Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.
A quick video showing how to get free music online. May take a couple minutes per song. To prove quality I used the song i download in the video as background music. "I Wish" by Skee-Lo

This is a Tinkernut video cast. This video shows you how to control your computer (mainly games and miscellaneous programs such as Google Earth) using your webcam.
Any hacker worth her salt will need to debug from time to time. One particularly efficient way to check your code is with the RATS code checking tool. In this video, you'll learn how to use the RATS code checking tool for C/C++, PHP and Perl. For a detailed walkthrough on how to use RATS scanner to audit your source code, take a look!

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

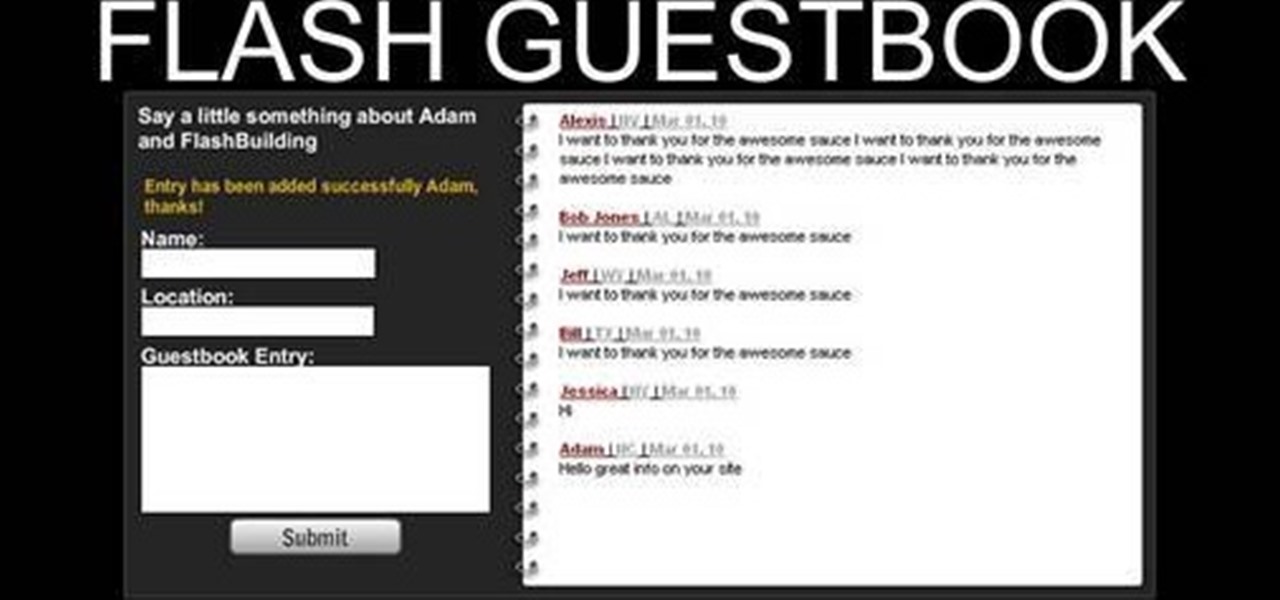
Allow visitors to your website to leave comments and feedback on your website with Flash and Action Script 3. This tutorial walks you through the process, also using PHP and MySQL, to create your guestbook and then add it to your website.

It's time to take control of your wardrobe. This week the Threadheads show you some quick and easy ways to apply applique's and iron on transfers.

The Motorola Droid is the reigning king of the Android family, but it's getting a little old and you're probably looking for a way to improve your phone's performance if you own one. Why not root the dang thing and install a custom ROM on it so it'll at least be organized the way you want it to be! This video will show you how to install custom ROM's (basically phone UI's) on a rooted Motorola Droid phone, allowing you nearly limitless customization options for your awesome phone. The ROM in ...

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Welcome back my fellow army of hackers! Today we'll be hacking a website. Hacking is technically not the right word used here. It should be defacing! So we are going to deface a website...

You can run Android 2.3 Gingerbread on your Sprint HTC Hero. Watch this video to learn how to use CyanogenMod to install Android 2.3 Gingerbread on your HTC Hero. Here is the link for the described in the video.

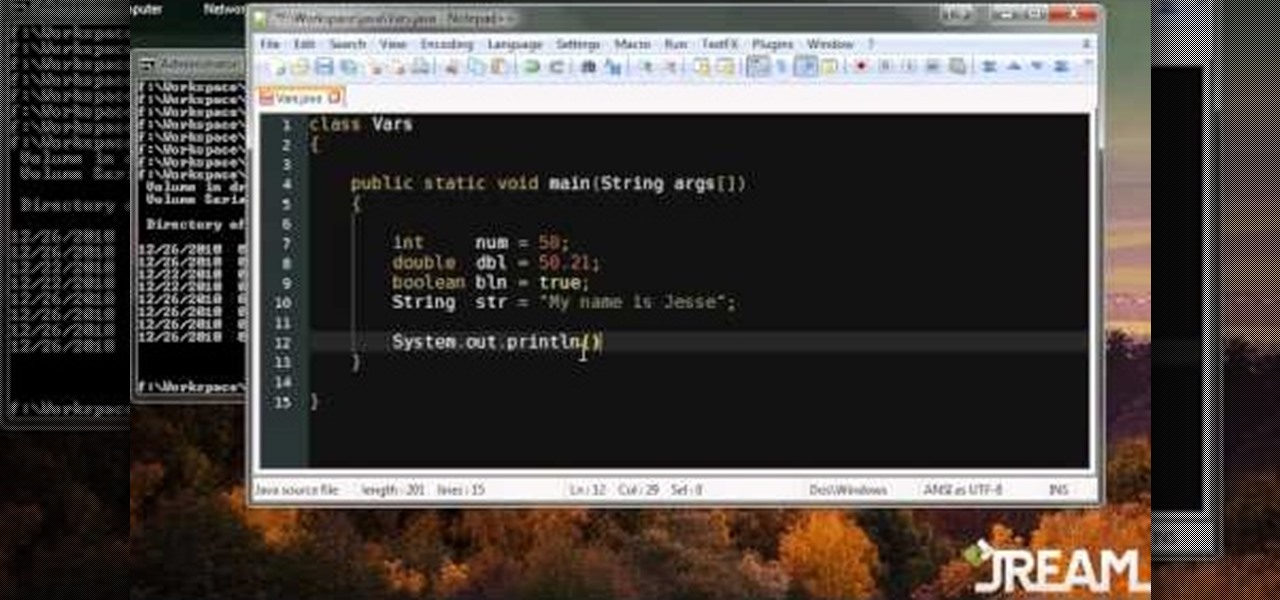
Java works a little differently than languages like Python or PHP when it comes to working with variables. This tutorial shows you what the difference is, how you can define your variables and the easiest ways to work with them when writing programs in Java.

In this clip, you'll learn how to add Shaders and Pixel Bender to Away3D Lite in Adobe Flash Builder. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

In this clip, you'll learn how to generate a basic MySQL database for use with Celtx. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

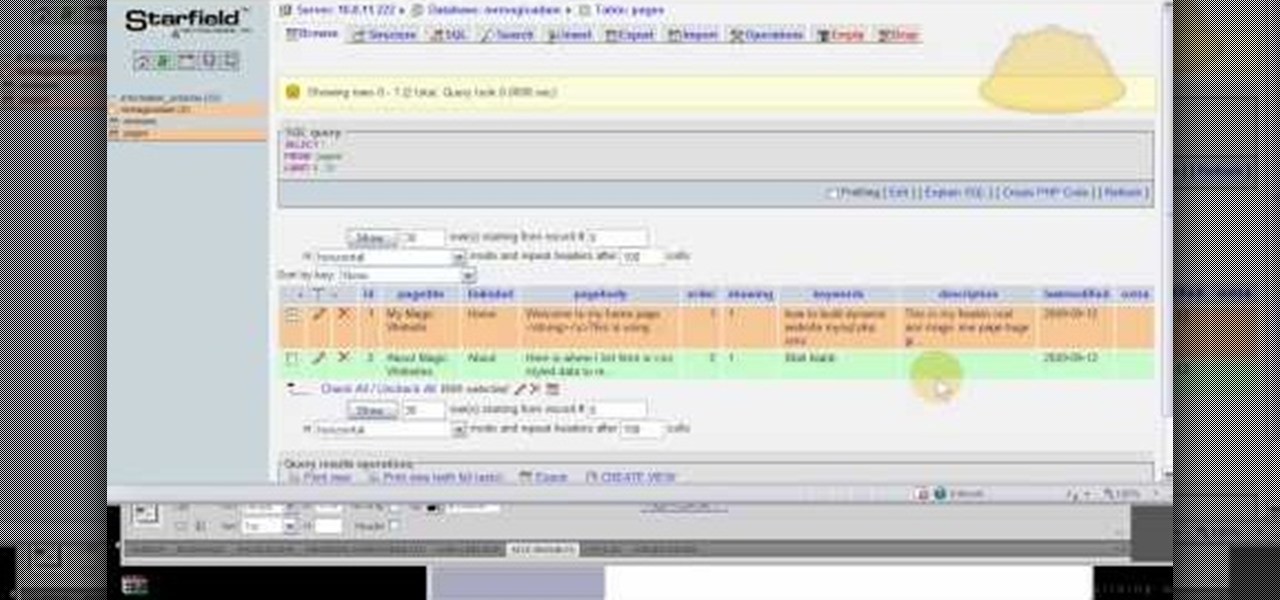
PHPMyAdmin is a tool for website creators who may not yet be comfortable writing custom database scripts using straight PHP. This tutorial shows you how you might use PHPMyAdmin for your own website and display all the information contained on your website in just one file.

Adobe Dreamweaver CS4 gives you several tools that you can use to manage your website without having to know the PHP or MySQL programming languages. This is a great way to keep track of and manage your website without having to learn how to code!

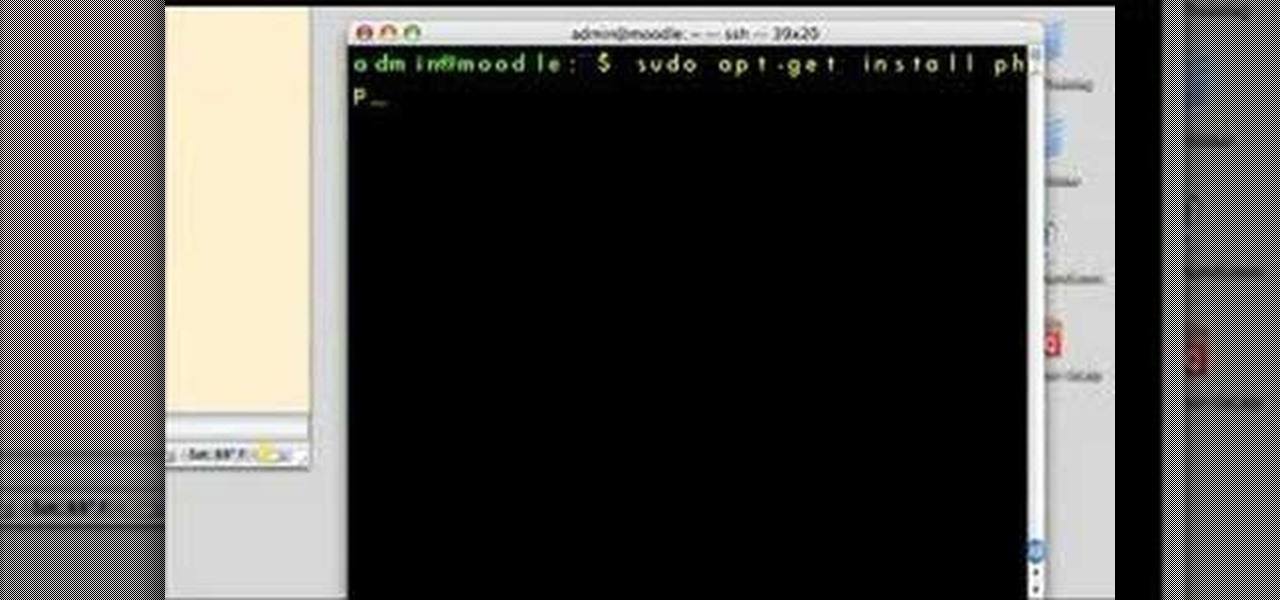
Interested in teaching an online course using your own server but can't quite figure out how to install everything you'll need? This video demonstrates how to sinstall the PHP GD Library for Moodle, the free, open source course management utility, via SSH. For exhaustive, step-by-step instructions, take a look.

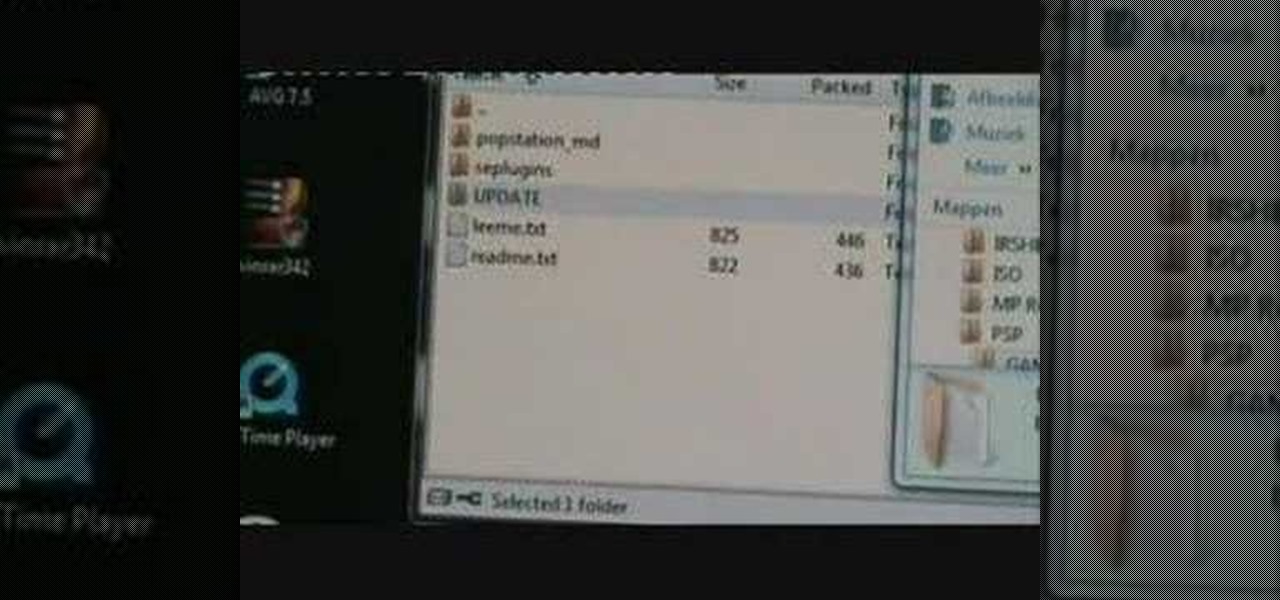
Watch this video to learn how to update your Sony PSP to firmware 3.71 m33-4. This is custom firmware which is used for many PSP hacks. The link to download this is http://www.pspsource.de/news.php?extend.2747

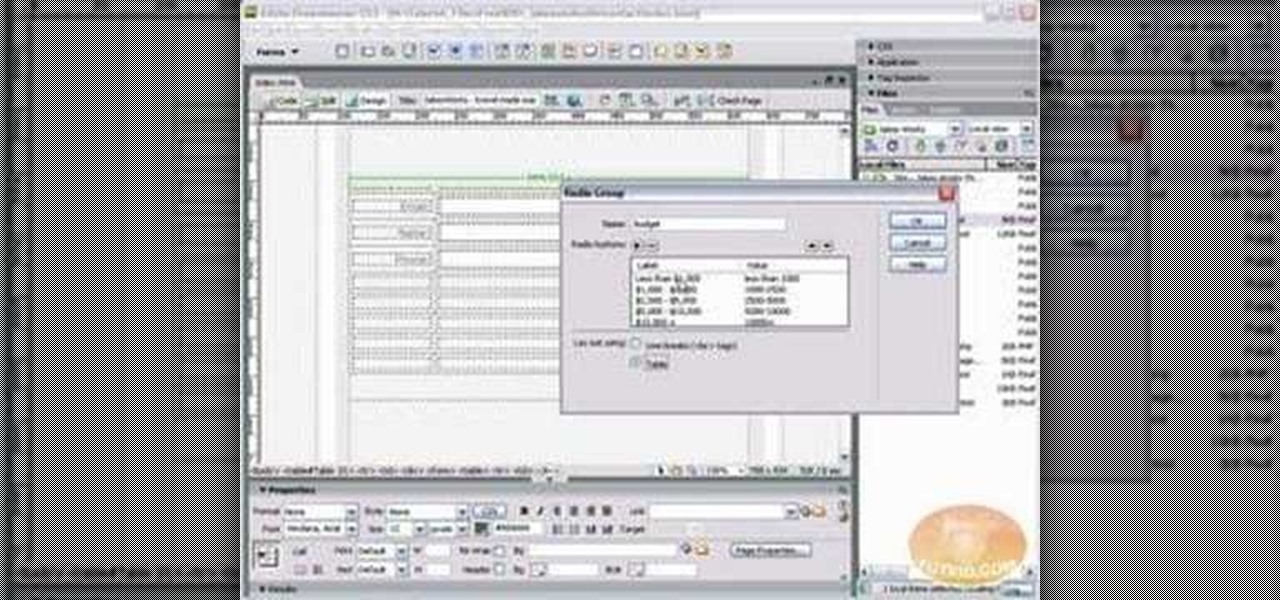
Learn how to build a web-based form using HTML. This tutorial covers using Labels, Text Fields, Text Boxes, Radio Button Groups, Checkboxes, The Clear and Submit buttons, Drop down Menus, as well as many of the properties you can edit while building the form. The form will be ready to be linked with a PHP file for use when you are finished.

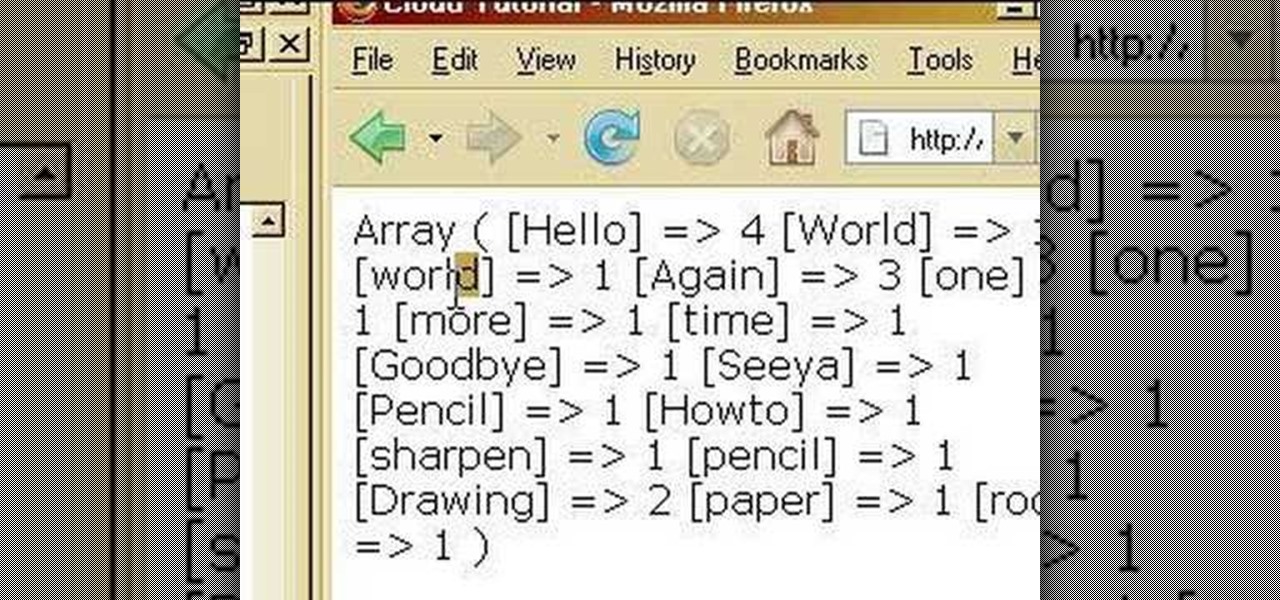
How to generate a tag cloud - a collection of tags that displays keywords in different sizes based on their frequency of use - using PHP.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

In this clip, you'll learn how to reset or truncate a MySQL DB table directly with script or indirectly through PHPMyAdmin. Whether you're new to the PHP scripting language or a seasoned developer mereley looking to pick up a few new tips and tricks, you're sure to benefit from this video tutorial. Take a look.

In this two part video drum lesson, learn the dynamics markings mezzo piano, mezzo forte, pianissimo and fortissimo. In order to do this lesson you will need the beat sheets "Dynamics" and "Dynamics 2."

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Tossing old computers and electronics in the trash is bad for the planet. Techno-Guru Lloyd gives a smarter alternative.

The internet has created amazing new standards for how closely information can be followed. If you want a portable analog unit that will monitor one important piece of online info continuously and have some DIY electrical knowhow, watch this video. It will show you how to use an Arduino Ethernet Shield to make an internet meter to monitor email, stocks, and other online info on a simple analog display. You will need to know some PHP to make this work.

Working with Lady Gaga for the "Telephone" music video must have opened up a whole new world of visual possibilities to Beyoncé, because for her new music video, "Why Don't You Love Me?," she goes way out of character to play a '50s housewife and several other '50s archetypes.

With thousands of beauty companies out there, we can generally find at least one lipstick shade that makes us look more dazzling than New Year's Eve. But sometimes, whether you need to match your lipstick to your dress or just can't seem to find The One, you need a specific color that no brand carries.

You can enable teathering and MMS on your iPhone 2G or iPhone 3GS even if you have AT&T or any other carrier by browsing to a website using Safari on your iPhone. Just select your country and carrier and download the profile.

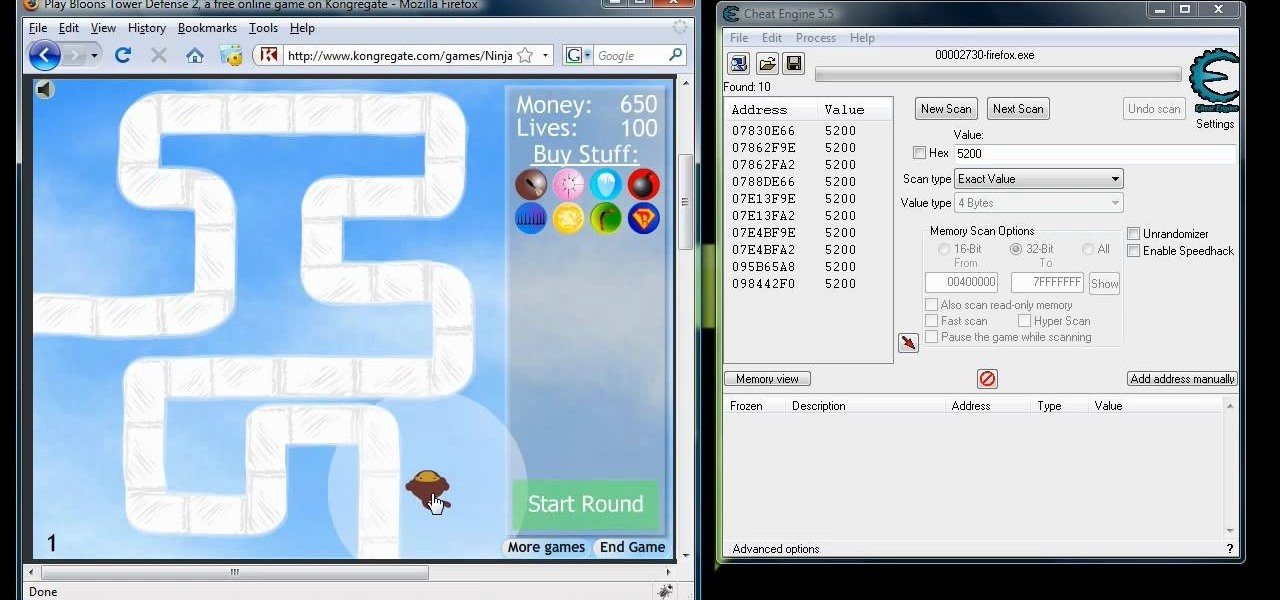
Household Hacker demonstrates how to hack flash games. To get started, you need:

This is for everyone who has ever been frustrated by this mightiest of puzzles. Solving the Rubik's Cube.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

Add a chat program to your website and allow the logged in users to talk to each other! You can write this program using Adobe Flash CS3, PHP and MySQL. This tutorial shows you how to write your own Flash chat program incorporating all three systems.