In this tutorial, we learn how to use KDE konsole bookmarks. You can add a bookmark, then go to the home directory and then you will be able to go back to where you previously were. To do this, save the bookmark of the entry that you are in. Do this by clicking the bookmark tab, then add bookmark. After this, go back to the home entry and then click on your bookmarks tab again. Once you click this, you will see your new bookmark on the bottom, when you click that it will bring you back to you...
This video tutorial is in the Computers & Programming category where you will learn how to encrypt files & folders on a Mac with TrueCrypt. Open up TrueCrypt and click on create volume > create an encrypted file container > next > standard truecrypt volume > next. Here you name your file, choose the directory where you want to put the file and click 'save'. Choose the encryption type and click 'save'. Choose the volume size and click 'next'. Now type in a password and click 'next'. Then in th...
This video tutorial belongs to the software category which is going to show you how to set up a home server from behind a router using WAMP. You will need a free program called wampserver. Go to their website, download and install the program. Then click on the icon and click 'put online' and the local host comes online. To check it, open up your browser and type in local host in the search box and it will show you the default index.php file. Again click on the icon and click 'www directory'....
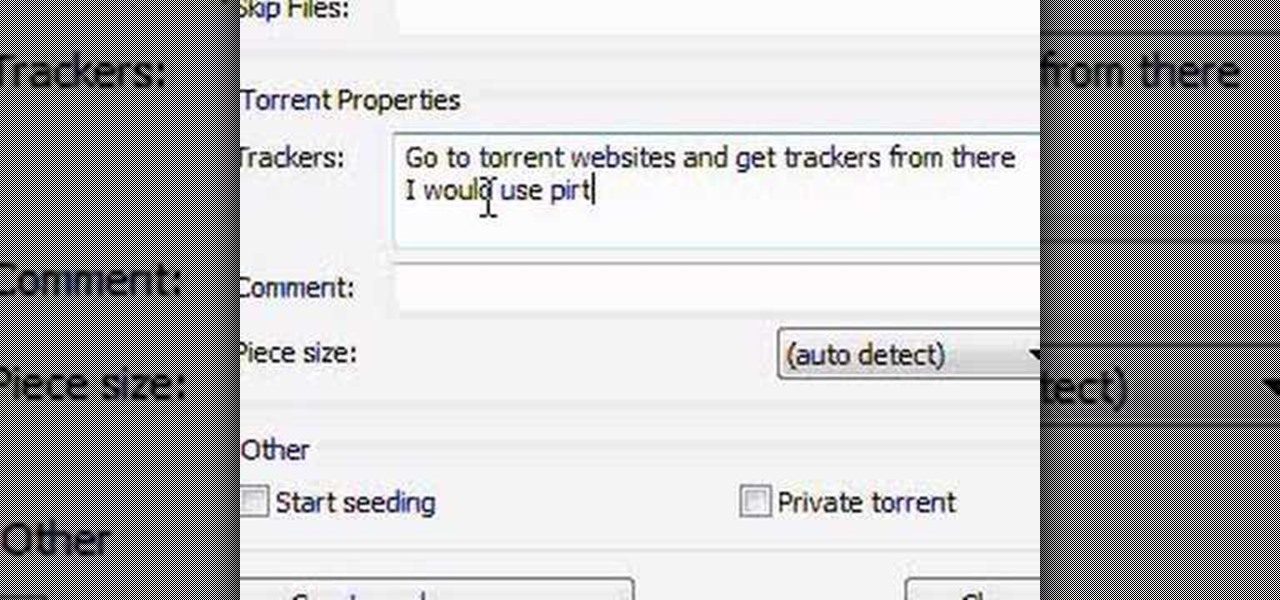
In this video tutorial, viewers learn how to create a .torrent file using u-Torrent. Begin by opening the program. Click on File and select Create New Torrent. Now select the file, select the directory and type in the tracker code. Then click on Create and save as. Once the file is created, click on File and select Add Torrent. Locate the .torrent file click OK. Now wait for the torrent file to finish downloading. This video will benefit those viewers who use u-Torrent and would like to learn...
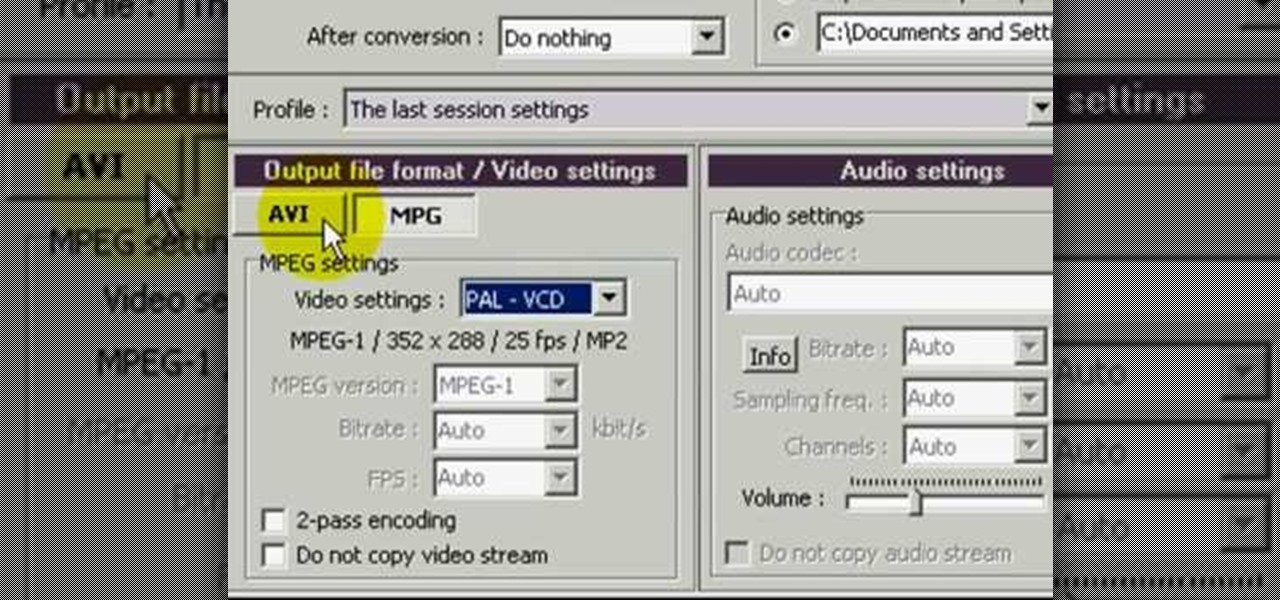
In this how to video, you will learn how to convert a flash video to an AVI file. First, download the Pazera Converter program. Open the program. At the left hand corner, click add files and find your flv file. Next, select and open it. Once it is imported, go to output directory and choose which folder you want the new file to be placed. Go to output file format and click AVI. You can also choose MPG instead if you want. Now click the convert button at the top. You will see a progress bar. O...

In this how-to video, you will learn how to see high quality pictures of your own house. First, go to your web browser and click on Maps and Directions in the directory on the MSN website. Next, click on locations and type the address of your house or whatever place you want to see. Once this is done, click on bird's eye to get a closer photo of the area. Next, click zoom in until you get an even larger image. You can also click on the picture and drag to move around the image. This video sho...

In this video, our author, atomicinteractive, shows use how to use Fetch FTP to upload a temporary webpage. Please make sure your directory has the html file. Please find your email with ftplogin information. This will also show login information for the control panel and creating alternate email addresses.

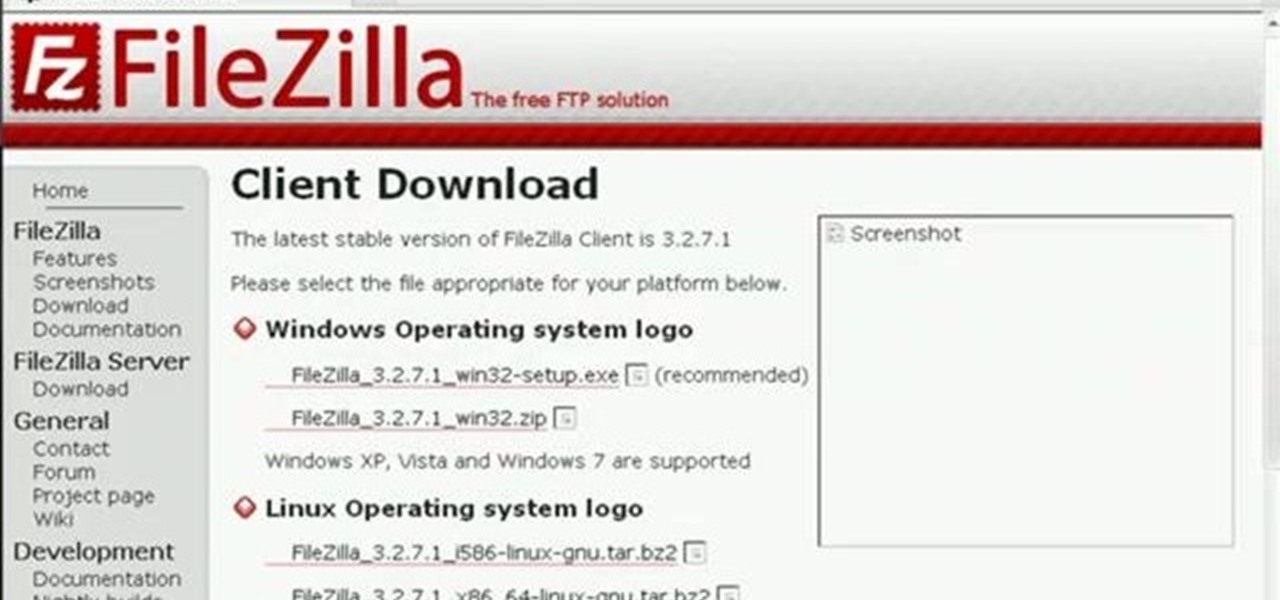
In this Computers & Programming video tutorial you will learn how to update a website with an FTP client (v† la FileZilla). Download FileZilla client from www.filezilla-project.org. Find your server IP address from your web host, which will be found in the hosting control center. In the video, it is GoDaddy.com. Open your filezilla client and put in the IP address of your web host and your username and password for your hosting account. Then click ‚Äòquickconnect‚Äô. This will connect you to ...

In this Computers & Programming video tutorial you are going to learn how to add "Hide" & "Unhide File" to the right click menu. Go to reg.exe and type in ‘regedit’ and click ‘enter’. On the page that opens up, Navigate to ‘HKEY_CLASSES_ROOT’ > directory > shell. Right click on shell and select new > key. In the ‘key’ box type ‘Hide Folder’. Now right click on the right side box of the page and select new > string value. Type in ‘HasLUAShield’ in to the box that opens up. Now on the left side...

This video teaches the secrets of partitioning a hard drive on a MAC in simple steps. First open the disk utility, select the root directory of your hard drive and click partition. Now select the required partitions under the volume scheme, adjust the drive space and name them. Select the format a MAC OS Extended (Journaled) and select GUID Partition table from option if you want to boot it. Click 'Apply' to start the partitioning and when its done start using it.

This instructional video shows you how to reboot your iPod Touch 2G after shut down. First shut down the device and plug it to a computer via USB. Use the links in the description if you have the newest version of OS X. Put the device in to DFU mode by holding the home and power key for 10 seconds, letting go of the power key keep holding the home key. Download the RSlite folder from the link in the description. Open the terminal, change the directory to the Rslite folder and type the code re...

There're plenty of great ways to get traffic, especially this off-site optimization technique using classified ads to point website traffic back into your site itself.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Android used to have a notification ticker, but those days are long gone. Now, important new messages pop up on the top half of your screen with what's known as a "heads up notification." If you're in the middle of something, these popup notifications can be pretty annoying — luckily, it's pretty easy to turn them off.

Alright, let's dig into this and get the simple stuff out of the way. We have a journey ahead of us. A rather long journey at that. We will learn topics ranging from creating object filtering systems to help us tell when a new object has come into a scene to building and texturing objects from code.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Android 7.0 Nougat has finally arrived—well, technically, it's in the process of arriving on Nexus devices across the globe. Google uses a staged rollout system to prevent excessive server load when issuing Android updates, which means even though Nougat has made its official debut already, you might not get that "Update available" notification for another few weeks.

I recently posted a Tutorial about setting up Dendroid: http://null-byte.wonderhowto.com/how-to/setup-dendroid-android-rat-0167299/. I have worked the last 5 days on getting the Dendroid Binder, given with the Dendroid Source, working. This solution only works on Windows systems!

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Hi , Today i will show you how to do HID Keyboard Attacks With Android BUT without using Kali NetHunter BUT You will need to install custom kernel to your Android device, that will add keyboard+mouse functions to it's USB port,So Lets Get Started

I wrote a python script that allows you to easily ask what service runs on a specific port and vice-versa. Now, I am sure that such a program already exists on our lovely linux OS's, but... I didn't think of that before I started, and haven't found it yet. So if you haven't found it yet either, maybe you'll find this of some use. It's just called getport. If I have a port number, and want to know what services run on that port, I do:

On mobile devices, the Notification Center received a huge facelift when iOS 8 was released, but it wasn't until Yosemite that its Mac OS X counterpart received the same amount of love—especially the much needed ability to add custom widgets, like a FaceTime dialer.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Say hello to the Sony Xperia T3, a light and slim Android smartphone—in fact, it's the thinnest 5.3" smartphone on the market.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

If you pre-ordered your Samsung Galaxy S4, it might very well be possible that you're reading this on your brand spanking new Android device. As is commonplace with the release of popular smartphones, rooting instructions are usually released simultaneously. I mean, what's the point of paying so much for an expensive phone if you can't have a little fun? Android developer Dan Rosenberg (aka djrbliss) recently announced that you can root your Samsung Galaxy S4 using the root exploit he origina...

This week, another guest returns to our Steampunk R&D show for the second time, Thomas Willeford. In our very first podcast, Thomas talked to us about creating his empire; this time we most notably talk about his recent appearance on the Science Channel's program Odd Folks Home, in an episode entitled "Blow Off Some Steampunk". Thomas Willeford is the owner and operator of Brute Force Studios, and has been responsible for some of Steampunk's most recognizable props and accessories, such as th...

The Emperor of the Red Fork Empire, aka Justin Stanley, joins us again on Steampunk R&D. This time the subject matter is a little more meandering than last time when I interviewed him about his background as an artist, maker, and performer. If you want, you can check out that podcast first before listening to the latest one below. In this podcast, we talk about current events in the Steampunk world, such as TeslaCon 3 & 4, defining Steampunk, Lantern City, the TSA, and more. We may or may not...

Justin Stanley, better known to many as the Emperor of the Red Fork Empire, is both an artist and a personality within the Steampunk community. His contributions range far and wide, and in this episode of Steampunk Research and Development, he talks a lot about his artistic vision, how to be an artist, and how best to give and receive artistic criticism.

This week on the Steampunk Research and Development Podcast, our guest is Joey Marsocci, better known to the world as Dr. Grymm. He's a full-time, professional Steampunk maker, and is the owner and operator of Dr. Grymm Laboratories. He's written several books and has worked as a designer at companies such as Hasbro and Disney. In fact, he worked with Disney to design the 20,000 Leagues Under the Sea attractions for both Paris and Tokyo Disney parks.

Today, on our first episode of Steampunk Research and Development, we'll be interviewing Thomas Willeford, owner and operator of Brute Force Leather. Thomas is a man of many talents, and has worked in a vast array of fields. His Steampunk work can be seen in his book, Steampunk Gear and Gadgets, as well as on the television show Castle. Thomas is also one of the creative consultants on the upcoming television show Lantern City.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

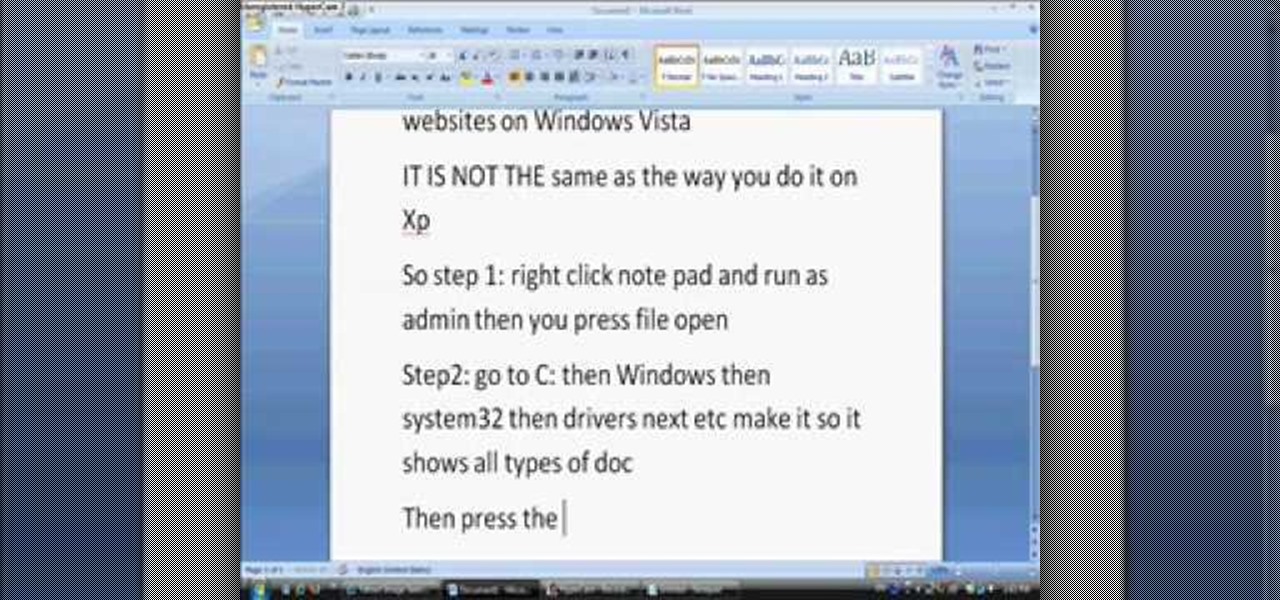
In this tutorial, we learn how to block websites on Windows Vista. First, you will right click on the notepad and then run as admin. From here, you will click "file open". Then, go to the C drive and open up windows. Then, you will go to the system and find the drivers, then click on the host file. From here, go to the second local host and press enter twice. Then, type in "127.0.0.1" and press tab. Then insert all the directories that you want to block. From here, you will be finished blocki...