Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

The 13-megapixel camera on the OnePlus One is capable of taking some pretty impressive shots, but the stock CameraNext app doesn't do the hardware justice. When compared to the camera app that ships on the ColorOS version of the One, you can immediately see an increase in clarity and low light performance.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Google has already started to roll out the over-the-air update of Android 5.0 Lollipop to older Nexus series phones and tablets, but chances are it will take a long time for the OTA to hit your device.

The Spanish and Portuguese introduced many things (some desirable, some not, depending on your POV) to Mexico in the sixteenth century: Christianity, language, and lots of flora and fauna.

Sony has been hard at work refining its Xperia line of flagship phones. With a 6-month release cycle, they've managed to slim bezels, increase viewing angles, and boost processing power in the 1.5-year span between the original Xperia Z and the Z2.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

There are some ingredients I cook with so often I can never buy too many of them, and most of them are produce. Onions, garlic and fresh herbs are staples in a lot of dishes, and they may be inexpensive, but when you use them on a daily basis it can add up.

In the past, we've shown you how to install CyanogenMod 10.1 on your Nexus 7, but that version was based off of the older Android 4.2 Jelly Bean. If you want to stay current, the newer CyanogenMod 10.2 is out in the nightly stage, which is based on Android 4.3, and you can get it right now.

Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams.

An average of 140,000 hard drives crash in the United States each week, according to online backup service Mozy. Additionally, 70 percent of Americans have lost a laptop, smartphone, or tablet, and the average person now loses 1.24 devices each year—less than half of which are ever recovered.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

In this tutorial, we learn how to draw a realistic portrait. Using a pencil, you will first draw the out line of the face. After this, add in the details and bold lines to the eye. From here, you will add in the details and shading to the rest of the face. Use your eraser to create smooth lines and white lines to make the features look glossy. Draw in a white line on the bridge of the nose to make it look more realistic. Also make sure to add in lines that are on the face as well as hair that...

You can make a magic memory stick on your PSP in some very easy steps. So first thing you need to do is download the files. Now extract the dc8 file on your desktop and drag that 500.pbp file on your desktop. Now plug in your PSP in your computer and copy the dc8 folder and go to PSP, game in your PSP memory stick and past it there. Now copy the 500.pbp file and go to the root of your memory and paste it on there. Now in your PSP, run the files which is mentioned in the video and you are done.

In this tutorial, we learn how to make your hair look thicker. First, raise the top sections of your hair up and then spray hairspray on them. After this, slightly tease the hear at the root. When you are finished with the, continue on down to the bottom of your hair until you have teased all the sections. Now, let your hair go down and lightly brush it with your teasing comb. Spray another coat of hairspray on it, then continue to the other side. When you are finished, you will have hair tha...

In this video, we learn how to upload Wordpress files using Filezilla. Before you get started, you will need to know the host, username, and password for your domain name. After this, click the quick connect button to connect to your server. The left hand side will show the local files on your server. Look in the root directory of your server and right click, then choose "create directory". Now, click on the plus sign to see a blog sub directory. Next, find where you downloaded Wordpress onto...

In this video tutorial, viewers learn how to cut an onion without tearing up. This task is very easy, fast and simple to do. It is recommended that users use a large knife to cut the onion. Begin by peeling the skin off of the onion. Then cut off the bottom root in a circular cut to remove the bulb. This will prevent the onion from releasing the gases that cause eye tearing. Now finish by making vertical and horizontal slices to the onion. This video will benefit those viewers who enjoy cooki...

Have you ever wanted Pantene commercial hair? You know, those glamorous shampoo and conditioner ads showcasing beautiful women with beautiful hair so devoid of common hair woes like split ends, raggedy texture, and frizz that it almost looks fake? We've always lusted for hair that brilliant, but thought up until now that such perfection was only achievable through having a hairstylist on call 24/7. But not anymore.

The Survival Podcasting present how to handle leggy or spindly seedlings that have grown too fast. Potted swiss chard seedlings are used as examples. The seedlings are growing well but are a bit floppy or spindly. This happens because the warmth from being started indoors encouraged their fast growth but since there is not enough light for them, they started reaching for the light. A `head space` is developed between the root and the leaves that makes the seedling flop over. A simple trick to...

Blip TV user Mr. Root teaches you how to mount an ISO image file using the Unbent Linux terminal. To do this and have access to the files inside of an ISO, without unarchived it, start the terminal. Type in dirk CD. Make sure the ISO image is on your desktop. Then type in sud o mount -o loop -t iso9660 and then the name of your image file, followed by CD/. This will create a new disk drive, which can be seen on the desktop. You can explore that disc like a real one. To unmounted your image, s...

Linuxjournalonline teaches you how to use GRUB to dual-boot Linux and another operating system. You need to go to etc/default/grub and edit that file. Here you can configure the time it needs to start booting a system and what OS to boot. You need to be root to edit this configuration file. Don't forget to run update-grub to force an update of grub.cfg. And this is the end of the short process needed to configure Grub 2 for Linux.

The alluring beauty of Asian women is celebrated around the world. And they often look years younger than their true age. Ever wondered what the secret was to the gorgeous skin of Asian women? We’ve uncovered a few.

Check out this cool video and learn how to create the Allassonic effect with a coffee cup, instant coffee and boiling water. When the bottom of a ceramic cup filled with boiling water and a heap of instant coffee is tapped at regular intervals the pitch of the sound heard slowly increases over time.

This how to video is overview of the same mode played in different positions on the harmonica. As you can hear there are better positions for the tune "Help Me" than other positions. For example the C harp in 4th sounds the worst because of the unstable root. Even though this tune is traditionally played in 2nd position (cross harp) I prefer to play it on a G harp in 3rd position because I think it offers more sonic options due to it's naturally occurring Dorian mode.

Willow can be woven into many shapes or to form a living boundary fence. The reason they are called living is because some of the stems used to create the structure root in the soil and grow to form new shoots. This does mean that annual trimming is needed to maintain the shape, but at the same time it adds interest to the garden. Creating a living structure is very simple to do and all you need is a few pruning tools and a bundle of willow sticks in various thicknesses. With this tutorial yo...

In a three part series on how to blow harp through 12-bar blues changes, moving one particular riff--root, fifth, flat seventh, octave--up a fourth (for the IV chord) and a fifth (for the V chord). Gussow is using a D harp.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

It's nice having a dark theme on Android 10 and One UI 2, but setting it on a schedule takes it a step further. Imagine the light theme turning on every morning, and the dark theme taking over after sunset — all automatically. It sounds pretty simple, but it's one of those things you wouldn't know you need until you try it.

TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Hot on the heels of all the talk about Google's newest Android Q update, known as Android 10, there's a new beta to check out. OnePlus is one of the many partners that can now offer its users a chance to test the latest version early. That means you can install the newest Android Q beta right this second on your OnePlus 6, 6T, or 7 Pro just like Google's Pixel smartphones.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

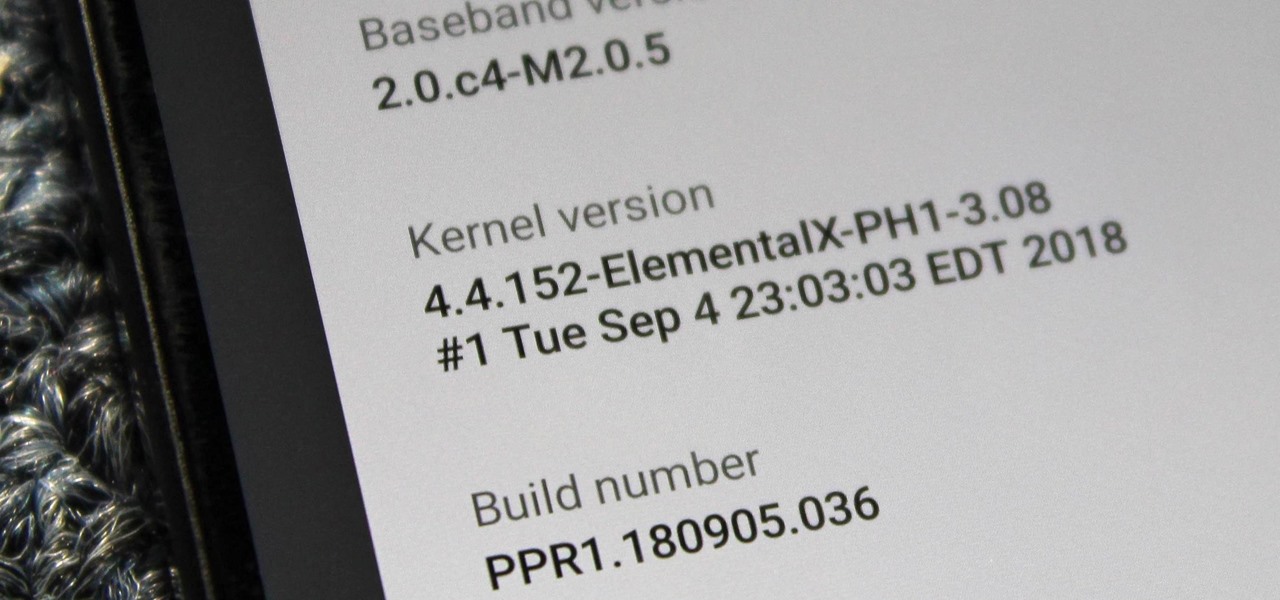
When you unlock the bootloader on your Essential PH-1, you open your device to a host of new possible tweaks. One popular modification is a custom kernel, which can not only speed up your phone, but give you new features that wouldn't be possible otherwise.