
Hack Like a Pro: How to Anonymously Torrent Files with Tribler
Welcome back, my nascent hackers!


Welcome back, my nascent hackers!

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.
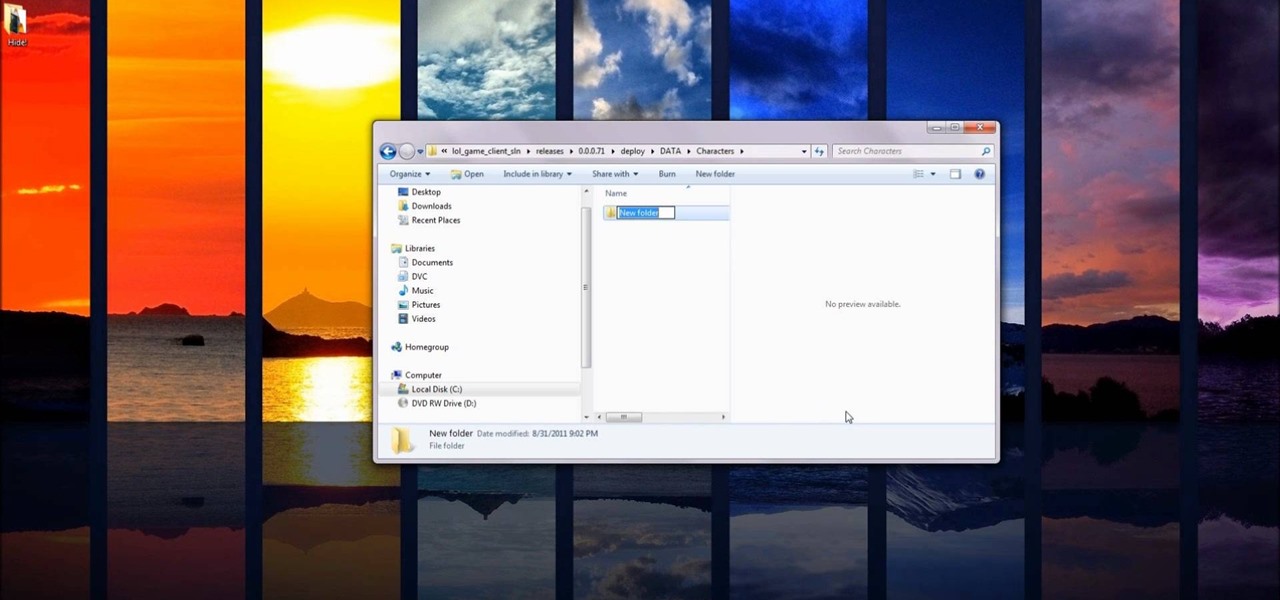
If you're interested in changing the recommended items presented to you each time you open the shop in League of Legends, check out this guide. You will need to have access to your Riot Games and League of Legends directories first.
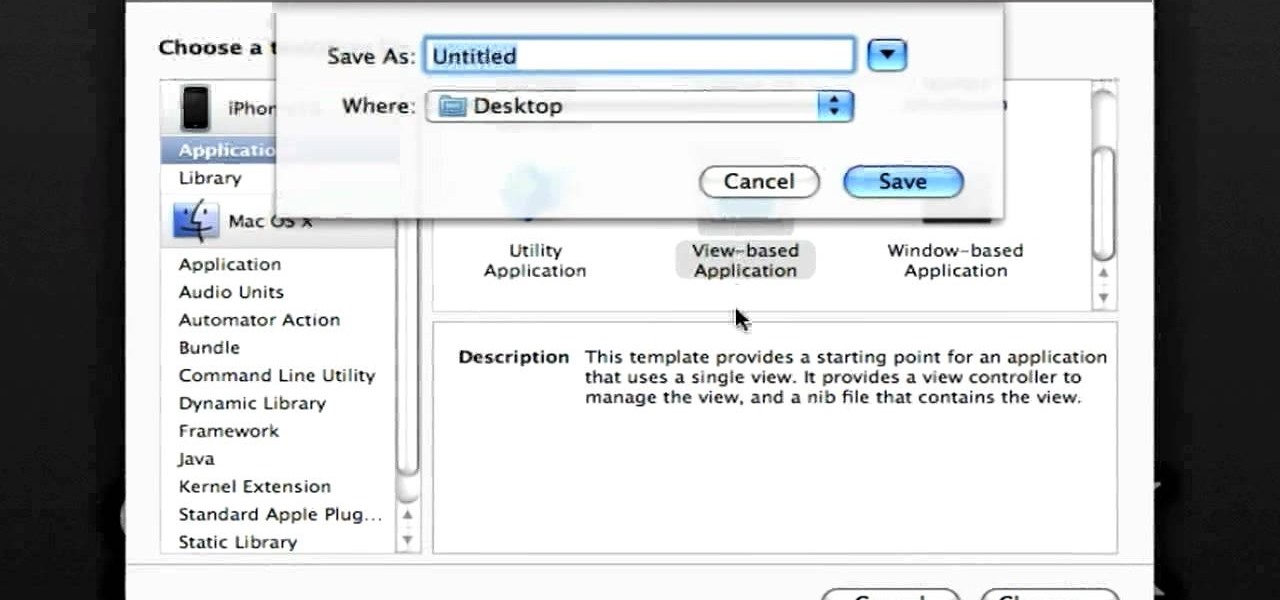
In this clip, you'll learn how to make recourse to the documents folder from within an iOS application. Whether you're new to the Objective-C operating language and Xcode IDE or are a seasoned developer merely looking to pick up a few new tips and tricks, you're certain to be well served by this tutorial. For more information, including a complete overview and detailed, step-by-step instructions, watch this free video Objective-C programming lesson for iPhone & iPod Touch developers.

Flickr is the most known and dependable photo sharing website to date, so if you haven't made an account yet, you better now, if you want to share your precious photos with family, friends, and even the whole world! Flickr allows you to store digital photographs online and share them with other people.
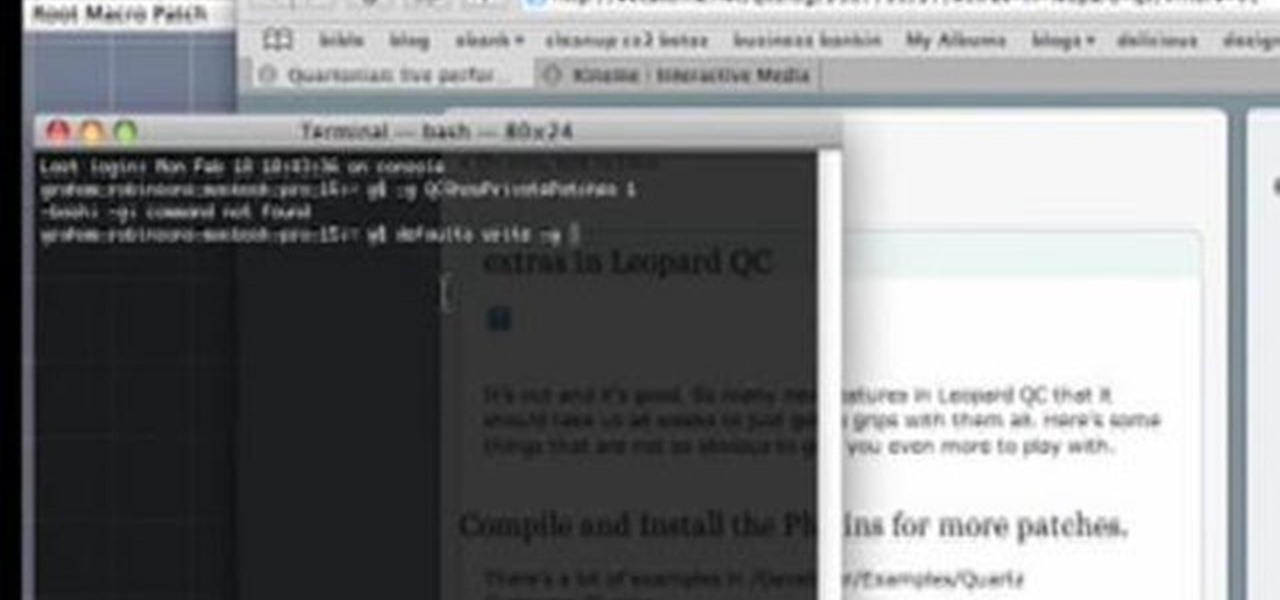
This is a very basic introductory video that teaches you how to successfully install Quartz Composer on your MAC OSX 10.5 Leopard. Quartz Composer is a node-based graphical data software that uses visual programming language. Built exclusively for use on the MAC OSX, it's a handy software for graphic designers.

This is the first of 3 steps that will show you how to juggle three balls. Jim the juggler demonstrates how to get them up and going. Step 1 begins with one ball, so be patient, you need to work your way up! (WMP files and smaller videos are available at the root directory)

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

The mighty Arduino microcontroller can be used to show children how robots work, it can be used to hack into hotel rooms, or it can be used to let you know when you've got a new job opportunity!

Use PubSubHubbub

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

With the release of the Samsung Galaxy S5 right around the corner, the first full system dump has been released by Sammobile. As the inevitable ports of functioning apps slowly begin to leak, today we've got a non-app aspect of the system and the one that tends to leak first—ringtones.

If you are ready to make your podcast more professional, have a look at this tutorial. In this video, you will learn how to take an ordinary, amateur podcast and use different programs to make it sound more polished. This will bring your podcast up to professional grade and make it more likely to get distributed by larger companies.
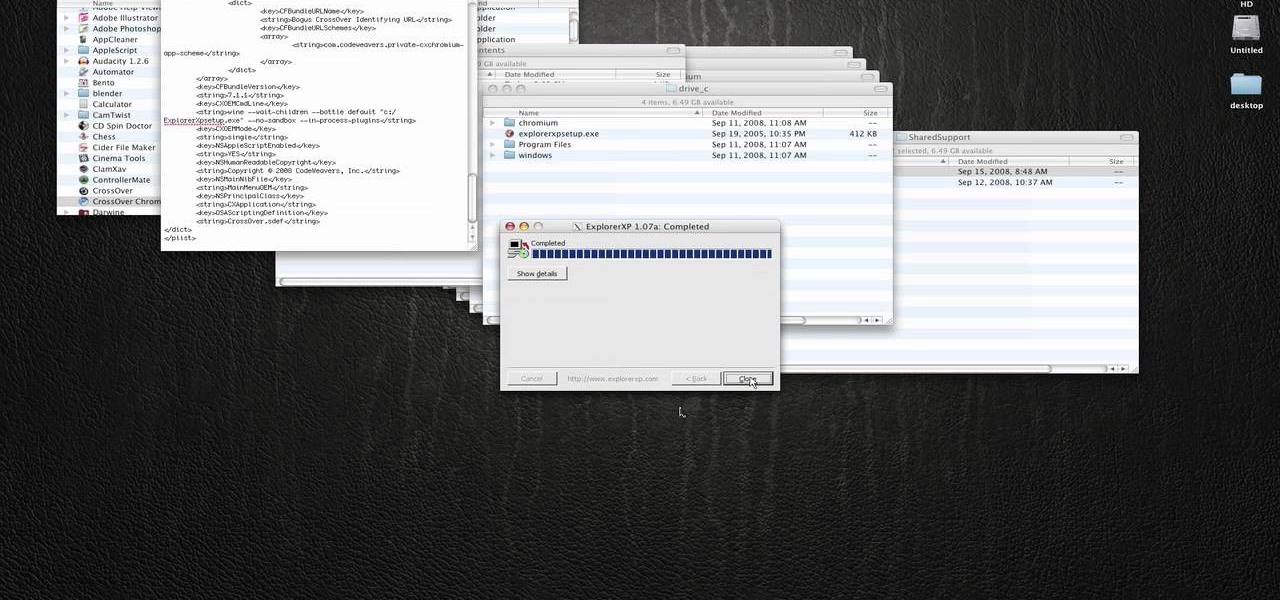
In this how to video, you will learn how to run Windows programs for free on a Mac using Crossover Chromium. You will need to download Crossover and install it by downloading it and dragging it into the applications folder. You will also need Explorer XP. Go to the applications folder and show the package content of Crossover. Go to shared support as you will need a file here later. Open Chromium, go to support, Chromium, and Drive, and then drop Explorer XP into the folder. Open the info fil...

This video shows the method to SSH into iPod Touch 1G or 2G. You need an iPod touch 1G/2G with Firmware 2.2.1 or previous (Windows), a Windows based computer and a jailbroken iPod Touch which has Wi-Fi connectivity. Open Cydia, go to search and type OpenSSH and install it. Go to settings, Wi-Fi and click on the blue arrow next to the network. Copy down your IP address from the resultant window. Open WinSCP.net and go to Downloads, installation package. Install the package and open WinSCP from...

We know, we know: How many people actually burn stuff onto CDs these days? Well, while external hard drives that hold several terrabytes of data and flash drives have kind of replaced our reliance on CDs, every now and then they're good for quickly compiling a "Pop Hits of the '80s" CD for your girlfriend or simply for storing your illegal version of Microsoft Office.

Attention aspiring screenwriters! In this tutorial, learn how to sell that script. You may have written the next Hollywood blockbuster – but unless you can finance the film yourself, you’ll need to sell the screenplay to a producer who can make it come to life.

Follow this quick video demonstration to see how to knit a shaker rib stitch. The shaker rib is also known as the half fisherman, and that's because it's not as bulky as the fisherman rib. During this process, you'll even see how you can knit one below, or k1b.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to make a Twitter tamagotchi bot with PHP.
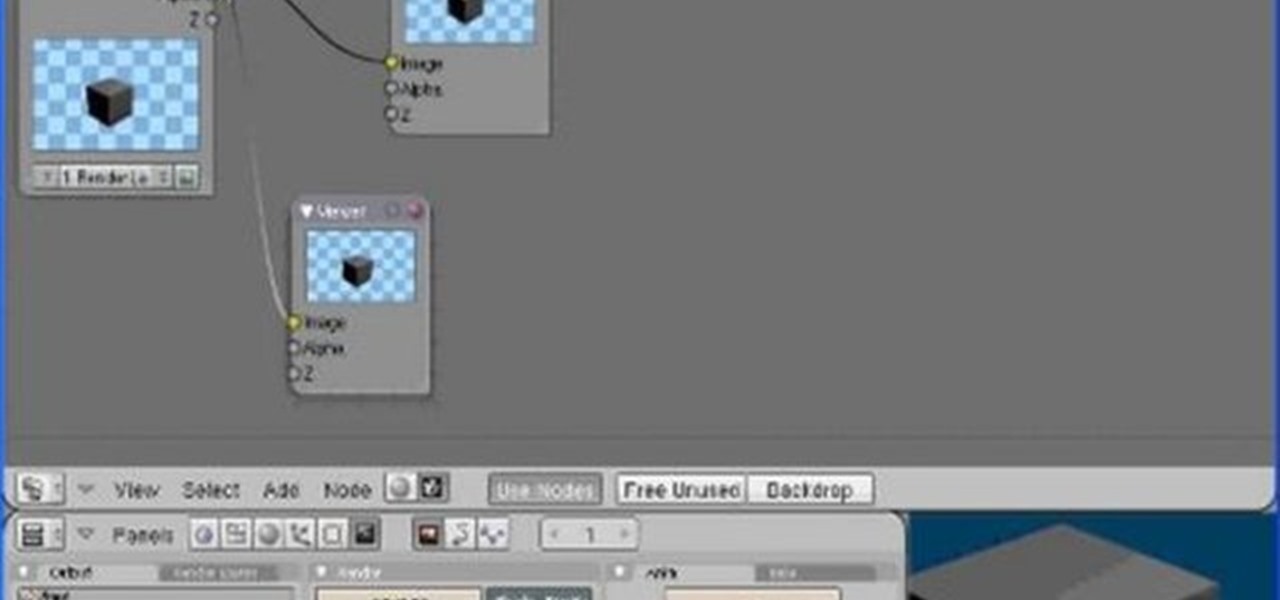
Conceptually, what is node-based compositing and what do nodes do? This clip uses the factory analogy to convey the concept. Blender can process video, images, sequences, and families of images in a directory. Then you'll fire up Blender and talk about threading nodes and how images are duplicated and routed through the compositing network ("noodle"), how threads are created between sockets. Creating threads, cut threads. The clip also points out common threading errors and misrouting threads...

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION
Ah, the fabled dark mode. In the past, many users were delighted to find the existence of something called Royale Noir, a dark theme option that was available for Windows XP. Yet for reasons unknown, Microsoft had kept knowledge of Royale Noir a secret until some bright minds discovered its existence, and the rest is history.

We use ADB and Fastboot for so many things in our softModder tutorials, and to get them, you normally have to download the entire Android SDK and install them. But not anymore.
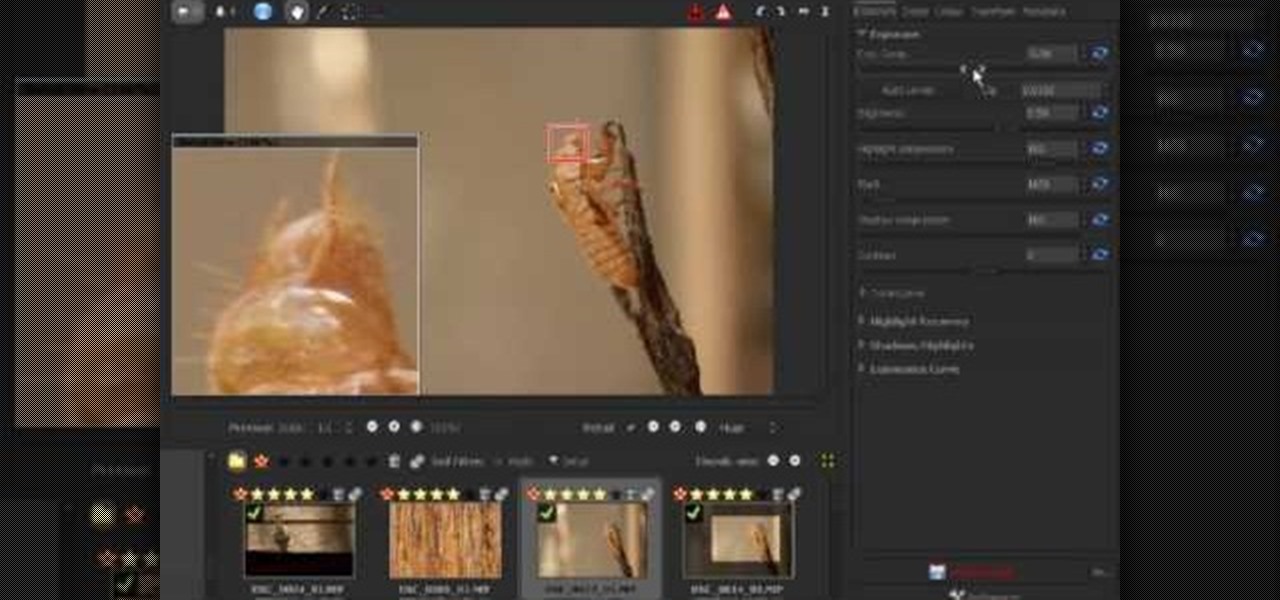
In this video, we learn how to use Raw Therapee with Gimp. First, you need to go online to Raw Therapee, then download and install Raw Therapee. Once you have this, open it up and familiarize yourself with the layout of the software and where the different tools are at. Next, change your preferences and pick your settings throughout the different folders. Next, find GIMP through the program folders as your installation directory. Now, it will export your images to GIMP automatically. This way...
First click the explore button, this will open a fold in which you will click homegroup and the second computer in the network. By clicking on that you will see what is in the homegroup. For example clicking on the video icon shows you all the videos available. If you right click on the video you can choose to watch it, open it, send it to different places, drag it onto your computer or copy and paste it into another directory.
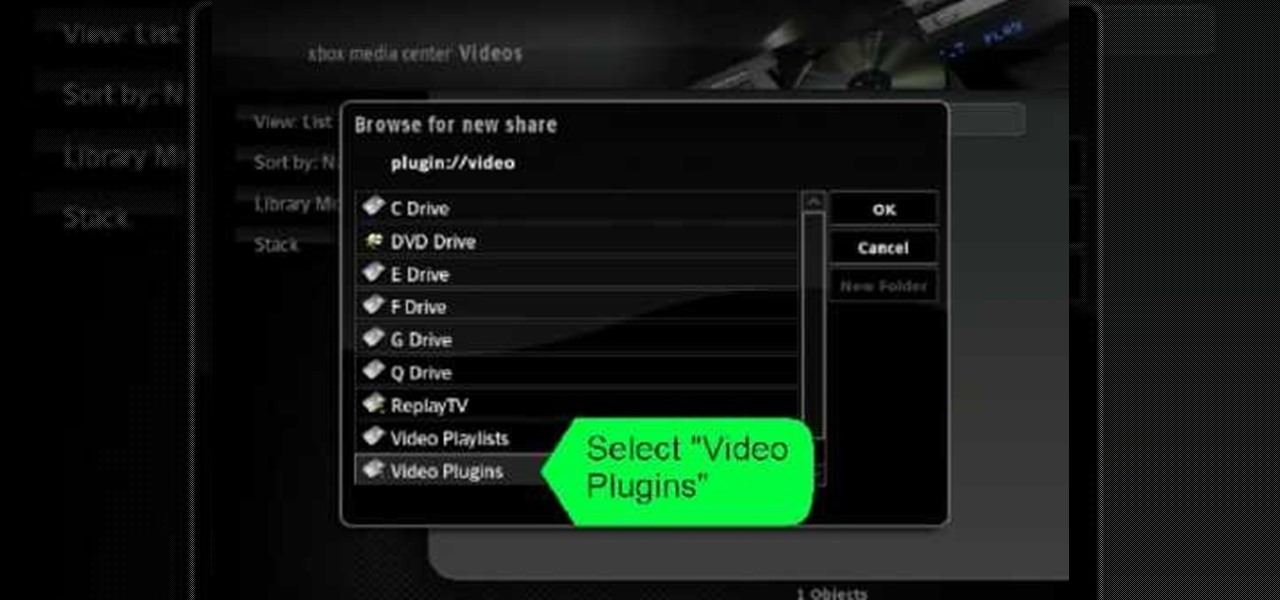
This video shows in detail and with annotations how to add plugins as sources in XBoxMediaCenter. With these plugins, you can watch selected media content from the web without browsing the websites with the computer. You browse through the items as if they were on the hard drive of the console. Available plugins include Joox, TVLinks, surfthechannel, seeqpod, powerflv, alpha centauri (german edutainment), stage6, lindenstrasse (german soap), myspace, Apple Movie Trailers, BBC radio, youporn, ...

Because of the way Android is laid out, you automatically lose a portion of the top and bottom of your screen thanks to the status and navigation bars. The thing is, you don't always need the navigation buttons. By hiding them, you can enjoy more of your Galaxy S10's big, beautiful display.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.
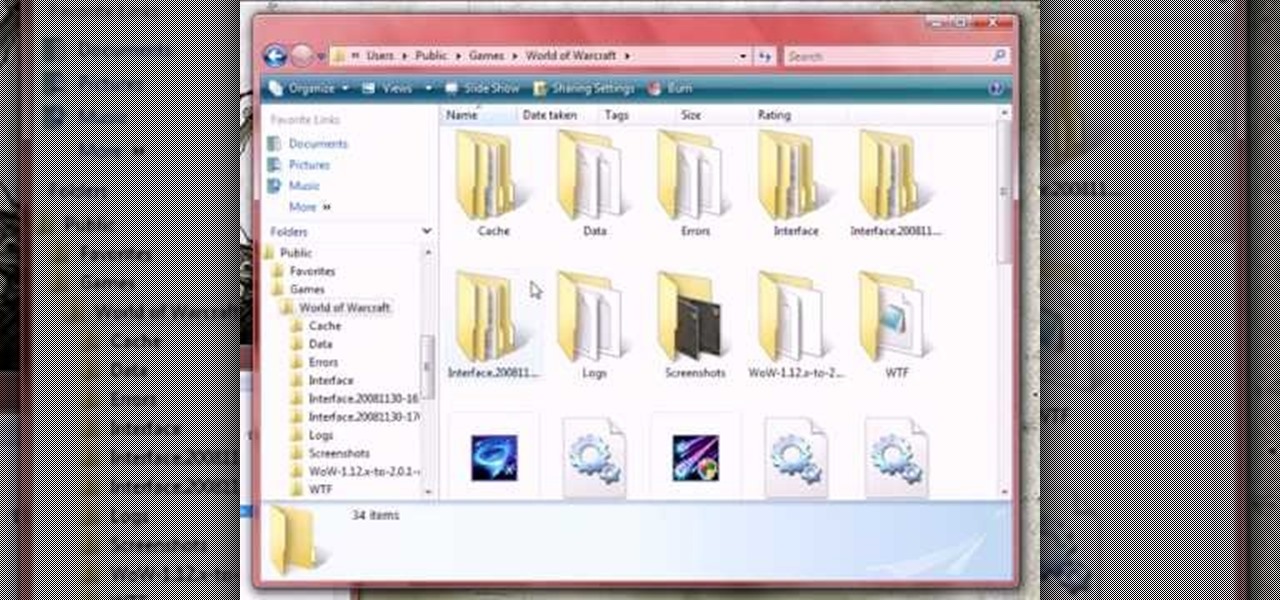
In this tutorial, we learn how to clear your World of Warcraft cache. First, you will go to your computer, then the local disk (C:), then users. From here, go to the public folder, then click on 'games', and then 'Word of Warcraft'. Once here, you will need to delete the 'cache' and 'wtf' folders. Next, you can exit out of this and continue to play your game as normal. This will clear out history from your game and make it load faster than before. If you aren't a Vista user, you will be able ...
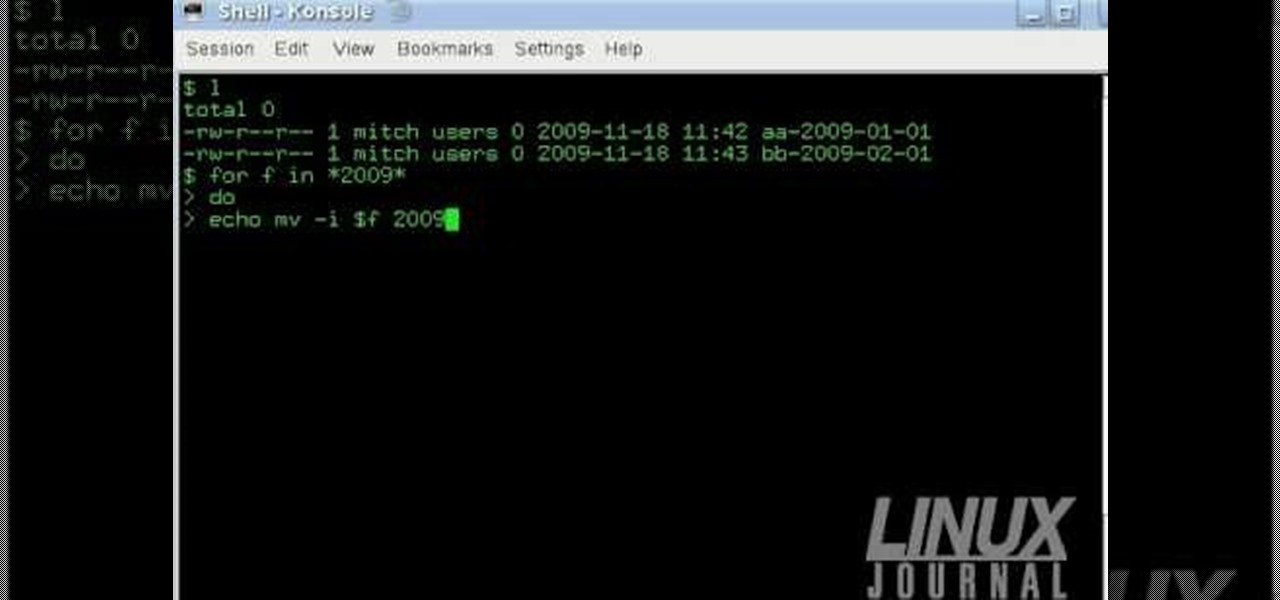
The Linux command shell provides a very powerful interface for doing various system tasks. This video explains with an example, how to use a bit of programming techniques to batch rename files with similar naming conventions.

In order to build Google Chrome extensions, you will need to familiar with scripting and codes. These are small programs that add additional functions for programmers. It is a compressed directory. These files must have a particular name: i.e. "manifest" (manifest.json). An extension will have at least one of the following: browser actions, page actions, content scripts, and utility web files.