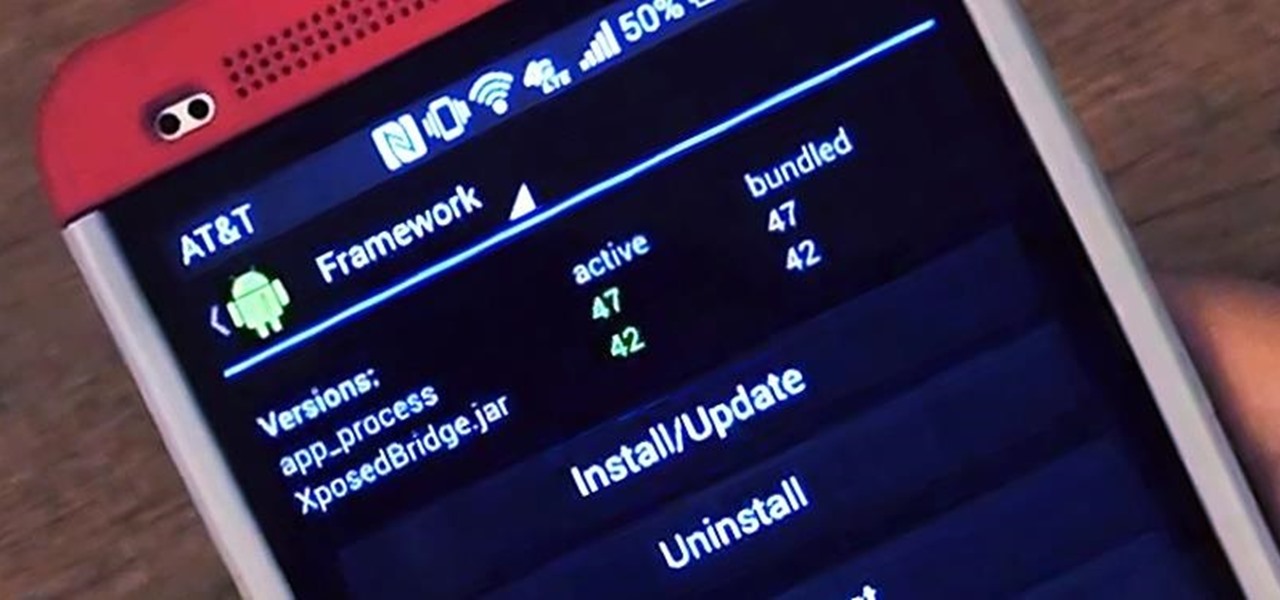
There are plenty of ways to customize your stock HTC One (or any Android device), from playing retro games to adding rotating live wallpapers. But to get the most out of your device, you need root access.
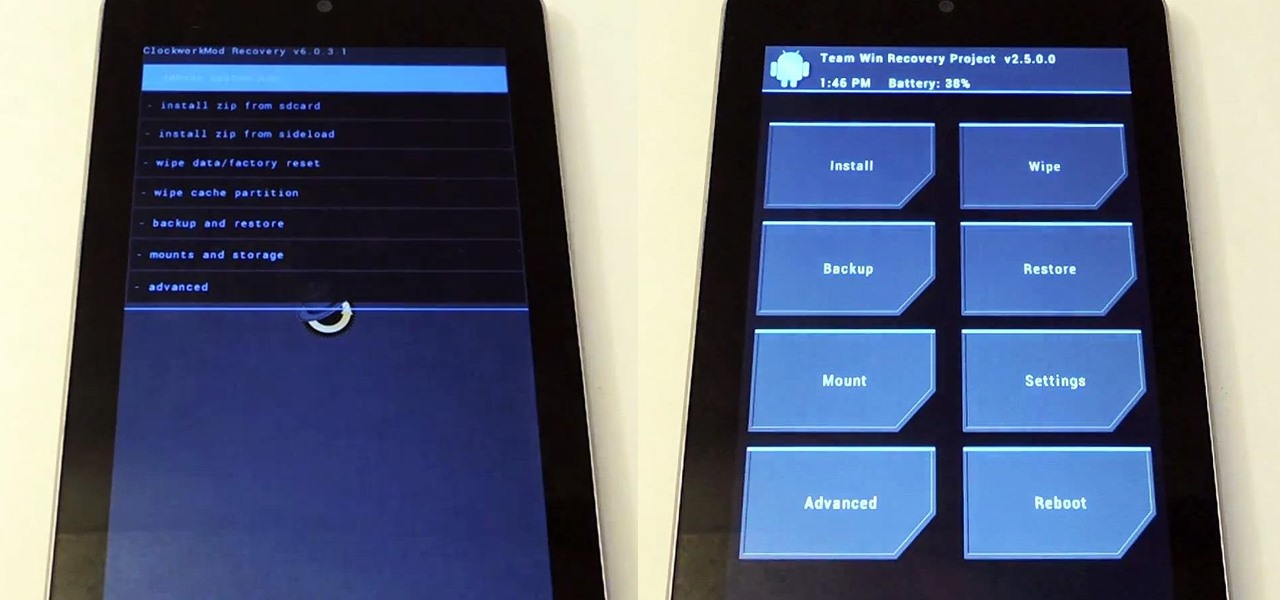
Android is constantly being refined, and the tools used to root and install custom recoveries are no exception. Earlier methods to root and install custom recoveries were very long and complicated. Any misstep along the way and you can end up with a bricked tablet.

Remember that PSP you had? I pretty much dropped mine when smartphones became more prevalent in the mobile gaming scene. Why would I want to carry around a huge PlayStation Portable when I've already got an Android in my pocket?

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

As we first reported here on Gadget Hacks, Google's new Pixel and Pixel XL smartphones come with an unlockable bootloader, with the exception of models sold by Verizon.

One of the biggest gripes I initially had with the LG G3 was the lack of options for the Shortcut keys, which are the volume keys that allow you to launch the camera or the QuickMemo+ app directly from the lock screen. I never use QuickMemo+, so having it as a shortcut was a complete waste of functionality.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

Windows 8 may have introduced a new, intuitive touch-based interface, but plenty of Microsoft loyalists were unhappy with the absence of the classic start menu that they were so accustomed to.

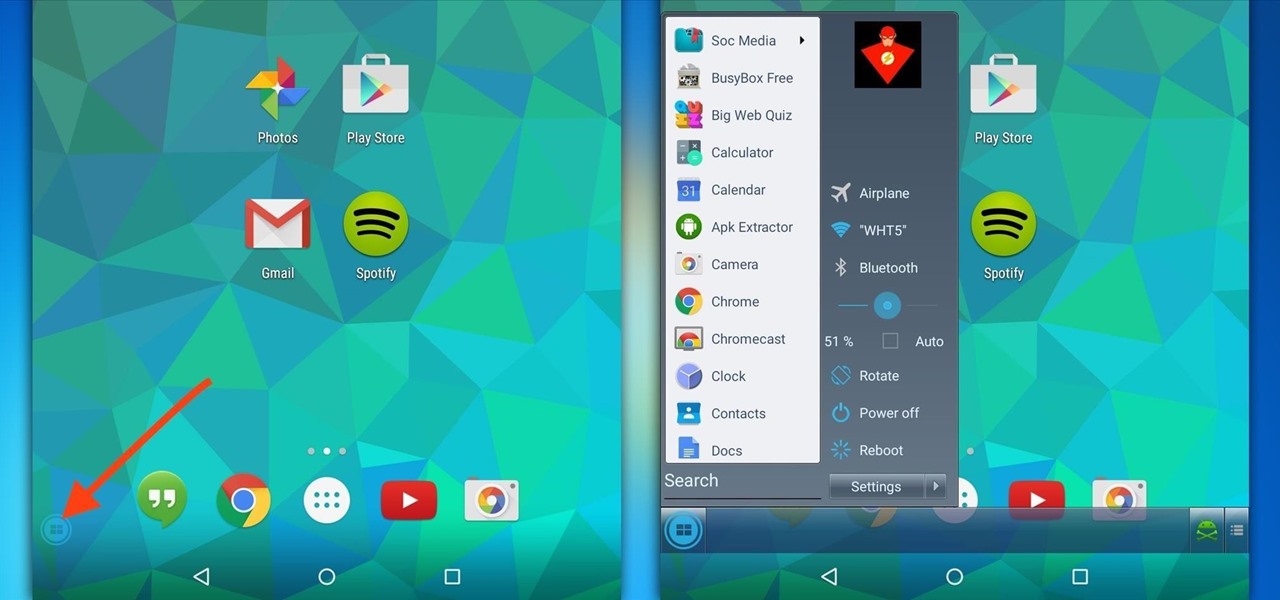
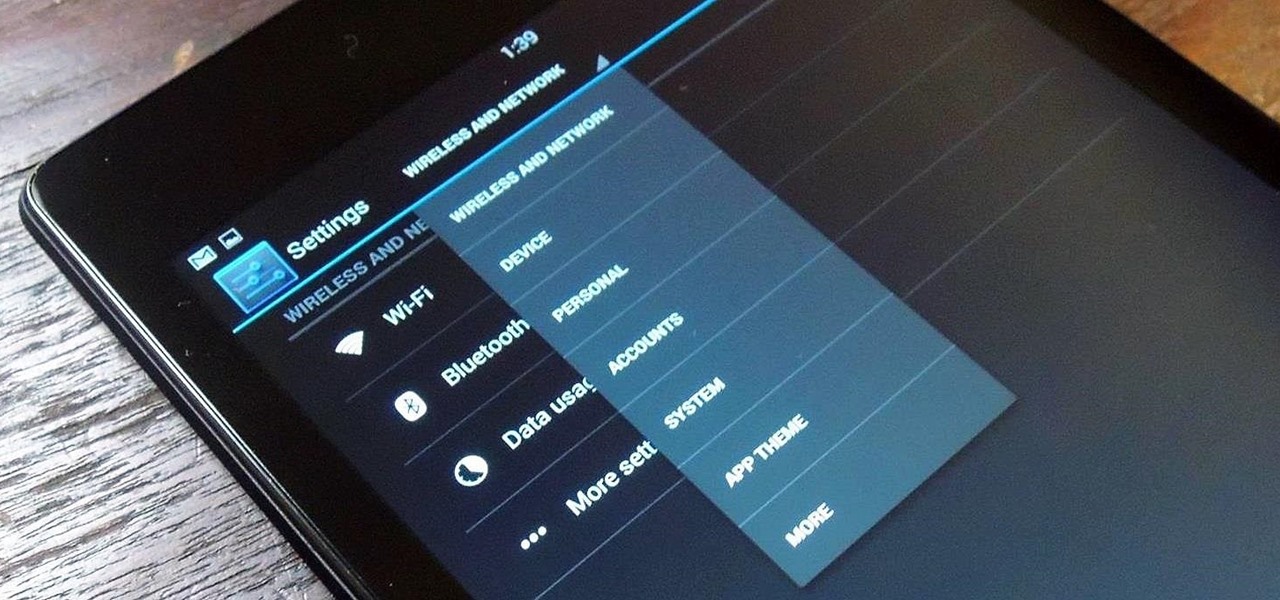
If you're someone who likes to customize their user experience, stock Android is a lot like a blank canvas. The firmware that comes preinstalled on Nexus devices is just Android—no manufacturer skins or carrier bloat involved. This simplicity opens up the door for many root mods and flashable ZIPs that can be installed in a custom recovery.

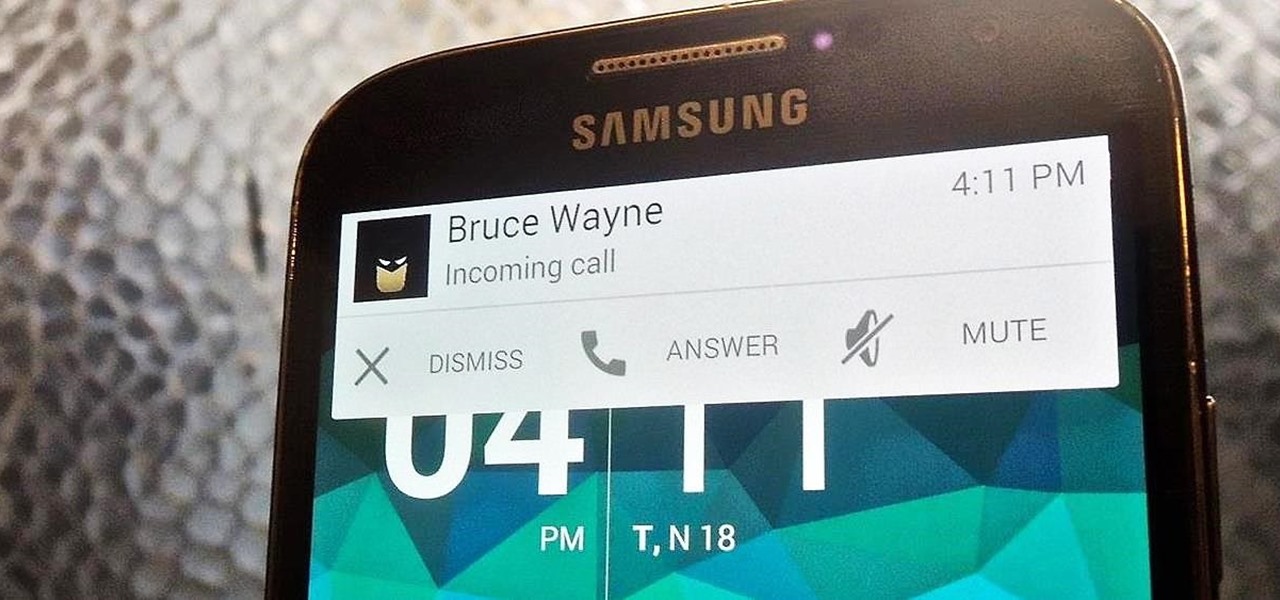
When playing a game or using an app, incoming call alerts can be extremely irritating on my Galaxy S4 because they insist on taking over the entire screen. The alert is a little different on other Android phones, depending on the manufacturer's skin, but all are fairly intrusive in one way or another.

Thanks to a recent back-end update to Google's Search app, every KitKat-running device can use "Okay, Google" from within any app—even the lock screen. However, the default settings for the OnePlus One's mic leave it unable to detect your voice unless you have it right up to your face. That isn't a good look for anyone, but thankfully there is an easy fix to get this working correctly.

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

According to a recent survey conducted by Edison Research and Statista, Pandora still has a firm grasp as the most popular music streaming service in the United States. With iHeartRadio, iTunes Radio, and even Spotify trailing behind by a large margin, it doesn't look like Pandora will lose their footing in the near future.

For the most part, Google Play Music makes it extremely easy to upload and organize your music library, as well as access it quickly using the default settings—but there are a few things it could do better.

It seems like most of the really cool and interesting modifications you can make to your Android device always require special root access, so when a fun mod comes along that doesn't require root—I feel it's my duty to alert you.

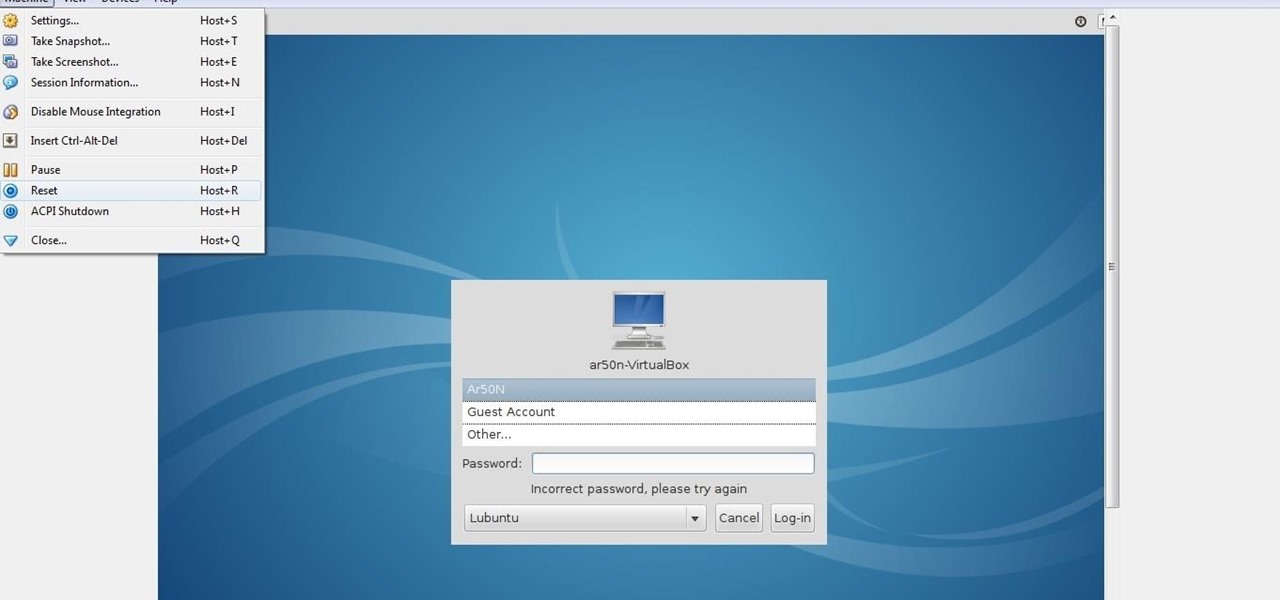
lubuntu is a is a lightweight Linux/Ubuntu that makes it suitable to virtual environments, that you run with VirtualBox to add a secondary machine to your computer or laptop. With this program you can run a number of operating systems upon the same platform.

The Samsung Galaxy S III is undoubtedly a great phone, but still has some minor issues to work out.

Playing advanced games on your phone can be pretty frustrating sometimes. Touchscreen devices are great for everyday apps and games designed solely for them, but when it comes to games that require multiple actions in conjunction with directional movement, it gets ugly.

There are loads of reasons for somebody to want to recover a Windows password, and there are lots of different ways of doing it. My favorite of all of these ways is to use a piece of software called Ophcrack because:

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

It seems like all tech companies want to know where we are. Even Apple and Google have been caught abusing their location access on iOS and Android. Luckily, there are apps that can trick your phone into thinking it's somewhere it's not.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

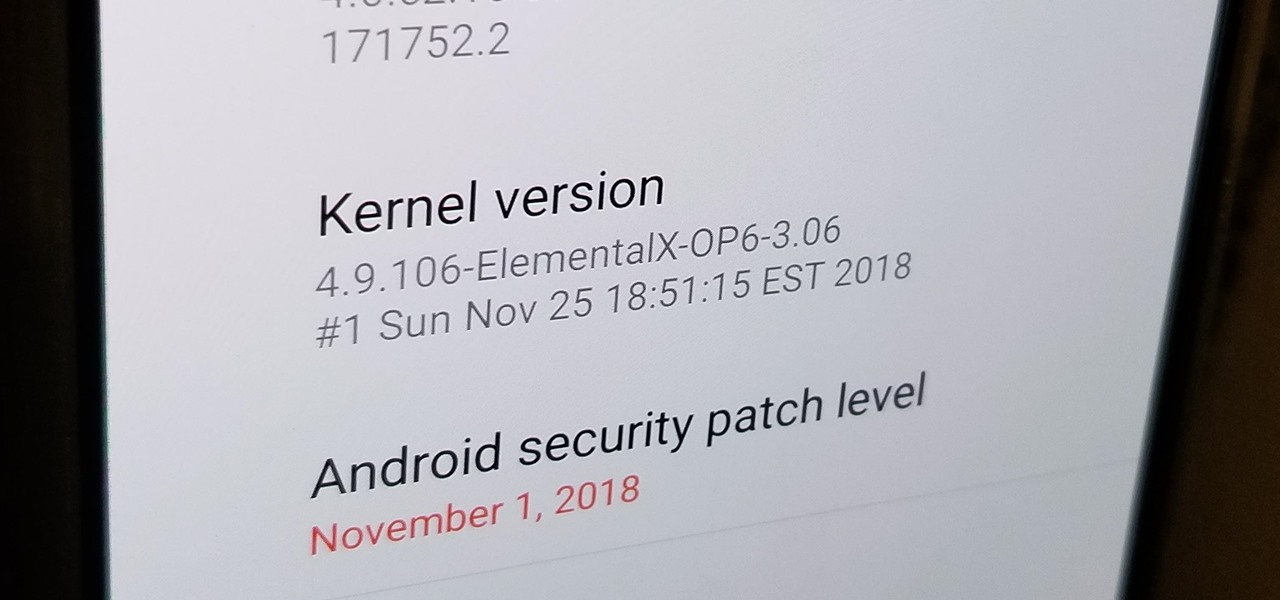
After you unlock the bootloader, install TWRP custom recovery, and flash Magisk to gain root access, what might be the next step of your modding adventure? A custom kernel, of course! Flashing a custom kernel onto your device gives you a whole new level of tweaks and customizations, and it allows you to have full control over how your system performs.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

To really personalize your HTC 10, you'll need to be rooted — but that can't happen unless you unlock your bootloader. Thankfully, HTC has made it relatively easy to unlock the bootloader on their 2016 flagship.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.

Paranoid Android has always been one of the most popular custom ROMs because of the inventive features its developers add to Android. Two of the biggest draws in particular have to be the "Halo" notification bubble, and the "Pie" navigation buttons, which can both fundamentally change the way you interact with your device.

One of the only downsides to the Pixel XL is that Google's flagship phone does not have stereo speakers. But if Android's awesome development community has taught us anything over the years, it's that limitations like these can be bypassed with some creative software tinkering.

A few months ago, LlabTooFeR leaked a full system dump from Google's then-unreleased Pixel and Pixel XL smartphones. That may not seem like a big deal at first glance, but the system dump contained all of the preinstalled apps and services from Google's new flagships—including the much-anticipated Google Assistant.

When we initially started juicing, we tended to gravitate towards the widely popular juice staples—carrots, cucumbers, celery, kale, spinach, and apples. However, as we grew more comfortable with these fruits and vegetables (and honestly, a bit bored), we realized there are other unsung juicing ingredients that are just as tasty and nutritious.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

I think we've all had that childhood (or adult) desire to have ice cream for dinner. But veggies for dessert? It's something I had nightmares about as a kid.