
TypoGuy Explaining Anonymity: A Hackers Mindset
CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.


CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

If you don't want to dress up as a vampire, witch, werewolf, or zombie again this Halloween, step things up a notch and go viral. There have been a ton of funny memes and absurd news since last October, so the only hard part is settling on the right one for inspiration for your costume.

Nothing makes my stomach growl and my mouth water quite like the smell of roasting chicken. It's a pretty universal reaction, too—there's a reason every grocery store places its rotisserie grills and delis near the entrance, after all.

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.

Many people deal with motion sickness on a daily basis, and if you're reading this, chances are you're one of them. Kinetosis can make your stomach roll, your entire body sweat, and make you feel fatigued and dizzy at even the slightest movement, whether it's related to carsickness, seasickness, or airsickness. And let's not forget the worst part—vomiting.

Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

Although pasta is a remarkably simple dish, I find it to be one of the most aesthetically appealing foods. The noodles—especially thicker iterations, like linguine and fettuccine—are graceful and luxurious. Add in some sauce coating the noodles, and a sprinkle of Parmesan or a drizzle of olive oil, and pasta single-handedly reminds us of a basic tenet of cooking: sometimes keeping it simple is the perfect way to go.
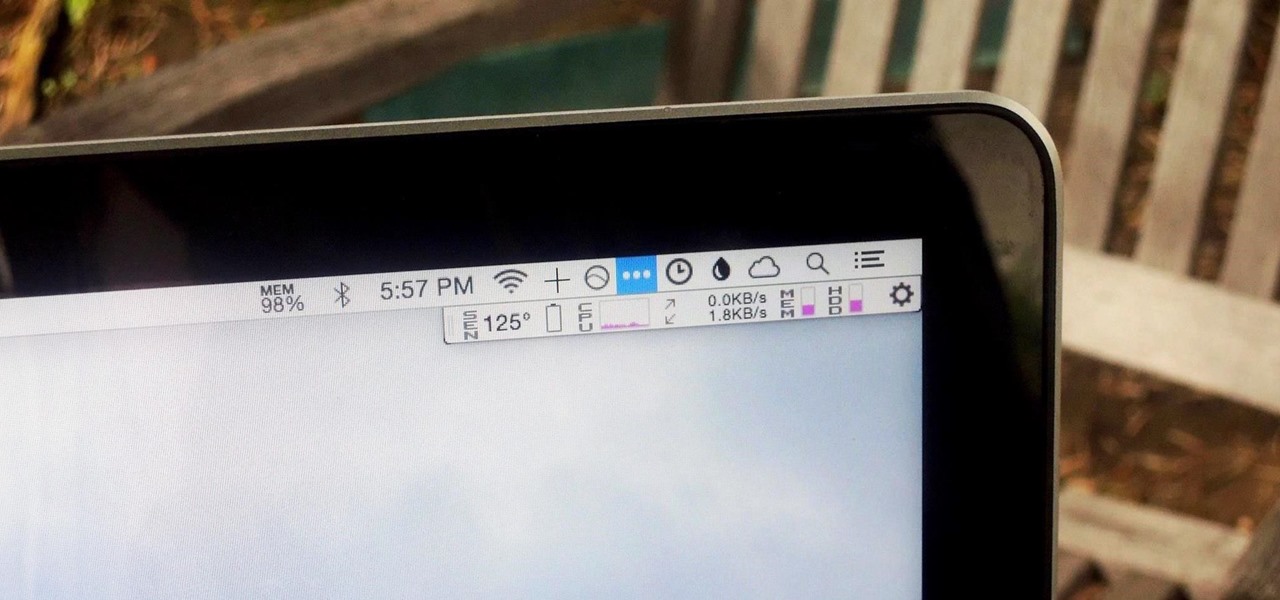
We recently showed you 8 menu bar apps that ever Mac power user should have, covering apps that allow you to control iTunes, eject drives, organize screenshots, and more—all from that tiny strip at the top of your screen.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...
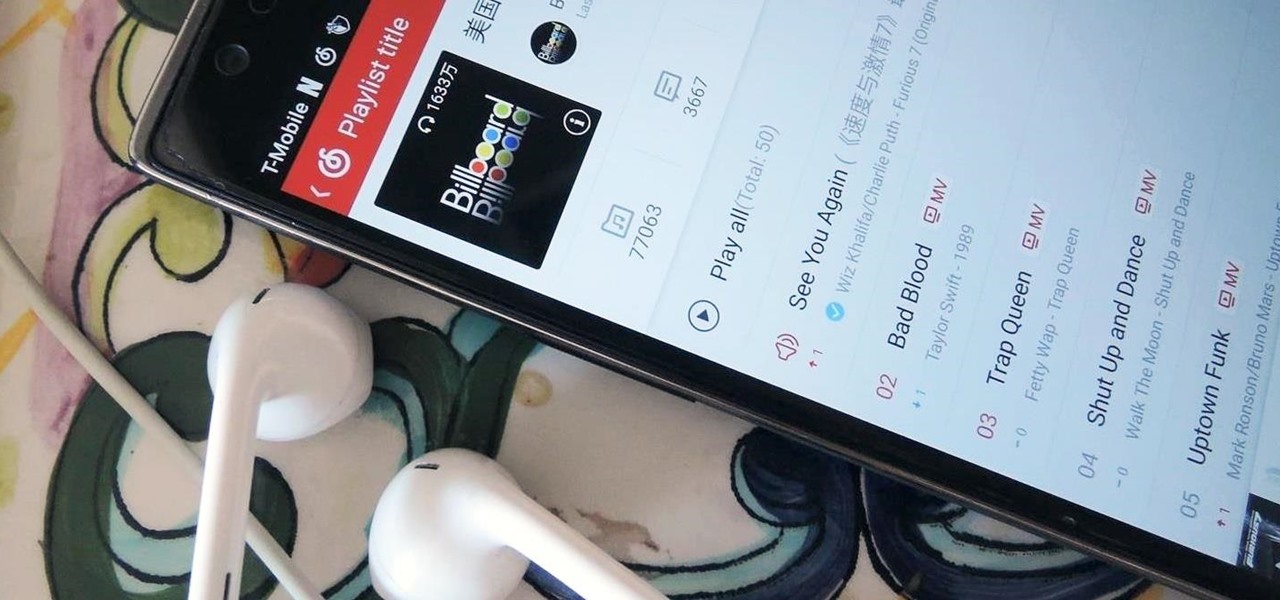
We recently lost Grooveshark, the free music streaming service that supplied users with a huge catalog of free music anytime, anywhere. Since its shutdown, I have been scrambling to find a half-decent alternative, and my expectations were more than exceeded when I found NetEase Music.

Most mobile games have moved to an online-only format, meaning you need to be connected to the Internet in order to get any kind of multiplayer action going. This is great when you're at home on Wi-Fi, but when you're out and about, slow and inconsistent data speeds can cause serious lag. Or worse yet, you may be nearing your monthly data cap!

As glorious as a good drink (or five) can be, the aftermath of alcohol on the body is one of life's least enjoyable features. A few hours of fun can come at the expense of a day or two of feeling dead to the world, with an upset stomach, an aching body, and a headache that makes it feel as though your friends used your head for a piñata.

At last, what you all finally waited for! Hi! Fire Crackers,

While the Apple Watch does have up to 18 hours of battery life each day on a full charge, your results will vary depending on how often you use it and what you're actually doing with it.

Facebook essentially strong-armed us all into installing their standalone Messenger app for mobile devices, but the recent initiative that allows third-party development on the platform definitely makes it worth your time.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

The gag reflex: it can interfere while in the dentist's chair, upon seeing another person throw up, or even just getting a whiff of a disgusting, stomach-twisting scent. Every time this reflex kicks in, it stops us immediately, inducing a choking, gagging, coughing fit.

It's 3 a.m. and you're wide awake—your mind is running wild with worries, workplace stress, and panic about the day that lies ahead. How can you possibly slip back into sleep and snag a few more hours of rest when you're so anxious?

Sitting in a cubicle and never seeing sunlight during the workday is unpleasant to even think about—and sitting in a flourescent-light cube can have terrible effects on both our work performance and overall attitude. Yet there are ways to counteract the effects of cubicle sitting, even if you can't sit in a sunny office or work from home.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

We all carry a bit of anxiety around with us. Is our boss still annoyed because we could barely stay awake in yesterday's pre-dawn meeting? Will our friend hate us forever because we forgot to call them back two weeks ago? Whatever worries pop up in your mind, whether they're monumental or insignificant, it can be hard to quiet those nagging voices, but you can shut down your nonstop mind with a bit of relaxation, distraction, and action.

My years in the restaurant business have taught me many things. Some of those things are best left unsaid and other things require a PhD in vulgarity, but the one thing I learned that I keep coming back to night after night is that you do not have to spend a lot of money to drink excellent wine. This is especially true of champagne...I'm sorry, sparkling wines.

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.

If you've ever noticed that the stock launcher on an Android device seems to just feel faster than any third-party home screen replacement app, this is not a placebo effect. Most manufacturers, Samsung included, force their stock launchers to reside permanently in your phone's memory, thus reducing the risk of redraws.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Shortly after the official release of iOS 8, news outlets like BGR, Gizmodo, and Huffington Post were instructing iPhone 4S users to refrain from updating (which were practically regurgitations of an Ars Technica piece).

Apple definitely wasn't first to the widget game, but any iPhone running iOS 8 or higher can add widgets to their Today View found via a swipe down from the top of the screen when on the home screen or in any app. There's even access to widgets on the lock screen via the same swipe down on iOS 8 and iOS 9 (on iOS 10, iOS 11, and iOS 12, all you have to do is swipe right on the lock screen).
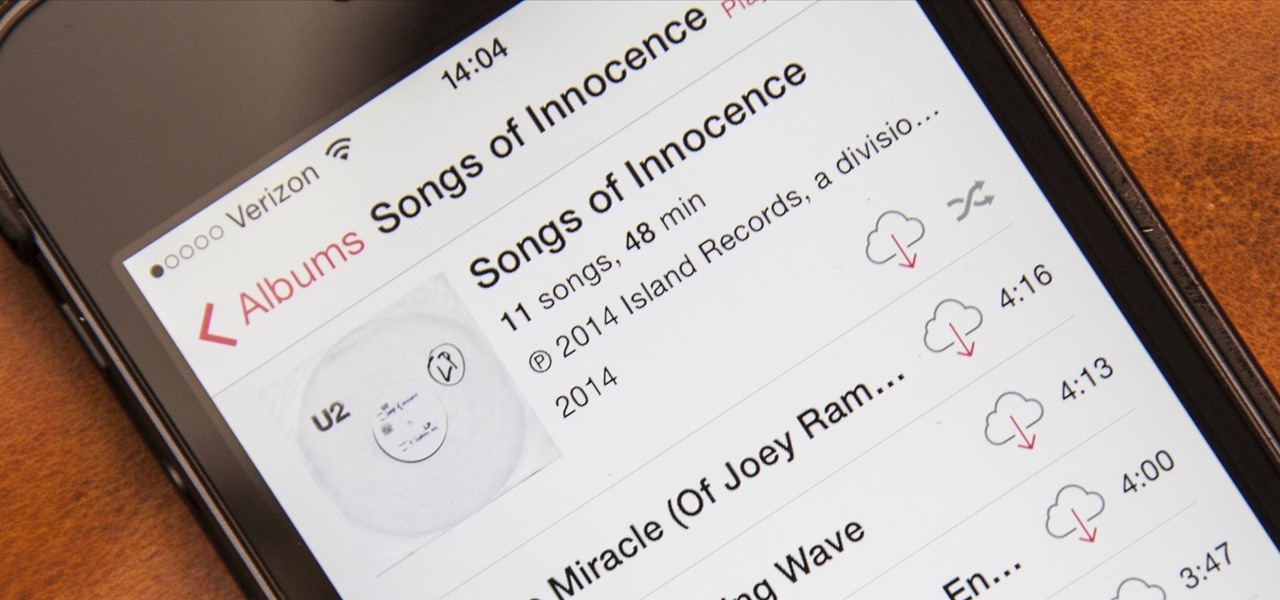
From my experiences, there are only two types of U2 people: those that love them and those that hate them. I'm the latter, so it's pretty damn annoying that Apple just added U2's new album, "Songs of Innocence," to my iCloud. If you find it creepy that U2 is appearing on your iPhone or in iTunes, don't worry—I've found a few ways to deal with it. UPDATE: How to Delete U2 Forever & Ever

One of the best features of Android is the fact that it's open-source, giving developers the ability to use it on pretty much any device they can think of, like on a Windows PC using Andy. That's what drove the creators behind the Android-x86 project to port over the mobile OS to any computer running an Intel processor.

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.
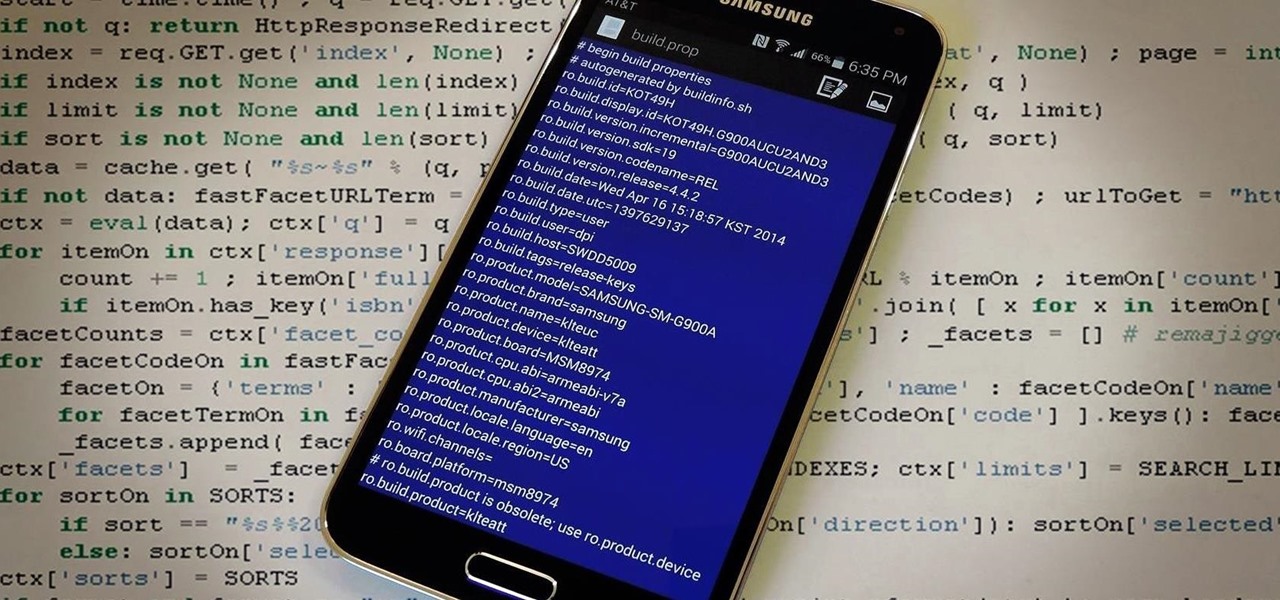
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Android has existed.

If you've ever had issues charging your iPad, iPhone, or iPod touch, like most other Apple products, the culprit to blame is usually a frayed or damaged cable. It's a common design flaw due to the thinness of the cords and the weak sheath surrounding them — but that's not always the problem.

If you've been to a farmer's market during tomato season, chances are you know that heirloom tomatoes are pricier (and funnier-looking) than their hybrid counterparts.

Many home cooks were taught never to press down on a burger as it cooks since that would ruin your all-beef patty by getting it to release the juices it needs to stay tender and moist.
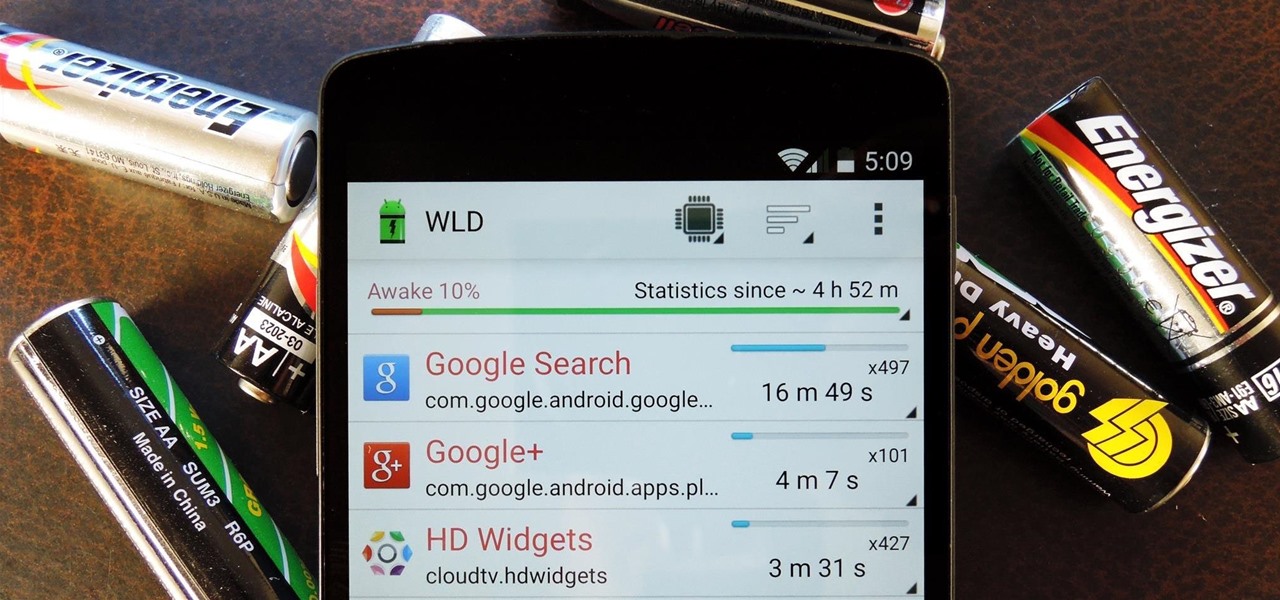
Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

If you're anything like me, your day doesn't start until you've sloughed away your grogginess with a scalding hot shower. That perfectly-heated water can clear stuffed sinuses, relax the muscles, and make pretty much anyone feel squeaky clean. However, a cold shower can do even more for you if you can stand the low temperatures.

Google has finally announced the newest flavor of its mobile OS, Android L (Lollipop?), and I couldn't be more excited. While we won't see its official release until the fall, there are still some features we can get our hands on right now.

Apple has released the 2nd beta of iOS 8, exactly fifteen days after the first version was unveiled at WWDC and subsequently released to developers. I've already shown you some of the new features of iOS 8, like location-based app alerts, randomized MAC addresses, hidden Safari tricks, and a slew of new things in the Messages app. But if you've had the chance the explore iOS 8, let's go through some of the changes that Apple has made to the latest iteration of its mobile operating system.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.