It's a real challenge to create exploding targets that can be set off by low velocity projectiles, yet remain safe to handle without risk of ignition during construction.

Yesterday, the entire Internet was talking about how the new Kindle Fire HD was supposed to be incredibly difficult to hack. Turns out, the folks over at XDA Developers are smarter than they thought—one day later, the mystery has already been solved. The exploit is the same one found by sparkym3 in Ice Cream Sandwich, but Amazon must have forgotten to patch it. As with any root, you can cause some serious damage, or brick your device completely if it's not done properly, so proceed at your ow...

Watch this instructional guitar video that shows you how to play simple Blues Runs in basic keys, all on two strings. This is just a simple collection of basic runs that beginners can incorporate into their playing - just gets away from basic chords a little. There's a short demo piece in E at the end of the video. This music tutorial is outlined as follows: fretboard diagrams, Blues runs in the key of E, Blues runs in the key of A, Blues runs in the key of D, Blues runs in the key of G, and ...

Dave demonstrates how to perfect your running technique with three easy drills. Running coaches use a wide variety of biomechanical drills and skills to enable the athlete to run more efficiently. Practice the following three drills to improve your running technique: run like a waiter/waitress, pelvic tilt, and baby steps.

Play tight defense and control the pace of the game. Learn how to run a man-to-man defense in youth league basketball in this free series of basketball lessons videos from an experienced coach.

Shut down the opponent's star player! Learn how to run a zone defense in youth league basketball in this free series of basketball lessons videos from an experienced coach.

Get all the players open for a shot. Learn how to play the motion offense in youth basketball in this free basketball lesson video from an experienced coach.

In this video the tutor shows how to graph a straight line using the rise over run method. The rise over run trick allows you to graph a straight line as long as you have a starting point and a slope value in the form of a fraction. The first step is to graph the starting point. In the second step he states that the numerator of the slope is rise and the denominator of the slope is run. He says that the rise is vertical and the run is horizontal and shows how do rise and run using those value...

Seems like it should be easier, but running downhill takes as much strength and control as running on the incline. Pick up the technique and you'll pick up your race time. You will need properly fitted running shoes

There's nothing wrong with running Windows on your OS X machine: all you need is Boot Camp, right? Wrong. There's a better way: virtualization software, such as the Parallels Desktop for Mac or VMware's Fusion. If you run virtualization software, you can run Windows operating systems like XP and Vista inside of OS X. Features like "Coherence" or "Unity Mode" even let you run a Windows application as if it were just another OS X app. But which software should you choose? In this tutorial, CNET...

The Android operating system for cell phones from Google lets you run multiple applications at the same time! By long pressing your home key (touching and holding) you can easily go back and forth between your most recently used apps. When you listen to music, you can easily switch to other apps while still enjoying your tunes! This video shows you the gist of it. Learn to run multiple apps on your Android-powered phone.

If you have been looking for a way to get the popular Joomla Content Management system running on Windows with IIS, you may have run into many problems. In fact, many people spend days trying to get Joomla running on IIS and run into roadblock after roadblock. The problem is getting PHP, MySQL, Joomla and IIS to all play nicely together. As you search for solutions, it is easy to find part of the answer, but rarely do you find it all in one place... until now. In this video tutorial we start ...

The deadly Wuhan coronavirus outbreak has not only has claimed lives in China but also has caused disruption around the globe, particularly in the tech industry. To date, the virus has claimed more than 1,000 lives in China, according to the country's officials.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.

Paying for street parking in New York City just got so much easier. Instead of searching for loose change or hoping you didn't forget your wallet, you can use a device you always have with you: your phone.

This just in! Some of Frito-Lay's chips might be bad for your health for reasons other than the fact that they're deep fried potatoes.

A New York creamery was forced to recall items after a fatal disease outbreak stemming from their soft cheese products.

To much of the United States, Zika seems like a tropical disease that causes horrible problems in other countries but is nothing to be worried about stateside. It may make you rethink your beach vacation abroad, but not much more than that. However, if you live in Florida or Texas, the possibility of getting a Zika infection where you live is real — and local outbreaks are more and more a possibility.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

The months of constant snowfall and freezing temperatures seems endless once the excitement of the first snowfall fades, and you become weary of traversing black ice and other slippery streets.

With the countless daytime talk shows starring and featuring doctors, nurses, and other medical specialists, discovering new ways to live a healthy life is just a remote click away. Although their shows might draw you in with incredible facts and mind-blowing secrets to weight loss success, it's important to take each televised recommendation with a bit of suspicion—most of these familiar faces aren't exactly telling the truth.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

Remember those horrible, soul-crushing studies from a few years back linking grilled meats with cancer? Unfortunately, they're still true, but scientists have recently found that an unexpected ingredient can curb some of the harmful effects of high-temperature cooking.
In any project management career, there is no such thing as a person who knows everything for each project. Many times, those who got too much confident with their jobs fail because they were not able to make things clear before and during the project implementation.

Life has many perils: parasites, predators, and pitfalls. Eventually, any organism will succumb, and if that organism has not first passed on its genes, those genes will face extinction.

Even though Eyeon Fusion has been designed to run on a PC, you can still get it to run well on a Mac. If your computer is already Intel-based, you can use Bootcamp to set up a partition and run Eyeon there. Alternatively, you can parallelize your desktop and use this to run Eyeon Fusion.

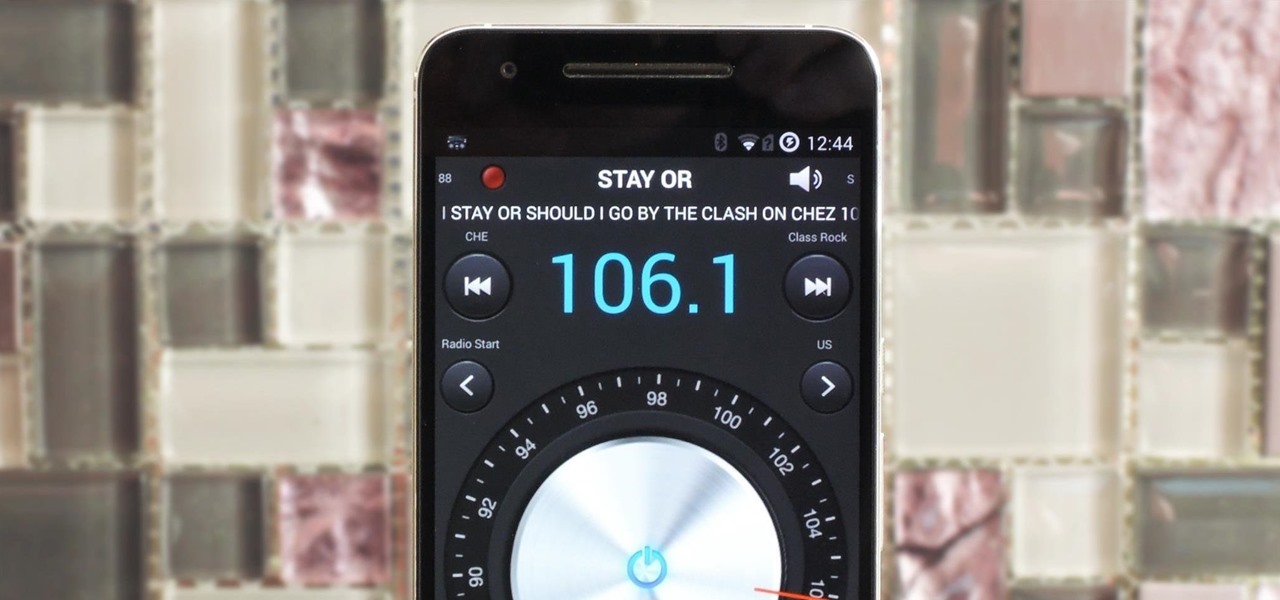
Android smartphones have all sorts of connectivity chips built in, including Bluetooth, Wi-Fi, GPS, NFC, and mobile data. But what about AM or FM radio, two of the most common methods of wireless communication?

With most of the new dishwashers today, they tend to run longer in order to give you the best quality wash. There are many special cycles that are built in that tend to extend the run time of the machine.

Basically there are three quick ways to run a program as administrator. You can do that by clicking on cmd. We usually use this cmd prompt for finding your I.P. address and you can modify user accounts also. Another way is to click on start and type cmd in Run. Make a right click on cmd and click Run as Administrator. Final way to run program as an administrator by having right click on the program and select properties next select Compatibility, then select Operating System and finally, sele...

You're a committed environmentalist but you love your candles. What are you to do? Did you know that you can recycle your candles? There's bound to be stuff left over. Just watch this video and learn!

Ever wanted to know how to disable an attacker? The trick to getting away from an assailant – even one who's bigger and stronger than you are – is to hit 'em where it hurts.

Testing products for a living is a bit more complicated than it sounds. You Will Need

Thanks to modern "smart phones" and the internet, media by the people, for the people is finally a reality. Here's how to use your phone to be a mobile journalist.

Watch this instructional fitness video to learn how to run steps. You need to find a stairwell to learn how to run steps. Running up stairs is a simple and efficient exercise, but you should make sure you are doing it right. It's important to walk down the stairs quickly but safely. Try a more advanced stair run by skipping steps.

Watch this instructional fitness video to learn how to jog faster. Running is a simple and efficient exercise, but you should make sure you are doing it right. Work on tempo runs, repeats and hills. It's important to stay relaxed when running and use all of your tense energy for moving forward. In order to run faster, you will have to push yourself, so take periodical breaks to regain breath and strength.