Because of Android's new SafetyNet system, certain apps can now block rooted users or prevent you from accessing them altogether — but at least for now, there are still ways around these restrictions.
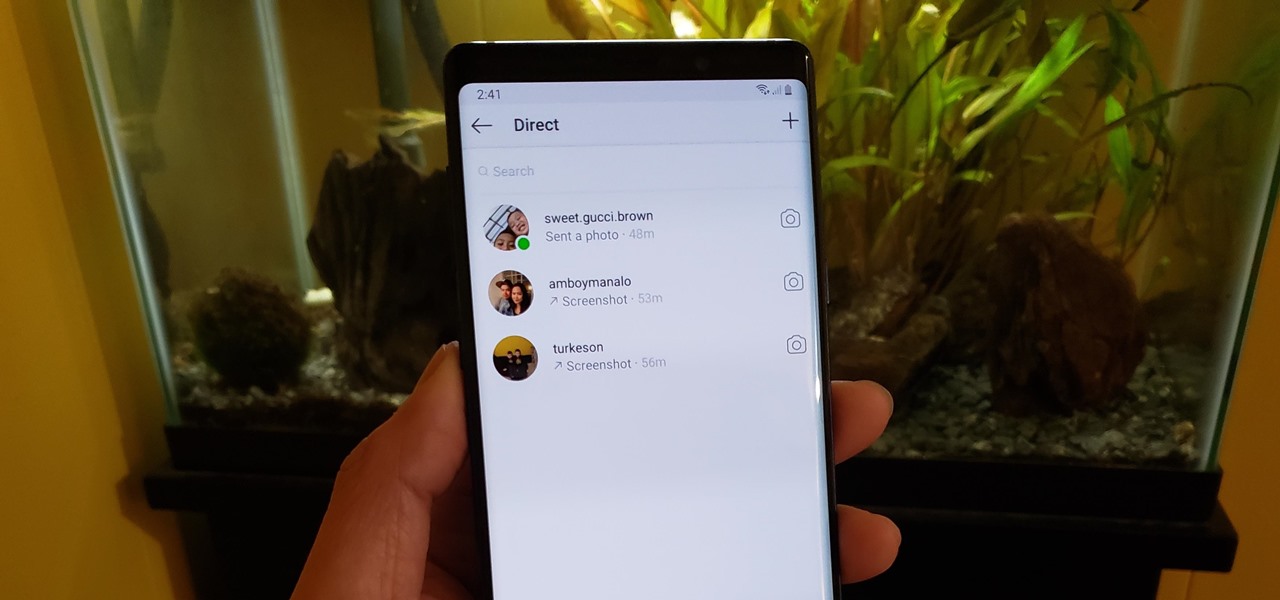
If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, there's an easy way to check if the phone you're about to buy is legit.

The Galaxy S8 and S8+ haven't even hit shelves yet, but some of the stock apps from Samsung's latest flagships have already been leaked. The biggest one so far is the new Samsung Experience Launcher, which replaces TouchWiz Home, and is quite a bit different from anything you'll find on previous Galaxy models.
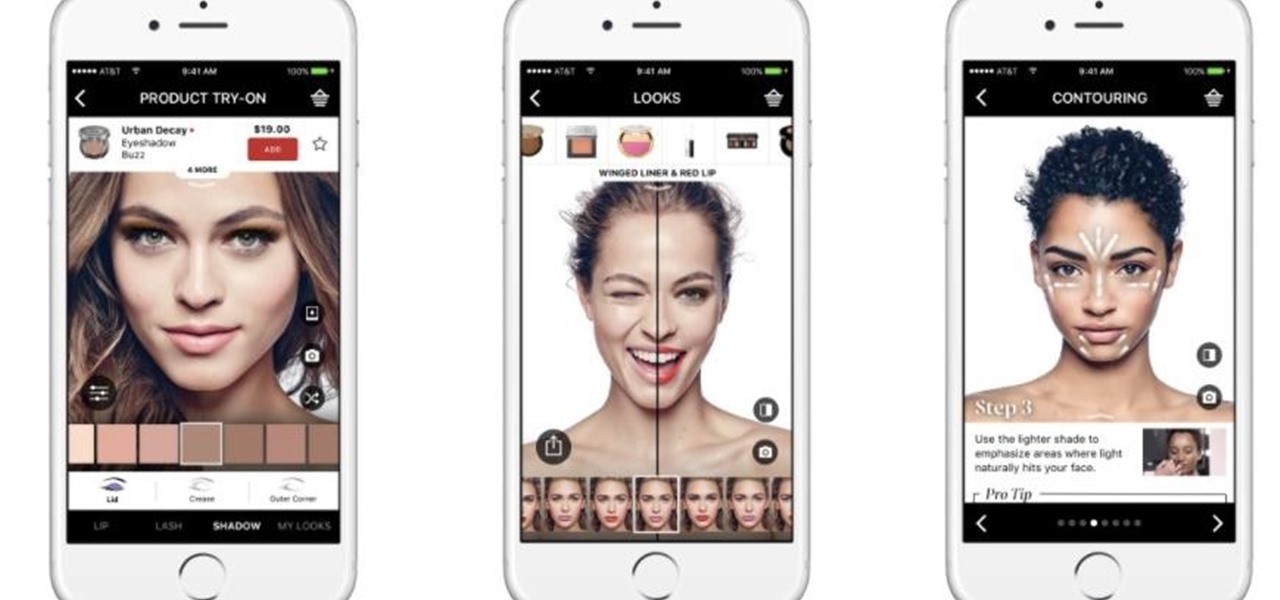
Listen up ladies, there's no need to go to Sephora and model a hundred different shades of lipstick anymore. Now with Virtual Artist, Sephora's award-winning app, for iOS and Android, you can virtually test thousands of shades of single and palette eyeshadows, lip colors, and even false eyelash styles from their new augmented reality-based feature.

The LG V30 has finally been announced and was rumored to be released sometime in September, but September has come and is almost gone, while LG fans have been waiting anxiously. The V series offers a more robust media experience when compared to LG's other flagship, the LG G6. Since the phone has been announced, we do have all of the details for the third flagship in LG's V series, and believe me, it's sounds like it'll be worth the wait.

Lenovo, the company that now owns Motorola, just announced two new entries in their wildly successful midrange Moto G series. The Moto G5, and its bigger brother, the Moto G5 Plus, were both shown off in detail at Mobile World Congress 2017 in Barcelona, Spain.

The Pixel and Pixel XL both use AMOLED screens, which are noted for their deeper blacks and sharper contrast ratios when compared to traditional LCD panels. However, AMOLED displays still have one fairly major downside, and that's the fact that they're vulnerable to screen burn-in.

Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one major repercussion: The servers that used to host the popular CyanogenMod custom ROM have now been shut down.

In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our refined hacking Ubuntu container. Before we dive right in, though, let's make sure we still have a functional Docker installation.

Now that Android 7.1.1 has been released, several features that were previously exclusive to Google's new Pixel phones are now available on the Nexus 6P. However, Google seems to be holding back on the Pixel's best features, as things like the "Night Light" red screen filter, "Moves" gestures, Google Assistant, blue accent color, and the new solid navigation buttons are still only officially available on the Pixel.

LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader is absolutely pointless, as having it locked will not hinder normal device usage, which is kinda true.

There's one thing that I've always liked about iPhones, and that's their centered digital clock in the status bar at the top of the screen. On Android, it's always on the right side by default, and there's no easy setting that lets you just change it to the center position. But if you have a Google Pixel XL, there's a simple modification you can perform to get exactly that—a centered status bar clock.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

Apple released 10.2 to developers yesterday, which contained some new features that you'll probably want right now on your iPad, iPhone, or iPod touch. Lucky for you, the Public Beta is pushing this same update out today.

Samsung's latest flagship devices, the Galaxy S7 and S7 Edge, as well as the Note7, have a useful feature called "Always On Display." With this one enabled, the clock and some other information will continue to be shown on the screen, even when you lock your phone or turn your screen off.

New releases of iOS are always pretty exciting. I remember the anticipation buildup of iOS 7 before it was announced at WWDC 2013, as it was expected to be a complete game changer compared to previous versions—and it was.

If you're standing in a foreign city, surrounded by signage in a language you don't understand, you won't suddenly be able to read it. But with a clever feature in Google's Translate app, your smartphone can.

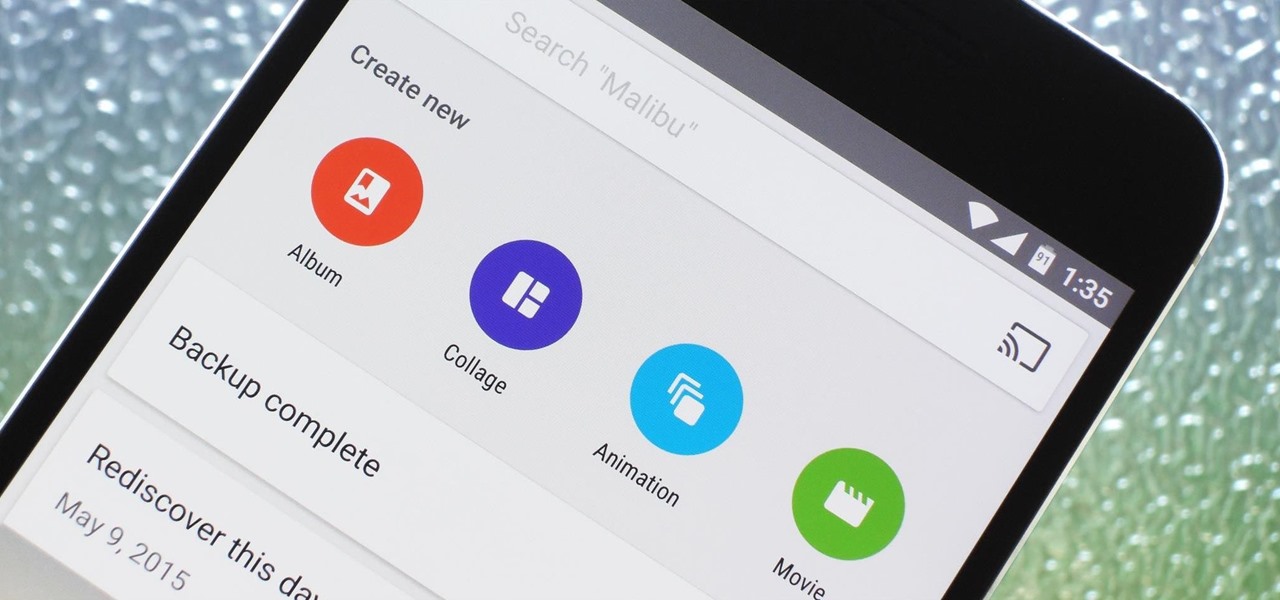
Google Photos is one of the best photo management services out there. It allows you to back up an unlimited amount of high-quality images without ever paying a dime, the photos and videos sync flawlessly across all of your devices, and its neural network-powered visual search feature seems like something that was pulled directly out of a Sci-Fi movie.

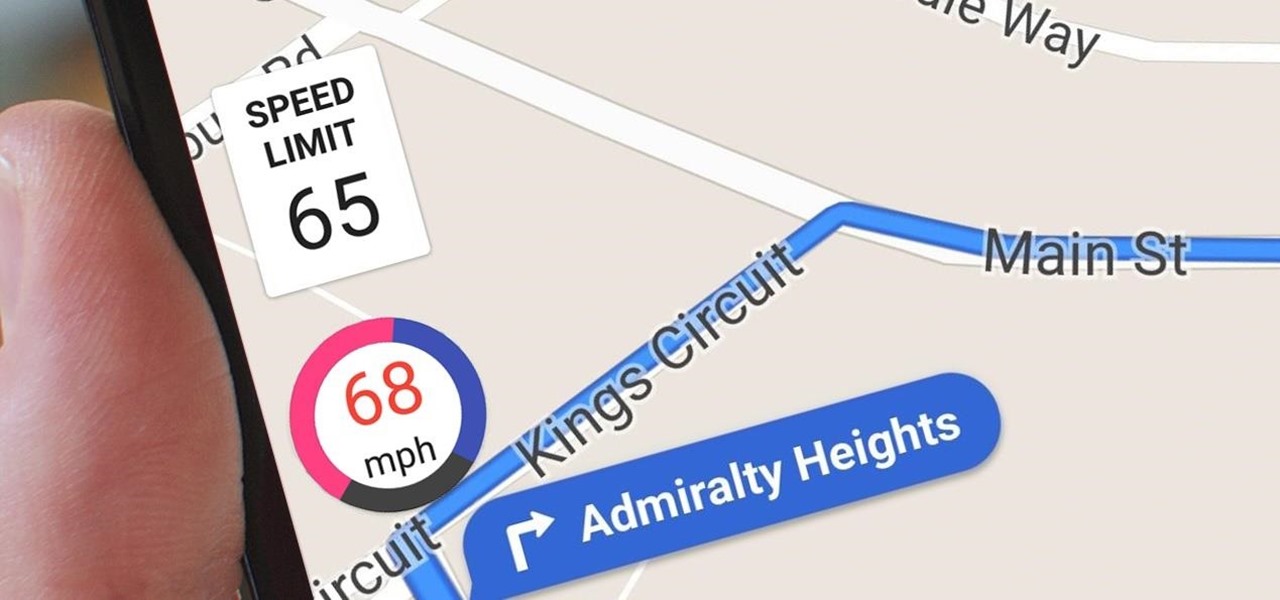
Google Maps does a lot of things well, but one feature it's always been lacking is an on-screen speedometer. Well, now you can add one with Velociraptor, and you can even set it to alert you when you're traveling above the speed limit.

Smartphones are designed to be used in portrait mode primarily, so smartphone apps are created with that layout in mind. This means that practically every app on your phone is vertically oriented, which, in turn, means that we have to scroll up and down quite a bit.

Samsung's latest flagship devices—the Galaxy S7 and S7 edge—both sport an interesting new feature called Always On Display, or simply AOD. When enabled, this feature keeps the clock, date, and other bits of information visible at all times—even when the screen is off.

The only knock on Samsung's last round of flagship devices is that TouchWiz is still alive and kicking. Aside from this overbearing skin that's been applied on top of Android, the Galaxy S6, S6 edge, Note 5, and this year's Galaxy S7 models are some of the best phones money can buy.

If you find yourself switching between Android devices frequently—for instance, your Nexus 6P and a Samsung tablet—you've probably noticed how the button placement can be different. Normally, it's back, then home, then the recent apps button, from left to right. But Samsung devices have this backwards, which can lead to frustration when muscle memory kicks in and the back button isn't where you expect it to be.

There are few things more annoying in life than getting interrupted—especially when you're in a groove, jamming out to your favorite song. If we can all agree on that sentiment, then why is it that our phones mute the music we're listening to for a few seconds whenever a notification comes in?

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

As one of the most popular home screen apps on Android, the Google Now Launcher is used by millions of people across the world. The two main reasons behind this success are its integrated Google Now home page and an elegant, easy-to-use design.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

Now is the time to act if you've been in the market for some must-have Android apps but felt like the price was a little out of your range. The Google Play Store is running a sale so you can pick up some high-quality paid apps—including the popular Nova Launcher Prime and Poweramp Music Player, among many others—for just $0.99 each. While there are quite a few solid apps here you should try—and with a two-hour refund window, why not try them all—here are our favorites you should seriously con...

Microsoft is working hard to make Bing a good alternative to Google for more than just looking up images of the "human anatomy" that Google and a lot of other search engines filter out of their results.

Every phone has its issues and quirks, and the Nexus 5 is no exception to this rule. One of the most common troubleshooting questions asked by its owners is "Why does my Nexus 5 keep shutting off or restarting?" where the device suddenly decides to reboot or power off randomly on its own.

Although they're often times the primary source of income for websites, on-site advertisements can annoy even the most tolerable reader. That's why ad blockers have been some of the most popular downloads on Firefox and Chrome for some time now, demonstrating that when it comes down to it, most people just want nothing to do with ads shoved in their face.

There's a feature in Google's Photos app for Android, iOS, and the web that lets you create shared albums with your friends and family. It's really a useful feature that makes it fun and easy to collaborate on an album with a person or persons of your choosing.

If you have never heard of a Virtual Machine (VM) before you might think it to be some new kind of gamers virtual reality system, and that would be incorrect. A virtual machine is a Virtually a real computer that exists inside of your own computer. You can run Kali inside of a Windows environment via your VM. Not quite the same as an actor portraying an actor on TV. A virtual machine will have it's own IP address and you have the ability to network to it from your Real (Host) computer and bac...

If you ever need to make calls and/or send texts to the U.S. or Canada from abroad, or even just receive them from those locations, there's an easy way to do so without breaking the bank. In fact, it's free, and all you need is a smartphone, computer, and some free tools.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

With new messaging services being pushed out constantly, it can be a pain trying to keep track of them all on your Android device. We had previously shown how to stay on top of them all with a unified "inbox" app, but that still requires you to have each individual app installed. While looking for a true one-stop messenger, I came across Disa.