
How To: Make a Video Blog
Want to know how to start your own vlog? Starting a video blog is simple... Get a camera!


Want to know how to start your own vlog? Starting a video blog is simple... Get a camera!

Whether you're a student, a toastmaster, just writing, or making articles on WonderHowTo, you will have to come up with a topic. The topic should be able to guide you to some of the things you want people to know about. Here are some ways that you can can come up with a topic.

Polymer clay is an exciting arts & crafts medium. Actually, "clay" is a misnomer; it contains no true clay, but rather consists of tiny particles of polyvinyl chloride (PVC) combined with plasticizer, which is what makes it malleable like clay.

Pranks are fun, but finding a way to maximize the affect of a prank can be tricky. Toilet papering the whole campus or repainting all of the parking spaces slightly smaller can take a long time and a lot of resources. A better plan of attack is to booby trap the choke points where your victims are forced to pass through. Think like a guerrilla. A dorm doorway is a good idea.

If there ever was a time for Null Byte to need people to contribute, it's now. Let's make Null Byte a place where anyone, from novice to master computer user, come and learn. It has been sometime since the last "Call to Arms" for Null Byte, and even longer since the last "Weekend Homework". We all know that this time of year is busy for everyone, but that didn't stop occupytheweb otw from creating a great article in his continuing "Hack Like a Pro" series.

This past weekend's workshop on replacing normal levers with buttons masquerading as levers went really well. Lots of players showed up and everyone had a great time. Most importantly, everyone learned how to make and use a T flip-flop!

Only a few people turned out for last week's workshop on Saturday, but they were all interested in learning this technique for hiding secret stashes with ordinary blocks. After that was covered, we even went on to teach each other different designs afterward! It was a great learning experience for everyone who attended, so consider joining us next week!

Are you looking to hide your chests in a not-so-conspicuous way, but don't know where to start? Do you want to finally have that safe and sacred place to store your diamonds, cake and beloved treasures? This tutorial incorporates this previous week's challenge on transforming houses. If you weren't able to participate in last week's challenge, you will still be able to get a feel for what everyone did!

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Need help getting started on this week's WTFoto Challenge? Look no further! In this tutorial, I will teach you how to create simple chalk symbols and writing in Photoshop. So read through this post and try it out yourself—or I'll tell your cousin what you said when you were drunk that one time. Keep in mind that the steps are similar for other programs, such as GIMP.

So far, I've talked a lot about what's going on in the world around us, but it's time I come back to politics for a bit. That said, the name of this world is somewhat misleading, in the sense that I talk about everything, not just politics! But I digress again.

Today's guide is on creating a password protected folder on Windows 7 without any additional software. Yes, you heard that right. No extra software at all! This guide is intended for beginners. But please note, this method should not be used to store financial or otherwise highly confidential material. It might be a good place to hide a planning document for a family member's birthday party or similar occasion where you need to keep something secret temporarily.

Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs will be reviewed by the community and myself. The coder that receives the most votes will be dubbed THE BEST.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Apple is famous for their easy to use consumer software such as Garage Band and iMovie. However, I've found their apps a little hard to use. Why?

We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials...

We're officially seeking Null Byters interested in teaching others! Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, and anything you feel like...

These boxes are inspired by a comment from Imaatfal Avidya on a corkboard post on Platonic polyhedra from sonobe units. Imaatfal was commenting about how the cube and octahedron are related to each other.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

As touched upon in the past, knowing all of the possible words you can play is key to being a better Scrabble player. If you don't have the vocabulary, then you can't compete against the best of the best, and you'll never even get the chance to spar against professionals such as Nigel Richards, Joe Edley, Andrew Fisher, and Wayne Kelly.

When you first become interested in learning how to program, it can be difficult to find a place to start. A lot of questions come up, especially if you're new to the idea of programming entirely. After you pick which language you want to learn, you have to worry about how you're going to write the language.

Ah, turducken. The fondest of all portmanteau words and the tastiest of all Thanksgiving day meals. Turducken is a turkey stuffed with a duck stuffed with a chicken—three glorious poultry meats molded into one marvelous, boneless hunk of flesh that any sane carnivore wouldn't dare resist. It's slapped together with pork sausage stuffing, sometimes even three different kinds, and caked with Cajun seasonings.

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

At Kaplan University, our main focus in developing our online MBA programs is career development. We believe the time and effort that is required to obtain a master’s degree online should be apparent the first day the student begins their new career. Earning an MBA could be a step in the right direction towards a fulfilling and satisfying career.*

Part 2 Welcome back! In my last post I talked about the exterior aspects and techniques of building a great looking house, and now we shall focus on the interiors.

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

The HP Touchpad 64 GB is out in action with a robust processor and additional applications in the market. Using the best technology on earth, it is looking forward to give a tough fight to the Apple’s iPad 2. The 64 GB HP TouchPad sound more promising to its predecessors. The experts feel that the two device, HP TouchPad 64 and Apple’s iPad-2 is more or less the same. Let’s have a glance over the device by discussing the various features it encompasses.

Sitting in the dentist’s waiting room, I found I couldn’t browse the internet on my smartphone anymore. My eyes were tired from reading and there were no headphones to listen to music. There are no magazines at this dentist’s office, just an old TV playing Russian music videos ad nauseam. Mostly female Russian singers, and curiously enough they all shared similar traits: they can’t dance. They look gorgeous, but the best they could do is small movements and two slow moves at best- a huge diff...

You'll see a lot of Linux action going down here at Null Byte. We use Linux for hacking-related stuff because it provides a more relaxed programming environment, making it easy to write exploits and tools. Linux has many features Windows is lacking, such as full control over the OS right down to the Kernel and massive availability of mature, open source (read: free & tweakable) tools & projects.

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.
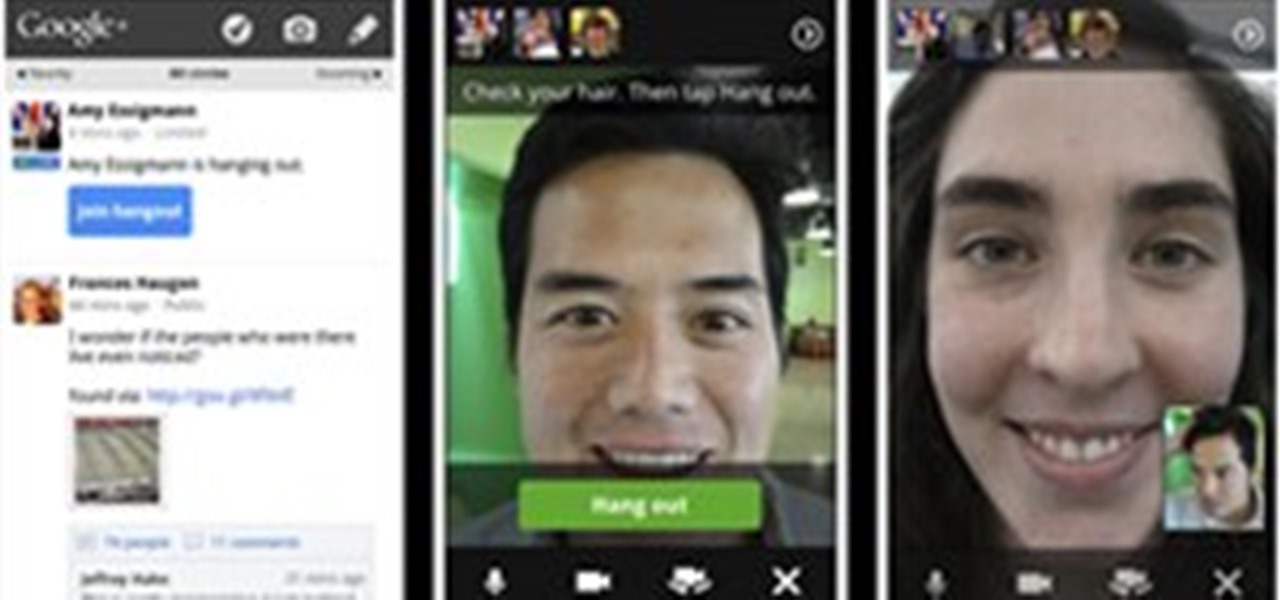
It may not seem like it, but it's been less than 90 days since Google+ was introduced to the world. Since then, we've seen many great features that have made Google+ one of the most attractive social networks around. Today, we've received even better news: major improvements and feature updates that are truly innovative.

Jim Lahey's no-knead pizza dough is more time consuming than Jamie Oliver's "cheat's pizza", but it's quicker and simpler than the more traditional dough recipes. The rise time is only two hours, and the kneading is minimal. I still prefer Jamie's pizza, but I sense this is because I haven't quite mastered Lahey's recipe yet.

Today's segment of Making Art on Your iOS Device takes us into the third dimension. The below apps are suitable for beginners looking to venture into the world of 3d modeling, as well as pros who simply want the basics of Maya in their pocket.

Most stateside gamers have probably never heard of Level-5. If they have, it's more than likely due to the charming and maddening line of Nintendo DS puzzle games, Professor Layton. Some might even remember Dark Cloud and its sequel from the early days of the PlayStation 2, and all eight of you PSP owners in the U.S. might recognize the epic Jeanne d'Arc. These games alone make Level-5 a noteworthy company, but they've quietly surpassed "noteworthy" status to become one of the largest and gre...

Meat and bourbon is a delicious marriage—whether it's bacon-infused bourbon, or bourbon drenched steaks. The recipe below is adapted from Nancy's bourbon-marinated rib eye recipe over at 'A Recipe a Day'. For this version, we used the classic New York strip, with a little sous vide twist (optional).

Making a video game requires an incredible amount of work. It requires people skilled in many disciplines to work together for thousands of hours merging visual art, computer programming, game design, sound design, and music composition into a fun game. The Indie Stone is a Scottish indie development studio started, like so many others, by industry vets who were tired of corporate restrictions and wanted to make the crazy games they had always imagined.
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.