sleep from Android dev Hamzah Malik.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

OnePlus pulled out almost all the stops with their latest flagship, but there are a few areas where the phone falls just short of perfect. The single bottom-firing speaker leaves a lot to be desired, for instance, but thanks to the awesome development community for the OnePlus 6, you can already give your phone true stereo speakers with a software mod.

Google's Pixel phones have a feature that lets you swipe down on the fingerprint scanner to open your notification shade and Quick Settings panel. It's one of those features that make you wonder why it wasn't there in the first place, since it gives you another way to interact with your device, and your fingerprint scanner isn't being used while you're screen is on anyway.

Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using an Xposed module to modify the YouTube app itself and force it into not showing ads.

Samsung is known for its added features, but occasionally, these can cross the line between functionality and bloat. For many users, this is the case with the "S Finder" and "Quick connect" buttons that are hard-coded into the notification tray on most Galaxy S6 and S6 Edge variants.

Many of Google's stock Android apps are some of the best options out there—especially now that they've all been made over with Material Design. But generally, as these are pre-installed system apps, they cannot be used on non-Nexus devices.

Given how much use it gets on a daily basis, the power button is always one of the first hardware features to call it quits on an Android phone or tablet. So if your power button is acting up, or you don't want it to, you can extend its lifetime by simply finding ways to use it less.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

On-screen navigation buttons offer many distinct advantages over physical buttons—they can change orientation along with your device, they're capable of visually morphing to indicate secondary functionality, and the user experience is more consistent when buttons and app elements require the same amount of force to press. Add to that the fact that they're far less likely to fail and can be themed or even switched out altogether, and it's hard to come up with an argument in favor of physical b...

If you've ever attempted to report a bug to a developer, no doubt you've heard the response, "Get a logcat." This is infinitely important to a developer because of the fact that a logcat captures a full report of every command that was recently executed on your Android device, and it allows them to see exactly where something went wrong.

It wasn't too long ago that I showed you how to unlock the LG G3 bootloader and install TWRP, and while the process was extremely easy, the custom recovery can look a little intimidating to new users. Even long-time users who know how to navigate it find it boring to look at, as TWRP has had the same basic aesthetics since its creation.

With Geohot's Towelroot allowing us to root our Nexus devices in under a minute without ever leaving Android, many of you are probably enjoying all of the Gadget Hacks that root access has unlocked.

When we look back on it, 2014 may be remembered as the Summer of Android Wear. With two new flagship smartwatches due out soon, Google's been readying its mobile OS for the wearables sector.

SNAP. That's the sound of your Samsung Galaxy S3's camera going off. Not that big of deal, unless you're trying to take some top secret pics or some candid shots of your friends. The shutter sound gives you away, and the next thing you know, you're deleting pictures. On most other smartphones, if the users turns the phone on silent or vibrate, the shutter sound is killed. If that doesn't do the trick, usually muting the shutter sound itself in the settings will do the trick. But for some of y...

The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an understated advantage of the software is how dead-simple it is to modify with root-level tweaks.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.